NoobCrypt ransomware / virus (Removal Guide) - Jul 2017 update
NoobCrypt virus Removal Guide
What is NoobCrypt ransomware virus?
NoobCrypt revival brings out new virus versions
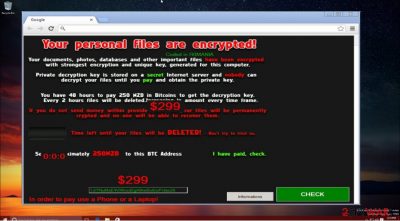
NoobCrypt virus is one of those ransomware [1] viruses which seem destructive at first but turn out to be not as malicious under further investigation. The initial virus version appeared in September, but it was quickly taken down by the virus researchers.
Unfortunately, that did not stop the criminals. After a brief period of silence, the virus came back with a new force. The latest malware version has changed its ransom note design and demand 100 dollar-ransom to be sent to their account in Bitcoin crypto-currency. The virus encrypts files with RSA-2048 and AES-128 ciphers and threaten that if the ransom is not paid in time, the hackers will corrupt user's personal files beyond recovery.
However, while the new ransomware variant is causing most of the upsurge at the moment, its previous version has not gone obsolete either. It is demanding 299 USD in return for the locked data.
Regarding its ransom message, one might suspect that this virus is the misdeed of amateur hackers. However, the original version still has managed to encode personal information with the help of a complex mathematically interrelated set of codes, specifically AES algorithm.
If we believe the content of the message, the virus was generated in Romania [2]. Thus, the residents of the latter country should be extremely cautious. On the other hand, it does not mean that if you live in the country far from this European state, you can escape this threat. That is why it is important to arm up with the knowledge about effective NoobCrypt removal.

Reviewing this ransomware, it does not present any extraordinary nor unusual features. As usual, hackers attempt to persuade you into remitting the payment for the locked personal files. Certainly, without the private key, decoding your files is not an easy task to do.
Thus, the cyber criminals employ psychological pressure [3] to urge you with the payment. They threaten to delete some files every two hours. The standard amount of the ransom equals 299 dollars. The victims of NoobCrypt ransomware are expected to purchase Bitcoins and then enter the unique verification code in the provided bar in the ransom message.
At first glance, the virus is ordinary file-encrypting malware. Users who are befallen by this menace might panic while searching for a way to retrieve the files.
However, IT experts have discovered that there are several significant flaws in the source code of the malware. It creates only one registry entry — HKEY_CURRENT_USER\k1j3jk153kj153. Thus, it is unlikely to re-launch itself after the reboot of the operating system.
The ransomware behaves more like a lock-screen virus. Luckily, there is no need to pay the money, because malware specialist, Jakub Knoustek, discovered a key. Enter ZdZ8EcvP95ki6NWR2 code into the bar which requires the verification code. After that, you will be able to decrypt the files for free. After that, remove NoobCrypt right away. FortectIntego is one of the security programs which quickly and effectively deal with the ransomware.
September 2016 update: NoobCrypt uses the same decryption password for all of its victims
Just recently Noob Crypt virus researchers have made a breakthrough with this ransomware by disclosing another huge flaw in the program's source code.
Iakub Knoustek, who initially came up with NoobCrypt decryption key, continued to inspect the virus even further and found that this key is only suitable for some computers, while the others remain undecryptable. The main problem is that there are several versions of the NoobCrypt malware and each of the version feature a different decryption code.
Luckily, the same code unlocks all computers infected with the same version of the virus. So, to decrypt your data, you only need to find out what particular version of the virus has infected your PC.
To do that, pay attention to the ransom note details such as the amount of ransom and the Bitcoin wallet address. For instance, the code “ZdZ8EcvP95ki6NWR2” only works for the virus versions demanding the highest ransom — 299 USD.
The virus version demanding 100 dollars for the data decryption can be decontaminated with a code “RedStarPenis”, while the ones asking for 50 USD can be unlocked using lsakhBVLIKAHg. Good luck decrypting your data! Just do not forget to eliminate the virus from your computer when you do!
Experts detect improved virus versions
After the IT professionals have shattered the hackers' ambitions mercifully, it seems that there is going to be one virus less in the virtual world. Nonetheless, the authors have proved not be so “noob” and decided to counterattack the IT specialists.
Consequently, an improved version of the ransomware was detected. The renewed edition contains several improvements, such as C+ evaluation copy.
However, to big disappointment of the crooks and the joy of the virtual community, the improvements made the virus worse. In other words, the hackers included obfuscating elements, but in the end they resulted in the version of the virus which does not require any decryption key!
However, such improvements reveal that crooks, whether they are member of organized cyber rime gang or just hacker-wannabes, still create significant problems for the users. Though rarely the virus updates mess up the virus itself, such
Principles of system infiltration
Since the hackers behind NoobCrypt seem to be amateur hackers yet, it is likely that the malware is distributed via P2P file sharing websites or other questionable advertising, gaming, or pornographic domains. Such domains often contain various hyperlinks.
After a user clicks on such link, he unintentionally downloads the file with the ransomware. Alternatively, it is a matter of time when cyber criminals decide to shift to another, a more profitable method of distributing the malware.
It is a common tendency to transmit file-encrypting viruses via spam emails. In the case of some previous ransomware, cyber criminals have manifested real mastery by creating fake letters which can be easily mistaken for the official emails received by governmental institutions.
Thus, if you receive an invitation to fill the form for a tax refund or customs declaration, do not open any attachments. They might contain NoobCrypt hijack within. In order to block any malware, which might disguise the virus, and decrease the number of spam emails, install an anti-spyware application.
NoobCrypt removal and recovery
Since this virus is not a mere PUP, we highly advise you to opt for the automatic elimination. The security application, FortectIntego or Malwarebytes, will remove NoobCrypt virus properly.
If you update the application regularly, it will safeguard your PC from all kinds of threats. However, you might encounter some problems related to NoobCrypt removal because the virus locks your screen and you cannot operate your device properly.
If after entering the above-provided code, the computer still remains unusable, use the recovery instructions below. After the threat is completely eliminated, you should focus on developing several plans in case ransomware targets your system again:
- Update security applications daily
- Store your private information in several locations
- Employ portable data keeping devices, such as USB sticks or DVDs to secure your data copies
Getting rid of NoobCrypt virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove NoobCrypt using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of NoobCrypt. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove NoobCrypt from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by NoobCrypt, you can use several methods to restore them:
Data Recovery Pro – the aid for the encrypted files
In case you happened to get infected with a modified NoobCrypt version and some of your files are still locked, run the application to regain access to the affected data.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by NoobCrypt ransomware;
- Restore them.
ShadowExplorer – another alternative
Upon encountering a more damaging ransomware virus, this utility may prove to be effective in restoring the files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from NoobCrypt and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Ransomware FAQ. Microsoft. Antimalware and cybersecurity portal.
- ^ Faravirus. Faravirus. Malware news, reviews and removal tutorials.
- ^ Social engineering (security). Wikipedia. The free encyclopedia.





















