RSAUtil ransomware / virus (Removal Guide) - updated May 2018
RSAUtil virus Removal Guide
What is RSAUtil ransomware virus?
RSAUtil – a ransomware that offers file decryption for a payment in Bitcoin
RSAUtil ransomware is a file-locking virus[1] which first appeared on world wide web in April 2017. It uses a complicated encryption algorithm known as AES, which, once applied, renders people's files useless[2]. The ransomware is written in Delphi[3] and targets English-speaking PC users in particular. The original version appended the file extension after encryption the following way: . [Ransom_email] .ID [victim's ID] . The ransom note is dropped into every folder which is called How_return_files.txt. The first version urged users to contact hackers via helppme@india.com and hepl1112@aol.com.
| Name | RSAUtil |
|---|---|
| Type of malware | Ransomware |
| Detection ratio | High. 47/66[4] |
| Related files | How_return_files.txt, svchosts.exe, NE SPAT.bat, DontSleep_x64.exe, DontSleep_x64.ini, DECODE_ALL_FILES.bat, config.cfg |
| File extensions used | .GORILA .VENDETTA .[alexjer554@gmx.com] .ID [victim_ID] .[batary5588@gmx.com] .ID [8 random digits] .[ransom_email] .ID |
| Ransom note | Always the same – How_return_files.txt |
| Distribution | Unprotected RDP, brute force attacks, malicious spam email attachments, rogue software downloads, phishing websites, etc. |
| Size of redemption | $750 (or more) in Bitcoin cryptocurrency |
| Elimination procedure | Restart your PC into Safe Mode with Networking and download FortectIntego. Run a full system scan with it to get rid of the ransomware. |
There is a wide list of extensions[5] used by RSAUtil. The versions that emerged in January 2018 used .GORILLA and .VENDETTA file extensions. However, previously the virus used .[alexjer554@gmx.com] .ID [victim_ID] and .[batary5588@gmx.com] .ID [8 random digits] extensions to mark encrypted files.
It seems that its developers win not stop distributing and improving the virus. Virus keeps coming back with new and improved versions – the latest one was spotted by security expert Amigo-A[6] on 13th of May 2018. This version RSAUtil virus asks users to contact criminals using Tizer78224@gmx.de, Tizer78224@india.com or Tizer77234@protonmail.com email. Please read more about different variants below.
The crypto-virus encrypts all personal files, including .avi, doc, .docx, .htm, .html, .jpeg, .jpg, .mpeg, .php, .png, .rar, .txt, .xls, .xlsx, .zip and many others. To decrypt them, users need a key which generated to each person individually. Thus, if a ransom is paid and the personal key is given, it will not be useful for anybody else. These decryptors are stored on a remote server and are only accessible to hackers. However, security experts recommend not to contact cybercrooks and remove RSAUtil virus instead.
The contact information may differ according to the RSAUtil ransomware version. Currently, criminals demand victims to pay $750 ransom. Victims are urged to exchange their money to Bitcoin cryptocurrency and transfer the redemption equal to $750 to 1CshTLvSfDrN1ATmC7vBNTkay1MtsA6KVs BTC wallet.
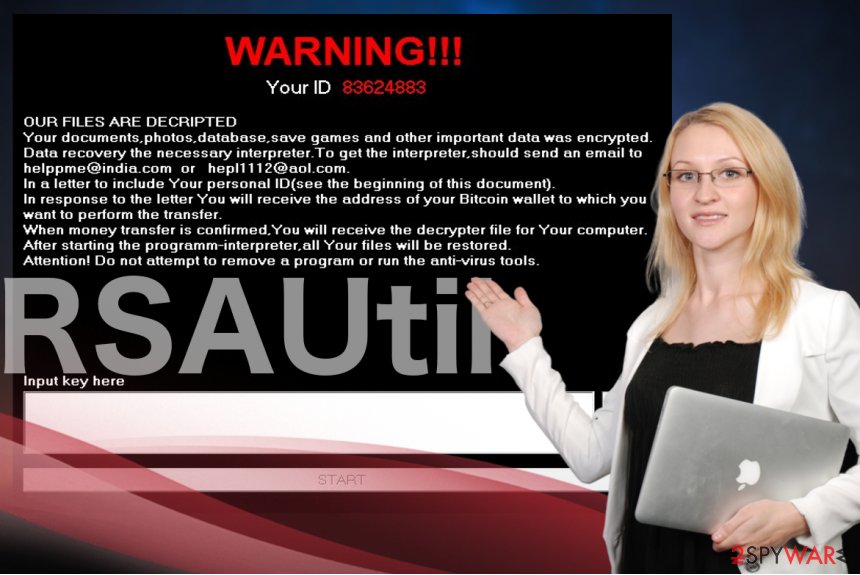
No matter how many changes have been made when improving RSAUtil virus, the ransom note name stays the same — How_return_files.txt. The note gets dropped on the infected device to inform the victims about what has happened to their files and offer some recovery suggestions.
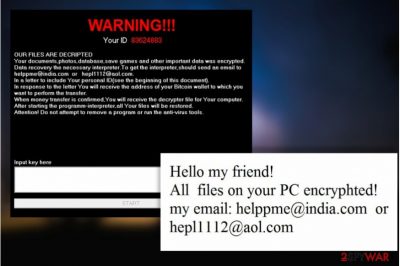
WARNING!!!
Your ID xxxxxxxxxx
OUR FILES ARE DECRIPTED
Your documents, photos, database, save games and other important data was encrypted.
Data recovery the necessary interpreter. To get the interpreter, should send an email to helppme@india.com or hepl1112@aol.com.
In a letter to include Your personal ID (see the beginning of this document).
In response to the letter You will receive the address of your Bitcoin wallet to which you want to perform the transfer.
When money transfer is confirmed, You will receive the decrypter file for Your computer.
After starting the programm-interpreter, all Your files will be restored.
Attention! Do not attempt to remove a program or run the anti-virus tools.
Extortionists have a wide list of email addresses used to scam people out of their money:
- helppme@india.com;
- hepl1112@aol.com;
- batary5588@gmx.com
- batary5588@india.com
- batary5588@protonmail.com
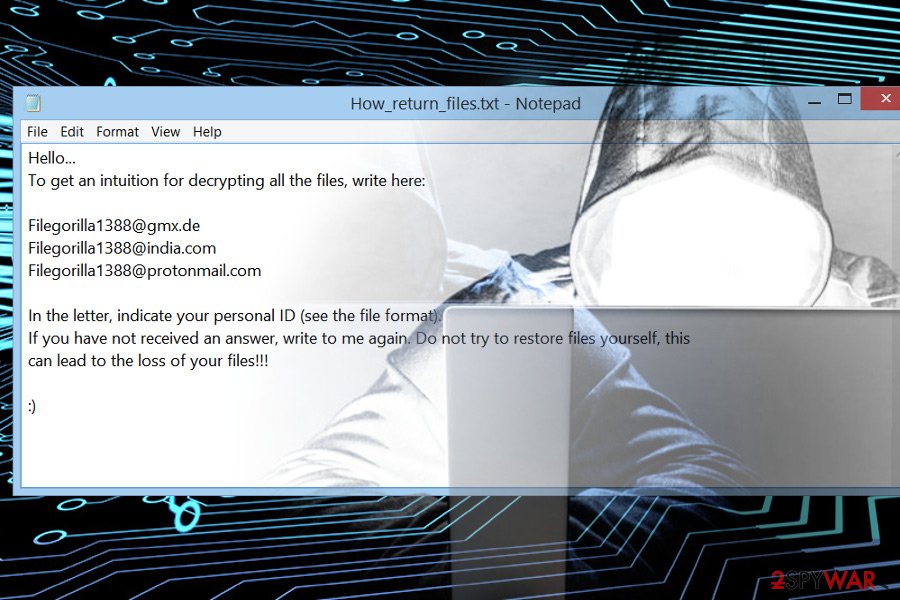
- filegorilla1388@gmx.de
- filegorilla1388@india.com
- filegorilla1388@protonmail.com
- panzergen552@gmx.de
- panzergen552@protonmail.com
- panzergen552@india.com
- vendetta553@gmx.de
- vendetta553@india.com
- vendetta553@protonmail.com
- robocript@gmx .us
- robocript@india.com
- robocript@protonmail.ch
- alexjer554@gmx.com
- alexjer554@india.com
- ursa2277@gmx.com
- ursa2277@yahoo.com
- ursa2277@india.com
- ursa2277@bk.ru
- ziz777@gmx.com
- ziz777@india.com
- some@mail.ru
- vine77725@gmx.de
- vine77725@india.com
- vine77725@protonmail.com
- jonskuper578@india.com
- jonskuper578@gmx.de
- jonskuper578@protonmail.com
- fox2278@india.com
- fox2278@protonmail.com
- fox2278@gmx.de
- lion7872@protonmail.com
- lion7872@gmx.de
- lion7872@india.com
- Tizer78224@gmx.de
- Tizer78224@india.com
- Tizer77234@protonmail.com
Hackers behind RSAUtil ransomware are undoubtedly trying to convince users into paying the ransom for their files, but our expert team recommends victims to eliminate this ransomware infection from the computer instead. This way, you will not support the wrongdoers and protect yourself from being robbed of your money. Keep in mind that RSAUtil removal should be your priority. After that, you can use our recovery instructions to recover your encrypted files.
If you have not been hit by RSAUtil yet, we highly recommend you reevaluate the security of your device and make backup copies of your files.
Having backups [7], you will calmly bypass any ransom demands and recover your files without spending a penny. Please keep in mind, though, that the storage drives on which you keep your backups must be unplugged from the device, otherwise, the virus may affect them too. So, before you try to recover your data, take care of RSAUtil removal first.
If your PC was compromised, we recommend scanning your device with antivirus software like FortectIntego to clean up every last bit of ransomware from your computer. Then, you may try to recover your files following professional software we introduce below the article.
RSAUtil versions listed
As we already mentioned, there multiple versions of the virus and it keeps coming back with periodically. Unfortunately none of the variants are decryptable yet, adn the only way to get files back is from a backup or by paying the ransom (we highly discourage users from paying crooks!). Nevertheless, you will fine a complete list of RSAUtil versions below.
- some@mail.ru. Appeared in mid May 2017 and appended . [Ransom_email] .ID [victim_ID] file extension;
- ziz777@gmx.com. First spotted late May 2017; appended [Ziz777@india.com] .ID [random_digits8] file extension;
- ursa2277@gmx.com. Spotted August 2017; added URSA.ID[victim_ID] extension;
- alexjer554@gmx.com. Was found in early October 2017; appended [alexjer554@gmx.com] .ID [victim_ID] file extension;
- batary5588@gmx.com. First appeared late October 2017;
- robocript @gmx.us. Was first spotted in November 2017 and added file extension [robocript@india.com] – ID [victim_ID]
- panzergen552@gmx.de. Found by researchers in early December 2017;
- vendetta553@gmx.de. Was first discovered in mid-December 2017 and added .ID [victim_ID ].VENDETTA extension to each of the files;
- Filegorilla1388@gmx.de. came at the same time as .VENDETTA but added .ID [victim_ID] .GORILLA appendinx instead;
- vine77725@gmx.de. Was first spotted before the new year of 2018. Hackers asked $2000 in BTC to be paid into 166asTTzXjy8xaw1feimY7s1xwozyy8ACi wallet;
- panda7499@gmx.de. First introduced late January 2018;
- jonskuper578@india.com. Security researchers spotted this version mid-February 2018. It encrypted files using .[ID425xxxxx] (example) file extension;
- fox2278@india.com. This variant emerged in early March and used .[ID231xxxxxx] appendinx;
- lion7872@protonmail.com. Discovered early April 2018;
- Tizer78224 gmx.de. The latest version was spotted in early May.
Virus distributed via mail spam and RDP attacks
The main techniques used by this crypto-ransomware are these:
- The described ransomware is known to be distributed via RDP[5] attacks. The hacker gets into remote desktop services illegally and uploads a pack of files on them. The package consists of several files, including a configuration file that is responsible for ransomware execution and clearly, the ransomware itself.
- Another technique used by fraudsters is malspam. Infected email attachments carrying documents supposedly relevant to the user is the bait that unsuspecting users still take very often. Scammers usually show outstanding skills when it comes to crafting fake emails.
Please remember that the emails you may receive from governmental institutions or other trustworthy-looking sources may not always be what you expect them to. In fact, you should be especially careful with them because names of such organizations are very often used as marionettes for executing malicious scams.
It is likely that ransomware may arrive on the computers disguised as attached tax return information, invoices or other documents, so our suggestion is to be careful when downloading them and executing them on your computer.
Eliminate RSAUtil ransomware virus professionally
If you want to perform a successful RSAUtil removal, remember that you will not do it any way better than by employing professional antivirus software and allowing it to go through the entire infected system automatically.
The antivirus tools will remove RSAUtil and all of its undesirable components from your computer, giving you the freedom to enjoy your regular activities instead of spending hours, hunting down malicious files.
Nevertheless, even the automatic ransomware removal may be challenging. For instance, the virus may block your security utility from running the system scan. If this happens, you will have to follow the manual virus decontamination procedure and try running the system scan again.
Getting rid of RSAUtil virus. Follow these steps
Manual removal using Safe Mode
The mentioned antivirus-blocking solution can be solved by following the guidelines below:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove RSAUtil using System Restore
Here is how you can decontaminate RSAUtil and initiate system scan for a definite virus elimination:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of RSAUtil. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove RSAUtil from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by RSAUtil, you can use several methods to restore them:
Method 1: file recovery with DataRecoveryPro
The tutorial below illustrates how to use DataRecoveryPro and restore files encrypted by RSAUtil ransomware
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by RSAUtil ransomware;
- Restore them.
Method 2: restore data with Windows Previous Versions feature
Learn how to use Windows Previous Versions feature in the following guidelines:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Method 3: recover files from system backups with Shadow Explorer
Use Shadow Explorer like shown below:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Method 4: Free RSAUtil decryptor
Unfortunately, free RSAUtil decryptor has not been released yet. Please check back later.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from RSAUtil and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Resources research crypto-ransomware. Zscaler. Revolutionizing cloud security with unparalleled protection and performance. Go beyond basic internet security with our 100% cloud solution.
- ^ Ben Johnson. How ransomware works. CarbonBlack. Arm your endpoits.
- ^ Delphi (programming language). Wikipedia. The free encyclopedia.
- ^ svchosts. VirusTotal. A free service that analyzes suspicious files and URLs .
- ^ Remote desktop protocol (RDP). SearchEnterpriseDesktop. All things desktop management.
- ^ Amigo-A. RSAUtil ransomware. Twitter. Social network.
- ^ How to make a full backup of your Windows 10 PC. Windows Central. Tech site.





















