Trust Wallet scam (fake) - Free Guide
Trust Wallet scam Removal Guide
What is Trust Wallet scam?
Trust Wallet scam attempts to steal your money, personal information or infect your system with malware
Trust Wallet is a popular cryptocurrency wallet that provides a secure and convenient way for users to store, receive, and transfer a broad array of digital assets. As a decentralized wallet, Trust Wallet allows you to maintain control of your private keys, enhancing security and privacy. Given its robust feature set and user-friendly interface, Trust Wallet has amassed a substantial user base.
Unfortunately, the wallet's popularity has also drawn the attention of scammers. With the growing number of users, there's an upswing in malicious actors attempting to impersonate the Trust Wallet service. These fraudsters aim to dupe users into giving up their accounts, personal information, or cryptocurrencies and often attempt to infect their systems with malware. They accomplish this through phishing emails and fake websites claiming to be affiliated with Trust Wallet – all of these attempts are just a scam you should avoid.
| Name | Trust Wallet scam |
| Type | Online scam, fraud, phishing |
| Distribution | Fake emails and specially crafted spoofing websites |
| Contents | Claims that users need to finish their account verification, then redirect them to a spoofing website where they are asked to enter their credentials or download malicious files |
| Removal | Never interact with any of the links provided, and scan your system with SpyHunter 5Combo Cleaner for enhanced security |
| Other tips | After the removal of malware, we also recommend clearing cookies and making sure that the system files weren't damaged – FortectIntego is a perfect tool for this job |
Deciphering Trust Wallet scams
As with any popular platform, Trust Wallet, a widely used cryptocurrency wallet, has unfortunately become a target for numerous fraudulent schemes. Fraudsters deploy a variety of crafty tactics, each tailored to trick unsuspecting users into compromising their digital assets or personal information. To stay protected, it's essential to unmask these deceptive practices and understand their modus operandi.
A common ploy is the “impersonation gambit,” where fraudsters use emails appearing to originate from TrustWallet. This impersonation is inherently misleading, as Trust Wallet never solicits your email address. Therefore, any such communication should immediately raise red flags, revealing the scammer's true intentions.
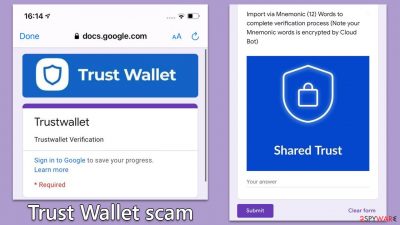
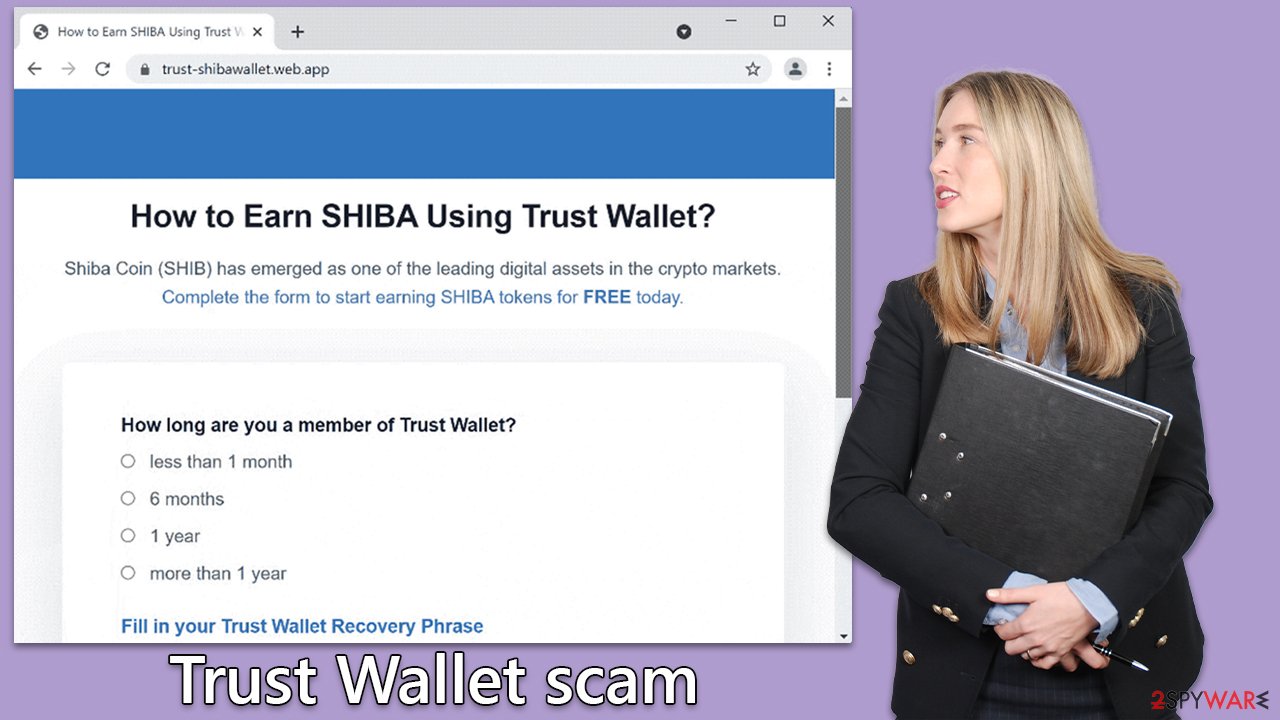
The second type of scam involves a crafty “verification ruse.” This scheme spins a tale around an urgent need for wallet verification, often bedecked with the official Trust Wallet logo to enhance its perceived authenticity. Users must remember that Trust Wallet will never prompt for wallet verification. Scammers also add a sense of urgency, urging you to click on links leading to phony Google forms designed to harvest your personal information.
Yet another trick up the scammer's sleeve is the “customer support trap.” Here, scammers pose as Trust Wallet's customer support team, asking users to fill out forms under the pretext of resolving a non-existent issue. Users must be wary of such traps, especially when they appear out of the blue and unsolicited.
The final and most dangerous scam centers around the “secret phrase snare.” Here, scammers request your secret phrase, the master key to your wallet. Disclosing it enables fraudsters to recreate your wallet, giving them unrestricted access to your digital assets. The golden rule is to never reveal your secret phrase, regardless of the situation.
While fraudsters continue to evolve their tactics, awareness and vigilance, remain your best defenses. To secure your computer from malware, you should employ automatic solutions such as SpyHunter 5Combo Cleaner or Malwarebytes security software.
How to stay safe
Understanding how to guard against these dangerous scams requires a blend of vigilance and cautious online practices. Several key principles help you steer clear of scam pitfalls in the cryptocurrency landscape:
- Keep your secret phrase confidential. The golden rule in the crypto world is to maintain absolute confidentiality of your secret phrase. This is the master key to your crypto assets and should never fall into the wrong hands. It's your personal responsibility to store it safely. Remember, the Trust Wallet team will never ask for your secret phrase.
- Avoid suspicious links. Refrain from clicking on suspicious links, especially those presented in emails or messages claiming to be from Trust Wallet. Phishing links are a common tool used by scammers to trick you into revealing sensitive information or downloading malicious software. Instead, directly type in the website URL of Trust Wallet if you need to access your wallet or find information.
- Exercise caution with emails. Be wary of emails purporting to originate from Trust Wallet. Remember, Trust Wallet does not send out emails asking for personal information or wallet verification. These are telltale signs of scam attempts. Moreover, avoid filling out any forms that are presented in these emails or on unofficial platforms and ask for your personal details.
- Stay updated. Keep up with the latest information from Trust Wallet's official channels. Trust Wallet frequently issues security warnings and updates, providing valuable insights to stay a step ahead of scams. Remember, knowledge is power, especially when navigating the challenging terrain of cryptocurrency.
These principles form the cornerstone of safe practices in the world of cryptocurrencies. Adherence to these can significantly enhance your security against potential scams.
Checking your device for infections
Another significant concern is the risk of malware infection from clicking links or downloading software from these malicious websites or emails promoting Trust Wallet scams. Once installed, malware can steal your data or control your device. Therefore, it's paramount to secure your devices.
Consider using advanced security software like SpyHunter 5Combo Cleaner or Malwarebytes. They offer comprehensive protection, scanning your system for any potential threats and removing them. Additionally, they can secure your online browsing, protect your personal information, and enhance your device's performance. Regular system scans help ensure your device remains malware-free.
Finally, we also recommend checking the installed extensions and clean browser caches for enhanced privacy and better security. Cleaning your browsers from cookies and other data regularly is recommended under any circumstances and is especially important if potentially unwanted programs or malware manage to infiltrate your device.
The easiest way to clean your browsers is by employing a powerful PC repair tool FortectIntego. It also can quickly find all the malware-caused system damage and repair it automatically, so you can use your device problem-free again. If you'd want to undergo these checks yourself, you can refer to the manual instructions below this article.
What to do if you have been a victim of a Trust Wallet scam
If you've inadvertently clicked on a suspicious link or provided your personal details on a fraudulent website, it's critical to take immediate steps to minimize potential damage. First, disconnect your device from the internet to prevent any further data transmission. If you've downloaded any files from the suspicious link, do not open them and delete them immediately, then empty your trash or recycle bin.
Once you've disconnected and removed potential threats, it's time to assess the situation and take protective measures. If you've given out your secret phrase, consider moving your funds to a new wallet. Unfortunately, once a scammer has your secret phrase, they can access your wallet from anywhere.
If you have disclosed other personal information, such as credit card details or social security numbers, contact the respective organizations immediately to inform them of the potential breach. Additionally, consider using identity theft protection services, which can monitor your personal information and help to mitigate any potential damage. Always remember acting swiftly and decisively can make a significant difference in such situations.
Getting rid of Trust Wallet scam. Follow these steps
Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

How to prevent from getting malware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.


















