How to remove ransomware
Ransomware is a virus – a malicious program, that is designed to encrypt files on local and networked drives. The main purpose of the attackers behind it is to extort money from companies, businesses, governmental institutions, and home users. Ransomware creators ask for ransom and that is where the term Ransomware has come from.
Data locking process with a secure encryption algorithm such as RSA ensures that, if no backups were retained, files could only be recovered by paying the ransom in bitcoin (for anonymity purposes).
While the first ransomware infections focused on locking users' computer screens and displaying a falsified FBI or other local authority messages, modern crypto-malware evolved to be more effective and efficient. In recent years, the cybersecurity landscape has seen a significant rise in this illegal business, as ransomware is becoming more lucrative.
Cybercriminal gangs began employing another effective tactic that increased their success. Before deploying ransomware to encrypt data, the first snoop around, acquiring administrative privileges on the network, allowing lateral movement. During this time, the attackers harvest sensitive documents and other information. If victims do not agree to pay the ransom, malicious actors publish the stolen files for everybody to see. To keep this data private, many organizations are forced to pay, even if they have backups to retrieve the encrypted files from.
The main ransomware types:
Depending on the peculiarities of the malware, IT experts classify file-encrypting threats into these categories:
File Encrypting Ransomware
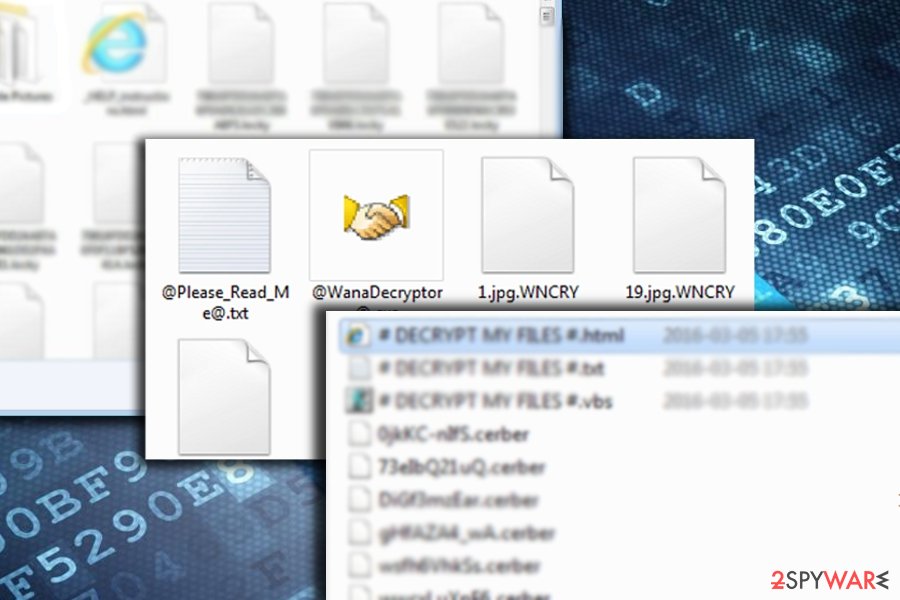
This version is mostly spread with the help of trojans via spam emails or illegal program keys. Once it infiltrates the computer, it finds the most used files and encrypts them by appending some extension. Usually, PC users who have faced this ransomware attack are saying their files have been renamed and cannot be opened anymore. Traditionally, encrypted files include photos, music files, videos, art, business, and other data that are considered important for the victim.
In addition, such a virus starts displaying a huge warning message claiming that the only way to decrypt encrypted data is to pay a ransom. In fact, it is right because most of such malware deletes the shadow copies of files and prevents their recovery.
Screen-locking ransomware
This type blocks the entire PC system and seeks to threaten PC users into paying an invented fine. For that, it presents itself as the warning message of the governmental authority. Typically, hackers use such names as FBI, police, and others.
Once it infects the system, it checks it for illegal files, like pornographic content or unlicensed program versions on a victim's computer. Once they are detected, a virus locks the computer down and starts displaying a huge warning message that looks like it belongs to some governmental authority. In this case, a victim is informed that there are illegal files that were detected after the scan on his/her computer. In addition, the user is asked to pay a fine in order to avoid getting into jail.
Browser-Locking Ransomware
This version does not infect the computer system. It relies on JavaScript that blocks the browser and causes a huge warning message. This fake notification is very similar to the one that is displayed by screen-locking malware. It mostly claims about the illegal user’s activity on the Internet and asks to pay a ransom for avoiding jail. Of course, such a virus has nothing to do with the FBI, Europol, and other governmental authorities.
Ransomware-as-a-service (RaaS)
RaaS is one of the main factors why the crypto-malware business is booming. If felons, who are interested in earning easy money but lack programming knowledge to create their own, may contact the ransomware developers via the darknet and engage in the distribution campaign.
After gaining access to malware configuration, crooks spread the virus via their networks. In exchange, they often receive 60-80% of the total revenue. Since the business is conducted on underground hacking forums, RaaS has become a significant issue to organizations.
Wipers
While wiper malware has its own category, some ransomware infections are programmed in a way that would destroy the data of the infected computer. In some cases, this happens due to the inexperience of hackers – they simply fail to write the code correctly. Regardless of the wiping function was included purposely or not, the victims can never retrieve their files back, so paying cybercriminals is useless.
Modus operandi of file-encrypting threats
Despite their differences in visual graphic interface or source, their purpose is only one – extort money. In order to do so, the cybercriminals employ different techniques. Here is a short summary of how crypto-malware differ from ordinary malware.
- Ransomware viruses encrypt sensitive user data, such as business documents, videos, photos, and other files.
- Ransom is demanded in exchange for the encrypted files.
- Such viruses can delete predetermined documents, multimedia objects, or any other files containing important information. They also manifest the ability to delete essential system components or important parts of other software.
- Trojanized versions steal login names, passwords, valuable personal documents, and other confidential information. This data is sent through a background Internet connection to a remote host.
- Ransomware assault may cause your operating systems system to underperform, more specifically, it may force a system restart or significantly affect its CPU speed.
- Certain types of this malware category may shut down cybersecurity-related software.
- More elaborate samples are able to disguise their activity on an operating system until they finish encrypting users' files.
Although they usually do not self-replicate, such threats can make lots of problems on your computer. They can make your vital information inaccessible. It is highly recommended not to pay the ransom, which is asked by this threat because that doesn't help to remove the parasite and restore affected information.
Distribution techniques and methods
Most ransomware parasites are able to propagate themselves and infect their target PC systems without users' knowledge. They can affect computers running Windows, macOS, Android, and other operating systems. There are two major ways how these parasites can get into your computer.
Trojan Horse and other malware. Most of these types of infections are spread with the help of trojans. Trojan.Lockscreen is the most used threat for installing ransomware on the system. They get into the system without the user's knowledge as they tend to arrive in files attached to e-mail messages that present themselves as messages from reputable parties, such as Amazon, eBay, financial institutions, etc. Once a user is tricked into downloading such an attachment, the trojan, carrying the ransomware payload, gets activated.
Fake pop-up notifications. Some samples of this malware category are distributed by fake pop-up notifications that can be seen either on illegal or on legitimate websites. Mostly, they are set to report about missing updates but they can also “inform” you about a need to scan the system for free and remove viruses from it. These ads are usually filed with unsuspicious names and legitimate logos, so they can trick even the most experienced PC user into clicking them.
Spam emails. This is the most profitable technique in ransomware distribution. Ironically, if users were more cautious, they could be able to prevent the hijack of most destructive threats. The key principle of this technique lies in wrapping the malware into a .doc or .js file. The notorious crypto-malware Locky is especially known to employ this technique.
By emphasizing the importance of the fake invoice or package delivery attachment, victims are persuaded to extract the attached file. If it is a .doc file, it might ask users to enable macro settings. If they are enabled, the corrupted file downloads the main payload of the malware. Alternatively, cybercriminals counterfeit subpoenas or the email supposedly sent by the FBI. Users should pay attention to the content of such emails. They often contain grammar mistakes and typos, and altered credentials.
Exploit kits. This technique is mostly preferred by developers of more sophisticated threats. Locky and Cerber virus authors are especially keen in using Angler, RIG, and Neutrino exploit kits. While, the former, Angler, was fortunately terminated, Rig and Neutrino continue facilitating the transmission peculiarities of crypto-malware. Their main principle of operation lies in compromising in selected domains. By injecting corrupted scripts, users, visiting such domains, end up being hacked by the very threats. Thus, the only viable way of preventing such cyber assault remains the usage of cybersecurity tools.
Software cracks and pirated programs. The easiest way for cybercriminals to infect users with ransomware is by making them install it themselves. It is not a secret that there are millions of users who visit torrent, warez, and similar websites that allow them to download pirated applications or cracks. Keygens, cracks, or loaders are designed to bypass the licensing process of a legitimate program and acquire full access or premium features to be used for free.
There are countless websites that distribute cracks. While the security software immediately warns about the danger of the infection, users tend to ignore such messages and proceed with opening the malicious executables. One of the most successful ransomware strains, known as Djvu, has been using this tactic for years, becoming the most prolific crypto-malware that targets home users.
Browser extensions. This is a relatively new technique, mainly employed by Spora ransomware developers. They also relied on EiTest script technique, which would compromise a certain web page by injecting a specific script. After netizens visit such domain, the content is transformed into an unreadable collection of numbers and characters, and “The HoeflerText font wasn't found” notification appears.
In order to read the content, users had to “update” a specific Chrome font browser add-on. Nonetheless, they only facilitated the hack of the file-encrypting threat. Lately, other fraudsters developed a technique of distributing malware via fake GoogleDocs invitations. Thus, in order to lower the risk of crypto-malware assault, users have to retain vigilance, while downloading new apps, enabling new features, and communicating with users via social networks.
Exploit kits used in ransomware campaigns
Exploit kits are usually adopted by sophisticated and large-scale viruses. As IT professionals and security experts discover more vulnerabilities and patch them, the safer systems around the globe become. Thus, those who update their software regularly should not fear the following exploit kits used by cybercriminals.
Rig Exploit Kit
Rig EK is one of the most prominent ones since 2016 and is used to infect victims in various countries. Rig is mostly used through compromised websites, abusing vulnerabilities of Adobe Flash, Internet Explorer and using malvertising techniques to lure users into clicking on compromised links. JavaScript, Flash, and VBscript-based attacks are used to complete the obfuscated infiltration procedure.
Rig Exploit Kit has been distributing ransomware since its appearance back in 2016, including Cerber, GandCrab, TeslaCrypt, Matrix, CryptoMix, and others. Additionally, the kit has been recently spotted to drop banking trojans and crypto-mining malware.
Grandsoft Exploit Kit
GrandSoft first emerged in 2012 and then stopped being used in 2014. However, it did re-emerge in 2017 and has been active ever since.
GrandSoft exploit kit uses a similar technique as Rig, although it is far less advanced when it comes to obfuscation. As soon as the victim lands on the malicious web page, the versions of Java, Flash, Silverlight, and AdobeReader are checked. If the vulnerability is found, the kit redirects to the payload retrieval function.
The recent usage of GrandSoft EK includes distribution of GandCrab in early 2018, as well as dropping crypto-miners, trojans, and password stealers (AZORult stealer).
Magnitude Exploit Kit
Magnitude EK was offered on the Dark Web since 2014, shifting into a private exploit kit in 2016 which was used exclusively to target South Koreans and Taiwanese. While at the start it focused on Flash Player vulnerabilities, it now only relies on Internet Explorer exploitation.
Initially, it delivered Cerber ransomware during 2017. At the end of the same year, hackers began to distribute their own virus – Magniber ransomware. While malware went to great lengths to specifically target North Korea, researchers recently noticed it being used on other Asia Pacific countries.

The biggest ransomware outbreaks in history
WannaCry ransomware
Cybercriminals have not failed to astonish the virtual community. However, on the eve of May 11th, 2017, the world was yet to witness the unprecedented cyber assault in the entire history of computer viruses. The next day, different public and governmental institutions, as well as private companies, all around the world started reporting their cyber systems to have been taken by ransomware. Its name was WannaCry.
- infected more than 200 000 devices in 150 countries
- demanded over 300 dollars in bitcoins
- devised on the basis of “EternalBlue” vulnerability
- targeted older and outdated Windows OS versions
- possibly created by Chinese hackers
It targeted solely Windows OS systems. World-class companies such as “Hitachi” or German transportation agency “Deutsche Bahn” were affected by the malware. The ransom note was visible on digital information and advertising boards. The outbreak led international IT cyber specialists to join forces in seizing the attack. Interestingly, that WannaCry hackers were able to wreak havoc due to a seemingly minor factor – EternalBlue (CVE-2017-0144) vulnerability.
The story of WannaCry dates several months ago when the gang of cyber crooks known as “ShadowBrokers” stole the hacking tool developed according to this vulnerability. Surprisingly, the merits for creating such a tool do not belong to hackers as many may expect, but rather to National Security Agency.
With the help of this tool, older versions of Windows which possessed weak transport SMB protocols fell into the trap set by the malware. Though after the leak was exposed and Microsoft quickly released the patch in March, the scale of WannaCry revealed the high number of outdated systems globally.
Nonetheless, the rampage of the malware did not take too long. An IT specialist Marcus Hutchins bought an unregistered domain monitored by the malware developers. Fortunately, he was able to find a “kill switch.” By activating it, the traffic of the malware was finally ceased. While the world was recovering from the attack and estimating losses and scale of damage, the virtual community expected the second wave of the attack.
Since then, affiliated versions, such as WanaCrypt0r, Wana Decryot0r 3.0, made an appearance. Recently, another IT specialist warned netizens as he found a peculiar domain that may be related to the distribution campaign of WannaCry 3.0.
As the virtual community retains focus on this family of viruses, further analysis has presented interesting results. The extracts of the source code of the malware hinted to “Lazarus,” a notorious gang of hackers who are suspected to be working under the protection of the North Korea government. However, other specialists found evidence suggesting that the culprit might have been of Chinese origin.
Speculations over the new series of attacks flickering in the media might indeed provoke the hackers to make a rush and launch another wave of the attack. The latest versions will, certainly, not include the “kill switch.” On the other hand, every computer virus, despite how powerful it may seem, has a weakness.

Petya ransomware
Petya ransomware is one of the most notorious viruses that crippled multiple high-profile organizations like airports, gas stations, banks, and even mostly in Russia and Ukraine in 2017, soon after the WannaCry outbreak.
The virus was first spotted in March 2016, infecting victims through contaminated e-mail attachments. Petya targeted Microsoft Windows operating systems, infecting the master boot record and encrypting system files which prevent Windows from booting. Instead, users were prompted to pay $300 in Bitcoin to regain access to their devices.
A new variant of malware hit the world in June 2017 and propagated via the NSA's EternalBlue exploit which was used in WannaCry attacks. Due to the different nature of proliferation, the virus was dubbed NotPetya by security researchers. Although this variant of the virus primarily targeted Ukraine (around 80% of all attacks) and Russia, several infections were spotted in the United Kingdom, the United States, Germany, France, Poland, and Italy.
Ukranian tax preparation software M.E.Doc was compromised to spread the virus, researchers believe. Although M.E.Doc denies any involvement in the ordeal, claiming that they are themselves, victims, the analysis revealed that the backdoor was present in the update system for the six weeks before the attack occurred, making it a well-planned and meticulously executed operation.
Ukranian cybercrime division confiscated the servers from the company, which revealed that software was not patched since 2013; because of this, the company might be liable for the attack as a whole, as security measures were not adequately undertaken. Additionally, the research found that one of the employee's account was compromised, and Russian involvement was detected.
Unlike WannaCry, NotPetya was programmed so that changes made to devices could not be reverted. Therefore, security specialists believe that its purpose was not money extortion, but rather fame and devastation caused to multiple organizations around the world. Among the victims were WPP, Maersk, DLA Piper, DHL, Rosneft, and many others. The operation of firms was disturbed so that some suffered over a $300m loss in revenues (Maersk).
Locky ransomware
Locky was first released in 2016 and was propagated via contaminated spam email attachments over 500,000 were sent out containing malicious document files. The payload would only be executed if victims allow the document to use the macro function. Unfortunately, many users did.
The virus locked up personal files and demanded a ransom of 0.5 – 1 in BTC cryptocurrency. The instructions, which were dropped on users' desktops, contained information about how to download and install the Tor browser and how to execute the payment.
In the time of its operation, Locky was updated several times, and new versions emerged. Not surprisingly, each variant came with improved obfuscation and proliferation techniques, making it one of the biggest threats of 2016. Hackers added offline encryption function, and variants like Diablo6 and Lukitus came as the most prevalent ransomware.
Locky was also distributed using Necrus botnet which included over five million hacked machines. An interesting fact is that the virus kept disappearing each time Necrus was used for the distribution of something else, for example, during Jaff ransomware spree. Nevertheless, the two viruses seem to be connected, security researchers believe.
One of the most notorious cases when it comes to Locky occurred in February 2016, when Hollywood Presbyterian Medical Center in Los Angeles paid a ransom of 40 Bitcoins, which at the time came close to $17,000. The staff could not operate the systems, neither could they access the medical data of patients.
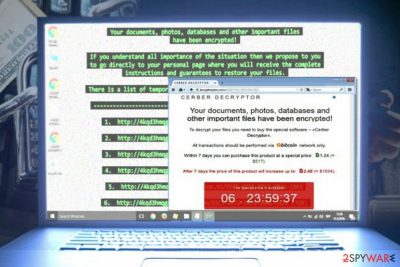
Cerber ransomware
Cerber virus was another significant threat of 2016 as it infected over 150,000 Windows users in July alone, including a total of 161 active virus campaigns. It was distributed using various exploit kits, including Magnitude, Neutrino, and Rig.
The malware was updated several times, adding new file extensions and asking for 1.2 BTW for data recovery. According to research, the virus was generating around $2.3 million of annual income.
Additionally, malware authors decided to share the functionality with whoever wants it – for a price. Cerber is known to be operated as Ransomware-as-a-service (RaaS), and bad actors can use the virus as long as they share 40% of the profits received from ransom payments. Bitcoin Mixing Service allows authors to obtain the percentage of payment automatically.
Cerber ransomware works in collaboration with other viruses, such as Kovter Trojan. The obfuscated email attachments from FedEx, UPS and other delivery services were used as an effective method to spread both viruses. It was capable of looking for files that belong to various Bitcoin wallet apps, and stealing crypto wallet data.
Another interesting feature is that malware does not target users from ex-Soviet countries, including Azerbaijan, Armenia, Georgia, Belarus, Kyrgyzstan, Kazakhstan, Moldova, Turkmenistan, Tajikistan, Russia, Uzbekistan, and Ukraine.
While Cerber is an advanced infection, it does have certain weaknesses. Several early versions are decryptable, and experts noticed some attacks failing to remove Shadow Volume Copies, allowing victims to restore files without much trouble. Nevertheless, several new versions are not decryptable, and virus keeps coming back stronger.

Avoid paying ransom
In the case of the assault, it is not recommended to pay the ransom. Many people have lost their money this way, as cybercriminals simply fail to keep their promises. In other cases, users reported that the delivered decryption tool simply failed to work. Another unfortunate side effect of paying the ransom is that it proves criminals that their scheme works, and they are keener on evolving threats to infect more victims worldwide.
Also, do not believe messages stating that you are dealing with governmental authorities because it's not true. Such statements are displayed just for exerting psychological pressure on people and persuading them into paying ransoms. Fortunately, numerous antivirus and anti-spyware applications can easily find ransomware files on the system and remove each of them. More information about them can be found in the Software section.
Countering crypto-malware on Windows OS
Despite how elaborate file-encrypting viruses are, manual termination is never an option. Even if it is just a screen locker, opt for an automatic solution. Press Alt+F4 combination of keys and then launch an anti-spyware tool. If, on the way to launching a security tool, you face a series of system errors, perform the below steps. Safe Mode will grant you access to vital functions and then you will be able to eliminate ransomware.
• Reboot computer in Safe Mode and repeat the installation of anti-malware app;
• Reboot computer in Safe Mode with Command Prompt and then install anti-malware program;
• Restore your system settings;
• Disable the affected web browser;
• Use FortectIntego or Malwarebytes;
• Contact 2spyware customer service through “Ask Us” section;
After the elimination process is finished, you might also install firewall software to complement your anti-virus tool. The former software proves to be effective in blocking trojans or ransomware which occupy devices by exploiting weak Remote Desktop protocols.
Terminating ransomware on Mac OS
Apple users are said to have a certain advantage over Windows OS owners. For a long time, the term “Mac ransomware” only brought a surprised look if not a smile on users faces. However, crypto-malware designed for Mac OS systems is no longer a fantasy. Mac OS-based file-encrypting threats target devices in the disguise of rogue applications or corrupted app updates. Indeed, such cases are significantly lower than the number of Windows-based file-encrypting threats.
Therefore, it is crucial to be aware of prevention measures. The same crypto-malware methods apply in terminating the malware on Mac OS systems as well. You will find explicit reviews of applications that might be effective in eliminating ransomware on Apple devices. In addition, there are also free tools that solely focus on detecting file-encrypting activities. Having such tool on the device might strengthen the overall immunity of the device.
Protect yourself from ransomware infections
Without a doubt, ransomware is one of the most devastating cyber infections in the wild. Its effects on files are potentially permanent, as security software cannot revert files to their former selves (anti-malware is not designed for that). And while there is a small chance of data recovery with third-party recovery solutions, most crypto-viruses perform secure encryption on data – even the supercomputers would take 1,000 years to calculate the combination that would unlock files. That is why it is so important to keep regular backups of your most important files.
Data backups can be one of the best measures that negate ransomware impact. However, the best outcome would be not to get infected in the first place – and there are many ways how to achieve precisely that.
- Install a robust security software with real-time protection feature, and keep it updated at all times;
- Update your operating system and the installed software regularly;
- Be aware of phishing emails: attachments that ask you to enable macros are dangerous and could result in ransomware infection;
- Use strong passwords and never reuse the same password for multiple accounts;
- Secure Remote Desktop connection and make it invisible to the internet;
- Never download software cracks or pirated program installers;
- Do not trust unexpected update or download prompts (Flash Player is especially abused in this regard).
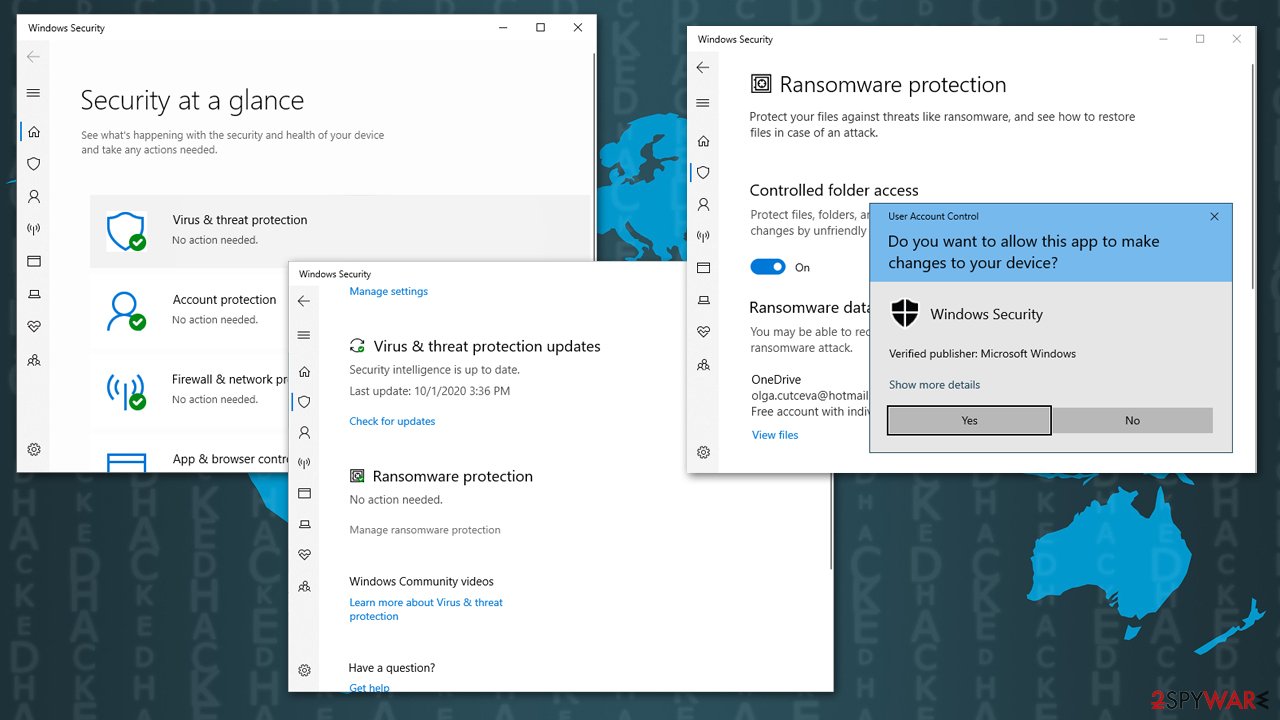
Also, if you choose Windows Defender as your main security application, you should enable the Controlled folder access feature. Here's how to do it:
- Type Windows Security in Windows search bar and hit Enter
- Select Virus & threat protection
- Scroll down and click on Manage ransomware protection
- Under Controlled folder access, turn the feature to On.
NoMore ransom project offers solution for ransomware victims
Numerous articles appeared on online media entitling 2020 to be the year of ransomware. As the world was paralyzed by the COVID-19 pandemic, threats like Djvu, Phobos, Dharma, and REvil grew rampant online. Netizens were entrapped between three options – either pay the ransom and rely on hackers mercy, restore data from backup files (at the best case of scenario) or give up the files.
Fortunately, cyber specialists and international law enforcement forces have worked tirelessly on the project which, later on, was introduced as NoMoreRansom. National High Tech Crime Unit of the Netherlands’ police, Europol’s European Cybercrime Centre, Kaspersky Lab, and Intel Security are credited for this initiative. It helps victims affected by crypto-malware.
At the moment, the domain encompasses a series of decryption tools of the most popular file-encrypting threats. However, even if netizens managed to get infected with older samples or less popular threats, they will also find the website highly beneficial. It is regularly updated with improved decryption tools.
Users, who have been struck with XData ransomware, might find the tool to decode their files for free. AES-NI, Globe ransomware, TeslaCrypt, and HiddenTear victims will also find a solution. With the expanding network of partners, NoMoreRansom keeps also gives prevention tips. The developers note that ransomware education is gaining more importance as mere cautiousness may save from highly troublesome and severe outcomes.
Latest ransomware added to the database
Getting rid of Bgzq ransomware
Remove Uazq ransomware
Remove Nood ransomware
Information updated: 2021-01-11