FessLeak ransomware
FessLeak virus Removal Guide
What is FessLeak ransomware?
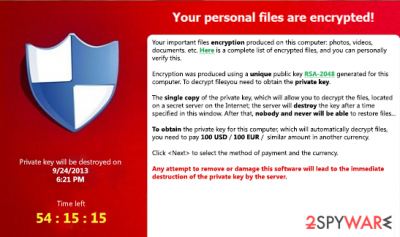
What is FessLeak?
FessLeak is a dangerous campaign that is used for spreading Cryptolocker, Cryptowall, CTB Locker and other cyber threats that belong to ransomware category. This means the only thing – if you want to avoid these threats, you should stay away from malicious websites that were registered on FessLeak@qip(dot)ru. Othgerwise, you can end up with the virus that seeks to encrypt important victims' files and then make them pay a required fee for their decryption. In most of the cases, this payment should be paid in bitcoins via Tor web browser and that's they only way that helps in this situation.. If a ransomware that belongs to FessLeak malvertising campaign infiltrates the system, the first thing that it does is system's scan. After scanning the system and finding predetermined files, it encrypts them using the RSA 2048 encryption. After that, each of affected files becomes locked. After trying to open any of these files, user sees a huge warning message, which informs him/her about the whole situation. Please, do NOT pay this ransom because you can never be sure that this will help you to get an decryption key. If you have been performing backups and now you have just discovered that your computer is infected with one of FessLeak malwares, then you should try to restore your files from there. Of course, you should also make sure that all malicious files (including the ones that belong to this ransomware) are eliminated before doing so. The easiest way to do that is to run a full system scan with updated anti-sptyware. For that we highly recommend using FortectIntego. If you have no idea what backup means, then you should try programs that are given at the end of this post.
How can FessLeak infect my computer?
There are several methods that are used for spreading ransomwares, including FessLeak campaign. It relies on malicious websites that are promoted thru fake alerts. Such alerts are usually filled with various logos, so they look quite convincing. If you, while browsing on the web, were interrupted by alert that claims that you need to update your Java or Flash Player, you must realize that it might be fake. Please, ignore such ads and never fall for them because you can be redirected to malicious website that can easily download Cryptolocker or other ransomware onto your computer. In addition, remember that you can also be tricked into downloading this threat to your computer via spam. According to the latest reports, spammers have been actively working in France and other Europe's countries, but there is no guarantee that there is no group of hackers who are trying to increase the distribution rate of these ransomwares in USA and other world's countries. In this case, the most important thing is to understand that there are lots of malicious emails spreading around. In most of occasions they look like official notifications about various purchases, fines, prizes and other things that have always been attracting people. If you have just discovered that FessLeak-related ransomware has already attacked your computer and blocked your important files, please follow this guide and get rid of this threat.
How to remove FessLeak virus?
If ransomware, using FessLeak campaign, has just affected your system, you will need a key if you want to decrypt your corrupted files. For that you need to pay a ransom. Nevertheless, you can also try a backup or using file recovery tools. If you have been performing backups, you should be capable of restoring your files. In addition, for that you can also try such programs as R-Studio or Photorec.
For FessLeak removal, we highly recommend using FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
Finally, we must add that we highly recommend thinking about the prevention of such infections like FessLeak-related ransomware, Cryptowall, Cryptolocker, CTB Locker and similar threats. For that you can use previously mentioned programs. Besides, don't forget to think about the immunity of your files and make backups as frequently as possible. In addition, you can use USB external hard drives, CDs, DVDs, or simply rely on Google Drive, Dropbox, Flickr and other solutions.
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
