Backdoor.Teamviewer (Removal Instructions)
Backdoor.Teamviewer Removal Guide
What is Backdoor.Teamviewer?
What you should know about Backdoor.Teamviewer malware?
First of all, we must note that TEAMVIEWER IS NOT MALICIOUS and it is NOT REATED TO BACKDOOR.TEAMVIEWER IN ANY WAY. It is a legitimate and trustworthy platform helping people connect remotely. It is a safe software that encrypts every conversation. However, according to the latest reports of virus researchers from Russia, hackers have started using TeamViewer to steal people’s personal information and money. They have been installing this software behind people’s back with the help of Backdoor.Teamviewer and its latest version Backdoor.Teamviewer.49. Once again, these viruses, which belong to Trojan horse category, have nothing to do with TeamViewer and its developers.
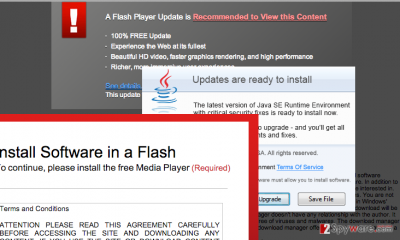
Reportedly, Backdoor.Teamviewer Trojan spreads with a help of Trojan.MulDrop6.39120 Trojan horse, which is spread online concealed as an Adobe Flash Player update. This update can be downloaded from high-risk Internet sites or malicious pop-up ads. If the victim agrees to update Adobe Flash Player, the Trojan.MulDrop6.39120 gets installed along with the upgrade, and it drops TeamViewer app on the compromised computer. Then it swaps one of TeamViewer’s components, called avicap32.dll, with a fake one, which carries Backdoor.TeamViewer.49 Trojan. TeamViewer uses this .dll file within every startup, so, to activate the Trojan, cyber criminals assign this TeamViewer version to startup automatically whenever the victim turns on the PC. When this program launches, the Trojan connects to its command and control (C&C) server and waits for instructions. To prevent this modified TeamViewer version from displaying error messages and to hide it from the victim, hackers turn off error reporting function and also hide TeamViewer’s icon from the Windows notification section.
However, it seems that cyber criminals do not only use this Trojan to steal victim’s personal information and money. Reportedly, frauds also seek to exploit victim’s computer and use it as a proxy server. To put it simply, crooks use the compromised computer as a tool to mask their real IP address and initiate illegal activities without being caught. It is very important to protect your computer from such malicious and complicated computer viruses as Backdoor.Teamviewer. To stop them from infiltrating your computer system is to install and keep an up-to-date anti-malware program on it. We highly recommend you to use FortectIntego software for that. If your computer is already infected with this Trojan, you must implement Backdoor.Teamviewer removal immediately.
How can this Trojan horse get inside your computer?
As we have already mentioned, you can download it as a Adobe Flash Player update. Unfortunately, Flash Player is a gateway for criminals to infect victim’s computers, so they create various bogus websites offering to install or update this software. Please, keep in mind that the only way to get a trustworthy Flash Player on your computer is to go to its official website and see what updates are offered for you. Also, stay away from pop-up ads offering you to install software updates because the most of them are related to suspicious websites and viruses.
You can also end up installing malware by browsing through high-risk Internet sites, installing freeware without monitoring its installation or by simply clicking ads that tend to appear out of nowhere. If you have never heard about clickjacking, bear in mind that it is a technique used by many cyber criminals, which helps them conceal malicious links under various clickable content. In other words, you can click on a deceptive link or ad and automatically install Trojan or another virus into your computer system. If you suspect that you have installed the aforementioned virus accidentally, it goes without saying that you must remove Backdoor.Teamviewer.49 as soon as possible.
How to remove Backdoor.Teamviewer.49?
If you suspect that your computer has been affected by Backdoor.Teamviewer.49 virus, you should scan it with a powerful anti-malware and let it delete all malicious files automatically. You do NOT need to uninstall TeamViewer, especially if you have installed it consciously. As we have mentioned in the beginning of this post, it is a legitimate software that does not pose any danger. The real danger is Backdoor.Teamviewer which can be used to steal your personal data and money. To remove this trojan horse from the system, you should install one of these programs: FortectIntego, Malwarebytes. We do not advise you to deal with this threat manually because it is a very complicated task to do. This threat roots deeply into the computer system, and it manages to make its files look like safe ones.
How to prevent from getting trojans
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
