CryptoWall virus (Removal Instructions) - 2021 update
CryptoWall virus Removal Guide
What is CryptoWall virus?
CryptoWall is a ransomware family that encrypts important files on the affected computers
CryptoWall is a ransomware family that is designed to use a sophisticated encryption algorithm to make files inaccessible on the targeted computers. Malware researchers spotted the first version of ransomware in 2013.[1] Since then, crypto-virus was updated several times. While some versions can be decrypted for free; others are still unbreakable in 2018.
The peak time for this ransomware was 2014. During its lifetime, ransomware mostly affected US and Canada users. However, the United Kingdom, the Netherlands[2] and Germany were hit by the attack as well. Though, several attacks were noticed in other countries as well. In 2018, malware is not spreading actively. However, users are suggested to remain vigilant to avoid cyber attack.
Ransomware program targeting Windows systems. It has spread through various infection vectors since its inception, including browser exploit kits, drive-by downloads, and malicious email attachments. Since late March 2014, it has been mainly distributed through malicious attachments and download links sent out by the Cutwail spam botnet.
Researchers assume that CryptoWall Locker virus is developed by the same group of crooks who might be accused of CryptoDefense, Cryptolocker, BitCrypt, Critroni, and Cryptorbit, ownership. It operates as Trojan horse that might arrive on the system using exploit kits and malicious spam emails. It is capable of infecting all Windows versions, including Windows XP, Windows Vista, Windows 7, and Windows 10.
On the infected system, it creates new registry entries to run with Windows startup. Additionally, it connects to remote locations and starts communicating with the Command and Control server. Right after it infects the system, it, it encrypts predetermined files and blocks the user so that he/she wouldn’t be capable of accessing them.
Ransomware uses RSA 2048 cryptography to target the most popular file types, such as:
.xls, .wpd, .wb2, .txt, .tex, .swf, .sql, .rtf, .RAW, .ppt, .png, .pem, .pdf, .pdb, .PAS, .obj, .msg,.mpg, .mp3, .lua, .key, .jpg, .hpp, .gif, .eps, .DTD, .doc, .der, .crt, .cpp, .cer, .bmp, .bay, .avi, .ava, .ass, .as.p, .js, .py, .pl, .db, .c, .h, .ps, .cs, .m, .rm.
It managed to so by employing elaborate file encrypting techniques which help it lock multiple files with different extensions at the same time. After the encryption process is complete, the threat presents the ransom message with data recovery instructions in DECRYPT_INSTRUCTION.txt, DECRYPT_INSTRUCTION.html, and DECRYPT_INSTRUCTION.url files.
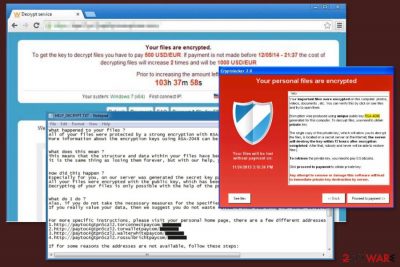
Also, shows such alert:
Decrypt service
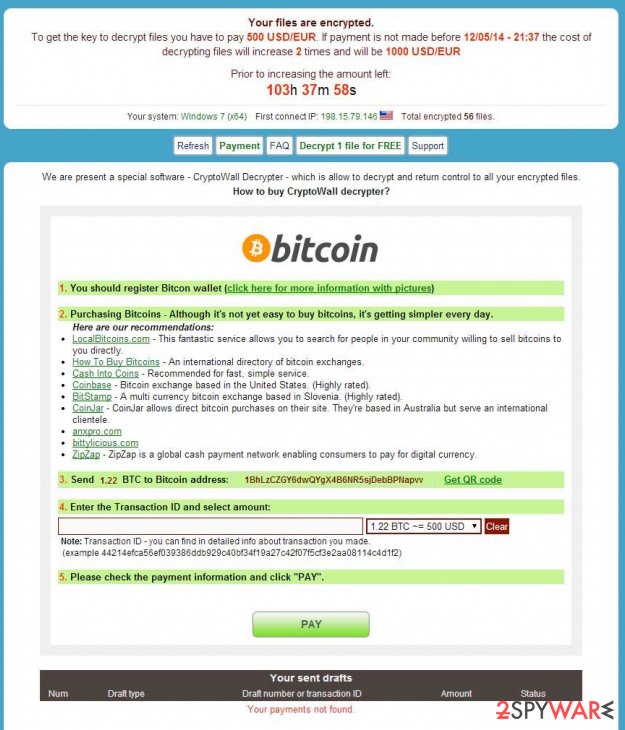
Your files are encrypted.
To get the key to decrypt files you have to pay 500 USD/EUR. If payments is not made before [date] the cost of decrypting files will increase 2 times and will be 1000 USD/EUR Prior to increasing the amount left: [count down timer]
We are present a special software – CryptoWall Decrypter – which is allow to decrypt and return control to all your encrypted files. How to buy CryptoWall decrypter?
1.You should register Bitcoin waller
2. Purchasing Bitcoins – Although it’s not yet easy to buy bit coins, it’s getting simpler every day.
3. Send 1.22 BTC to Bitcoin address: 1BhLzCZGY6dwQYgX4B6NR5sjDebBPNapvv
4. Enter the Transaction ID and select amount.
5. Please check the payment information and click “PAY”.
It is unwise paying the money as there are few guarantees that you will retrieve the files. It’s just a malicious method used for earning illegal money. After the attack, you should run a full system scan with FortectIntego or Malwarebytes ASAP to complete removal. Please, make sure you use the updated version, which will help you to remove all malicious files that belong to this ransomware.
Victims have to enter CAPTCHa correctly in order to access ransom payment website
Following data encryption, ransomware drops files that contains a link to the payment website which greets victims with saying:
Service to decrypt the files.
To continue please enter the code from the picture in the input field.
When victims enter the CAPTCHa correctly, they are allowed to enter the payment website. Here developers of the ransomware provide detailed information how and where to buy Bitcoin in order to send them to the provided Bitcoin wallet address.
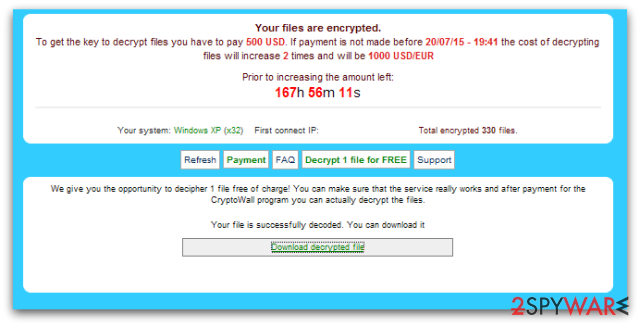
However, victims are warned that if they do not pay 500 USD/EUR until the given time, the size of the ransom will double up to 1000 USD/EUR. Additionally, victims who are considering paying the ransom can test the CryptoWall decryptor. They can decrypt one file for free.
The security experts warn that this might be the only file that you might manage to retrieve after the ransomware attack. This malicious program is created for swindling the money, and data recovery is just the matter of hackers’ conscience. Besides, some variants of malware are already decryptable. Thus, you just have to remove virus from the computer to use the free and safe software.
In 2021 we list 4 main versions of CryptoWall ransomware
Cryptowall 2.0. This ransomware is almost identical to original ranwomware: it encrypts files, warns the victim about their encryption and then asks to pay a ransom. It uses the RSA-2048 encryption algorithm to encrypt the files and seeks to make it victim pay either $500 USD, 500 EUR or 1.22 Bitcoin. To collect this money, virus generates a unique Bitcoin payment addresses for each of affected PC users.
What is important is that this variant uses its own TOR gateways, for example, tor4pay.com,pay4tor.com, and pay2tor.com. This virus also differs from the first version because when it encrypts files, it deletes the original versions of user's records.
Cryptowall 3.0. Just like other versions, this threat is used for collecting ransoms. This version spreads with the help of exploit kits, what means that it can get into the system easier than its previous examples. Once it infiltrates the computer, it encrypts needed files with the help of the same RSA-2048 algorithm and starts asking the money.
The ransom note of this virus claims that the victim has to pay a ransom of 1.22 Bitcoins or $500 within seven days. What is more, the third version adds a .aaa extension to the filenames of encrypted data.
Cryptowall 4.0. Also known as HELP_YOUR_FILES ransomware, this virus is filled with several features that haven't been seen previously. One of them is the ability to encrypt those files that have already been encrypted by the user. Also, it can disable you from using a System Restore and, just like each of previous variants, can also delete all Shadow Volume Copies [1]. However, now this updated version asks to pay $700 in exchange for the decryption key.
Cryptowall 5.1 uses the same encryption technology as previous versions. Specifically, files encrypted with AES-256 pose a bigger challenge for IT experts. Furthermore, the ransom note is presented in the Italian language so users residing in this region are suspected to be the primary target. It also sets 48-hour limit to transfer the files.
The authors of this malware present the mail address – cryptowall51@sigaint.org – for public communication. Another peculiarity of this threat is .locked appended file extension. Even if this cyber menace has assaulted your device as well, do not nurture big expectations that hackers will transfer the files even if you remit the payment.
CryptoWall imposter detected: Smrss32 ransomware virus
Envying the success of ransomware, many hackers attempt to generate as powerful file-encrypting malware as this one. Newly detected Smrss32 ransomware tries to deceive users into thinking that it is another version of this menacing cyber threat. However, such deception was quickly brought into the daylight by Michael Gillespie, a ransomware researcher.
Though it managed to encode more than 6 000 file types and wheedle out money from several victims, it has significant flaws [3]. Therefore, IT experts are working on the decryption tool. Since the threat pretends to be a version of CryptoWall, it attaches .encrypted to the affected files. The ransomware is known to be using AES encryption method. If you have been attacked by this virus as well, make sure to remove it first before attempting file recovery.
Victims of ransomware are not willing to pay the ransom
The original version has 2.0, 3.0, 4.0, and 5.1 variants. Version 2.0 was updated at the end of 2014. It is capable of generating unique payment addresses for each of the victims. What is more, it has authentic gateways to TOR and uses the secure deletion method that doesn't allow to use recovery tools while trying to decrypt important files.
Version 3.0[4] was released in January 2015. It seems that it is capable of encrypting new file names (HTML, PNG, TXT, URL), Soon afterward, version 4.0[5] was released in spring and 5.1 in winter of 2016. However, this illegal business does not seem to be very profitable.
During its rampage on the Internet, it has earned more than $325 billion dollars worldwide.[5]. However, specialists estimate that one of the latest versions CryptoWall 4.0 managed to collect only $18 billion dollars in comparison with other versions of the cyber infection.
Moreover, the number of sent malicious emails with the ransomware dropped significantly as well – 7.2 million in contrast to 36,114. At first glance, such decrease might only suggest the withdrawal of the virus from the ransomware market. However, it was only a diversion.
On July 27, 2016, the medical center in New Jersey[6] reported that their database was hacked and more than 20 000 records of patients names, addresses, and credit card numbers and other confidential information was encrypted.
Spam emails, infected ads, exploit kits and other strategies are used in ransomware distribution
Cyber criminals used four main methods to spread ransomware and infect devices:
- malicious spam emails;
- exploit kits;
- malicious ads;
- malware.
Malicious spam emails are traditional distribution method that allows attaching malware payload to the legitimate looking email. Malsam campaigns with CryptoWall typically included a zip archive that downloaded ransomware into the computer as soon as a victim opens it.
Thus, users should stay away from unknown emails that urge to open attached files. Bear in mind that ransomware might be included in Word, PDF or other legit file formats. Thus, before opening any attachment sent from unknown senders, you should check the security of a file using online scanners.
The second method used in malware distribution is exploit kits. Criminals used Rig, Nuclear,[7] and Angler[8] exploit kits that take advantage of three vulnerabilities in Java and Adobe Flash Player:
- CVE-2012-0507,
- CVE-2014-0515,
- CVE-2014-0556.
Exploit kits were injected into both legitimate and malicious websites. If a user visits a corrupted website, she or he is redirected to site with an exploit kit which immediately checks the system for security vulnerabilities and installs malware if possible. Thus, it is highly recommended to install all available updates to avoid ransomware attack.
Additionally, malware has been noticed spread via malicious ads that were delivered on the popular and entertainment websites, such as MSN, the New York Times, BBC, etc. According to the security experts, it was the largest ransomware campaign back in 2016 when criminals took advantage of Angler exploit kit.[9]
Lastly, ransomware might infiltrate computers if they have been already infected with other malware. It was detected that two malicious programs – Downloader.Upatre and Trojan.Zbot – were used for downloading ransomware into computers.
Therefore, users are advised to install professional anti-virus software to protect their PCs from cyber threats. However, if you suspect that your device might have been infected, you should check the system’s security and wipe out all malicious components immediately.
Delete ransomware from the computer and recover your files
To remove ransomware virus from the computer without causing damage to the system, you have to use reputable malware removal software, for example, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. However, security software might be impossible to install or run due to the ransomware attack.
In order to bypass these problems, you should disable the virus first. For that, you have two options. You can either reboot system to Safe Mode with Networking or apply System Restore. Both of the methods are explained below.
However, do not forget to run a full system scan once you disable the virus. Once you preferred anti-malware tool deletes the cyber threat, you can think of data recovery. If you have backups, you can use them. Otherwise, you can try decryptor (if you were hit by a decryptable version of the virus) or try third-party tools. The recovery file is given below.
Getting rid of CryptoWall virus. Follow these steps
Manual removal using Safe Mode
Virus might block the access to your antivirus software or try to prevent you from its removal in some other ways. When in such situation, do not panic and follow the instructions below.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove CryptoWall using System Restore
Our experts have prepared the guide below to help you decontaminate the virus and carry out its removal smoothly. Scroll below to learn about its steps:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of CryptoWall. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove CryptoWall from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by CryptoWall, you can use several methods to restore them:
The effectiveness of Data Recovery Pro
There have been released decryption software for the original version of ransomware, but as new versions of the malware have emerged, the decrypter might not work. However, virus researchers are still working on it. Thus, you might try using Data Recovery software to retrieve some of your files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by CryptoWall ransomware;
- Restore them.
Applying Windows Previous Versions feature for the recovery of files encrypted by Ransomware
If you are infected with a version of CryptoWall on which our provided decrypter does not work, you may try the recovery using Windows Previous Versions feature. We explain how to use this tool here:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer as a solution to file recovery:
As we have mentioned, you can use free tool to unlock files encrypted by Ransomware. Nevertheless, some of the virus versions may be resistant to this decryption method, thus, software like Shadow Explorer may come in handy. Try this technique out following steps below.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
CryptoWall Decrypter
Using this free decryption tool might give you a chance to recover the files.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from CryptoWall and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ CryptoLocker. Wikipedia. The free encyclopedia.
- ^ Zondervirus. Zondervirus. Security news.
- ^ Catalin Cimpanu. Smrss32 Ransomware Targets a Whopping 6,674 File Extensions. Softpedia. Free Downloads Encyclopedia.
- ^ John E Dunn. CryptoWall 3.0 – the most succcessful malware in history is not unstoppable. ComputerWorld. UK Business technology and IT Management News.
- ^ Jeff Stone. Cryptowall 4 Is In The Wild, After Previous Versions Extorted $325 Million From Ransomware Victims. International. Business Times. Business News, Technology, Politics.
- ^ Kayla Thrailkill. Two More Medical Facilities Infected With Ransomware. PC Pitstop TechTalk. PC tech, tips and tricks.
- ^ Michael Mimoso. Nuclear Exploit Kit Spreading Cryptowall 4.0 Ransomware. Threatpost. Security news.
- ^ Paul Ducklin. Angler exploit kit rings in 2016 with CryptoWall ransomware. Naked Security. Computer security news, opinion, advice and research.
- ^ Graham Cluley. Crypto-ransomware Spreads via Poisoned Ads on Major Websites. Tripwire. Advanced threat detection and file integrity monitoring.





















