Stepik ransomware (virus) - Recovery Instructions Included
Stepik virus Removal Guide
What is Stepik ransomware?
Stepik ransomware seeks to extort money from innocent victims
Stepik operates like any other typical ransomware virus – it is designed to encrypt all files on the system and then demand ransom for their return. It does not seem to belong to any currently known malware strain and was first spotted in the wild in the first half of November of 2021.
The virus attacks Windows computers exclusively, although the attack vectors are currently unknown. Typically cybercriminals use spam email attachments, software vulnerabilities,[1] or repacked/cracked software as the main distribution means. Regardless of the distribution methods, ransomware is never installed purposely by users, and they are tricked into doing so in one way or another.
Once installed, Stepik ransomware begins the infection process of a Windows machine and all networked devices connected to it. The system modifications are in place for malware to fulfill its main purpose of data encryption, which converts all pictures, videos, documents, databases, and other files into unusable ones. During this process, each of the files acquires a .stepik extension (note that they are not corrupted by rather locked with a strong encryption algorithm).
The virus creates a unique key and sends it off to a remote server controlled by attackers. This guarantees that the data is held hostage by the crooks, as the decryption key is required to restore all files to their original form, making them usable again. Of course, hackers are not willing to give it up for free and instead ask for a payment in Bitcoin – a cryptocurrency that ransomware authors use.[2]
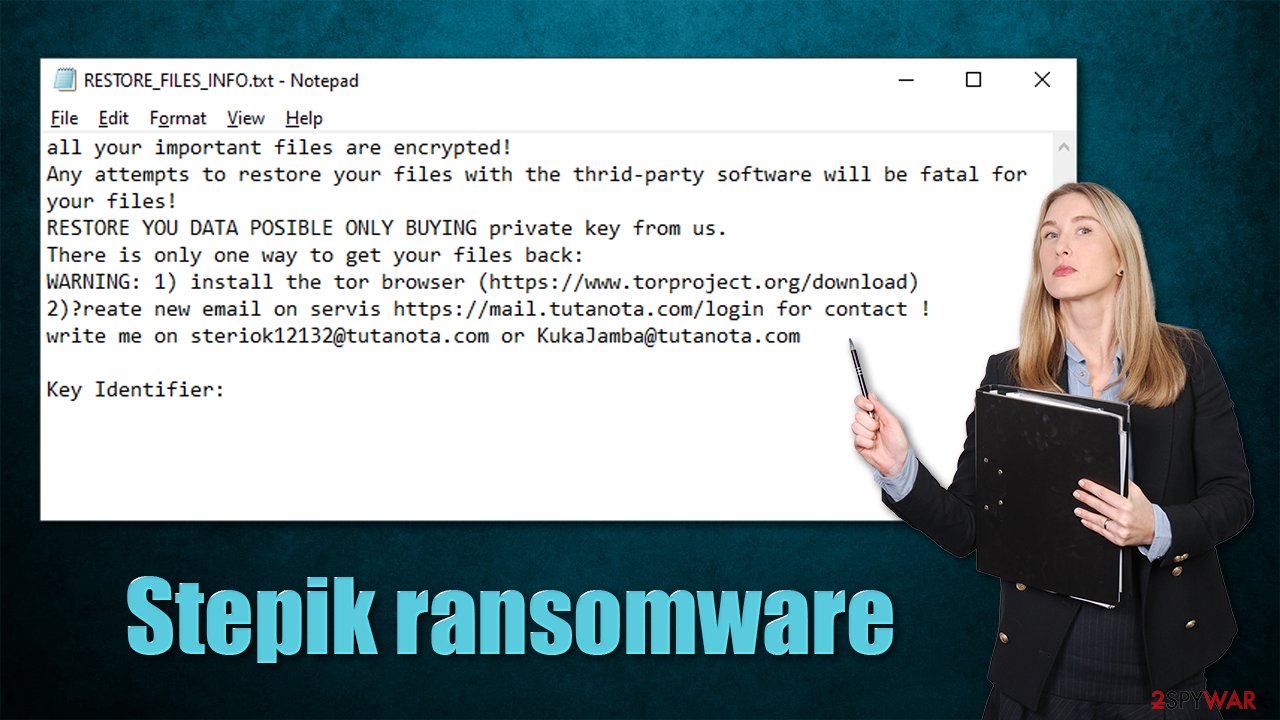
In the ransom note RESTORE_FILES_INFO.txt, which is placed on the desktop and various folders on the system, it is claimed that the victims need to contact cybercriminals via steriok12132@tutanota.com or KukaJamba@tutanota.com emails. Users should also create an account via Tutanota – an email service commonly used by hackers for communication thanks to its end-to-end data encryption,[3] making them fully anonymous.
We strongly recommend you refrain from paying the attackers, as you might get scammed out of your money, all while never receiving the key needed for file deception. Keep in mind that this malware strain is relatively new and it is unknown whether the crooks behind it can be trusted with sending you the required tool after payment.
| Name | Stepik ransomware |
|---|---|
| Type | Ransomware, file-locking malware, cryptovirus |
| File extension | .stepik extension appears at the end of every file name |
| Ransom note | RESTORE_FILES_INFO.txt, placed on the desktop |
| Contact | steriok12132@tutanota.com or KukaJamba@tutanota.com |
| Data Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Manual virus removal is not recommended, as it might be difficult for regular users. Instead, SpyHunter 5Combo Cleaner or other anti-malware tools should be used |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the system and avoid its complete corruption, we recommend scanning it with the FortectIntego repair tool |
Ransom note example
A ransom note is something that ransomware authors commonly use to provide contact information through. It is in the best interest of the attackers to do so, as it increases the chances of retrieving payment. This is why each of the victims is also assigned a unique key identifier, which is shown within the note itself – it is meant to be sent via the provided email to identify each of the victims. For example, ransomware like Palq or Efdc infects hundreds of users daily, and it would be rather difficult to identify each of the victims without it.
Stepik virus authors keep it relatively short and go straight to the point. Here's the writeup of the full message that victims receive after data encryption is finished:
all your important files are encrypted!
Any attempts to restore your files with the thrid-party software will be fatal for your files!
RESTORE YOU DATA POSIBLE ONLY BUYING private key from us.
There is only one way to get your files back:
WARNING: 1) install the tor browser (https://www.torproject.org/download)
2)Сreate new email on servis https://mail.tutanota.com/login for contact !
write me on steriok12132@tutanota.com or KukaJamba@tutanota.comKey Identifier:
The attackers claim that using alternative methods to restore your files would bring no results and that victims should instead contact them for a decryptor. Whether you decide to go for it or not, remember that cybercriminals behind ransomware are not your friends, and they don't care about you. You should never trust them.
Instead, we strongly recommend performing Stepik ransomware removal correctly and then employing alternative methods for data recovery. Follow the steps below.
1. Remove malware from the system
Most people who get infected with ransomware have never even heard of it and even if they did, they know very little about it in a general sense. It is common because none of the users initially believe they might be victims of the devastating computer infection.
Thus, once users find that they can no longer open any of the files on the computer, they might straight out panic. While it is true that ransomware is among the scariest infections out there, panicking will not result in anything positive. The first step you should take is taking care of ransomware removal.
Some ransomware strains are known to self-delete after they complete data encryption, while others continue running in the background. The latter kind can download additional modules, update itself, proliferate other malware, steal sensitive information, and continue encrypting all their incoming files.
Regardless of which category the Stepik virus belongs to, you should always employ SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable security software for its elimination. Manual removal is also possible but should be avoided due to numerous reasons. Security software can find and remove all the malicious files and stop the infection from functioning.
It is worth noting that security software can't repair damaged system files, as it is simply not designed for that. Damaged system files remain and can cause major operational disruptions in the future. Therefore, we recommend you employ a PC repair tool FortectIntego to fix all the corrupted system files instead of reinstalling the OS altogether.
Note: ransomware could interfere without the operation of security software. If that's the case, scroll down to the very bottom to find instructions on how to access Safe Mode and perform a scan from there.
2. Recover .stepik files without paying the ransom
Once malware is removed from the system, you can proceed with the next step – your file recovery. As evident, cybercriminals ask you to pay the ransom and recover your data in that way. As we already explained, it is far from an ideal scenario – you might get scammed and it would only prove to malicious actors that their illegal business scheme works as intended. Therefore, we recommend taking the alternative route instead, although its results can't be guaranteed.
If you have no backups for your encrypted files, it is vital that you copy the encrypted files onto another medium before you proceed. Otherwise, the files might get corrupted and would be irretrievable even with a working decryptor. It is also important to note that your antivirus software will not restore your files, as it is simply not designed for that. What it will do is remove all malicious files and processes from your infected machine – an absolutely necessary step.
1. Try recovery software
Data recovery software is your best bet at recovering files when no decryptor is available. It is not guaranteed to work, but you should definitely try this option.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Stepik ransomware Stepik ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
2. Wait for a decryptor
Security experts are known to work on decryption tools for major ransomware strains. In some cases, flaws within the encryption process can be found or criminals' servers seized by the lay authority agencies. In any case, you could look for decryptors on the following pages, although keep in mind it might take a while until there's a working one made.
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors
3. Bonus tips
There are two main things you should do to negate ransomware infection impact – backup your vital files (and keep them updated) and always run a protection software, such as SpyHunter 5Combo Cleaner, that would warn you about the incoming malware attacks. That being said, it is important you don't ignore warnings from security software and automatically add the newly-downloaded files to an exception list, especially if you frequent illegal websites that distribute pirated apps and games.
If you need help with data backups, please refer to the instructions below – we provide OneDrive and Google Drive guides. Another thing you could do is contact your local authorities that deal with fraud and cyber attacks. This could help catch the culprits, eventually releasing of keys used to encrypt victims' files.
Getting rid of Stepik virus. Follow these steps
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Access Safe Mode to remove malware from Windows
If malware is not letting you use antivirus in normal mode, access Safe Mode and perform a full system scan from there.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Once you reach Safe Mode, launch SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable antivirus, update it with the latest definitions, and perform a full system scan to eradicate malware and all its malicious components.
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Thomas Holt. What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. Popular Science Magazine.
- ^ Why hackers rely on Bitcoin for ransom payments. DW. News and current affairs from Germany and around the world.
- ^ End-to-end encryption. Wikipedia. The free encyclopedia.





















