Shade ransomware (Virus Removal Guide) - Decryption Steps Included
Shade virus Removal Guide
What is Shade ransomware?
Shade ransomware service shut down: 750,000 unique decryption keys revealed on GitHub
Shade ransomware, often dubbed as Troldesh, is a file-encrypting virus that keeps infecting regular PC users, companies, and businesses via spam email campaigns since 2014. At the time being, there are more than 15 diverse versions, which uses diverse file extensions, such as .7h9r, .xtbl, .ytbl and .da_vinci_code, no_more_ransom, .better_call_saul, .heisenberg, or .windows10, but share similar encryption methods, distribution strategies, and demands[1].
Various researches revealed that Shade ransomware proliferates in Russia and Russian speaking countries. If a potential victim opens an infected email attachment, he or she grants ransomware permission to enter the system and lock files using AES-256 encryption algorithm. Aside from data locking, Shade Troldesh ransomware drops cryptocurrency miners on the system and actively participates in aggressive advertising – traffic boosting services.
Update 2020: At the end of April 2020 cybersecurity researchers reported that Shade ransomware service has been shut down by its developers. Criminals revealed more than 750,000 unique decryption keys that have been collected within more than five years. The entry contains an apology of the criminals and full guidance on how to decrypt files encrypted by Shade ransomware.
Although decryption keys are now open to everyone, the process requires IT knowledge and may be difficult to perform. Therefore, we highly recommend waiting until reputable security vendors release an official Shade decryption software. Although there is a decryption tool developed by Europol, the Dutch National High Tech Crime Unit, Intel, and Kaspersky available at NoMoreRansom website, it cannot retrieve files encrypted by the latest Shade ransomware variants.
| Name | Shade ransomware |
|---|---|
| Type | Cryptovirus |
| Ransom note | README1.txt or README10.txt |
| File extensions |
|
| Encryption method | This ransomware strain uses a unique AES-256 encryption cipher to lock up files and documents that are founded on the infected computer system |
| Active since | The first activity by Shade ransomware has been spotted in 2014 and developers have made it more advance and complex since then |
| Distribution | Spam email campaigns are the most popular method used for Shade ransomware distribution. Nevertheless, this malware ranks as the top 1 virus that is distributed via questionable email messages |
| Elimination | Use trustworthy antivirus to remove Shade virus. Note that manual elimination is not a possibility for this case as the ransomware is too hard to eliminate on your own |
| Repair | If the malware has left some system files damaged on your computer, you can give FortectIntego software a try as this tool might help you to recover some harmed objects |
| Decryption software | If this ransomware virus has affected your data files, you can recover them without paying the ransom. For this purpose, download the decryption tool directly from here, or look it up on this web page |
| ACTIVITY | Shade ransomware service has been shut down at the end of 2019. Upon closure, developers of the virus revealed over 750,000 unique decryption keys that are available at GitHub[2] |
This threat exclusively focuses on infecting the European region, specifically, the UK, France, Germany, Italy, Ukraine, and Russia. Nevertheless, Russia tops as the region experiencing the biggest losses due to Shade ransomware attacks. According to the latest information, the virus started a Russian-oriented spam email campaign, which took the start in October 2018. ESET team reported[3] that activity stopped during the Holidays, but has renewed between January 1st and 24th. Research has disclosed that 52% of malicious email attachments created by the Shade team went to Russian addressees. The campaign focused on phishing emails with subject lines impersonating legitimate organizations like B&N Bank.
Throughout its existence, the ransomware has managed to earn millions of dollars. Cybercriminals are constantly improving their malicious creations, so there is no doubt that Shade ransomware will attempt to invade as many computers as they can.
The virus locks images, video material, documents, music files, and other data it finds on the computer using AES-256[4] encryption method. If this menace has fallen you, find out how to remove Shade virus. FortectIntego might also be a helpful utility of you try using it for repairing some system components that have been damaged by the malware.
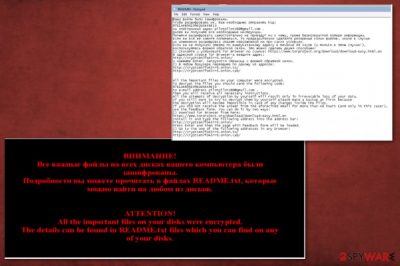
After the ransomware encrypts all the valuable files, it automatically changes the desktop's background and opens up README.txt file which informs you of the encrypted files. The ransom message is provided in two languages – Russian and English. Moreover, the virus also attaches different extensions to each of the encrypted files.
Once it marks target files, it displays this ransom note telling that paying the ransom is crucial to recovering the files:
All the important files on your disks were encrypted.
To decrypt the files you should send the following code:
A4B50EXXC45D44XXX1F9|0
to the e-mail addresses: graceseYoumans1983@gmail.com or drugvokrug727@india.com.
All the attempts of decrypting the information by yourself will result only in irrevocable loss of your data.
Shade uses two methods to deliver the ransom: via email address and Tor server. In the latter case, users are required to access the anonymous browser and then follow the instructions to transfer the money. Even if the data is of vital importance, do not pay the money as it does not guarantee that Shade malware decryption service will help you retrieve your blocked information.
For data recovery, use a free decryption tool that has been already created. You can find its download link at the end of this article besides expert[5] approved tips. All in all, you need to initiate Shade virus removal as soon as possible and then start decrypting your files.
Another interesting fact about Shade ransomware is that it has more than one purpose. Of course, it operates as a typical file-encrypting virus and demands a ransom afterward. However, experts have discovered that this malware is also used to generate and increase online traffic for receiving more income from advertising campaigns. This way the developers of Shade ransomware can collect more revenue than using the malware for file locking only.
2019 Update
The newest information regarding Shade ransomware virus surfaced at the end of January. Attackers used phishing campaigns to spread their malware around, mainly targeting Russians. The previously known crypto-malware renewed attacks and used malicious JavaScript attachments.
ESET reported that the campaign that was discovered back in October 2018 has been removed after the Holidays, during which Shade virus remains still. According to Juraj Janosik, this second attack is more intense and doubled in volume. The activity with infected spam email attachments was discovered and revealed that 52% o those attachments were sent to Russian email addresses and the rest of them targeted mainly Ukraine, France, Germany, Japan.
Subject lines on these emails state about order details, updates, or payment details, and senders impersonate legitimate organizations, for example, Russian B&N Bank or retailer Magnit. Emails even impersonate specific managers or company employees.
Emails contain file attachments like ZIP archives or documents. The particular campaign included malicious JavaScript hidden in a ZIP archive named info.zip or inf.zip. The minute user opens the file ransomware payload is launched on the device. As Janosik reported, a direct downloader immediately launched Shade virus and performs encryption on users' files.
Researcher stated:
Once extracted and launched, the JavaScript file downloads a malicious loader, detected by ESET products as Win32/Injector. The malicious loader decrypts and launches the final payload – the Shade ransomware. Our telemetry data shows hundreds of such URLs, all ending with the string “ssj.jpg”, hosting the malicious loader file.
Troldesh (Shade) ransomware ranks as the top 1 malware being delivered through email spam
Regarding news reports released at the end of 2019, Shade ransomware has become the most popular malware that is distributed via email spam campaigns. Group-IB’s Computer Emergency Response Team (CERT-GIB) has testes numerous spam and questionable email messages that were holding malware and the most common computer parasite in the first half of 2019 was spotted to be Shade (Troldesh) virus.
The other two places in the most popular three go to RTM and Pony Formgrabber malware, however, they still take a small percentage combining to Shade ransomware that holds 57% of popularity via email spam distribution. Nevertheless, cybersecurity researchers have found out that ransomware infections have become more popular when it comes to monetary benefits that are being collected by malicious actors as the top goal.
Shade ransomware itself has been upgraded by multiple more advanced features that allow the crooks to spread the virus more effectively and receive much more income than they were able too since the malware's first release. Even though this malicious infection has been active for a few yours since now and can be even purchased for further distribution on various black markets, victims should not be that afraid of it as there are decryption tools already available for files and documents that get encrypted with Shade ransomware.
At the end of our article, you will find a link to the official decryption software that has been provided by Softpedia specialists. However, the other two decryption tools released by Kaspersky and Intel Security experts have also been posted online. You can find the software on The No More Ransom website while continuing with the “decryption tools” section and searching for your needed object.[6]
Shade ransomware collects users' personal information
Cybercriminals have upgraded Shade virus, and now this malware installs a remote administration tool (RAT) upon its arrival on the victim's computer. First of all, the ransomware checks the computer and scans it to find a particular type of documents, which indicates that the computer is used by accounting departments only in Russian-speaking organizations.
In case it detects these documents, it does not launch the ransomware and installs Teamspy Trojan instead. This Trojan is also known as SpY-aGENT, TVRAT, or TVSPY. Trojan then drops a modified version of TeamViewer, 7ZIP tool, NirCmd utility as well as TeamViewer VPN driver and RDP Wrapper Library on the computer system. With the help of this set of tools, cybercriminals manage to modify the operating system's settings and control the PC system remotely.
Criminals spy on computer users in order to decide how much money to ask from him in exchange for a decryption key; besides, they modify the ransom note for individual victims as soon as they sort out what threats to use against particular computer users. This is a dangerous technique and users must take precautions to protect their computers from Shade attacks!

Malware distribution techniques include safe-looking emails
Ransomware infection may occur after downloading the infected attachment via malicious email messages. They contain a .zip file which includes an infected file, for example, PAYMENT.vbs, PAYCHECK.vbs, PENALTY.vbs. Once it is opened, it automatically releases the malicious payload and downloads ransomware to your computer. Then the virus spreading all over the disks and encrypts your files.
Also, malware may infect your computer via a Trojan, alternatively known as an exploit kit. It is especially detested for its ability to disguise as a legitimate file. In order to detect it, it is of utmost importance to install a reputable anti-spyware program, which will track down the malware.
As the most common ransomware distribution technique is spam email campaigns, malicious actors make spam emails looking more legitimate while impersonating known organizations or even government institutions, banks, popular companies. You should note that this is a common technique and delete suspicious emails more frequently.
Shade virus can be stopped
Europol, the Dutch National High Tech Crime Unit, Intel, and Kaspersky have joined forces to terminate the Shade virus. These companies entered the previously launched project “No More Ransom.” The cooperation presented the long-awaited results for the international community – a decryption tool. You can also find it below in this article. After raiding multiple command and control servers, the cyber allied forces were able to locate the one distributing Shade Trojan.
What is more, they deliver good news for its victims, a free decryption tool now can be found on the Internet. This joint operation has deprived the developers of the ransomware of acquiring an additional 1,45 million USD. The project attracted more participants as the virtual community, particularly businesses and thousands of ordinary users, have been continuously attacked by file-encrypting malware.
The companies also expect Microsoft to join in the near future. Its cooperation would be highly beneficial taking into account that the absolute majority of ransomware viruses are created for Windows OS systems.
Update: For an unknown reason, Shade developers decided to stop the ransomware service and shut it down in 2019. The cyber community received information on such a decision in April 2020 only when criminals created a repository on GitHub with more than 750,000 unique master keys for data decryption and full instructions on how to enable the given keys.
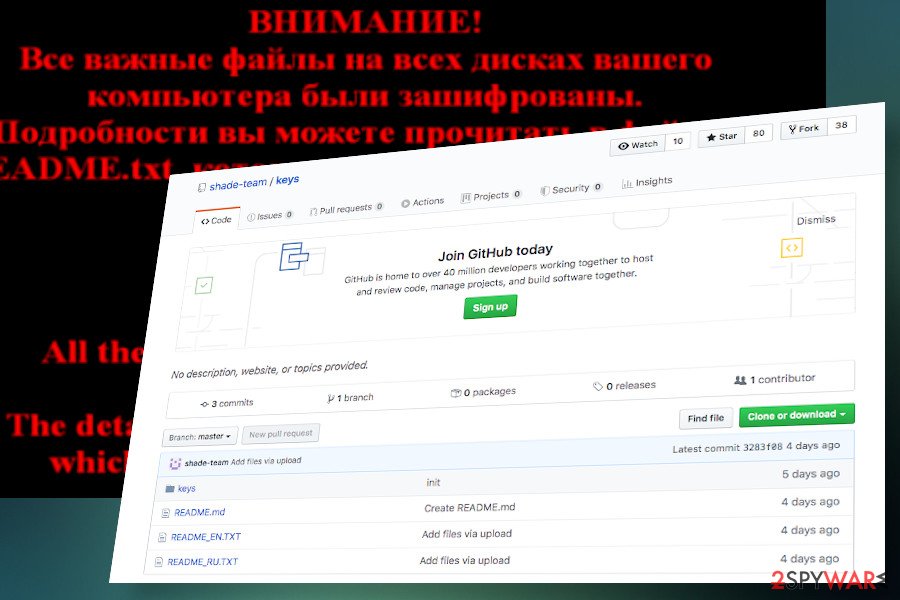
According to the developers, the keys provided will unlock files encrypted with .xtbl, .ytbl, .breaking_bad, .heisenberg, .better_call_saul, .los_pollos, .da_vinci_code, .magic_software_syndicate, .windows10, .windows8, .no_more_ransom, .Tyson, .crypted000007, .crypted000078, .rsa3072, .decrypt_it, .dexter, and .miami_california file extensions.
Although everyone can try to decrypt files encrypted by Shade, the process requires advanced IT skills. Nevertheless, reputable security vendors are already working on Shade decryptor's updates.
Shade virus removal and data recovery requires professional help
If you have just discovered .7h9r, .xtbl, .ytbl, .da_vinci_code or .no_more_ransom extensions added to your important files, it means that your computer is probably infected with Shade virus. As you may have already understood, this is a dangerous virus that was created for the only reason – make its victims pay the ransom.
There is a way to fix everything without supporting the hijackers. First of all, you need to install a reputable anti-spyware program to remove Shade ransomware permanently. After the elimination process, you should either restore your encrypted files from backup or try this program: Shade decryption tool.
Nevertheless, Shade ransomware virus might have made a negative impact on some of your system objects and software. If you have found some damaged components, you can try fixing them with repair software such as FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes.
If you want to prevent such loss in the future, make sure to back up your files or store the important data in different locations, i.e., data storage domains. Storing files online, e.g., Google Drive or OneDrive, might not be secure because they are linked to the PC. The information kept online is always exposed to a greater risk than domestic data storing devices.
If the virus is shutting down security programs and prevents Shade ransomware removal, take a look at the instructions below to recover the access and continue with the virus extermination.
Getting rid of Shade virus. Follow these steps
Manual removal using Safe Mode
Try entering the Safe Mode with Networking before scanning the system with anti-malware:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Shade using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Shade. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Shade from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Luckily, virus experts have come up with data recovery solution — a tool capable of bypassing Shade ransomware encryption and allowing the users to access their files again. We will put a link to this tool below. Nevertheless, you might be infected with a virus version that is resistant to this decryption technique. In such a case, we recommend using one of the alternative data recovery techniques below.
If your files are encrypted by Shade, you can use several methods to restore them:
Opting for Data Recovery Pro
This utility is one of the tools users may shift their attention after getting attacked by the ransomware. It may succeed in recovering your valuable files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Shade ransomware;
- Restore them.
How does Windows Previous Version feature work?
If the System Recovery function is enabled before the virus attack, it saves the copies of the files every time you make new changes to them. This means that you can recover the previously automatically saved copies of your files to the a chosen version of them. To do it properly, follow the guidelines presented here:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
The benefits of ShadowExplorer
This tool is effective as long as the virus does not delete the Volume Shadow Copies of your files. You can give this method a try by following the steps below.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decrypter for Shade ransomware
Here, you can download the free decryption tool which will unlock your files and you will not have to pay the ransom.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Shade and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Tarcisio Marinho. Ransomware encryption techniques. Medium. Where words matter.
- ^ Shade-team / keys. GitHub. Software development platform.
- ^ Juraj Jánošík. Russia hit by new wave of ransomware spam. Welivesecurity. Security researchers' blog.
- ^ Advanced Encryption Standard. Wikipedia. The free encyclopedia.
- ^ Virusai. Virsuai. Spyware related news.
- ^ No More Ransom. Decryption Tools. No More Ransom. Relevant tools and software.





















