Gplyra Miner (Tutorial)
Gplyra Miner Removal Guide
What is Gplyra Miner?
Gplyra Miner: what is it and how does it work?
Although “Gplyra Miner virus” might not be the most accurate words to describe this program, there are no doubts that it is not a good one. Gplyra Miner is a highly suspicious piece of software that can enter your computer silently and use your computer’s resources to mine digital currencies. When this potentially unwanted program (PUP) enters the computer system, it performs a security check and checks if the computer is protected with anti-malware software. If it is secured, the miner does not even install itself on the computer system. If it is not, the threat successfully executes and starts its questionable activities.
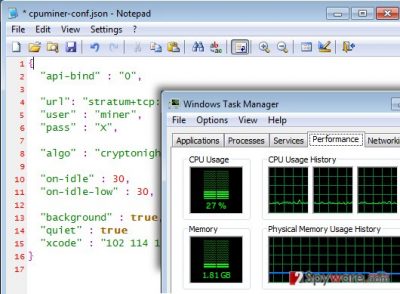
Gplyra Miner places several files in the system. One of them is called CPM.exe, and it is an executive file, which is just an altered copy of CPU Miner malware. This program starts automatically whenever the user turns on the infected PC. Another file that it saves into the computer system is called cpuminer-conf.json, which is filled with instructions that the miner follows. In addition to that, it connects to a certain website (poolminers(.)net) and assigns the victimized computer as “miner.” When all preparations are done, the miner starts using computer’s resources. Surprisingly, it uses up to 30% of CPU power, and it significantly slows down computer’s performance. It goes without saying that you cannot use this power to run other programs, so they are going to run slow, lag, or even crash.
You should remove Gplyra Miner without a hesitation because it is a vague program that takes advantage of your computer without your knowledge. Besides, the fact that it has managed to enter your computer system unnoticed means that your device is not protected, and we strongly recommend you to take care of that. If you want to remove Gplyra Miner automatically and also strengthen the protection of your device, we recommend you to install FortectIntego software.
Why is this program running on your computer if you haven’t installed it?
You can install this miner on your PC unwillingly. Usually, it spreads along untrustworthy third-party software, which can be downloaded from the web for free. For this reason, you should never download freeware from unreliable Internet sites, and if you do so – install it with caution. If you have downloaded a program from a questionable web source, do not rush to install it. There are a few things you should know. First of all, Default/Standard, or Basic/Express installation settings are not trustworthy, and they do not guarantee safe installation. Vice versa, if you choose these settings, you just agree to install all additional programs bundled with your selected program and also make several alterations on your computer system.
If you want to install your desired program without installing additional suspicious applications, opt for Custom or Advanced settings. Then you will be provided with a listing of suggestions to install third-party apps, so just remove the ticks from checkboxes next to them.
Gplyra Miner removal
Obviously, leaving this program on your computer is a very bad idea. Gplyra Miner is a dangerous piece of software that should not remain on your computer; otherwise, it is going to generate profits for its authors by using your computer and also making it vulnerable to various computer threats and attacks. What is more, this miner spreads in conjunction with other PUPs, so there is a great chance that your computer is infected with more than one possibly critical application. If you are not an IT expert, most likely you cannot identify such programs at the first sight. Therefore, we suggest using an automatic spyware/malware removal software, for example, FortectIntego.
How to prevent from getting malware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
