You’ve made the 16.39-billionth search! scam (fake) - Free Instructions
You’ve made the 16.39-billionth search! scam Removal Guide
What is You’ve made the 16.39-billionth search! scam?
“You’ve made the 16.39-billionth search!” is a scam message that seeks to extort your personal info
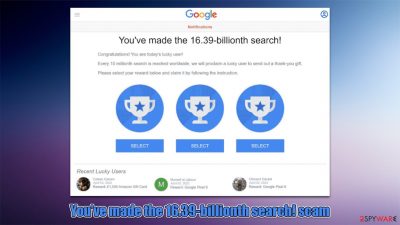
You've made the 16.39-billionth search is a scam message you might come across after you click a malicious link on some other site. Alternatively, redirects could be caused by adware or other malware installed on the system.
Once redirected, users are presented with the message which claims that they have been selected by Google to participate in a giveaway and that they are allegedly lucky to have encountered this page. In reality, Google has nothing to do with it, and the creators of the message have some evil intentions.
The main goal of scammers behind the “You've made the 16.39-billionth search” scam is to make users provide their personal information, download potentially dangerous software, or subscribe to various useless services. Quite often, websites that host the scam also redirect users to other dangerous places, so the more users interact with it, the worse off they might be later.
If you have encountered this scam, please do not interact with any of the promoted components. Instead, make sure you perform adequate checks on your system and clean your browsers accordingly. We explain everything below.
| Name | You've made the 16.39-billionth search scam |
| Type | Scam, phishing, survey scam |
| Infiltration | Adware could be the cause of redirects to scam websites; clicks on malicious links on other websites |
| Scam content | Scammers claim that the user has been selected to participate in Google's survey for a free gift |
| Risks | Installation of PUPs or malware, sensitive information disclosure, financial losses |
| Removal | Check your system for adware with SpyHunter 5Combo Cleaner and do not interact with scam content; if you have disclosed your personal details, expect more phishing attacks |
| System fix | If you want to clean your web browsers quickly and/or fix virus damage automatically, we recommend using the FortectIntego repair tool |
The scam scheme
Social engineering is the art of psychological manipulation of users who are less aware of online fraud. Quite often, scammers use familiar features, logos, and even messages that are identical or similar to those users have seen before in order to confuse them easier.
Google is one of the most prominent names out there, and there's hardly any user who ever used the internet who wouldn't know that name. Scammers use this popularity to their advantage and create fake websites that mimic the company, even though it has nothing to do with these fake sites.
“You've made the 16.39-billionth” search is not the first scam that crooks have created so far. We have previously observed “You've made the 5-billionth search” and “You've made the 9.68-billionth search” messages before, although the message barely differs. It is important to note that there could be a myriad of websites hosting these scams, including Rizereward.com, Wirietheppre.com, Wardoprize.com, Flskon.click, Suddenwomencaptain.xyz, and others.
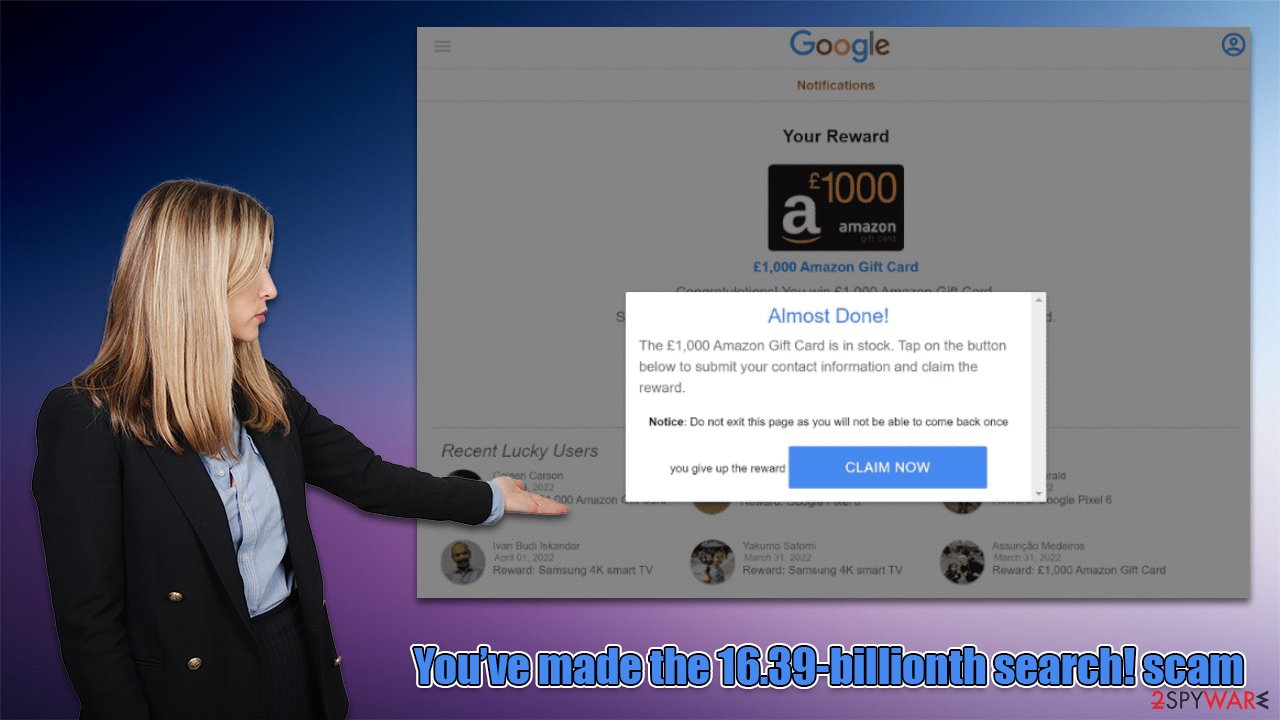
The main goal of threat actors is to convince visitors that a legitimate company, namely Google, is offering them free gifts – all they need to do is pick one. Here's the message that people receive upon entry to a site that hosts the scam:
You've made the 16.39-billionth search!
Congratulations! You are the lucky winner!
Every 10 millionth search is reached worldwide, we will proclaim a winner to send out a thank-you gift.
Please select your lucky prize below and claim it by following the instruction.
After selecting one of the items, it would be revealed that users are eligible to receive an iPhone, PlayStation, or some other valuable gift. In the end, users would be asked to reveal their personal information, which can include phone number, home address, email, or even credit card information.
Those who provide these details would later realize that the promised gift is fake, as it would never arrive. Please do not give in to these scams, as you might suffer from serious privacy issues or even be a victim of identity fraud.[1]
Removal instructions
If you have encountered “You've made the 16.39-billionth search!” along with other suspicious websites, there might be adware or malware installed on your system. Combining both manual and automatic elimination methods would bring the best results. Thus, we recommend you check the instructions below.
Uninstall programs
Some unwanted programs might be installed on the system level. To uninstall them from Windows, you should reach the Control Panel section and then go to Apps and Features, which would allow you to uninstall suspicious programs easily.
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
If you are not quite sure about this step, you don't have to do it, as you might end up uninstalling a useful program by accident. In this case, we highly recommend running a scan with powerful security software, such as SpyHunter 5Combo Cleaner or Malwarebytes instead. This process would ensure that all the most aggressive unwanted, and malicious software is eliminated
Remove extensions and clean your browsers
Adware and other potentially unwanted programs can be installed as extensions, which operate via the browser. In this case, you can remove them by clicking the “Extensions” button or accessing browser settings.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open the Mozilla Firefox browser and click on the Menu (three horizontal lines at the window's top-right).
- Select Add-ons.
- Here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Stop notifications on Safari Stop notifications on Safari]()
The next step is to ensure that cookies and other leftover files are eliminated from the system as well. Cleaning web caches can be extremely beneficial, as it removes the trackers used by various third parties, prevents browser errors due to bugged[2] caches, and reduces the chance of dangerous session hijacking[3] attacks.
If you would like a quicker solution that would allow you to clean the browser and system automatically, you can opt for using FortectIntego. The app would also repair any damaged system sectors, which would stop crashes, errors, and similar issues that could arise after malware infections.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
How to prevent from getting adware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Identity fraud. Wikipedia. The free encyclopedia.
- ^ Software Bug. Techopedia. Professional IT insight.
- ^ Allie Johnson. Session hijacking: What is a session hijacking and how does it work?. Norton. Security research blog.












