“IP address & personal information might be exposed” scam (fake) - Tutorial
“IP address & personal information might be exposed” scam Removal Guide
What is “IP address & personal information might be exposed” scam?
“IP address & personal information might be exposed” – a message delivered by malicious websites
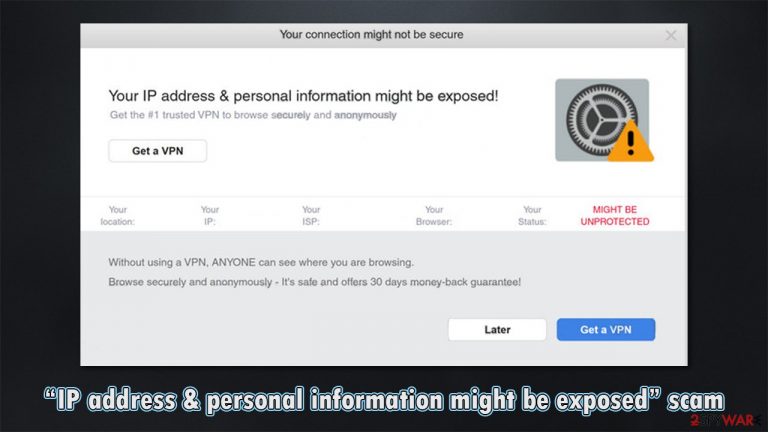
An online scam recently emerged with flashing a fake message – “IP address & personal information might be exposed”. This scam is pushed by various untrustworthy websites aiming to promote software that is likely to be malicious by claiming that users are unsafe while browsing the internet. In this case, it is promoting a VPN program. Sites like this endorse legitimate products as well and generate click revenue through deceptive and questionable tactics.
However, more commonly, they distribute potentially unwanted applications or in short – PUAs, which are not malware[1]. Sometimes they function as adware causing the device to slow down, selling information to advertisers, tracking a person's internet usage, and inserting their own advertising into web pages. They try to look like they provide users a useful service, when in reality, as it is activated, often does not function as advertised.
If you think you have been infected by adware you should follow our step-by-step guide below, as we provide you with ways you can get rid of it yourself manually, or automatically by using one of our recommended tools.
| Name | IP address & personal information might be exposed scam |
| Type | Scam |
| Infiltration | Compromised websites, pop-up ads, potentially unwanted applications. |
| Scam content | Claims that the visitor's IP address is exposed encouraging to download untrustworthy software |
| Dangers | Installation of PUPs or malware, sensitive information disclosure, monetary losses |
| Removal | In order to avoid viewing malicious ads, you should install a reliable ad-blocking app. You should also check your system for adware – you can either do it manually or perform a full system scan with antivirus for a quicker solution |
| System fix | If you want to clean your web browsers quickly and/or fix virus damage automatically, we recommend using FortectIntego repair tool |
Usually, users stumble upon scam-promoting sites by accident when typing in URLs into the search engine incorrectly or by websites that redirect to them. This could also happen through clicking on invasive advertisements or installed PUAs.
Scams like this do not require complicated skills. This particular scam uses scare tactics by showing a worrying message, making a person feel exposed and unsafe, and providing them with a quick solution that is appealing. Upon creating the page, it is spread by shady advertising networks and all you should do if you come across this page is leave it immediately and not interact with it.
Tactics used by scammers to lure people in
IP address & personal information might be exposed scam preys on not so computer savvy people to make them perform an action useful to its creators by using a few different strategies.
The full message on the website reads as follows:
|
Your IP address & personal information might be exposed! Get the #1 trusted VPN to browse securely and anonymously GET A VPN Your location: Without using a VPN, ANYONE can see where you are browsing. Browse securely and anonymously – It's safe and offers 30 days money-back guarantee! |
As you can see, upon stumbling on this site, it states that the user's IP address and personal information might be exposed. It then shows the person's location and device IP address which can scare people who do not know that by default, IP addresses are public anyway and that it is not something out of the ordinary. All Internet communications require Internet Protocol (IP) addresses. If a website you visit could not see your IP address, it would have no way to send you pages, images, files, and so on[2].
The scam then suggests a user get “the #1 trusted VPN” to protect their privacy on the internet. A VPN (virtual private network) is a service that gives you online anonymity by creating a private network from a public internet connection. They encrypt your data and hide your IP address by bouncing your network activity to another server far away. This hides your online identity, so you can browse the internet safely and anonymously. But for cybercriminals, VPNs can be a way to spread malware, which is a big online security risk. If you want to read more about what VPNs are and how to choose one, you can do so by going to a detailed analysis we did on VPN Software.
If you have continued with the installation process of this suggested VPN or keep seeing this page or similar ones over and over again, notice an increased amount of pop-ups, commercial banners, offers, and other content you should check if you have any PUPs on your system by using one of our recommended tools for detecting unwanted programs SpyHunter 5Combo Cleaner and Malwarebytes or other trustworthy security applications. Or you can follow these steps to remove it manually:
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
If you are using a Mac, proceed with these steps:
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Reasons for seeing scam websites just like this
One of the biggest reasons why you could be seeing advertising pop-ups is that you have a PUP on your system. Most commonly PUPs get downloaded through software bundling[3]. This usually happens when a person installs some software from third-party vendors which is free. It is always recommended to download programs from the official websites to avoid infecting yourself with a virus or adware.
When going through the installation process, you should not rush it and skip through the steps. Read through the privacy policy and make sure there are no extra files included that you do not need. If you see files not related to the service you are trying to download, just uncheck the boxes next to the file name.
PUAs can also have official promotional pages. For example, “IP address & personal information might be exposed” is known to use the “user-shield-check.com” domain. Intrusive pop-up ads are used to spread PUAs as well. Once clicked on, these ads can execute certain malicious scripts to complete a stealthy installation without users’ consent or knowledge.
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Wikipedia. Potentially unwanted program. Wikipedia. The free encyclopedia..
- ^ Wikipedia. IP address. Wikipedia. The free encyclopedia..
- ^ M.R. Anglin. What is a Software Bundle? (with picture). EasyTechJunkie. Research Blog..
