Ukash virus (Virus Removal Instructions) - May 2017 update
Ukash virus Removal Guide
What is Ukash virus?
Ukash virus blocks access to the computer, asks to pay a “fine” to regain it
Ukash virus is a malicious computer program that belongs to ransomware and Trojan categories. Once installed, such virus restricts access to the PC or encrypts files on the system and then displays a full-screen message urging to pay a ransom[1]. There are many versions of this ransomware, including versions for Mac and Android. The majority of these viruses state that the computer has been locked for violation of federal law. The malicious program creates an image that a particular institution located in victim's country was informed about his/hers illegal activities, such as watching illegal content, distributing malware[2]. To convince victims that these malicious programs are work of law enforcement agencies, these programs display names and logos of legal authorities. Some of these programs are even capable of taking control of victim's webcam and showing live view just to convince the user that his/hers activity is being recorded. The most preeminent and infamous examples of such malware are FBI virus[3], Police virus, “Your computer has been blocked” virus. These deceptive viruses usually provide a list of accusations and try to scare the victim by promising to put him/her behind bars for a long time if one fails to pay the forfeit within given time. The malicious virus asks the victim to collect the required amount of money, visit store and exchange it for a Ukash voucher. The coupon contains a code that needs to be entered into the malicious program. If the victim enters the right code, the computer gets unlocked. The virus is almost identical to MoneyPak ransomware group. However, these viruses do not seem to be active nowadays, because now the majority of ransom-demanding viruses urge to pay the ransom via Bitcoin payment system.
Ukash virus is a typical extortion tool used by cyber criminals and the only difference that distinguishes it from typical ransomware that it pretends to be a legal program rather than clearly asking for ransom. There are two types of such ransomware viruses – those that block access to the computer, and those that encrypt your files[4]. The second type is far more dangerous because once such viruses run encryption algorithms on personal records, they become corrupted and the only way to reverse the process is to use a private key, which is stored at criminals' private servers. In most cases, data recovery is impossible. Luckily, the majority of viruses that fall into the aforementioned malware category just display a screenlocker, which can be disabled easily. Sadly, sometimes victims pay the ransom before looking for information about these programs online, or even if they have never done anything illegal. It is apparent that the developers of these virtual extortion tools use social engineering[5] to convey the sense of urgency, scare the victim and force one to pay the ransom. If you fell victim to a similar virus, we suggest you remove Ukash from the system using a strong and trustworthy anti-malware software like FortectIntego. Before you start the removal process, make sure you read instructions provided by our expert team. 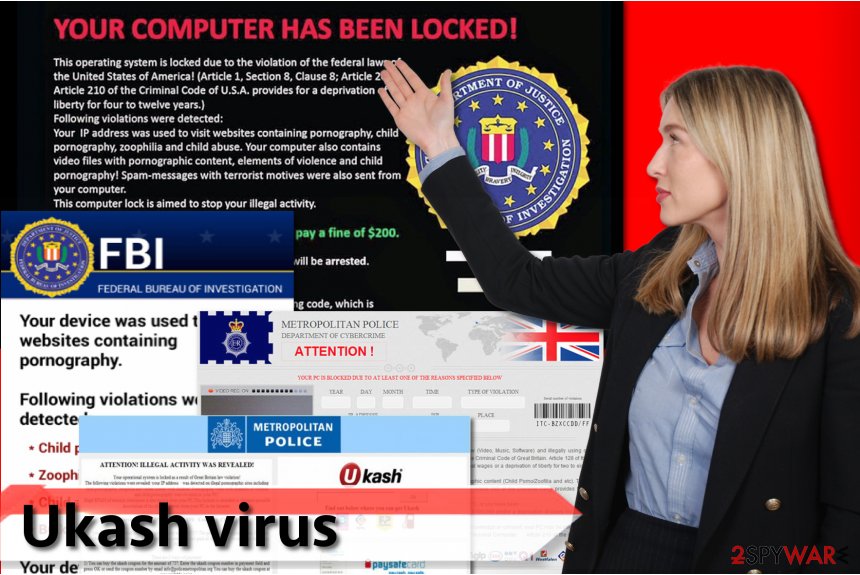
The most infamous versions of Ukash malware
FBI virus. FBI ransomware is a malicious Trojan that has been infecting computer users since 2012. It is one of the oldest ransom-demanding viruses that are still active in 2017. The virus blocks access to the computer by launching a full-screen message with Federal Bureau of Investigation – Department of Justice logo on it. The alert demands a ransom paid in the form of either MoneyPak or Ukash voucher. The dangerous Trojan requests $100-$200, although it can be removed just by ending the malicious process and deleting the malicious program. Versions of this virus are actively attacking Android users as well.
Metropolitan Police Ukash virus. The virus was first spotted back in 2012, around the same time as FBI virus showed up. The virus displays victim's IP address, and states that “the process of illegal activity is detected.” The virus accuses the victim of sending spam containing terroristic materials and also visiting websites that provide illegal content. The virus asks to buy a prepaid card worth £100 and enter its code into the ransomware's program window. Since this virus works as screenlocker that doesn't encrypt files, the victim only needs to delete the virus to start using the PC again. Considering that it is a profoundly malevolent program, experts advise removing it with a professional anti-malware product.
Royal Canadian Mounted Police Ukash virus. This virus launches the scary alert message via Safari browser, and it mostly attacks Mac users. The browser tab shows “Your browser has been locked” line, and the website itself says that all activities of the computer are being recorded. The virus typically accuses the victim of violating copyright laws, distributing prohibited pornography contents and ironically, neglectful use of the computer. This ransomware variant asks for $50 although it can be deleted just by closing the Safari window and scanning Mac OS with compatible anti-malware software.
Android ransomware. Smartphones running Android operating system are vulnerable to Android Ukash virus. This virus also asks to pay the ransom using described prepaid cards. The latest variants of this virus are even capable of attacking IoT devices – LG Smart TVs. Versions of this virus typically accuse the victim of watching illegal content and ask to pay a ransom in order to unlock the device. People who fall victim to attacks against mobile devices should perform a factory reset for the device. There is no necessity to pay the ransom because these viruses typically cannot corrupt data on the compromised device.
Be aware of malware distribution methods to keep malicious programs away from your computer
All ransomware that belongs to this malware family are spread with the help of trojans that can come either with infected downloads or through spam emails and their attachments. Of course, the user has no idea about Ukash virus and discovers it only when this virus restricts access to the computer. Besides, the victim is welcomed by a huge message titled 'Attention! Illegal activity was revealed' and said that there are some serious law violations found. Scammers suggest dropping the charges if the victim pays a “fine” within 24 hours or a week. However, you must be aware that no such official organization collects fines paid in prepaid cards. Besides, such organizations NEVER lock computers down and leave users without the Internet connection. We have some tips for computer users that can help to keep ransomware viruses away from the smart devices:
- No matter what kind of programs you have on your computer, keep all of them up-to-date. This way, attackers won’t be able to exploit vulnerabilities in outdated software to execute commands on your PC.
- Install a proper security software. If you want to block ransomware attacks, you need to use a program that can identify malicious attempts to infect your system.
- Do not open suspicious email attachments. If you ever receive an email letter from someone you do not know, firstly lookup for information about the sender online or, if needed, contact the company the sender claims to be working for.
Expert tips on how to remove Ukash viruses
If you lost access to the computer due to ransomware attack, we suggest you use our instructions on how to remove Ukash virus. Keep in mind that we recommend removing the virus using professional malware removal programs. It is hard to uninstall ransomware because such malicious programs never leave an uninstaller. Carefully read all steps provided in Ukash removal guide below and follow them to rescue your PC from ransomware. In case you were infected with the virus that targets Mac operating system, simply run a scan with security software that is compatible with Macs, for example, Malwarebytes or SpyHunter 5Combo Cleaner. Victims who use Android operating system should follow instructions provided here.
Getting rid of Ukash virus. Follow these steps
Manual removal using Safe Mode
Instructions provided in the guide presented below will help you to regain access to your computer system and remove Ukash virus right away. The guide that contains screenshots explains how to reboot your PC in Safe Mode so that you could start the malware removal software properly. If the Method 1 and Method 2 won't help you to kill the virtual infection, you might want to try these additional steps:
1. Restart your computer to 'Safe Mode with Networking' with the help of F8 button;
2. Launch MSConfig and disable all startup entries rundll32 turning on any application from Application Data;
3. Restart the system once again
4. Scan your computer with FortectIntego or other anti-spyware program to remove infected files from the system.
UPDATE: You can also try the following methods to remove Ukash virus from your computer:
- Users infected with Ukash group of viruses are allowed to access other accounts on their Windows systems. If one of such accounts has administrator rights, you should be capable of launching anti-malware program.
- Try to deny the Flash to make your ransomware stop function as intended. In order to disable the Flash, go to Macromedia support and select 'Deny'. After doing that, run a full system scan with anti-malware program.
Manual Ukash virus removal (special skills needed!):
- Reboot you infected PC to 'Safe mode with command prompt' to disable FBI virus (this should be working with all versions of this threat)
- Run Regedit
- Search for WinLogon Entries and write down all the files that are not explorer.exe or blank. Replace them with explorer.exe.
- Search the registry for these files you have written down and delete the registry keys referencing the files.
- Reboot and run a full system scan with updated FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes to remove remaining files.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Ukash using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Ukash. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Ukash from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Ukash, you can use several methods to restore them:
Run Data Recovery Pro tool
If the ransomware managed to encrypt your files, run a system scan with Data Recovery Pro, which is a great data recovery software.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Ukash ransomware;
- Restore them.
Look for Previous File Versions
Have you ever created System Restore point? If you did, follow these instructions to restore individual files that were recently corrupted by the virus.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try to find Volume Shadow Copies
Volume Shadow Copies are very useful copies of your data, which can help to restore them in case original copies get corrupted. Sadly, the majority of ransomware viruses delete them. To check whether the malware eliminated this backup or not, run ShadowExplorer.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Ukash and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Chester Wisniewski. Location-based threats: How cybercriminals target you based on where you live. Sophos News. Security Made Simple.
- ^ Kevin Savage, Peter Coogan, Hon Lau. The evolution of ransomware. Symantec Security Response. Unparalleled Analysis of IT Security Threats.
- ^ New Internet Scam. FBI Stories. Breaking News, Podcasts, Videos, Local, State, National, and International News and Stories.
- ^ Ransomware Facts. Microsoft Malware Protection Center.
- ^ What is Social Engineering?. Webroot Resources. Computer Virus Information.





















