Your Computer Has Been Blocked. Know the latest versions (2020 guide)
Your computer has been blocked Removal Guide
What is Your computer has been blocked?
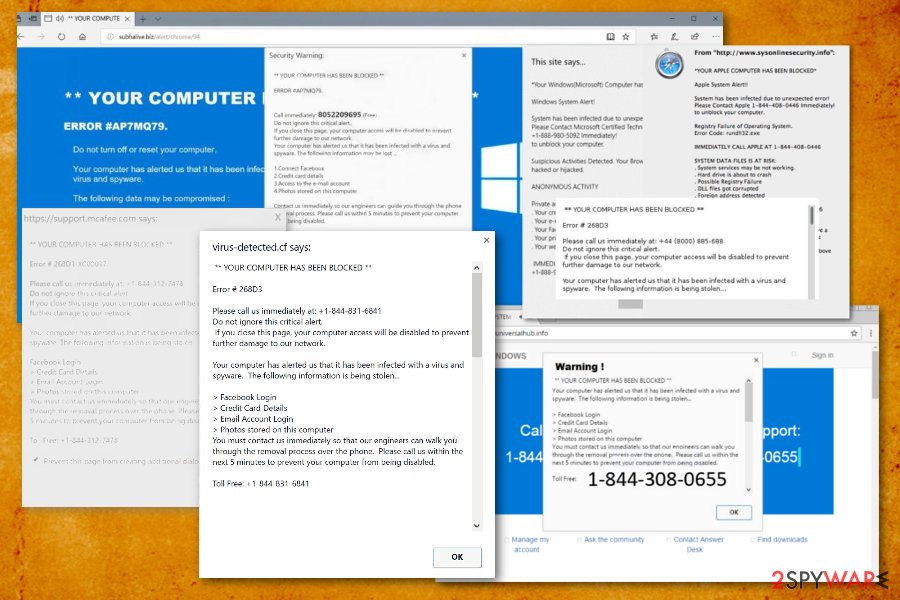
Your computer has been blocked – a false message stating about malware infiltration and risk to private data
Your Computer Has Been Blocked scam is the result of an adware program running on the machine that delivers various pop-ups and other alerts to redirect online traffic. People get tricked into thinking that their device got infected and personal data or valuable credentials are at risk due to the spyware. This alert states about stolen information, but this data can only be in danger when you let hackers on your device or reveal personal information over the phone.
However, you shouldn't call the provided number because people on the other side are criminals. The virus is a program that displays a system message stating illegal user's actions online to get your money or data. This scam is malevolent software that prevents access to the victim's PC either by locking the screen or triggering numerous alarming pop-ups on web browsers.
It is linked with the “This computer is blocked.html” file which launches scams informing users about illegal activity noticed by such governmental organizations as the FBI. “Your Computer Has Been Blocked” virus can even perform ransomware-type activities like demanding a ransom for the alleged criminal behavior. In most cases, these messages focus on getting users scared and eager to contact the support.
| Name | “Your Computer Has Been Blocked” |
|---|---|
| Type | Scam, adware |
| main file | This computer is blocked.html |
| Purpose | Swindle money from people by tricking them into believing that they have been caught by the government for illegal activities or their device is affected by a hacker or spyware |
| variants |
|
| Symptoms | Displays a fake message about privacy or security of your computer, suggests to call “technicians” or pay directly to the “government” |
| Main dangers | Demands money, asks providing personal information, offers to install the fake software |
| Distribution | Spam email campaigns, deceptive websites, other malware |
| Elimination | Use anti-malware tools for the adware that triggers scam messages removal |
| Repair | Particular issues with the machine can be fixed using tools like FortectIntego |
Having in mind that the fake alerts are filled with logos and other convincing details, they look legitimate scare people into contacting cybercriminals or paying the demanded money. Typically, such programs aim to force people to call tech support scammers[1] or pay immediately to regain access to the computer.
Unfortunately, contacting malicious people or paying the money can lead you to even more damage, including a data loss. This scam has various ransomware features and this makes it even more dangerous to your personal privacy and the system of your device.
There are many versions of the technical support scams and each of these viruses will provide you with fake information regarding your computer's security, stating that someone violated your privacy by hacking your computer and now you have to get in touch with “certified technicians”[2] to solve the problem.
However, similar messages are used by ransomware developers, and these viruses typically blame the victim for doing something illegal. Of course, these viruses cannot actually detect any illegal activities on the computer, but their purpose is to convince the victim that they are capable of doing it. Accordingly, such viruses seek to convince the victim to pay a smaller fine within several days to “drop the charges.”
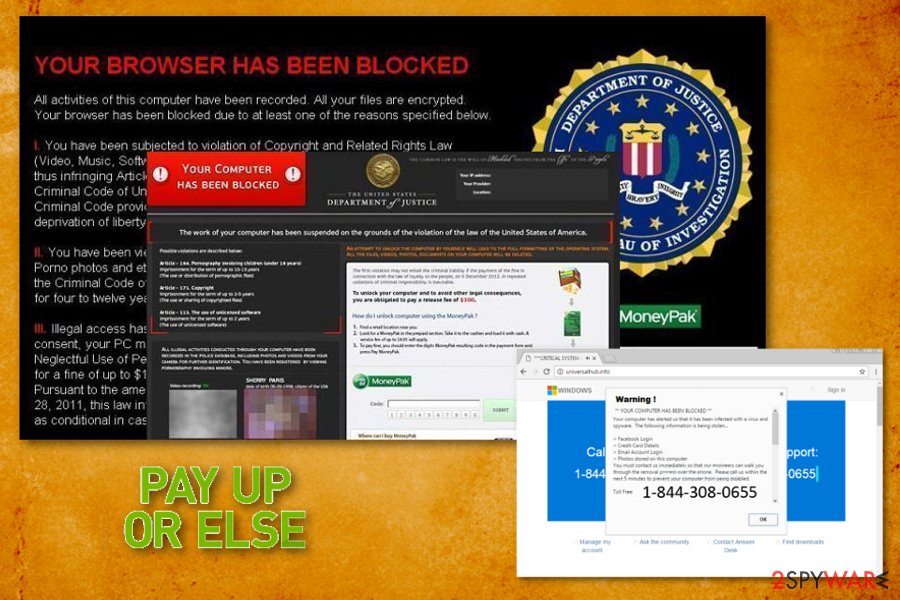
One of the most widespread variants of this malware belongs to the ransomware[3] category. Once installed, it displays a full-screen fake notification which is expected to scare people into thinking that they have violated several laws of the United States of America and now have to pay the fine for that.
Typically, it blocks the system with a huge alert which seems to be sent by an official government representative (The Federal Department of Justice in this particular case). Besides, it speaks to the victim in the same language where he/she is located.
The sad news is that there are actually Internet criminals behind the bogus notification. They seek to make you pay the supposed fine of $300 by purchasing the Moneypak voucher and sending the code to them.
You should NOT do that! You can unblock your computer and remove Your Computer Has Been Blocked ransomware from the system by following special steps that are listed below or scanning your system with trustworthy anti-malware tools.
Many functions and features of tech support scam
The virus is rather old, security experts report about a new wave of similar viruses used by tech support scammers[4]. In this case, YOUR COMPUTER HAS BEEN BLOCKED malware declares that the user's computer system is full of errors that can be fixed only by contacting Microsoft Tech support agents.
The virus usually infects main web browsers and sets them to trigger redirects to specifically designed web pages controlled by online fraudsters. These web pages often resemble Microsoft's Support Page. Phishing web pages then trigger a pop-up which usually has a title “This site says…” or “From [webpage URL]:”, which is then followed by a scary message saying that the system has been infected, compromised, hacked, or affected by mysterious errors or viruses such as Zeus virus.
The bogus messages always contain a tech support phone number, which is typically presented as “toll-free.” Of course, you should never dial these numbers given in fake ads of such malware because people who are going to pick it up are scammers[5]. Their aim is to make you believe that the system is heavily infected by super-advanced hackers and that the only way to rescue your PC is to follow commands from “certified technicians.”
Typically, such scammers ask the victim to do a list of useless tasks just to confuse him/her, and such commands usually are followed by a request to provide remote access to the so-called technician in order to fix the computer faster.
You should never provide remote access to cybercriminals because they might download and install ransomware or another virus on your computer; scammers who don't get access to the computer frequently seek to sell certain “security packages” to the victim, which usually contain one or two legitimate programs plus several free ones such as Adblocker browser extension.
Of course, scammers sell these packages at an enormous price. Such malicious programs belong to the Tech support scam virus group. An example of deceptive pop-ups urging to call tech support scammers is displayed below.
You can temporarily disable this malicious warning message by closing your web browser. However, a full Your Computer Has Been Blocked removal requires running a full system scan with reliable computer protection software, such as anti-spyware or anti-malware (you can find some suggestions in the Software section, although we usually recommend using Malwarebytes or SpyHunter 5Combo Cleaner programs).
You should not waste your time with that because malware which is related to this Tech Support Scam can also collect personal and non-personal information about the user. So, although this virus will not lock your files like the ransomware we described earlier, having it installed on your computer can result in a number of privacy violations or even identity theft.
Other versions of the false security mesages
“Zeus virus detected – Your computer has been blocked”
Zeus virus detected scam has various functions as a browser-based scam which alarms users with fake alerts that their operating system has been compromised. You might also notice the error message which indicates Error: Virus – Trojan Backdoor Hijack #365838d7f8a4fa5.
The further content of the message warns users not to exit the web page as the supposed Microsoft support group will have to “disable your computer.” It is pure nonsense but merely a deception. The message also contains a 1-888-615-5854 number though it may vary due to an expansive network of these felons. There is no need to meddle with the fraudsters but exit the web page and scan the browser to eliminate the scam web scripts.
“Your computer has been blocked. Confirm navigation”
This is another version of the browser malware. In order to scare users, the crooks make up the story that your confidential information is about to be stolen. This type of browser scam also temporarily hijacks the browser, as you may not easily exit the page.
As common for this tech support scam, the number of the supposed Microsoft technician is provided. Note that no genuine Microsoft alerts display messages with the included phone number. Such browser scams are not able to “disable” the computer as well. More elaborate PC-based tech scams and ransomware are only capable of inflicting such commands.
Error 268D3 – Your computer has been blocked
Error 268d3: Your computer has been blocked version of the malware displays an almost identical alarming message which frightens users that their devices have been compromised with data-stealing malware. This version of the scam also plays the integrated audio file. An abrupt male voice warns users to call 1-888-375-1978 or another number to “enable” the device again.
Certainly, all these claims are nothing more than deceptive lies. Some sub-versions of this scam may also function under bsodm.exe. If clicking “Prevent this page from creating additional dialogues” does not work, click ESC+CTRL+SHIFT to launch the Task Manager. Find the command, right-click on it and exit it. It is also recommended to scan the browser.
Error # FXX07 pop-up scam
Error # FXX07 – Your Browser Has Been Blocked is the campaign focused on scamming people with fake alerts and messages on the web browser. Deceiving redirects and locked screen alerts state about particular issues or risks to your valuable data like logins or passwords and files stored on the device. This warning doesn't differ from any other Your Browser Has Been Blocked scam alerts, except the particular Error code shown on the pop-up.
Remember that all these browser pop-ups and lock screens are not showing the legitimate message and there is no malware on your machine that could steal logins to any accounts, passwords, or banking credentials. However, scammers can aim to steal all these details when you call the provided support team phone number. Once scammers get contacted they try to get paid for the alleged service or get on the remote access to the targeted PC. Then criminals can either infect the machine further or gather data directly from the victim.
“YOUR APPLE COMPUTER HAS BEEN LOCKED” scam
APPLE COMPUTER HAS BEEN LOCKED virus is a particular version of this technical support scam that targets Apple devices with fake system messages posing as a warning from Apple support. Note, that Apple Care or Apple Support are not sending such alerts and especially not delivering any phone numbers or contact information. Calling the toll-free number can only lead to cybercriminals with questionable goals.
These allegedly certified Apple technicians ask victims to either let them fix the problems by accessing the device remotely or suggest installing particular software. Each way scammers infect the machine and can then collect data you enter or steal information stored on the system already. Credit card credentials and personal details can be stolen when you get asked to pay for the service or purchase tool promoted by these fake technicians.
Your Microsoft Computer has been blocked
Your Microsoft Computer has been blocked is yet another fake alert that has nothing in common with the risk on your computer. It means that you have installed a piece of malware that displays fraudulent warnings to you, seeking to frighten you and convince you to get in touch with tech support scammers, which deceptively claim that they are “Microsoft technicians.”
The “Your Microsoft Computer has been blocked” virus message also includes such alert:
Windows System Alert! System has been infected due to unexpected error!
However, all these words are entirely made up, and you will not find a single true statement in them. The main aim of these programs is to scare the PC user by repetitively mentioning the word virus and telling lies about all possible problems that can happen to the computer, such as hard drive is about to crash, DLL files got corrupted, possible registry failure. These lines can scare an inexperienced computer user, and force him/her to take ill-considered actions.
Deceiving methods of the tech support scam/ adware delivery
Just like other technical support scams, this virus comes in a form of email attachments, which are usually distributed via massive spam campaigns. Besides, some users have also reported that they got infected after downloading a free program to their computers.
Speaking of tech support scam viruses, they can reach the system along with freeware or shareware, pirated software, and also via email. To avoid these malicious programs, we highly recommend you to act responsibly when installing free programs downloaded from the world wide web.
Remember, many free programs recommend installing extra programs alongside them, and you have to refuse to do it if you do not want to end up installing adware, browser hijackers, or tech support scam malware. To decompose software packages, we recommend choosing Custom or Advanced settings for their installation and deselecting every optional item added to your desired piece of software.
Help for the successful Your Computer Has Been Blocked scam removal
Many users do not know how to remove the virus, although all it takes to wipe it off the system is running a professional malware removal software. However, when trying to remove this or other ransomware from the FBI virus group, the biggest problem is unlocking the system.
First of all, you should restart your computer using the instructions provided below to run it in a Safe Mode with Networking. Once the computer boots, download an anti-malware software or update the one you already have; after that, perform a full system scan with it. You can also try to unlock your screen by opening your Task Manager -> Processes tab and ending black.exe process.
When you complete this task, you should scan your system with anti-malware immediately. Your Computer Has Been Blocked removal is a long and sometimes difficult process, therefore, to avoid similar attacks in the future, it is advisable to regularly backup of your data and keeps it in an alternative place.
Get rid of the Your Computer Has Been Blocked virus by cleaning all possibly related potentially unwanted programs with anti-malware tools and similar intruders that come via the internet. You can rely on FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes and run the full system scan to eliminate any damaging files.
Getting rid of Your computer has been blocked. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Your computer has been blocked using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Your computer has been blocked. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Your computer has been blocked and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Breaking down a notably sophisticated tech support scam M.O.. Microsoft TechNet Blogs. Microsoft Malware Protection Center Blog.
- ^ Zack Whittaker. We talked to Windows tech support scammers. Here's why you shouldn't. ZDNet. Technology News, Analysis, Comments and Product Reviews.
- ^ Ransomware. Microsoft. Malware Protection Center.
- ^ Jérôme Segura. Tech support scams and Google Chrome tricks. Malwarebytes Labs. The Security Blog From Malwarebytes.
- ^ Matthew Hughes. Just Hang Up: Why You Shouldn’t Taunt Fake Tech Support Scammers. MakeUseOf. Technology, Simplified.





















