Picshot.xyz browser hijacker (virus) - Free Instructions
Picshot.xyz browser hijacker Removal Guide
What is Picshot.xyz browser hijacker?
Picshot.xyz is a browser hijacker that shows ads to users for monetization purposes

Everybody has certain habits and preferences when it comes to web browsing – users choose which browser to use, which websites to bookmark, and which extensions to add to improve the overall experience. Unfortunately, there are plenty of add-ons that are useless, and they modify web browsers' settings without even asking. These types of apps are usually referred to as browser hijackers, and Picshot.xyz falls right into that category.
Browser hijackers are commonly not installed intentionally, as they are commonly spread in bundles downloaded from third-party sources. Additionally, deceptive ads (fake updates or tech support scams) might also spread various potentially unwanted programs, some of which might even be malicious.
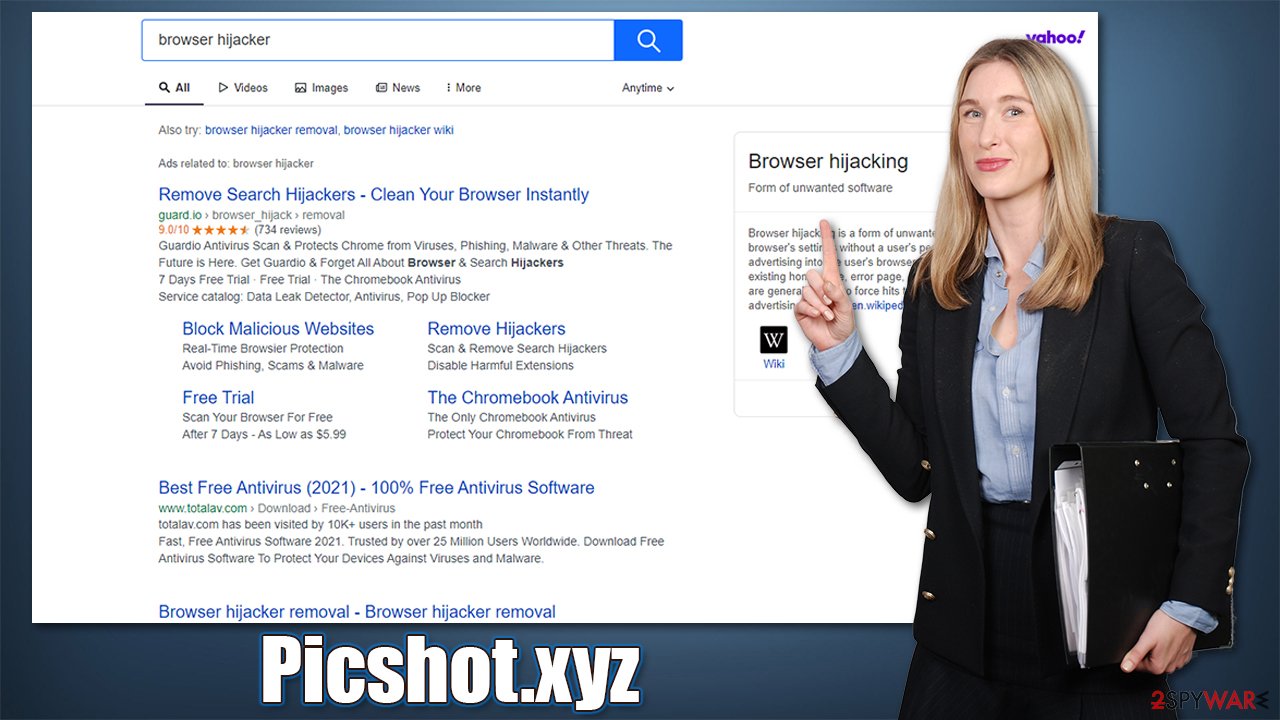
Once installed, Picshot.xyz changes the homepage of Google Chrome or another browser to its own. It also places a search bar in the middle to be used for searches. While it does not look like anything special or different, users would soon see that the provider and the results are no longer what they are used to be:
- Top results are filled with sponsored links[1] and ads
- A search provider has been changed to a different one, for example, Yahoo or Bing.
While this might seem insignificant, it actually changes the way people browse the web. They are more likely to click links they otherwise wouldn't and might even be tricked into installing useless software or subscribe to deceptive services. There are plenty of other reasons to remove the hijacker from the system – we explain in detail how to do that below.
| Name | Picshot.xyz |
|---|---|
| Type | Browser hijacker |
| Distribution | Software bundle packages, deceptive ads, fake update prompts |
| Symptoms | Unknown extension or application is installed on the system; homepage and new tab address are set to something else; a customized search engine is appended to the homepage; search results are filled with sponsored links and ads |
| Risks | Installation of other potentially unwanted programs, privacy risks due to information gathering practices, financial losses |
| Removal | To get rid of the unwanted browser extension, you should access the settings section of your browser. You should also check for other PUPs or malware with a powerful security tool |
| Optional steps | Cleaning your browsers is just as important as removing the extension that caused the unwanted ads and redirects. For that, check the instructions below or employ FortectIntego repair and maintenance utility |
How do browser hijackers work?
The deceptive infiltration methods of browser hijackers and similar unwanted apps are just the beginning. While it is true that hijackers are nowhere near as dangerous as Trojans, ransomware,[2] or other malware, they should not be ignored. They clog your browsers with unnecessary toolbars and changes to the search provider with one goal in mind – to insert ads into searches and make users click on them.
In the meantime, there are no useful features that are provided to end-users, even though it is commonly claimed otherwise – be it in the description of the app or within the name itself. For example, StreamingSearch, StreamSearchApp, or CoolStreamSearch might imply that some type of video streaming functionality is supported by the extension, while, in reality, there are no such function supplies. Instead, users' browser settings are changed and ads inserted.
These ads, while mostly harmless, might contain links to less secure or deceptive websites. Nonetheless, we strongly advise against clicking them and exploring sites' contents. Besides, the altered search provider is not something that most people are fond of.
When speaking of browser hijackers, we can not let them slide without mentioning the information-gathering practices. PUP authors commonly collect data in order to share or sell it with third parties, as well as produce more targeted ads. Here is an example of collected data:
- IP address[3] and ISP
- Technical device details, including unique device identifier (if applicable)
- Browser type, language, bookmarks, etc.
- Links clicked, websites visited, search queries
- Cookies, etc.
There is no pretense for a regular browser hijacker such as Picshot.xyz to remain on your system. therefore, you should proceed with the instructions below and remove it from your system for a better browsing experience.
Remove Picshot.xyz to restore your browser back to normal
Browser hijackers are usually not that difficult to remove, although it might be a bit problematic if the changes came up suddenly (i.e., the app was not installed intentionally). What makes matters worse is that the URL name does not always correlate with the browser extension or an application that initiated those changes. Besides, some applications simply go rogue suddenly and start engaging in activities they never used to previously; for example, they start showing excessive ads.
It is the easiest to perform Picshot.xyz removal with the help of powerful anti-malware software such as SpyHunter 5Combo Cleaner. During the scan, security software can find and eliminate all the malicious and unwanted components for you. It can also check for other PUPs and more dangerous threats, as malware tends to run in the background without emitting any symptoms.
Of course, if you know which extension is causing troubles, you can remove it just like any other one. Go to Settings > More Tools > Extensions or simply right-click on the extension icon at the top-right corner of the browser.
A browser hijacker can also be installed as a program on the system level. In this case, you need to access the relevant section on your computer and uninstall it from there. Here's how:
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
After you eliminate the unwanted app, you should not forget your browsers – especially if it was an extension. Browser hijackers use cookies and other technologies to track users, even after the app itself is already gone. Besides, some PUPs might continue showing ads and redirect to different providers until browsers are adequately cleaned.
If you want to skip this process, we recommend using FortectIntego to do this automatically. Alternatively, proceed with the instructions below:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
PUP distribution methods and how to avoid them
As we already mentioned, many people don't install potentially dangerous software intentionally, but they are rather tricked into doing so. Software bundling is the most prominent distribution method and has been used by many websites for many years now.
By itself, there is nothing wrong with offering users to try additional applications, although it can easily become a problem if users are not adequately informed about what is being offered or how to decline it. And it is precisely what third-party software distributors make use of – users' inability to read the installation instructions properly.
Websites and freeware authors do not receive revenue from purchases, so the operation needs to be monetized in order ways. There are a few options available, including in-app purchases or ads. Likewise, bundled software offers distributors and developers to increase the popularity of certain apps and receive payment for it. This is why so many sources tend to hide optional components within the installation installer, away from users' eyes. This scheme is called pay-per-install, and certain parties receive good money for it.
Unfortunately, this is where the practice becomes deceptive. While it is true that the optional software can be declined, it does not make it right that users need to search where to do that. For example, “Skip offer” buttons are commonly placed on the left side instead of the right (which is associated with proceeding with installation), offers are written in fine print, or pre-ticked checkboxes are used.
Also, Advanced or Custom installation mode is often discouraged, and users are urged to use Recommended settings, which would automatically include optional installs. Thus, always pick the former and never rush through the installation steps, all while making sure all the deals and offers are declined on the way.
How to prevent from getting browser hijacker
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Sponsored link. PCMag. The Latest Technology Product Reviews, News, Tips.
- ^ Ransomware. Wikipedia. The free encyclopedia.
- ^ Cory Mitchell. IP Address. Investopedia. Sharper insight, better investing.








