Temlown ransomware (virus) - Free Guide
Temlown virus Removal Guide
What is Temlown ransomware?
Temlown ransomware is a malicious program that asks users to pay for their files
The Temlown virus belongs to the VoidCrypt ransomware family and was first spotted in late September 2021. Ransomware is a type of malware designed to extort money from innocent users and has been growing as one of the main attack methods in the cybercriminal world. Since malware is not that prevalent, it is yet unknown which methods cybercriminals use for its distribution.
Once installed on a Windows computer, the virus uses a combination of sophisticated AES and RSA encryption algorithms to lock all personal data. This results in all pictures, documents, videos, images, and other files being inaccessible to victims. During this process, all the affected files lose their original icons (they are replaced by blank ones) and have a unique extension appended which look as follows:
- file.jpg.[noitanimodd@gmail.com][MJ-WA9473106825].temlown
Note that the string that follows after the email address differs for each of the users, as it represents a unique ID. This is commonly used by attackers to identify their victims easier.
As soon as the encryption of files is complete, the malware drops a ransom note Read-this.txt, which serves as a message from cybercriminals. Unlike with other malware, ransomware authors do not hide the fact of what has been done to users' computers and instead use these types of notes to inform them about what happened to files and how they are supposed to proceed next if they want to retrieve them.
In this case, crooks demand an unspecified amount of Bitcoins for a decryption tool. They also offer a free trial decryption service, which can only be applied to a file no larger than 1MB. For communication purposes, two emails are provided – noitanimodd@gmail.com and temloown@tuta.io.
We strongly advise you not to pay the ransom, as there is no guarantee you retrieve access to your files. Instead, check all the information below, as we provide alternative methods that could help you recover at least some of your data without paying and risking losing your money.
| Name | Temlown |
|---|---|
| Type | Cryptovirus, ransomware data locking malware |
| Malware family | VoidCrypt |
| Encryption method | RSA + AES |
| File extension | .[noitanimodd@gmail.com][MJ-random].temlown |
| Ransom note | Read-this.txt |
| Contact | noitanimodd@gmail.com, temloown@tuta.io |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | To remove malware automatically, use SpyHunter 5Combo Cleaner security software |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
Malware distribution and how to avoid it
Since Temlown is a relatively new variant of VoidCrypt, it is not clear how the attackers spread it. Most of the time, crooks rely on time-proven methods that simply work the best, although innovation is also something they are inclined to use sometimes. For example, hackers have used the fileless[1] infection method in the past few years – it proved to be very effective as it is difficult to detect malware that resides in the system's memory.
Luckily, most widespread ransomware strains use more traditional infection methods, and they are relatively easy to avoid. Here are some tips provided by novirus.uk security experts:[2]
- Backup your personal files;
- Use SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable software at all times – make sure it is updated as necessary;
- Don't ignore warnings from security software and don't assume it's a false positive;
- Never download software cracks or pirated programs from illegal websites;
- Update all software, including your operating system, as soon as the updates are available;
- Use strong passwords for all your accounts and never reuse them;
- Use official sources to download software.
The ransom note
As already mentioned, ransomware authors typically deliver a ransom note so that users would find out about what happened to their computers and how to proceed next. This increases the chances of victims paying the ransom – which is the main goal of the attackers.
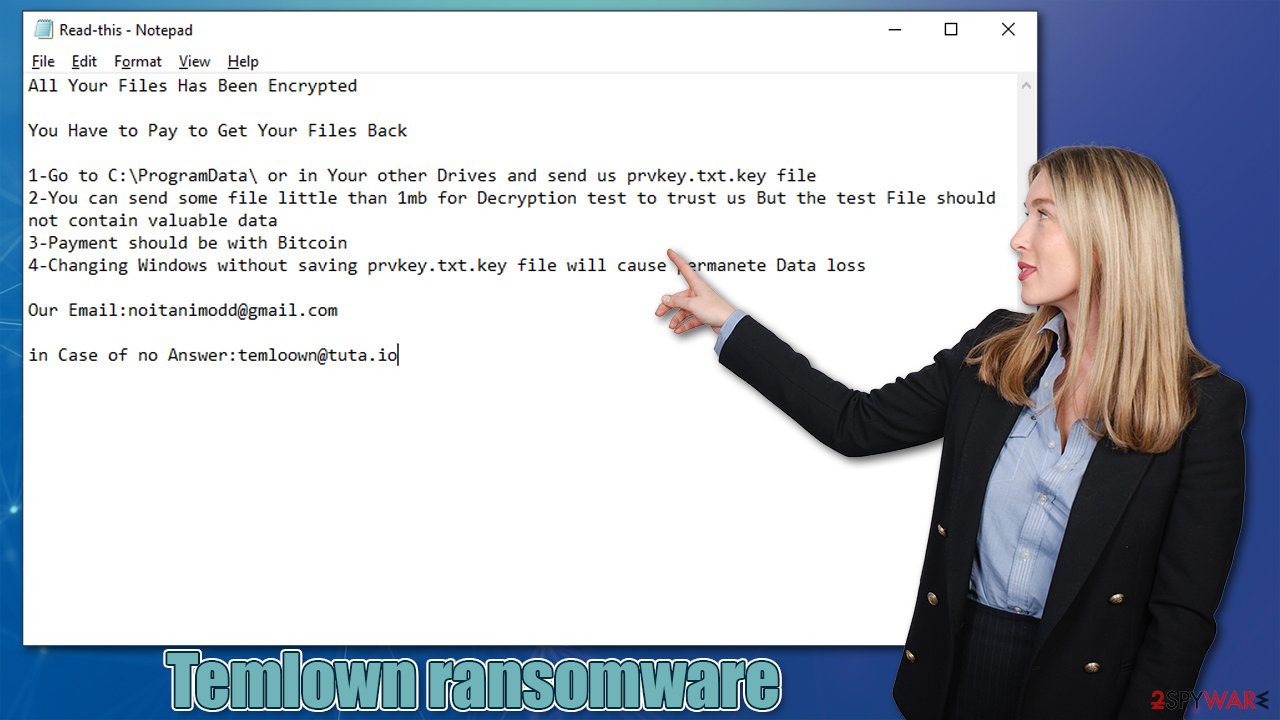
Temlown ransomware delivers a ransom note which goes straight to the point – here's what it says:
All Your Files Has Been Encrypted
You Have to Pay to Get Your Files Back
1-Go to C:\ProgramData\ or in Your other Drives and send us prvkey.txt.key file
2-You can send some file little than 1mb for Decryption test to trust us But the test File should not contain valuable data
3-Payment should be with Bitcoin
4-Changing Windows without saving prvkey.txt.key file will cause permanete Data lossOur Email:noitanimodd@gmail.com
in Case of no Answer:temloown@tuta.io
According to the message, users have to retrieve the “prvkey.txt.key” file from the local drive and send it to the cybercriminals. Allegedly, if this file were deleted or not sent to cybercriminals, data recovery would be impossible. Also, they highlight that changing anything within the operating system, including performing Temlown ransomware removal, would result in permanent data loss.
There are many reasons why not to pay malware authors. First of all, it was reported that the VoidCrypt malware family is known to fail in providing the decryption tool, even after the payment. The payments also motivate crooks to create even more versions of malware and spreading it around even more actively – it simply proves that the illegal business model works.
It is true that the locked data requires a unique encryption key that is only accessible to criminals. However, you can never be sure that the decryptor can be retrieved. Therefore, you might be risking not only your files but also your money. Instead of paying, we strongly recommend you remove the Temlown virus from your system and then use alternative methods for data recovery. Follow these steps we provide below.
1. Use anti-malware software
The first step when dealing with ransomware is its termination from the infected system. Because malware might be communicating with the attackers through the internet, you should disconnect your WiFi or Ethernet immediately. You can then try launching SpyHunter 5Combo Cleaner or Malwarebytes security software and scanning your machine fully to remove the infection at once.
Note that in some cases, the virus might interfere with the operation of security software. If that happens, you can bypass this functionality by accessing Safe Mode and performing a full system scan from there. If you need help on how to do that, find the detailed guide at the bottom of this post.
2. Alternative methods for data recovery
There is a huge misconception about ransomware – many people believe that anti-malware software can restore their files back to normal as soon as the scan is performed. Security software is not capable of doing this because it is simply not what it is designed for. Its main goal is to eliminate malicious files from the system and prevent malware from continuing its operations. It can't fix system file damage or decrypt files that were locked by ransomware. In other words, you won't recover .temlown files after you scan your machine with security software.
Another myth that is commonly spread among victims is that the data is corrupted. This is not true (in most cases at least), as the files are unreadable only because they are locked by a unique and complex key made of a long string of alphanumeric characters.
While anti-malware can't retrieve your files, there are few other methods that might be effective. First of all, if you have backups – use them. This is your best line of defense when it comes to ransomware infections, and you can recover easily if you keep your data on secure backups.
Unfortunately, most ransomware victims fail to back up their files and end up losing them (we provide a detailed guide on how to effectively do that at the bottom of this article). Luckily, you are not out of options yet. First, you should try specialized software that focuses on data recovery:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Temlown ransomware Temlown ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Data recovery software might not always work, as it highly depends on many factors. For example, whether malware failed to correctly encrypt files or whether it managed to delete Shadow Volume Copies.[3] Thus, in some cases, security research finds flaws within the malware's encryption method and creates a free decryptor for victims, although keep in mind that this might take a while.
In some cases, the law authorities can seize the attacker's servers. This always results in victims recovering their files for free. Below you will find links that could be used to find decryption tools online:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

3. Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software cannot do anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstallation is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it can also remove malware that has already broken into the system thanks to several engines used by the program. Besides, the application can also fix various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
Getting rid of Temlown virus. Follow these steps
Access Safe Mode to remove malware from Windows
If malware is not letting you use antivirus in normal mode, access Safe Mode and perform a full system scan from there.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Once you reach Safe Mode, launch SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable antivirus, update it with the latest definitions, and perform a full system scan to eradicate malware and all its malicious components.
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Temlown and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Fileless threats. Microsoft. Docs.
- ^ Novirus. Novirus. Cybersecurity advice and malware insights.
- ^ Shadow Copy. Wikipedia. The Free Encyclopedia.

























