Gmail virus (Virus Removal Guide) - updated Mar 2019
Gmail virus Removal Guide
What is Gmail virus?
Gmail virus – a term used to describe malware that gets into your system via the Gmail service

Gmail virus is a broad term that combines phishing attempts, scams, hoaxes and malware that can compromise victims' computers severely. Typically, the most dangerous factors are the obfuscated attachments that come in various formats, such as .doc, .zip, .html, or even .pdf. Once malicious macros are enabled, or the user is redirected to the server that hosts malware, the infection happens instantaneously. However, Gmail virus can be prevented when using extreme caution, in combination with Google's efforts to stop such dangerous attacks. For example, the industry giant introduced a feature that scans files for viruses inside the email. However, users reported that they receive a message “Gmail virus scanners are temporarily unavailable,” which usually arises when the internet connection is too slow.[1] When that fails, however, users reported that they got infected with a so-called Gmail Filter Virus – a threat that turns the infected host into a spam bot machine. Thus, users who recently spotted weird activities on their PCs after opening a Gmail spam message, it is highly likely that Gmail virus was installed on the device.
| Name | Gmail virus |
|---|---|
| Similar to | WhatsApp virus, Yahoo Powered, Chrome virus |
| Category | Malware, adware, scam |
| Spreads via | Infected email attachments, fake emails |
| Main dangers | The loss of personal information, infiltration of malware |
| Symptoms | System slow downs, crashes, redirects to fake websites, annoying ads |
| Elimination | Run a full system scan with FortectIntego and remove detected elements |
Gmail virus is closely related to Google Mail which is still considered as one of the best email service providers with more than 1.5 billion monthly active users (as of October 2018).[2] There is no wonder why cyber criminals target this virtual communication platform – there are hundreds of thousands of potential victims here.
The attackers target Google Mail users by sending them malicious file attachments in the form of .zip, .js or .word files. However, this email service provider has banned .JS[3] file attachments, preventing the attackers from infecting computers with Gmail viruses easily.
This, however, did not lower the number of ransomware victims anyhow – the attackers continued sending malware in other formats and didn’t even worry about this new restriction too much. They can simply pack the .JS file into a .ZIP now and bypass this restriction with ease.
Scammers can also compromise your account with Gmail virus by sending you fake Google Docs links. In May 2018, security experts noticed a new phishing attack[4] which was used to send thousands of fake messages to potential victims asking them to check the Google Docs file.
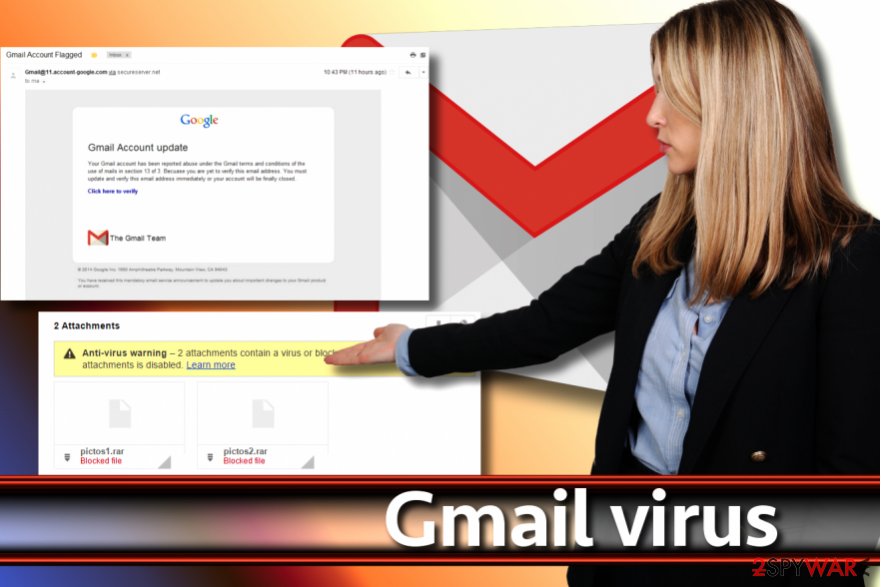
Clicking on the link redirected the victim to the Google security page asking to provide a permission for a virus in Gmail to manage one’s email account. Consequently, the virus used victim’s account to distribute itself to victim’s contacts. Such and similar scams are widespread, so make sure you are very careful with emails that you receive from people you don't really know.
Another technique, used by hackers, was compelling and, no surprise, efficient. The attackers distributed deceptive emails containing a fake Gmail attachment. The deceit lies in the message body. The email attachment looks real, although it is simply a well-designed and precisely-placed image with a hidden URL[5].
Clicking on it takes the victim to a phishing website that looks like a legit Gmail login page. Of course, after entering the login details, the victim’s account gets hacked.
It is a must to remove email virus from your computer as soon as you accidentally download it from your email account. If you are lucky, you might prevent it from causing damage to your system or infringing your privacy. For a successful Gmail virus removal, we recommend using FortectIntego software.
Gmail service failed to scan the attachment can result in Gmail Filter virus infection
As previously mentioned, some users encounter the problem when getting email attachments in their spam box or even inbox – “Gmail virus scanners are temporarily unavailable.” The error typically indicates a problem with internet connection speed – the online scanners simply can't connect, and Gmail virus scanner becomes unavailable.
Due to that reason, users proceed to open a (malicious) attachment. Unfortunately, that can result in a Gmail Filter Virus infection. The threat uses a sophisticated scheme to infect victims, modify Gmail Filter settings and then hide its tracks by deleting the malicious message altogether. Finally, it will send the copies of the infected emails to everybody on the address book automatically. This means that the infected host might not even know that these actions are performed using his or her Gmail account.

Therefore, you should make sure you scan your device for malware using reputable security applications like FortectIntego or SpyHunter 5Combo Cleaner. Gmail Filter virus can hardly be noticed, so a scan with anti-malware is recommended.
Avoid getting virus from your email inbox
We want to provide some general tips to avoid getting your account hacked or compromised. Some of these tips will help you to prevent ransomware attack, too. We also recommend you to check this guide on how to identify an email with a virus.
- If you are a user of this email service provider, be careful and do not trust suspicious messages that urge you to reset your Gmail password, upgrade your account or do something that requires entering your login details. This is a common trick used by frauds that seek to lure you into phishing websites with fake login forms. If you entered your login details in these websites, your account would be compromised instantly.
- Fraudsters have some favorite scamming techniques. Usually, they are the most active during certain yearly events, such as Black Friday or Tax season. They compose convincing emails asking the victim to open the attached file or link, offering to view “important documents/invoices/special offers/discount codes.” Unfortunately, these attachments/links are just a disguise that hides malicious content.
- In general, the main rule is to never open or interact with emails sent by strangers. You should always inspect the sender’s email address and check whether it looks legitimate or not. If it doesn’t, do not even consider opening the attached files or links. In fact, you shouldn’t click on the message body as well!
Frequently asked questions about Gmail malware
Below, we provide the list of most common Gmail virus forms that bother computer users. We have inserted actual user complaints about the virus. These are the common problems that people run into. We have answered these questions – we hope that they will help you to avoid or survive Gmail virus attack.
Question: Someone is sending emails from my email address. My friends say that I sent spam although I didn’t!
Answer: There are two scenarios in your situation. Your account might be compromised, but if you cannot find any of the messages in your Sent folder, it can mean that someone has spoofed your account. It means that your friends receive emails from someone who is forging the sender and making your email appear as the sender address or a reply-to address. We recommend you to perform Gmail Security Checkup to secure your account.
Question: My Gmail account was hacked, and I can no longer sign into it. How can I recover my account?
Answer: Dear visitor, the first thing that you want to do if your email account was hacked is to change your password. Second, fill out Google Account Recovery form.
Try to think of ways how your account was hacked. You may have provided your login details in a phishing website that looked like email login page, although it is also possible that your computer was compromised by a keylogger or a data-stealing Trojan that provided your logins and passwords to attackers. In such case, perform a thorough system check with anti-malware like FortectIntego.
Question: I opened a malicious file attachment that I opened via Gmail. As a result, my computer was infected with ransomware. I am disappointed – does this mean that Gmail virus’ filters do not work?
Answer: Dear visitor, Gmail virus’ filters are powerful; however, cyber criminals always find ways to bypass them – even if it is hard, it is possible to do so. For this reason, you can never feel too protected while exploring email messages, even if you are using the best email service in the world. Always stay careful and do not fall for cyber criminals’ tricks.
Distribution of Gmail virus
There are several common distribution techniques[6] that criminals use to distribute viruses via email. Usually, they pretend to be sending some legitimate files, such as receipts, invoices, subpoenas, reports, resumes, shipping information, or other documents that do not raise suspicions at all.
However, these documents often contain a Macros script that requires only one click on “Enable content” button to execute itself. As a consequence, the script downloads the malware to victim’s computer and automatically launches it.
Fraudsters also like to send malicious URLs to victims, asking to visit them for a specific purpose. It can look like a link to reset your password, view a document or a Dropbox file. Of course, clicking on such link and interacting with content behind it is what allows malware to infiltrate your computer.
Your email account can be compromised and used to send out spam if you use an unprotected computer that is vulnerable to malware attacks. An unprotected computer can be easily contaminated with Trojans, keyloggers, or other data-stealing viruses. The chance to compromise your computer increases if you tend to download illegal software from the Internet. Such software packs are one of the main sources of malware.
Remove Gmail virus from the system
If you infected your computer after opening an email attachment, your number one task is to remove Gmail virus as soon as it is possible. We strongly recommend using Safe Mode with Networking and a reliable anti-malware combination for malware removal if you cannot launch your anti-spyware. Otherwise, Gmail virus removal might be disrupted.
In case your computer hasn’t been compromised, but you lost access to your account, get in touch with the email service provider and follow their directions to recover your account.
Getting rid of Gmail virus. Follow these steps
Manual removal using Safe Mode
The provided steps will help you to get rid of Gmail virus with the help of safe mode with networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Gmail using System Restore
To get rid of email virus with the help of System Restore, use the following guide:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Gmail. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Gmail and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Gmail Virus Scanners are Temporarily Unavailable. Black Hat World. An internet forum owned by Damien Trevatt .
- ^ Number of active Gmail users worldwide from January 2012 to October 2018 (in millions). Statista. The Statistics Portal.
- ^ .JS File Extension. FileInfo. The File Extensions Database.
- ^ Adi Robertson. Google Docs users hit with sophisticated phishing attack. The Verge. Technology, Science, Art, and Culture News.
- ^ Mark Maunder. Wide Impact: Highly Effective Gmail Phishing Technique Being Exploited. Wordfence. Security News, Threat Research, Blog.
- ^ VirusActivity. VirusActivity. The Latest News about Virus Activity.





















