“Windows 10 May Be In Danger” scam (fake) - Free Guide
“Windows 10 May Be In Danger” scam Removal Guide
What is “Windows 10 May Be In Danger” scam?
“Windows 10 May Be In Danger” scam uses scare tactics to promote a legitimate antivirus tool
“Windows 10 May Be In Danger” is a web scam that uses various scare tactics to make users install antivirus software. The page promotes a legitimate antivirus tool called Total AV. However, the developers of the program have nothing to do with this fraudulent campaign. Users can sign up for an affiliate program via the Total AV official website, so the crooks probably receive revenue for every installation with their link.
Schemes like this are usually promoted on shady websites that engage in illegal activities because they are unregulated. Untrusted advertising networks can place their ads in them and lure users in with deceptive messages. Another reason why you could have ended up on this page is that you have adware[1] hiding in your system that generates unwanted commercial content like pop-ups, banners, and redirects in your machine.
| NAME | Windows 10 May Be In Danger |
| TYPE | Online scam; adware |
| SYMPTOMS | A page pop-ups up claiming that Windows 10 could be infected with viruses |
| DISTRIBUTION | Compromised websites, deceptive ads, software bundling |
| DANGERS | Installation of PUPs or malware, sensitive information disclosure, monetary losses |
| ELIMINATION | In order to avoid viewing malicious ads, you should install a reliable ad-blocking app. You should also check your system for adware – you can either do it manually or perform a full system scan with antivirus for a quicker solution |
| FURTHER STEPS | If you want to clean your web browsers quickly and/or fix virus damage automatically, we recommend using FortectIntego repair tool |
Scammers use social engineering techniques
Social engineering is a manipulation tactic that exploits human error. In this case, scammers want to frighten users into taking an action. First, they do this by designing the website to look like a legitimate Microsoft page. They even put Microsoft's support email address in the corner to gain trust.
The page also shows the user's IP address[2] and browser version. This is also meant to make users believe the message shown. This tactic is also used in another scam that we previously wrote about called “IP address & personal information might be exposed.”
The truth is that almost every website you visit can see your IP address, browser version, and approximate location if you have that turned on because they use cookies.[3] So do not be fooled if you see your “personal information” flashing on the screen. Scammers want you to act quickly before you have a chance to think.
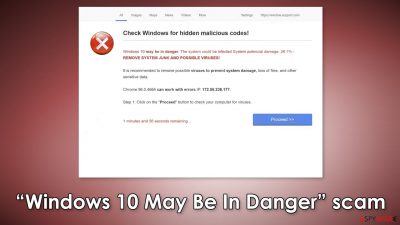
Second, fraudsters use words that may raise concerns for average users who are less IT-savvy. The message that people first see says:
Check Windows for hidden malicious codes!
Windows 10 may be in danger. The system could be infected.System potencial damage: 28.1%
REMOVE SYSTEM JUNK AND POSSIBLE VIRUSES!It is recommended to remove possible viruses to prevent system damage, loss of files, and other
sensitive data.Chrome 96 0 4664 can work with errors IP 172.58 236 177.
Step 1: Click on the “Proceed” button to check your computer for viruses.
1 minutes and 56 seconds remaining…Proceed >>
They also use a time limit to introduce a sense of urgency and leave no time for people to think. Once users proceed, the page shows a “SCAN IN PROGRESS” message. Of course, after the scan is complete, the page shows a bunch of viruses that have apparently infected the device. The website says that in order to remove them, people need to download special software, and this is the part where users get redirected to the Total AV website.
Start the removal process
You might be seeing the “Windows 10 May Be In Danger” scam page because you have a malicious extension added to your browser which is causing pop-ups, banners, redirects, and an overall increase of commercial content in your device. Even if you do not notice these symptoms we suggest investigating your browser.
The first thing you should do is go to your browser settings and check if you see any suspicious add-ons in the list. The best way to do this is by removing the extensions one by one and seeing if you notice any difference. You can follow our guide if you need help:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Internet Explorer:
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
![Remove add-ons from Internet Explorer Remove add-ons from Internet Explorer]()
One more thing you should do is clean cookies and cache from your browser. Many websites use these tracking technologies to see the links you click on, things you purchase online, and other data like your IP address, which we mentioned before. Generally, these technologies help websites to personalize the user experience.
But we see that more often, cookies are used to generate revenue. They can be sold to advertising networks or other third parties and used for malicious purposes so security experts recommend clearing them regularly. You can use a maintenance tool like FortectIntego which will do this automatically.
Remove PUPs hiding in your system
Unwanted ads can also be caused by adware, so we strongly suggest using anti-malware tools like SpyHunter 5Combo Cleaner and Malwarebytes to scan your system. Manual removal of a PUP can be tricky if you do not have experience. Even if you uninstall the program itself, it can leave some traces behind (like files, registry entries, etc) which can result in a renewal of the infection.
PUAs are also often disguised as handy tools that you would never suspect. Professional security tools will scan your machine, eliminate intruders, and prevent such infections in the future by giving you a warning before a suspicious program can make any changes.
Adware is mostly spread on freeware distribution sites. The owners include additional programs in the installers without clearly disclosing this on their platforms. Most people skip through the installation process and do not notice bundled software.[4] That is why it is so important to have a tool that can detect these processes for you.
You can use the guide below to remove Total AV if you have installed it or to try to identify any suspicious programs that should not be on your computer.
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.
![Uninstall from Windows 7/XP Uninstall from Windows 7/XP]()
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
How to prevent from getting adware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Adware. Malwarebytes. Cybersecurity Basics.
- ^ IP address. Wikipedia. The free encyclopedia.
- ^ What are Cookies?. Kaspersky. Home Security.
- ^ Liam Tung. Google: Unwanted bundled software is way more aggressive than malware. ZDNet. News Stories.