How to remove remote administration tools
Remote administration tools are legitimate until hackers get their hands on them
Remote administration tools are initially legitimate applications that can be used to monitor somebody's actions in real-time. There are thousands of such apps available, some of which might be open source or viable commercially. Such apps are typically based on based on the server and client technology, where a remote connection can occur via the local network or the Internet. The server part runs on a controlled computer and receives commands from the client, which is installed on the remote host.[1]
Remote administration tools are divided into malicious and legitimate applications. Parasitical RATs, also known as remote administration trojans, are very similar to backdoors and have very similar functionality.[2] However, they are not as viral as backdoors and do not have additional destructive functions or another dangerous payload. They do not work on their own and must be controlled by the client.
The malicious RAT works in the background and hides from the user. The person who controls it can monitor the user’s activity, manage files, install additional software, control the entire system (including any present application or hardware device), modify main system settings, turn off or restart a computer.[3]
The name of these malicious programs are also commonly used in scare campaigns – malicious actors distribute fraudulent emails to users whose login credentials were previously compromised in a data breach. The message claims that the victim's machine is hacked, and a remote administration trojan was installed that let them record compromising material via the camera.
Users are then prompted to pay in Bitcoin for the hacker not to disclose the alleged video to their relatives, coworkers, and friends. In reality, it is unlikely that the malware is installed on the device of the user who received the email in the first place. However, the terminology used by the attacker, along with the real credentials of the victim, might convince even the more advanced users that the message is legitimate.
While sex-based extortion was prevalent even before the internet times, the rise in online fraud using the same theme online has especially peaked during 2018 and has not stopped being distributed ever since. The extremely sensitive nature and psychological manipulation are what made the bitcoin-extortion scams so successful.
| The main purpose | To allow remote access to the system |
|---|---|
| Types | Safe and malicious. Malicious tools can also be called as Remote Access Trojan |
| Main danger | Can be used by hackers to connect to the target system without the user's permission |
| Popular examples (malicious) |
Gh0st, NanoCore, AMMYY, Beast, PC Invader, Back Orifice, Bifrost, Blackshades, Sakula, Havex, Orcus RAT, Dark Comet, njRat |
| RAT scam campaigns |
|
| Symptoms of the infection | Locked keyboard, other software installed without permission or knowledge, the device runs slow and crashes (signs of infection) |
| Can be set to | Steal information, alter system settings, install malware, track the victim |
| Installation | Manual (when legitimate RAT is installed on purpose) and stealthy. In this case, installation is performed with malware, infected email attachments, etc.[4] |
Legitimate remote administration tools are commercial products targeted mostly at system administrators. Their primary purpose is to allow the authorized access to computers for fixing them or controlling them remotely. Nevertheless, legitimate RATs have the same functionality as parasitical programs and, therefore, can be used for obvious malicious purposes.
This type of malware gets used in targeted attacks and massive spam campaigns.[5] Malicious file attachments in phishing emails get used to distribute such infections since the downloaded and opened file triggers the infection automatically RAT can run without any permission or users' knowledge.
Later on, after the initial infiltration, such trojans can be set to spread other malware like ransomware or cryptojacking malware. This way remote access trojans work as backdoor tools for other viruses. RATs can also run processes in the background directly like cryptocurrency mining.

Activities that are performed with the help of a Remote Administration Tool
As we have already mentioned, legitimate RATs are very similar to illegal ones. However, they are used only for illegal activities, such as the ones given below:
- Allowing the intruder to create, delete, rename, copy or edit any file. The attacker can also use RAT for executing various commands, changing system settings, altering the Windows registry and running, controlling or terminating applications. Finally, it can be used to install optional software or parasites.
- Letting the attacker control hardware, modify related settings, shutdown or restart a computer without asking user's permission.
- Allowing the malicious person to monitor the user's activity on the Internet. This activity can lead the victim to the loss of passwords, login names, personal documents, and other sensitive information.
- Capturing screenshots and tracking user's activity. All data, which is collected with the help of such a technique, is transferred to the intruder.
- Degrading computer's performance, decreasing Internet connection speed and security of the system. Typically, such viruses can also cause computer's instability.
- Hiding from the user and complicating its removal as much as possible.
The distribution techniques of Remote Administration Tools (RATs)
Remote administration tools (RATs) aren’t similar to regular computer viruses. Their server parts must be installed on the affected system as any other software. Of course, this can be done either with or without user's content. There are two major ways how can an unsolicited RAT get into the system:
- Manual installation. A legitimate remote administration tool can be manually installed by the system administrator or any other user who has sufficient privileges for the software installation. A hacker can break into the system and setup his RAT. In both cases, a privacy threat gets installed without the affected user’s knowledge and consent.
- Infiltration with the help of other parasites. Malicious remote administration tools are installed by other parasites like viruses, backdoors or worms. Often they are dropped by specific trojans, which get into the system using Internet Explorer ActiveX controls or exploiting certain web browser vulnerabilities. Their authors run insecure websites filled with malicious code or distribute unsafe advertising pop-ups. Whenever the user visits such a site or clicks on such a pop-up, harmful scripts instantly install a trojan. The user cannot notice anything suspicious, as a threat does not display any setup wizards, dialogs or warnings.
To sum up, the malicious version of remote administration tool allows the attacker to work with an infected computer in the same way as with its PC and use it for various malicious purposes. The responsibility for such activity is usually assumed by guiltless users on which systems malicious RATs were installed, as it can hardly be revealed the person who was controlling a parasite.
Any remote administration tool can be used for destructive purposes. If the hacker was unable to obtain any valuable and useful information from an infected computer or have already stolen it, he eventually may destroy the entire system to wipe out his tracks. That means that all hard disks would be formatted, and all the files on them would be erased. Typically, the malicious versions of remote administration tools can affect computers running Microsoft Windows OS. However, there are lots of less prevalent parasites that are designed to work under different environments, including Mac OS X and others.
The most infamous examples of RATs
There are thousands of different remote administration tools. The following examples illustrate how powerful and extremely dangerous these threats can be.
PC Invader is a malicious remote administration tool used by hackers to modify essential networking settings of remote systems. Pc Invader is considered very dangerous as its main aim is to can change vital computer settings, its IP address, DNS address, computer name, default gateway, etc. It also can shutdown or restart a computer.
Back Orifice is an infamous malicious remote administration tool that allows the intruder to do with a compromised computer everything he wants and even more. This tool has a massive amount of dangerous functions and leaves the victim completely unprotected and disorientated. Back Orifice can be used to manage files, run and install applications, terminate defined processes, modify essential system and networking settings, control the operating system, installed software and hardware devices, log keystrokes, take screenshots, capture video or audio, steal passwords, etc. This remote administration tool supports plugins and, therefore, can have different additional functionality.
Beast is just another virus, which belongs to a huge family of Remote Administration Tools. The author of this threat is a known hacker, who is called Tataye. As we know, the first versions of Beast appeared from April 2001 to March 2004. This threat is written in Delphi and is compressed with ASPack.
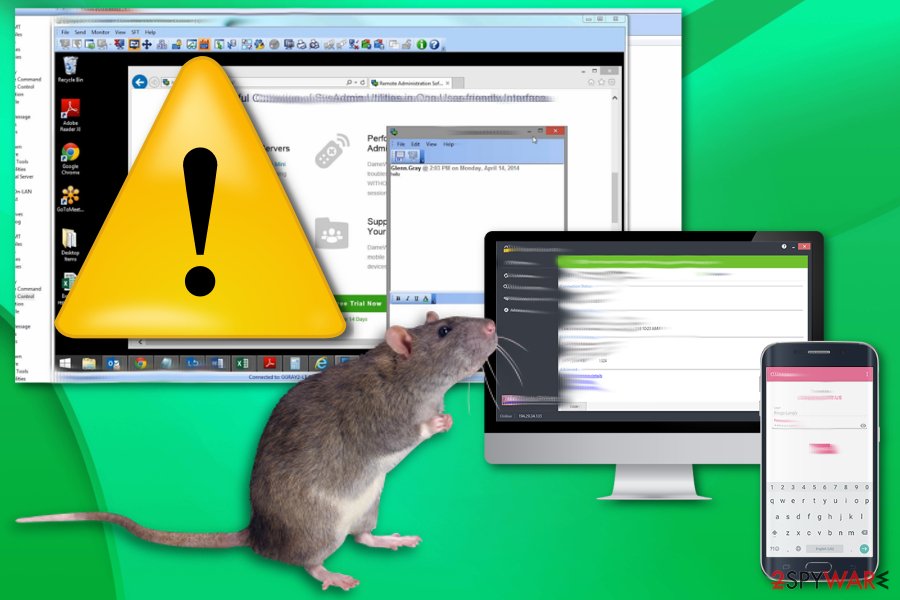
Fraudulent emails claim RAT infection
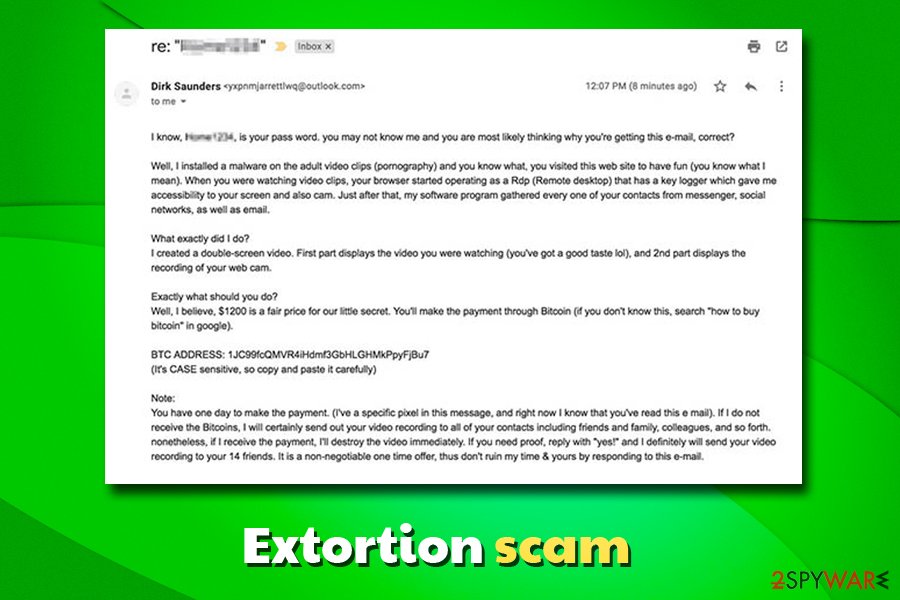
Extortion scams started to be popular in the past few years, and crooks use various techniques in order to make users pay an inadequate amount of money by using blackmail. These types of scams are usually distributed via the emails that were previously compromised in the data breach of a well-known company, such as Ticketmaster, Marriott hotel chain, or Equifax.[6]
Upon receiving the email, users are caught off guard when it starts with “Your email password is XXX,” and it turns out to be correct. In some cases, the password might be outdated, but that still strikes the user hard, as he or she cannot understand where email authors obtained this information.
Immediately, the explanation comes:
I infected you with my private malware, RAT, (Remote Administration Tool) some time ago.
The malware gave me full access and control over your computer, meaning, I got access to all your accounts and I can see everything on your screen, even turn on your camera or microphone and you won’t even notice about it.
Such a statement puts most users in panic mode, as they do not know what to expect, and they believe that their private information is now stolen. In most cases, users are then explained that the RAT allowed the hacker to take over the user's camera and film the compromising video when the user visited an alleged porn site. This is, of course, not true – there is no RAT and no video.
While such a scenario is entirely possible if remote access trojan is installed, the extortion emails only claim this infection, and it is not real. The trick is to make victims believe that the malware is actually present on their devices, and the exposed password is meant to be proof.
Allegedly, those who do not oblige and pay the ransom (which can reach up to $10,000!), the crook is threatening to disclose the video to all contacts in social media networks, access to which was granted via the stolen credentials.
This scam works so well because users are unaware of massive data breaches that occur regularly, and most are too embarrassed/scared to share about the ordeal and end up paying the malicious actor.
Thus, be vigilant and never trust extortion emails. While some sort of compromise is possible, it is always advisable to scan your computer with reputable anti-malware software which would immediately detect and terminate RATs and other present malware. Extortion scam victims who would have checked their machines with security software could have avoided massive financial losses.
Removing RATs from the system
You cannot remove the malicious versions of RATs manually because they hide their files and other components deep inside the system. The most reliable way to eliminate such threats is to use a reputable anti-spyware tool. Such programs can easily help you to detect and remove even the most dangerous viruses, so there is no need to postpone their installation on your computer. You can fix your computer and get rid of any RAT with the help of FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes.
If you think that you are advanced enough to find RAT's files on your computer manually, you should think twice before each removal of your detected components. Otherwise, you may run into serious problems, like computer's instability. Note that lots of Internet resources, such as 2-Spyware.com, can help you with the manual removal of your malware. Detailed instructions on how to remove RAT (malicious one) from the system can be received by adding a question on Ask Us page.
- ^ Remote administration. Wikipedia. The free encyclopedia.
- ^ What is a Remote Administration Tool (RAT)?. Securingtomorrow. Blog about latest security threats.
- ^ Andrew Heinzman. What is RAT Malware, and Why Is It So Dangerous?. Howtogeek. We explain technology.
- ^ Jessica Drew. Email attachments: when is opening them safe?. Toptenreviews. Product comparisons.
- ^ Jake Doevan. New Flawed AMMYY RAT spam campaign infects victims’ computers. 2spyware. Spyware related news.
- ^ Equifax data breach was "entirely preventable," congressional report finds. CBS. American English language commercial broadcast television.
Latest remote administration tools added to the database
Removing BO Sniffer v1.2
Uninstalling Cold Fusion
Terminate PC Invader
Information updated: 2021-06-15