Vista Protection 2014 (scam) - Easy Removal Guide
Vista Protection 2014 Removal Guide
What is Vista Protection 2014?
Vista Protection 2014 – a scareware program that pretends to be security software
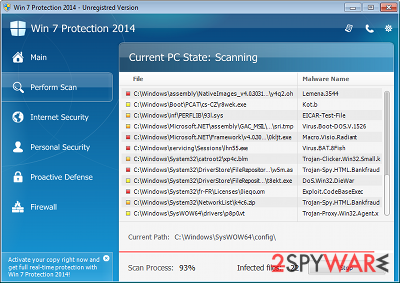
Vista Protection 2014 is a serious cyber threat which goal is to trick users into buying its license. For that, cybercriminals use scare tactics by showing users fake notifications about virus infections on a Windows machine when, in fact, the only virus is the program itself. What makes it worse is that the program is commonly distributed by already installed Trojans on the system or via fake online scanners that show bogus messages on various malicious sites.
The name of this rogue is adaptive, meaning that “Vista” can be replaced by any other operating system version. The same logic applies to a year – it changes as time passes. If you found this malware showing you virus alerts, do not believe the scan results, and especially do not waste your money on its “license.”
| Name | Vista Protection 2014 |
| Type | Rogue antivirus |
| Distribution | Trojan downloaders, fake scanners, software vulnerabilities |
| Operation | Makes it look like the system is infected in order to make users purchase program's license which is useless |
| Danger | Monetary losses, personal data leak, system file corruption |
| Removal | Scan your device with powerful anti-malware |
| System fix | If your system starts crashing or throwing errors, use FortectIntego to fix virus damage at once |
The changes that the rogue makes to the infected operating system are very serious and are easily comparable to those done by malware. Like we already mentioned, it is a cyberthreat itself, so it should be treated as such. Real security programs would never disable Windows features or show an incredible amount of false positives with an intent to mislead.
Vista Protection 2014 belongs to a huge family of rogues that is known as Braviax. It consists of lots of other versions of this threat that are capable of infecting other Windows OS. If malware manages to infiltrate a computer, the first thing that is done is system's modifications, which may include:
- Disables the Task Manager
- Sets itself to be launched with every system boot
- Modifies Windows registry
- Drops multiple files that are later shown as malicious by rogue's scan, etc.
Additionally, it starts displaying fake system scanners and alerts that all report about invented viruses. Here is one example of such misleading messages:
Tracking software found!
Your PC activity is being monitored. Possible spyware infection. Your data security may be compromised. Sensitive data can be stolen. Prevent damage now by completing a security scan
By showing these alerts, Vista Protection 2014 seeks to scare its victims and make them think that the only real way that can fix their computer is the licensed software version. Buying it, however, does absolutely nothing, and the system will remain infected.
In fact, this app does not have any database and does not use any malware-detection techniques that are prevalent in most modern security suites such as SpyHunter 5Combo Cleaner or Malwarebytes. Thus, employ these tools to find and delete this malicious program from your system for good.
Double trouble: rogues are often installed by Trojans
As we have already mentioned, Vista Protection 2014 is spread with the help of Trojans that can easily enter your computer through security holes and other vulnerabilities. If you want to avoid them, you should always make sure that you have a reputable anti-virus installed on your computer.
Also, security experts recommend avoiding illegal websites, suspicious emails, and questionable programs spread on the Internet for free. If a rogue antivirus infects its target PC, it starts various system modifications and causes fake system scanners.
As we have already said, you should ignore these ads because they are displayed for the only thing – seeking to trick you into purchasing a fake licensed version. If you noticed such similar alerts telling that your computer is seriously infected, you should check it with a reputable anti-spyware because it's one of the clearest signs showing that your machine was affected by a rogue.
Uninstall Vista Protection 2014
If you noticed Vista Protection 2014 alerts telling that your computer is infected by trojans, adware, and other dangerous programs, it's a clear sign showing that it is infected. Do not waste time and remove this rogue anti-spyware.
For this, we strongly recommend using the automatic removal option and avoiding manual removal because you may remove the wrong files and damage your PC system. You should download a reputable anti-spyware, update it and run a full system scan. If you need a detailed guide explaining how to do that, read this guide.
ATTENTION! As we have already mentioned previously, Vista Protection 2014 may try to block the installation and activity of legitimate security programs. If you can't download or launch any of them, try these options:
1. USING SYSTEM RESTORE TO DISABLE VIRUS:
- Click Start -> All Programs -> Accessories -> System Tools -> System Restore.
- As soon as Restore system files and settings window shows up, select Next.
- Choose the restore point that you want and click Next .
- Click Finish to confirm and wait until your PC reboots.
- Now download FortectIntego and run a full system scan after updating it.
2. REBOOTING TO SAFE MODE WITH NETWORKING:
- Restart your computer
- As soon as your computer becomes active, start pressing the F8 key continuously until you see Advanced Boot Options screen.
- Here, select Safe Mode with Networking (for that, use the arrow keys) and then hit Enter.
- Login as the same user as you were in normal Windows mode
- Now right click on IE or other browser's icon and select Run As or Run As administrator. Enter your Administrator account password (if needed).
- Now launch security software and perform a full system scan
3. CREATING GUEST ACCOUNT FOR SCANNING COMPUTER:
If you have another user (guest) account, you can try to run a full system scan from it. You just need to log into it and download FortectIntego for a full system scan. You can activate your guest account with a help of these steps:
- Click Start -> Control Panel and select User Accounts and Family Safety.
- After a new window shows up, click on Add or Remove User Accounts -> Guest Account.
- Now click on Turn On button and restart your computer
- Now wait until you see Windows log on screen and select Guest account for downloading recommended anti-spyware.
4. USING ANOTHER PC FOR DOWNLOADING ANTI-SPYWARE:
- Take another computer that is not infected by this virus and download FortectIntego or SpyHunter 5Combo Cleaner on it.
- After completing the procedure, transfer this anti-malware to the CD/DVD, external drive, or USB flash drive.
- In the meanwhile, kill malicious processes on your infected computer. For that you can use this tutorial.
- Stick the device you used for transferring anti-spyware program to your infected PC and launch it.
How to prevent from getting rogue antispyware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
