The threat of the year: Cryptolocker
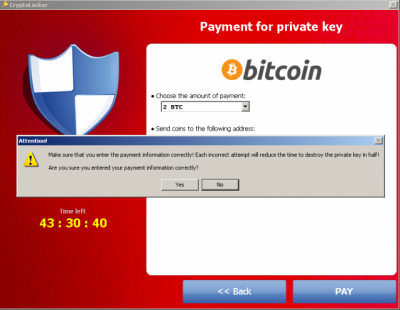
What has been causing such huge losses? Of course, it’s the ransom, which is usually required by Cryptolocker right after it encrypts victim’s files. For encrypting them, this threat uses AES algorithms, so it’s impossible to guess the code that is needed for decrypting encrypted files. You can also hardly apply one of these tools that are promoted as file recovery tools because such threats are constantly updated. Failing to pay the fine puts you at the risk of losing your files because attackers claim that they will destroy the private key unless you pay the ransom. If you are interested how much this virus asks in exchange for recovering affected files, you should know that this threat demands ransoms from $200 to $10,000.
Of course, this payment is not the only loss that is caused after Cryptolocker’s infiltration. If the target is a huge company, the loss includes the costs associated with the loss of employee’s productivity, fees for IT services, network mitigation, network countermeasures, etc.
Obviously, families and companies should educate their people to help them identify social engineering and malicious email attachments. The main thing that has to be remembered by those who want to prevent infiltration of Cryptolocker virus is that they should be really careful with every email from unknown sender. In addition, they should stay away from suspicious advertisements that look too good to be true. Finally, infected websites or websites that are filled with adult content should be avoided and never visited. Finally, we should give you one more tip that was given to people by FBI: “If you receive a ransomware popup or message on your device alerting you to an infection, immediately disconnect from the Internet to avoid any additional infections or data losses.”

