Close your Tab adware (virus) - Free Guide
Close your Tab adware Removal Guide
What is Close your Tab adware?
Close your Tab is a bogus extension used by crooks to spam users with ads
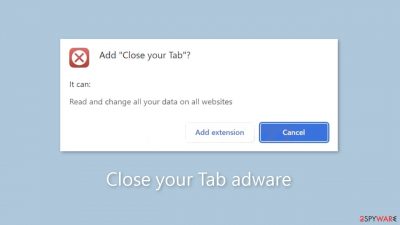
Close Your Tab is a deceptive browser extension that provides no benefits. Instead, it functions as adware,[1] bombarding users with commercial content such as intrusive pop-ups, banners, and redirects. Regrettably, unscrupulous individuals may take advantage of rogue advertising networks that display advertisements that lead to dangerous websites.
As a result, unsuspecting people may be directed to scam sites designed to trick them into disclosing personal information, downloading potentially unwanted programs (PUPs),[2] or even downloading malware. It is strongly advised to remove this application as soon as possible because it fails to deliver on its promised functionalities.
Furthermore, this app may display pop-ups promoting adult websites, bogus antivirus software, software deals, surveys, and giveaways. This could result in financial losses, identity theft, or damage to the operating system. Furthermore, if others, particularly children, use the affected device, they may be exposed to inappropriate content.
| NAME | Close your Tab |
| TYPE | Adware |
| SYMPTOMS | Annoying pop-ups and other types of advertisements start appearing on the screen |
| DISTRIBUTION | Shady websites, deceptive ads, freeware installations |
| DANGERS | Links embedded in the ads might lead to dangerous websites |
| ELIMINATION | Eliminate the extension through your browser settings; scanning the machine with anti-malware tools is recommended |
| FURTHER STEPS | Use FortectIntego to get rid of any remaining damage and to optimize the machine |
Distribution methods
applications like Close your Tab frequently have deceptive “official” promotional websites that boast about non-existent features. Users typically come across these sites while browsing unregulated and dubious web pages. Illegal streaming sites, for example, are notorious for hosting deceptive advertisements and clever redirects.
It is critical to avoid visiting unfamiliar websites and to avoid clicking on random links and advertisements, even if they appear to promote legitimate products or services. It is always best to go directly to the official source. It is also strongly advised to download applications from official app stores or developer websites.
Applications that are listed on reputable digital marketplaces go through a rigorous review process. However, a few rogue apps do manage to slip through the cracks every now and then. To reduce risks, we recommend conducting extensive research prior to clicking the “Download” button. Read reviews, evaluate ratings, and consider the number of users.
Choose applications with a high number of positive reviews and a large user base. Furthermore, read the application descriptions carefully, as fraudsters frequently make grammar or spelling errors that can serve as red flags.
Freeware installations
Another scenario to consider is the unintentional installation of Close Your Tab adware on your computer. This situation may arise if you frequently use freeware distribution platforms that include supplementary programs in their installers, often without clear disclosure.
As previously stated, when installing software, it is best to stick to official sources. Furthermore, always use the “Custom” or “Advanced” installation methods, read the Privacy Policy and Terms of Use carefully, and, most importantly, review the list of files. To prevent the installation of unrelated applications, uncheck any boxes next to them.
Remove Close your Tab adware
Close your Tab adware can be removed by going to the browser settings and looking at the extension list. We recommend removing plugins one by one to see if you notice any changes.
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Adwarehttps://www.malwarebytes.com/adware. Malwarebytes. Cybersecurity Basics.
- ^ Potentially unwanted program. Wikipedia, the free encyclopedia.
- ^ Dusan Vasic. What Are Cookies? The Good and the Bad of Browser Cookies. Dataprot. Security Solutions.










