CryptoLocker (Removal Guide) - Mar 2021 update
CryptoLocker Removal Guide
What is CryptoLocker?
CryptoLocker – an infamous ransomware virus that was stopped by the Operation Tovar
CryptoLocker is ransomware that encodes files and asks for victims to pay up in the given time. This is a file locking virus that was active from September 2013.[1] It attacks Windows machines via Gameover Zeus botnet[2] and encrypts files using RSA & AES ciphers. As soon as data is encoded, hackers ask for $100 to $300 ransom payment in order to retrieve the decryptor for the unusable files.
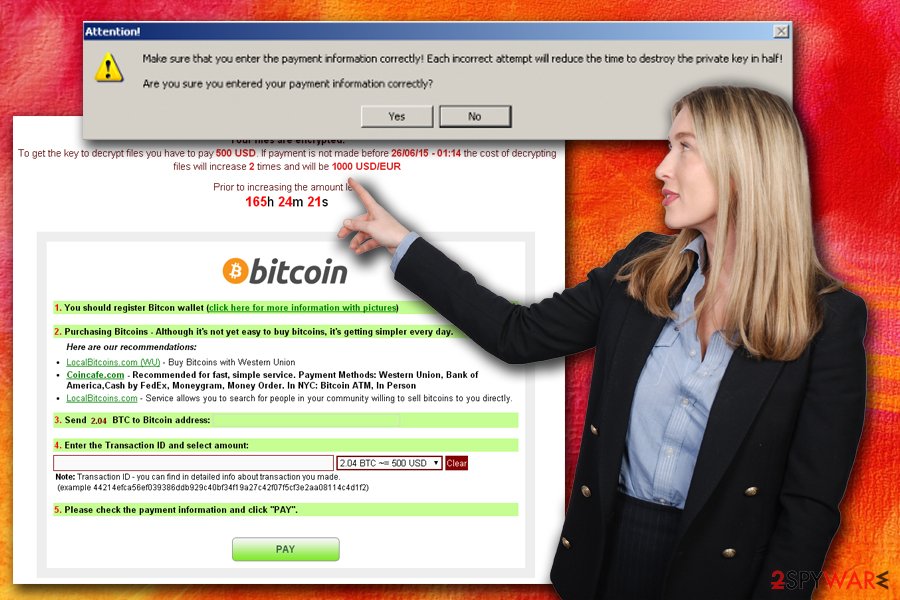
The ransom note is displayed in a “CryptoLocker” program which also explains that victims only have 72 hours to recover their files. If the ransom is not paid using MoneyPak or Bitcoin transfer during that time, the key is destroyed and access to data is lost permanently.
| SUMMARY | |
| Name | CryptoLocker |
| Type | Ransomware |
| First spotted | September 5th, 2013 |
| Taken down | June 2nd, 2014 |
| Taken down by | Operation Tovar, organized by the FBI and Interpol |
| Encryption algorithm | RSA & AES |
| Ransom demanded | $100-$300 |
| Ransom payment rate | 1.3% which equals to $3 million in profit |
| Decryption | Original version decryptable (as well as few others) |
| Elimination | Download and install FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. Do not attempt manual removal |
CryptoLocker virus was discontinued on June 2nd, 2014, when Operation Tovar[3] took down the Gameover Zeus botnet. The security firm gained access to the database used by hackers to store all decryption keys.
This allowed users to retrieve their data without paying the ransom. Since then, many other versions of the virus emerged, but they are not related to the original one. If you get a message that your files are encrypted by CryptoLocker, it is most likely other ransomware, such as TorrentLocker.
The main goal of Cryptolocker is to infiltrate your computer without your knowledge. For that, malware relies on seemingly harmless email messages. These messages typically contain malicious attachments which carry the payload of the ransomware. Once the victim is tricked into opening it, the virus infiltrates the target PC system, encrypts victim's files and displays a ransom note which is displayed below.
No matter that it belongs to the same category as FBI virus, Police Central e-crime Unit virus or Department of Justice virus, this virus tries to convince its victims that they have to pay a ransom by encrypting their personal files. CryptoLocker[4] is the file-encrypting ransomware, so it uses RSA public-key cryptography to lock the following file types on victim's PC:
3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, srf, srw, wb2, wpd, wps, xlk, xls, xlsb, xlsm, xlsx.
As you can see, this list is full of widely used files names, such as doc, xls and similar. To restore them, Cryptolocker ransomware asks you to pay a ransom via Moneypak, Ukash, cashU, or Bitcoin. Typically, this threat asks from $100 to $300, but the price can be increased any time soon.
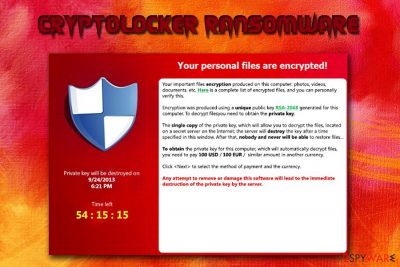
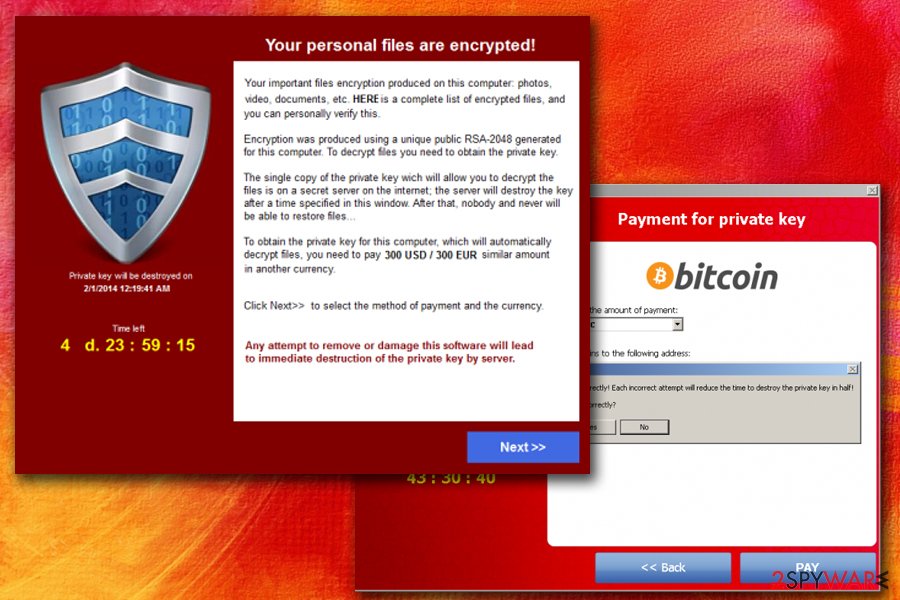
According to the warning message, which is typically displayed by this threat, people have only a certain amount of time to pay a ransom and recover the connection to their files. Cryptolocker leaves the so-called ransom note, which showcases such information:
Your personal files are encrypted!
Your important files encryption produced on this computer: photos, videos, documents, etc. Here is a complete list of encrypted files, and you can personally verify this.
Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt files you need to obtain the private key.
The single copy of the private key, which will allow you to decrypt the files, located on a secret server on the Internet; the server will destroy the key after a time specified in this window. After that, nobody and never will be able to restore files…
To obtain the private key for this computer, which will automatically decrypt files, you need to pay [specified amount of money in EUR or USD] similar amount in another currency.
Click To select the method of payment and the currency.
Any attempt to remove or damage this software will lead to the immediate destruction of the private key by server.
Fortunately, Cryptolocker cannot harm those who have been backing up their data and making extra copies of their files. If you have copies of your photos, business documents, and other files, you don't need to pay a ransom. You just need to remove this ransomware from your computer and prevent additional damage.

For Cryptolocker removal, we highly recommend using FortectIntego, which has been showing great results when eliminating files of this virus. For restoring your files, we kindly ask you to read data recovery options provided below the article.
However, it seems that frauds have decided to ease the rules for victims who choose to pay the ransom but simply cannot gather the fixed amount of money within the specified amount of time. Typically, when the anti-virus software deletes the ransomware, the victim can no longer pay the ransom.
Therefore, the latest versions of CryptoLocker have a new feature to change the desktop's wallpaper when the anti-virus detects the threat and display a message on the screen informing the victim where to download the ransomware again in case he or she still wants to buy the decryption software.
Although we highly recommend not paying the ransom, we understand that some companies might not be able to survive without personal data that has been stored on the compromised computers, so in such cases, paying the ransom might be the only chance to evolve the business. Again, we remind you that we do not recommend paying up. Keep in mind that you can never be sure whether criminals provide working decryption tools!
Cyber criminals use rely on malicious spam emails to spread ransomware
CryptoLocker is considered as one of the most efficiently distributed crypto-ransomware viruses and, speaking of its distribution, we have to say that authors of this virus combine several different techniques to spread the virus.[5] It has been noticed that they use both old and new distribution techniques, failing to comply with any moral norms.
According to experts, Cryptolocker virus is spread using officially-looking emails, fake pop-ups, and similar techniques. Earlier, ransomware has been distributed via hideous email letters that contained malicious attachments, malware-laden ads, which advertise programs or updates that actually contain the virus executive file, or exploit kits, which allowed crooks to infect victims' PCs by exploiting their computers' vulnerabilities.
Beware that this threat can infiltrate your computer thru fake pop-up that claims that you need to update your Java, Flash Player or similar program, so make sure you install these programs from their verified developers' sites, not from some suspicious third-party sites.
On September 2016, several new ransomware distribution techniques have been spotted. The first one is based on malicious emails posing as letters from electricity supplier VERBUND. This company is not related to these scammers in any way – they just use a reputable company's name to convince users to click on malicious links or open infectious email attachments containing CryptoLocker ransomware.
The message subject is Detailaufstellung zu Rechnung Nr. [numbers]. If you have received such letter, delete it immediately without clicking on links included in the message or opening attachments it contains!
The second ransomware distribution method that has been discovered is a filthy and hideous way to trick the user and force him or her to open the malicious file containing the virus. Scammers pose as employees of healthcare companies and send deceptive emails that can cause a heart attack on the victim. They deliver a bogus blood test report, stating that the victim might be suffering from cancer due to the lack of white blood cells.
The message asks to print out the blood test results that are in an attached document and bring these to the family doctor ASAP. Such news can make anyone panic, and forced to open the attached document without even thinking that this is just a bait. When the miserable victim opens the attachment, the ransomware takes control over the system and encrypts all victim's files without any remorse. As you can see, cyber criminals can go very low because all they care about is money.
12 Versions of Cryptolocker ransomware virus still active in 2021
Crypt0L0cker virus
Crypt0L0cker virus is one of the file-encrypting viruses that is capable of infiltrating computers thru fake Java updates or thru infected email attachments. After encrypting victim's files, this virus adds .encrypted or .enc file extension to each of them and starts showing a warning message asking the victim to pay the ransom.
This virus was first spotted in 2015. However, several years later it is still actively infecting computer users. Crypt0l0cker 2017 version demands 2.2 Bitcoin for giving a user a chance to decrypt encrypted files. Please, do NOT pay the ransom and use a guide below to fix your computer. You can always recover your files from backup for free.
CryptoLocker-v3
CryptoLocker-v3. When infected with this ransomware (you can download it after clicking on the fake popup that says that you need to update your Java or Flash Player), you can expect that it will block the most of your files.
For encrypting the files, this threat uses RSA-2048 (a unique public key) and asks 1 BTC ransom which was equal to $350 USD in 2015. Making this payment is the same as supporting the scammers and their future crimes, so you should never do that. This malware uses .crypted file extension which is added to every file it encrypts.
Cryptographic Locker
Cryptographic Locker is very similar to CryptoLocker ransomware. It lets its victim know what files it encrypted by adding .clf file extension to every file it encrypts. All these files are saved in %Temp%\CryptoLockerFileList.txt. Right after appearing on the Internet, this ransomware was asking 0.2 BTC ransom in exchange for the decryption key which is needed for recovering files.
During its active distribution, the amount of ransom was equal to $100. However, as well all know, the price of bitcoins keeps changing. If you happen to get infected with this malware, please, do NOT pay the fine because there is no guarantee that this will help you to recover the connection to your files. Instead of doing that, you should use a guide below.
PCLock ransomware
PCLock ransomware is another ransomware that tries to scare its victims by encrypting their files. This procedure is typically initiated with the help of XOR encryption. Fortunately, it is not as aggressive as the original CryptoLocker version, so you should be capable of eliminating it by removing its main file WinCL.exe and other files with the help of security software.
Please, do NOT pay 1 bitcoin ransom which is required to be paid in the ransom note called last_chance.txt for unblocking encrypted files. After you remove PCLock from your computer, you can use the decryption tool invented by security experts for unblocking encrypted files.
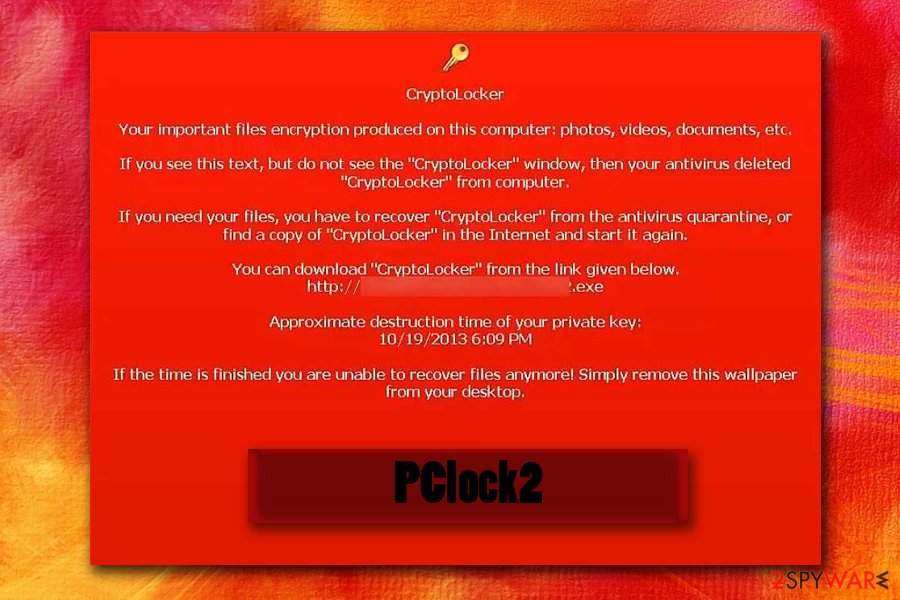
CryptoTorLocker2015
CryptoTorLocker2015 is capable of infecting Windows OS and Android OS. Once it does that, it uses XOR encryption for blocking victim's files. If your system is filled with precious photos or business documents, you can lose them. Infected files are typically marked by .CryptoTorLocker2015 file extension. You should also find the ransom note called as HOW TO DECRYPT FILES.txt on your desktop.
Fortunately, Android users need only to uninstall the affected application, which was used for downloading CryptoTorLocker virus to their computers, to remove this virus from their devices. Windows OS users are recommended using reputable anti-virus or anti-spyware software for CryptoTorLocker2015 removal.
Crypt0 ransomware
Crypt0 ransomware was discovered in September 2016. This ransomware variant also attempts to use a part of CryptoLocker's name to seem scarier than it is. This version appends ._crypt0 suffix after the original file name, while other viruses add the extension after the original file extension.
This ransomware leaves HELP_DECRYPT.TXT ransom note, which informs the victim about the attack and asks to use contactfndimaf@gmail.com for data decryption instructions. The virus is a foolish copy of CryptoLocker and can be decrypted using this free Crypt0 decryption tool.
Il tuo computer e stato infettato da Cryptolocker! ransomware
Il tuo computer e stato infettato da Cryptolocker! ransomware virus is yet another version of CryptoLocker which is aimed at Italian-speaking computer users. This version of ransomware asks for a smaller ransom than other viruses – it requires “only” 130 eur from its victims. However, that does not mean that victims should pay the ransom.
Just like its predecessor, this ransomware changes file extensions (it uses .locked file extension) and gives its victim a specified amount of time to pay up. Currently, malware researchers keep silent as there is no free decryption tool available; however, such tool might show up in the future.
CryptoLocker 5.1 ransomware virus
CryptoLocker 5.1 ransomware virus was released in 2016. Since its first appearance, it has been working on infecting Italian users. Alternatively, it has been alternatively known as Il tuo computer e stato infettato da Cryptolocker! threat. Though it attempts to disguise under the name of notorious cyber menace, IT experts still suspect that it is not so powerful as the original version.
Speaking of the current virus, it appends .locked file extension and demands 250€ in exchange for the decryption key. The transaction is expected to be made within 48 hours. Brush aside any thoughts to transfer the money and concentrate on the elimination.
Cryptolocker3 ransomware virus
Cryptolocker3 ransomware virus is an imposter-type malware which can also be called as lock screen ransomware [6]. Such viruses do not actually encrypt the computer files but prevent their victims from accessing them and using the regular computer functions. However, after several months of functionality, Cryptolocker3 entered another sub-section in which malware acts like the original ransomware virus[7].
This parasite uses XOR encryption algorithm and appends .cryptolocker file extension. There is currently no safe decryption tool for the locked files, but we can assure you that the experts are working on it actively and you can expect your files to be decrypted in the future. In the meanwhile, you need to remove this parasite from your computer without any delay.
MNS Cryptolocker
MNS Cryptolocker is yet another ransomware virus which uses Cryptolocker's name. While there is no evidence that it is related to the notorious cyber infection, it does not mean that this malware is less harmful. Once it encrypts victim's personal files, ransomware drops its ransom note asking the victim to send 0.2 BTC ($180 USD) via Tor or other anonymous networks.
Virus does not append new extensions to the target files, so you become aware of the infection only when you try to open one of them. Unfortunately, this malware can eliminate shadow volume copies of the target files with the special command known as vssadmin DELETE SHADOWS /all /quiet. Because of this feature, victims find ShadowExplorer useless. The most interesting fact is that MNS Cryptolocker can delete itself from the system.
CryptoLockerEU ransomware virus
CryptoLockerEU ransomware virus was detected in January 2017. It appears to be a modified copy. The virus calls itself CryptoLockerEU 2016 rusia, which gives an idea that it was developed in 2016 by Russian hackers. During the data encryption procedure, the virus encodes files using a RSA-2048 algorithm and gives each file a new extension .send 0.3 BTC crypt.
The name of the ransom note is supposed to look like that: РАСШИФРОВАТЬ ФАЙЛЫ.txt. However, due to an error in virus' source code, it appears as ĐŔŃŘČÔĐÎ ŔŇÜ ÔŔÉËŰ.txt. Currently, files cannot be decrypted. Victims should use backups or wait for free decryption programs that malware researchers might release soon.
CryptON
Cryptolocker Portuguese ransomware or CryptON is the latest variant of CryptoLocker-related ransomware. Some believe that it may be released by the same group of hackers because it uses a similar source code and displays typical nature of CyptoLocker on the infected computer.
The most interesting fact is that this virus is aimed at Portuguese-speaking users since the ransom note and the ransom payment interface are presented in this language. In particular, the ransom note used by this malware is called COMO_ABRIR_ARQUIVOS.txt which essentially means “how to access your files” in English. Likewise, the encrypted files are renamed in the following manner: [file_name].id-[victim’s ID]_steaveiwalker@india.com_.
To retrieve access to the files, the victims are demanded to pay 1 BTC. By no means should you pay the hackers! Instead, remove CryptON CryptoLocker and try to recover your files using our recommended data recovery options.
Suggestions on how to keep your files safe from crypto-virus
If you want to stay safe, you should never trust misleading ads that pretend to be helpful because the only thing what they do is spread viruses and useless programs. Also, make sure you delete spam and double check every email that was sent to you by unknown senders. Besides, don't forget to disable hidden extensions (if you are using Windows OS)[8] and, to avoid the loss of your files, you should think about their protection.
The first thing that you should do is to download a reputable anti-spyware on your computer. We recommend using FortectIntego. In addition, make sure you perform backups as frequently as possible because this could help you to recover your encrypted files.
Finally, you should use such solutions as Google Drive, Dropbox, Flickr, etc. when trying to protect your extremely important files. However, keep in mind that this powerful virus might be able to access these online storage places via your Internet connection and encrypt these files, too.
Therefore, it is recommended storing data backups on removable storage devices such as hard drives or USBs. Unfortunately, if you are infected with this ransomware right now, you should know that there is no official Cryptolocker decrypt tool yet. Nevertheless, you can check the guide given on the second page of this post and recover your files with some special tools. Don't forget to remove ransomware before recovering your files because it may disable them again!
Delete ransomware with professional malware removal program
Please, do NOT pay a fine because this doesn't guarantee that you will receive a key required for files' decryption. In order to remove CryptoLocker virus from the system, you need to scan your computer with FortectIntego or SpyHunter 5Combo Cleaner.
If your anti-spyware or anti-malware tool does not start because the ransomware is blocking it, you need to follow special tips that we prepared to help you with this procedure. CryptoLocker removal instructions are provided at the end of this post. You can also find informative data recovery instructions down below.
Victims of Cryptolocker ransomware can use a free online tool created by FireEye and Fox-IT to decrypt files compromised by this malware – decryptcryptolocker.com
Frequently Asked Questions related to Cryptolocker in 2021
Question: My PC has been infected by Cryptolocker ransomware. The infection has also affected my sd memory card in which I've stored important picture. I'm reading now a notification saying that I have a certain amount of time to pay the ransom, but there is no specific period indicated. Does anybody know how long files remain available to recover after they are affected by ransomware?
Answer. We feel responsible for answering your question ASAP to warn all people in advance. Paying the money for the decryption key is a huge mistake which can result in money and data loss. So, please, don't risk that much.
The first thing that you have to do after receiving a ransomware notification is to run a full system scan with a reputable anti-spyware (the list of them is given below) and remove Cryptolocker virus ASAP. After that, check whether your files still cannot be accessed. In this case, install data recovery tool (e.g. Photorec, R-Studio) or use file backups.
Question: I've been hit by Cryptolocker virus twice! I suppose I was dealing with different versions. Nevertheless, could you please tell me how could I prevent this in the future? It's painful to pay $500 to these bastards. However, I had to do so since nothing else has helped. Please, advise.
Answer. It's a pity to hear that you have been attacked by ransomware twice. We assume that the reason for a repeated attack might be inappropriate Cryptolocker removal. Anyway, now you are asking how to protect your computer from this threat. Honestly, there is no hundred percent reliable method that would give you zero chances of getting infected with any ransomware.
Nevertheless, there are several tips that we can give for you. 1. Stay away from illegal websites. 2. Do not open suspicious emails, especially those containing attachments. 3. Do not click on software update prompts that pop up on your screen out of nowhere. 4. Do not visit websites filled with adult content. 5. Finally, keep a reliable anti-spyware installed on your computer and update it regularly.
Question: I've just been browsing through the websites I regularly visit, and suddenly a pop-up window locked my screen stating that data stored on my computer has been encrypted and that I have to pay the ransom. Is this a joke or I have to pay $500 for getting rid of Cryptolocker?
Answer. Unfortunately, if the message that you've indicated has been brought by Cryptolocker ransomware, then it seems that your computer has been affected with ransomware. Probably you have already checked personal files stored on your computer and discovered that they are blocked. Nevertheless, you should NOT pay the ransom to get decryption code that is needed for unblocking locked files.
Although some users claim that they have been provided with a decryption key after sending the money, no one can guarantee that you will be the lucky one. Thus, instead of spending your money on nothing, install a reliable anti-malware (you can select one from the list below), delete Cryptolockerand try to recover data using data recovery tool.
Question: Please help! My files were locked by Cryptolocker virus last night, and I continuously receive a notification that contains instructions how to make the payment. I feel helpless as I cannot afford to pay such a big sum of money although pictures stored on my PC are worth millions for me. Can anyone help?!
Answer. Cryptolocker ransomware is a nasty infection. its developers only seek to earn easy money and frequently manage to do so. For you, as well as for the other victims of this ransomware, we want to highlight that paying the ransom will not solve the problem. There is no guarantee that your data will be restored.
Beyond that, making the payment will not help to remove ransomware. In order to fix your computer and restore data stored in it, you are recommended to install a powerful anti-malware and run a full system scan with it. Finally, you should either use file backups or data recovery software for getting your data back.
Question: Cryptolocker has stolen my data. However, some of the .doc, .pdf. and .jpg files were very important for me. Is there are a way to decrypt at least some pieces of data? Maybe there's a way to fix this issue manually?
Answer. Unfortunately, there is no way to get rid of Cryptolocker manually. There are only two ways to get decrypt data – either use backups or use a reliable file decryption tool, such as Photorec or R-Studio. Besides, in order to remove this threat once and for all, update or install a reliable anti-spyware and run a full system scan with it.
Getting rid of CryptoLocker. Follow these steps
Manual removal using Safe Mode
To remove this ransomware with Safe Mode with Networking, follow the steps below. Keep in mind that this ransomware is an extremely vicious virus which comes in a variety of different shapes. It is likely that some of these versions will try block you from running security software and remove it from the computer. If you happen to be in such situation, scroll down below to find guidelines how to eliminate this obstacle.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove CryptoLocker using System Restore
To get rid of CryptoLocker with System Restore method, please use this guide. Keep in mind that it is a serious threat that will not leave your computer without a fight. So, they may block antivirus scanners from initiating and purposefully crash these programs before they launch.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of CryptoLocker. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove CryptoLocker from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Although it might be possible to recover files encrypted by CryptoLocker malware by paying the ransom, we highly recommend you to forget this option. The decryption software might come bundled with more malicious files, or might not help you to retrieve your precious records at all. Additionally, if you paid, you would fuel up criminals' efforts and induce them to continue evolving and distributing this virus.
IMPORTANT. If you think that you have been infected by CryptoLocker, there is a great chance that you are mistaken. The original virus has been defeated several years ago and is no longer distributed. If the ransom note says that you are infected with this specific virus, it might not be true – some viruses pretend to be this fearsome ransomware just to frighten the victim. Besides, some fake versions of this malware can be decrypted.
We strongly recommend you to run a system scan to find out what is the actual name of the virus, or send us a question providing the name of the ransom note, file extensions added to encrypted files and maybe some pieces of information the ransom note contains. It would also be helpful to hear what kind of picture the ransomware sets on the desktop – all this data can help us identify what virus has affected your PC. Alternatively, you can take a look at these data recovery suggestions and choose the desired method to recover your files:
If your files are encrypted by CryptoLocker, you can use several methods to restore them:
Use Data Recovery Pro to recover your files
Many programs promise to recover your files after they get deleted, corrupted, or damaged in another way. We recommend using Data Recovery Pro – it might help you to recover some files. Instructions below will help you to start this program and scan the system for encrypted data.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by CryptoLocker ransomware;
- Restore them.
Use Windows Previous Versions method to recover individual files
If your personal files have been distorted by this malicious ransomware, try to rescue a few of them by taking advantage of Windows Previous Versions feature. Sadly, this method is only effective if System Restore function has been enabled on the system.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
CryptoLocker decryption tools
If your PC has been infected by a version of CryptoLocker, use the appropriate tool to decrypt them. Below we provide a list of free decryption tools capable of restoring encrypted files:
- Files locked and _crypt0 file extensions added? Then use this Crypt0 ransomware decryption tool.
- Files encrypted and have .CryptoTorLocker2015! file extensions now? CrypTorLocker2015 decrypter can be downloaded from here.
- PCLock ransomware does not append specific file extensions, but you can easily identify this virus by running anti-malware software. Files can be decrypted with this PCLock Decrypter.
Victims of Cryptolocker ransomware can use a free online tool created by FireEye and Fox-IT to decrypt files compromised by this malware – decryptcryptolocker.com
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from CryptoLocker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Matthew Hughes. CryptoLocker Is Dead. MakeUseOf. Technology website, focused on bridging the connection between users, computers, devices and the Internet through education.
- ^ Forrest Stroud. GameOver Zeus. Webopedia. The web encyclopedia that features more than 10,000 entries in its technology definition database.
- ^ Meaghan Molloy. Operation Tovar: The Latest Attempt to Eliminate Key Botnets. FireEye. Cyber threats researchers.
- ^ Nino Fred P Gutierrez. Ransom.Cryptolocker. Symantec. Security Response Blog.
- ^ John Zorabedian. Anatomy of a ransomware attack: CryptoLocker, CryptoWall, and how to stay safe (Infographic). Sophos Blog. Security made simple.
- ^ David Bisson. New tech support scams mimic ransomware, lock users' computers. Graham Cluley computer security news.
- ^ Jakub Kroustek. Crypt888 Ransomware Has Facelift as It Seeks Fresh Victims. AVG antivirus news sites.
- ^ CryptoLocker: What Is and How to Avoid it. Panda Media Center. All about Family safety, Malware and Internet security.





















