Marlboro ransomware / virus (Free Instructions) - Decryption Methods Included
Marlboro virus Removal Guide
What is Marlboro ransomware virus?
Marlboro ransomware gets defeated in less than 24 hours
Marlboro virus has been spotted by our experts on January 12, 2017. We must mention that this virus has a different name – DeMarlboro ransomware virus. Although this ransomware is not as dangerous as Locky virus [1], getting infected with it gives you a hint that your computer system is unprotected. As soon as it enters the system, it determines whether the system is 32 or 64 bit and uses a particular installer then. The indicated ransomware appends .oops file extension to files that the virus corrupts. However, Marlboro ransomware appeared to be a foolish ransomware variant that uses XOR encryption to lock victim’s files, although in the ransom note, the virus claims to be using RSA-2048 and AES-128 ciphers[2]. The virus leaves a ransom note, which is named _HELP_Recover_Files_.html, filled with data recovery instructions. The virus simply takes files hostage, deletes Volume Shadow Copies[3], and it demands a ransom to set encrypted files free. The ransom note commands the victim to send 0.2 BTC (more or less $155 in Bitcoins) to crooks’ Bitcoin address and then launch Decryptfiles.exe program, which the virus saves to Desktop and Documents folders. Now this is where the developers of Marlboro malware get creative. Instead of pointing the victim to Tor browser’s download site and telling to visit a personal payment website, the crooks simply leave the Marlboro decrypter on victim’s system, which gets activated automatically as soon as the victim transfers the money to criminals’ Bitcoin address[4].
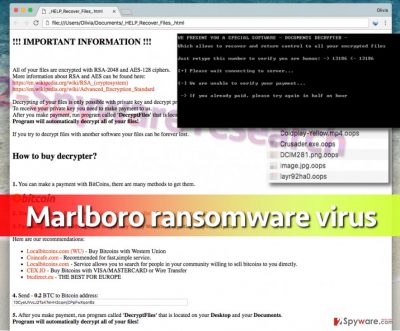
The decrypter presents itself as “a special software – documents decrypter – which allows to recover and return control to all your encrypted files” and, what is even more unusual, the decrypter asks to retype a shown number to verify that the user is a human being. The decrypter then connects to its server to verify the payment, and, if failed, asks the victim to retry in half a hour. If you have been infected with this virus, you must remove Marlboro malware before you try to take any data recovery actions. Use a strong malware removal tool for this task, for instance, FortectIntego or Malwarebytes. At the end of this post, you can find detailed Marlboro removal guidelines that explain how to deactivate the virus and start the malware removal tool.
Updated on January 13th: Marlboro ransomware is defeated, and a free decryption tool is available. Do not even think about paying the ransom! You can download the decrypter made by Emsisoft researchers here.
Ways of distribution
The virus is obfuscated heavily and approaches victims as a DOCM document[5]. Reportedly, malevolent actors working behind Marlboro ransomware project spread this virus via phishing emails that politely ask the recipient to open attached files. All PC users should be aware of this ransomware distribution technique, because, despite its simplicity and banality, it is so far the most efficient way to infect computer systems with malware. Users should be extremely careful and protect their devices by stocking up data backups and installing anti-malware software on their computers (to block malicious programs from entering the computer system and executing harmful commands). It is believed that the virus spreads via other channels as well, for instance, compromised web ads pointing to websites hosting exploit kits, also Trojan horses and so on. If you were infected with this virus a few minutes ago, turn off the computer immediately and plug out the Internet connection cable from the compromised PC.
How can you remove Marlboro malware before using the decryption tool?
Unless you are willing to pay the ransom, you should remove Marlboro virus as quickly as you can. Just do not act hastily – read Marlboro removal instructions presented below this post to learn how to start your computer in a Safe Mode with Networking to be able to run your anti-malware or antivirus software. Otherwise, the virus might block your attempts to launch the malware removal tool (to avoid detection). Please do not try to remove Marlboro ransomware on your own because the virus makes various modifications in Windows Registry, as well as system files (.dll files), not to mention the dozen of files that it drops on the computer system.
Getting rid of Marlboro virus. Follow these steps
Manual removal using Safe Mode
To remove Marlboro virus successfully, you will need to reboot your computer using guidelines presented here. We suggest you read these instructions carefully. Have this tutorial by your hand when rebooting the computer (for example, open this page via your mobile phone or just print them out).
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Marlboro using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Marlboro. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Marlboro from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Do you have a data backup? If so, you will be able to use it now. Do not plug the backup into the compromised computer unless you have deleted the virus with a powerful anti-malware tool. If you plugged the drive with data copies into a computer while Marlboro virus is still on it, you would lose your backup. In case you do not have a backup, we suggest you try these data recovery methods:
If your files are encrypted by Marlboro, you can use several methods to restore them:
Recover with Data Recovery Pro
If you do not have a backup, try Data Recovery Pro. It is a useful data recovery application that helps to restore deleted, corrupted and encrypted files. However, remember that Marlboro virus is sophisticated and Data Recovery Pro might not be able to recover all encrypted records.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Marlboro ransomware;
- Restore them.
Look for Windows Previous Versions
Have you ever enabled System Restore function? If so, you might be able to experience the benefit of it. Follow these instructions to restore individual files:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Use Marlboro decrypter
Researchers from Emsisoft managed to crack the ransomware in less than one day. You can use the tool they have released to set your encrypted files free. Simply download Marlboro decrypter here and find one encrypted file which takes at least 640 bytes of space on your PC and also an unencrypted version of it. Select both files and drag them to decrypter’s .exe file.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Marlboro and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Jan Širmer. A new Locky ransomware attack is coming. Avast Blog.
- ^ Olivia Morelli. Locky ransomware. How to Remove? (Uninstall Guide). 2-Spyware. Fighting against spyware.
- ^ Volume Shadow Copy Service. Microsoft Windows Dev Center.
- ^ Stephen Mihm. Are Bitcoins the Criminal's Best Friend?. Bloomberg. Business and markets news, data, analysis, and video.
- ^ Ronghwa Chong. Locky ransomware distributed via Docm attachments in latest email campaigns. FireEye: Cyber Security .





















