Best-Secure browser hijacker (fake) - Chrome, Firefox, IE, Edge
Best-Secure browser hijacker Removal Guide
What is Best-Secure browser hijacker?
Best-Secure is a useless extension that redirects search queries
Best-Secure is a browser hijacker that messes up users' browser settings. It changes the homepage, new tab address to best-secure.xyz, and implements a different search engine. It can affect Google Chrome, Firefox, Internet Explorer, Edge, and other browsers that have the ability to use add-ons.
People use browser extensions because they add some type of value, like block ads and suspicious websites, change the geolocation, or automatically add coupon codes for the biggest discounts when shopping online. This one is different; usually, it takes over the browser suddenly and unexpectedly and does not provide any benefits.
That is not the only reason why people should not want to have this app. The individuals behind this created it to monetize users' browsing activity. They do this by collecting data about the sites you visit, links you click on, purchases you make, and so on, which raises many privacy concerns.
| NAME | Best-Secure |
| TYPE | Browser hijacker; potentially unwanted program |
| SYMPTOMS | Changed homepage, new tab address, redirects to a different search engine |
| DISTRIBUTION | Questionable sites, deceptive ads, freeware installations |
| DANGERS | Data gathering about users' browsing activity |
| ELIMINATION | You can remove an unwanted extension via browser settings or by scanning your system with anti-malware tools |
| FURTHER STEPS | Use FortectIntego repair tool to fix any remaining damage left after removal |
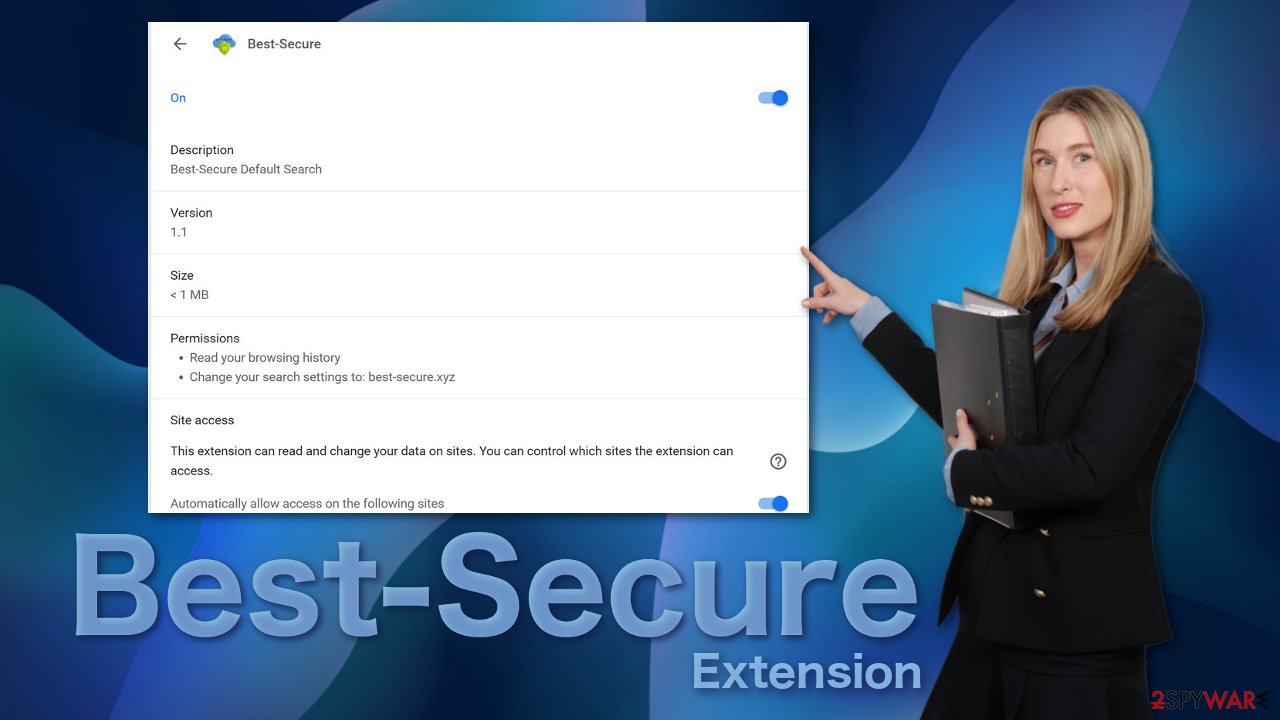
People almost never add hijackers on their own accord because under the permissions section, they would see that it can:
- Read your browsing history
- Change your search settings to best-secure.xyz
But that is not all. Best-Secure also shows search results from Bing.com every time you type something in the search box. Although Bing is a well-known engine, and there is nothing shady about it, it still causes inconveniences for users because it displays different results. Hijackers rarely have their own unique search engine; they use existing ones to make them functional and serve their purpose.
Ways you could have got the hijacker
Most of the time, users get in this kind of trouble because of their own carelessness or not having basic knowledge about security threats. People think that the internet is a safe place and viruses are a thing of the past, and that is true for the most part if you just use it for social media or YouTube videos.
But there are many ways to encounter uninvited guests in your digital bubble. If you visit questionable sites a lot, like illegal streaming platforms[1] to watch movies and TV shows for free, they are filled with deceptive ads[2] and sneaky redirects. That is because usually, they are not regulated. On some of those pages, when you want to start the movie, you have to click the play button about 5 times until it stops opening ads in a new tab.
Another possibility is that you have a PUP installed in your system that has hijacking capabilities. If you recently downloaded freeware from unofficial sources, there is a good chance that it was bundled with additional software you did not know about. Software bundling[3] is very commonly used by sites that provide free versions of programs because they still need to monetize their activities somehow.
Because they offer free programs, they include additional ones in the installer that perform various unwanted tasks in the background. They usually sneak in unnoticed because people ignore the installation process and just trust the sources.
Take back control of your browser
Remove the extension affecting your experience
You can remove Best-Secure manually the same way as any other browser extension via settings:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Internet Explorer:
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
![Remove add-ons from Internet Explorer Remove add-ons from Internet Explorer]()
Because the add-on is known to gather various information about user's browsing activity, it is a good idea to take care of your browsers after elimination. You can let FortectIntego do the job for you automatically. This repair tool can fix any remaining damage and delete cookies and cache so websites you visited cannot track you anymore.
Additional removal option
If you installed a program via bundled software, the previous removal method might not have worked for you. For this one, we recommend deploying SpyHunter 5Combo Cleaner or Malwarebytes anti-malware tools to scan your machine for you because it can be difficult to identify which particular app is responsible. It can have any name and icon, so if you do not have experience, we strongly suggest letting security software take care of it. What is more, it can prevent such infections in the future by warning you about suspicious programs.
If you still prefer the manual removal method, we have instructions for Windows and Mac machines:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.
![Uninstall from Windows 7/XP Uninstall from Windows 7/XP]()
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
PUP prevention tips
To avoid this happening in the future, we recommended using only official and trusted sources for software installations. But you should still implement these habits in your routine:
- Always choose the “Custom” or “Advanced” installation method
- Go through all the steps and do not rush
- Read the Terms of Use and Privacy Policy
- Check the list of programs up for the installation and untick the boxes next to ones you do not need
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Brittni Devlin. Why Should You Avoid Illegal Streaming Sites?. MakeUseOf. Home Security.
- ^ Wikipedia:Deceptive advertising. Wikipedia. The Free Encyclopedia.
- ^ Will Dormann. Bundled Software and Attack Surface. Insights. Software Engineering Institute.