Gryphon ransomware / virus (Removal Guide) - Recovery Instructions Included
Gryphon virus Removal Guide
What is Gryphon ransomware virus?
Gryphon ransomware “steals” file extensions from other viruses
Gryphon virus is a new computer infection with an aim typical to most cyber infections – making a substantial and effortless profit. Technically, it is known as ransomware [1]. For the communication with their victims, hackers indicate email addresses: decr@cock.li and decrsup@cock.ll.
The same email address is featured next to the files that undergo a complex encryption process: documents are appended with [decr@cock.li].gryphon extensions. More recent ransomware versions add .crypton file extensions on encrypted records.
Malware experts believe that this cyberthreat might be related to the BTCWare ransomware family as it is build using the code of this infamous virus. Due to such obvious relations, some people are already relabelling this malware as BTCWare Gryphon virus.
Currently, the virus experts are aware of one Gryphon virus version which spreads around as payload.exe file. Once this executable manages to infiltrate the computer, it enables the ransomware to start encrypting files and, eventually, display a ransom note demanding money for data decryption.
Experts have been monitoring this cyber infection for a while, and the mentioned features are major improvements compared to the initial virus version (Test ransomware) which added .[test].gryphon extensions to the computer files and had no defined interface, to begin with.
If you find your files encrypted, don’t allow yourself to be manipulated by the cyber criminals and remove Gryphon from your PC before the parasite receives additional updates. Use FortectIntego or Malwarebytes to fix your device.
Gryphon makes a diversion by adding .cryptON extension
If you follow the trends in the IT sphere, you may recall that each ransomware has a distinguishable feature – different file extension. Nonetheless, there are cases, when a couple of the same family viruses or even different crypto-malware append the same extensions. Relatively new Gryphon virus happens to behave likewise as well.
It attaches %s.[gladius_rectus@aol.com ].crypton extension similar to the one attached by a different virus – CryptOn ransomware. It presents its demands in HELP.txt file. After the victims are ready to transfer the money, they are instructed to contact the perpetrators via gladius_rectus@aol.com or gladius_rectus@india.com.
While there are no major improvements, the authors have employed a different RSA key for encrypting the AES which lowers the overall Gryphon decryption probabilities. Luckily, the new variant is already detectable by multiple cyber security utilities.
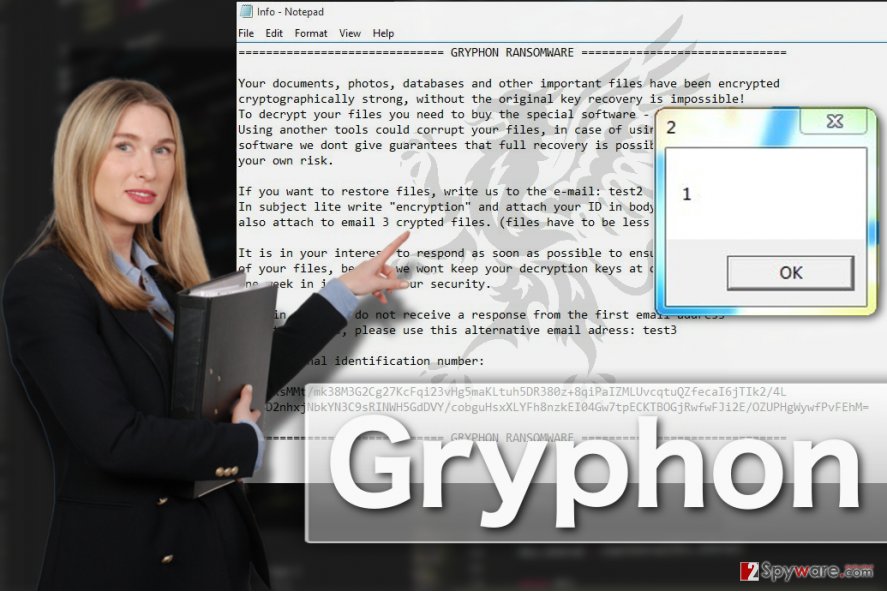
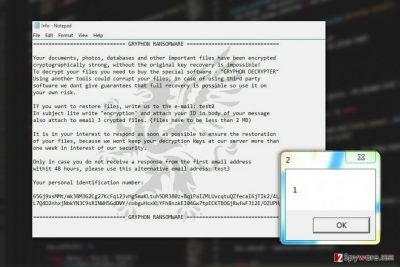
The original version of the malware greets its victims by opening HELP.inf or !## DECRYPT FILES ##!.txt files which contain the following message:
GRYPHON RANSOMWARE
Your documents, photos, databases and other important files have been encrypted cryptographically strong, without the original key recovery is impossible!
To decrypt your files you need to buy the special software – “GRYPFON DECRYPTER” Using another tools could corrupt your files, in case of using third party software we dont give guarantees that full recovery is possible so use it on your own risk.
If you want to restore files, write us to the e-mail: test2
In subject lite write “encryption” and attach your ID in body of your message
also attach to email 3 crypted files. (files have to be less than 2 MB)
It is in your interest to respond as soon as possible to ensure the restoration of your files, because we wont keep your decryption keys at our server more than one week in interest of our security.
Only in case you do not receive a response from the first email address withit 48 hours, please use this alternative email adress: test3
Your personal identification number:
[Victim’s ID]
GRYPHON RANSOMWARE
It seems that the virus is currently undecryptable. Besides, it messes with the computer's Master Boot Records which may need additional fixing after the malware is removed from the PC. The good news is, the parasite does not seem to be erasing Volume Shadow Copies from the infected system which allows relatively easy recovery of your important data.
But first, you must take care of the Gryphon removal. Be careful not to leave dangerous malware files lurking inside your system. Unattended files can trigger the virus to come back to your PC and encrypt your files again.
Ransomware prevention tendencies:
Gryphon ransomware is a perfect example of how various in-development programs can turn into full-blown ransomware infections which may seriously damage infected computers and corrupt users’ personal files.
Thus, a smart thing to do is to learn how to avoid becoming a target.
You can start by following these simple rules:
- Stay away from poor reputation websites and don’t use them as sources for your software downloads
- Be careful when opening emails, especially if they arrive from unfamiliar or suspicious senders. Spam folder is the absolute red zone. Emails end up there for a reason thus you should avoid opening them unless you are completely sure the email is safe.[2]
- Obtain reliable security software, enable firewalls and keep all computers protection tools up to date
- Don’t forget to enable automatic System Updates as well! If you are still using outdated and unsupported operating system version, we also recommend upgrading to the newest one.
Implementing these rules in your daily computer use should diminish the chances of getting infected with Gryphon or any other ransomware viruses.
Eliminating Gryphon malware
The first Gryphon removal step you should take is to obtain a professional tool that would have no problem eliminating ransomware from your PC. You can find descriptions of our recommended tools in the Software section of our website.
For those who don’t want to invest in new antivirus software or simply can’t remove Gryphon from their computers automatically due to the lack of system capacities, we provide a manual step-by-step guide below this article.
Getting rid of Gryphon virus. Follow these steps
Manual removal using Safe Mode
Gryphon ransomware may still be a virus in-developement, but it may fight its way of staying installed on your computer. Therefore, you should learn how to block the malicious processes and enable automatic system scan with antivirus. We explain how to do that below:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Gryphon using System Restore
If you don't want to risk while eliminating the ransomware from your computer you should help your antivirus software out by decontaminating the virus following these steps below:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Gryphon. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Gryphon from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Gryphon, you can use several methods to restore them:
Technique no.1: Data Recovery Pro
If you want to employ Data Recovery Pro for the recovery of your files, you should follow the guidelines below and do it properly:
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Gryphon ransomware;
- Restore them.
Technique no.2: Windows Previous Versions feature
The instructions below the article will explain how to use Windows Previous Versions feature and hopefully recover your files:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Technique no.3: Shadow Explorer
Shadow Explored may be your best chance at recovering encrypted files. Here is how to use this tool properly:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Gryphon and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Ransomware. Cert. We support businesses, organisations and individuals affected by cyber security incidents, and provide trusted and authoritative information and advice.
- ^ Brien Posey. 10 tips for spotting a phishing email. TechRepublic. News, Tips, and Advice for Technology Professionals.





















