JourneyDrive Mac virus (Free Guide)
JourneyDrive Mac virus Removal Guide
What is JourneyDrive Mac virus?
JourneyDrive is a malicious Mac application that may compromise your online security
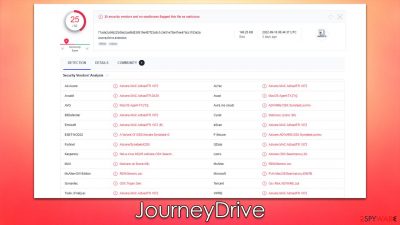
JourneyDrive is a malicious software example that has been increasingly appearing and spreading around on different Mac operating systems. It belongs to a malware family called Adload, which has hundreds of versions released prior to this one. Unlike other malware, it does not spread automatically, as users are tricked into installing it because of the various phishing techniques used by its developers.
It downloads and installs a browser extension on Safari, Chrome, Firefox, or another web browser to assist the JourneyDrive virus in carrying out its malicious activities: it adjusts the home page, new tab, search provider, and other settings (however, this may vary from version to version). This aids the malware in pushing sponsored links and advertisements. It also collects personal information such as credit card and banking details via elevated permissions.
Since malware can make significant changes to your system and add its own components, it is important to remove it as soon as possible. JourneyDrive is a threat to your personal safety and computer security, so we recommend that you uninstall it immediately – we provide all the details on how to do just that.
| Name | JourneyDrive |
| Type | Mac virus, adware, browser hijacker |
| Malware family | Adload |
| Distribution | Software bundles of illegal apps, peer-to-peer networks, fake Flash Player updates |
| Symptoms | A new extension is installed on the browser, along with an application of the same name; search and browsing settings altered to an alternative search provider; new profiles and login items set up on the account; intrusive ads and redirects |
| Removal | You can remove Mac malware with the help of powerful security tools, such as SpyHunter 5Combo Cleaner. If you want to attempt to get rid of the infection yourself, check the manual instructions below |
| Security tips | Potentially unwanted applications often leave traces within web browsers – cookies, for example, are used for tracking. You should get rid of these leftovers with FortectIntego or employ our manual guide |
How does the virus spread?
Many users are startled to find JourneyDrive on their devices because they can't recall ever installing it. However, this is fairly common because the virus spreads via deceptive means such as software bundles from high-risk websites and fake messages or malicious ads.
To begin with, we recommend that you avoid websites that provide pirated software since they are very insecure. The security procedures are ineffective, and some of these sites are deliberately created by criminals to spread malware. This implies seemingly free application installers may be disguised as malware.
Users must provide their Apple ID when downloading such software, allowing the infection to be installed without difficulty. Thus, we recommend avoiding giving authorization to programs downloaded from untrustworthy sources.
Another method to become infected with the virus is by downloading it as a fake Flash Player update.[1] In fact, they are the most common way of getting your Mac infected, and Adload variants are no exception. These deceptive indications may be found on numerous malicious websites, which visitors unintentionally while browsing the web. Using an effective ad-blocker can make a significant difference in these circumstances, although avoiding visits to high-risk webpages dramatically decreases the risk of infection.
Removal of JourneyDrive virus
Here is a complete list of everything you'll need to clean your system effectively. Adload is one of the more tenacious malware for Macs, so we strongly advise against using the manual method alone. The combination of both is recommended instead.
When the malware infiltrates a system, it employs AppleScript[2] to give itself high permissions, making it undetectable to Mac security features like XProtect.[3] Additionally, the malware will drop dozens of items onto the system, which enhances its capabilities and prevents users from removing it easily.
This might make the removal process much more difficult, therefore we strongly advise that regular users utilize automatic remover tools like SpyHunter 5Combo Cleaner or Malwarebytes. You may use the software to prevent Mac security tools from being affected by malware's evasion techniques and ensure that no future infections occur.
Manual elimination is also possible – we explain how to perform it below. However, keep in mind that it may not be effective, and the virus may return. Note that if you are using security software for removal, you should still remove cookies and other web data from your browsers manually.
Remove main components of the malicious app
To begin the removal of a malicious application, you must first close any and all processes running in the background that may be associated with it.
- Open Applications folder
- Select Utilities
- Double-click Activity Monitor
- Here, look for suspicious processes related to adware and use the Force Quit command to shut them down
- Go back to the Applications folder
- Find ExtendedService in the list and move it to Trash.
![Uninstall from Mac 1 Uninstall from Mac 1]()
Upon infiltration, the virus might establish new User profiles and Login items for persistence. This might be the reason why you can't get rid of the app or the extension.
- Go to Preferences and select Accounts
- Click Login items and delete everything suspicious
- Next, pick System Preferences > Users & Groups
- Find Profiles and remove unwanted profiles from the list.
Finally, you should get rid of the extension that is used by crooks to harvest various personal data. Proceed with the following steps (note: if you can't perform this step, skip it for now):
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Get rid of leftovers
Leftover files, known as PLIST, hold various important configuration settings and might play a vital role in malware's operation. Remove them with the following steps:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and delete all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
You should also clean your web browsers to remove various trackers and other caches to ensure proper malware removal. You can employ FortectIntego for this job, or you can follow the manual steps below:
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
If you were unable to remove malware components within your web browser, don't worry – you can simply reset it as we explain below. Unlike other options, this won't lose any of your bookmarks or preferences as long as you remember your account details. To reset your browser, follow these steps:
Safari
- Click Safari > Preferences…
- Go to the Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop, and then select Empty Caches.
![Reset Safari Reset Safari]()
Google Chrome
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.
![Reset Chrome 2 Reset Chrome 2]()
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Graham Cluley. New Mac malware spreads disguised as Flash Player installer via Google search results. GrahamCluley. Computer security news, advice, and opinion.
- ^ AppleScript. Wikipedia. The free encyclopedia.
- ^ Ian Murphy. Apple’s XProtect completely fails to detect new AdLoad campaign. Enterprise Times. Business Technology News.








