What is Adware? In Depth analysis and removal guides
Adware – a type of software you should not trust
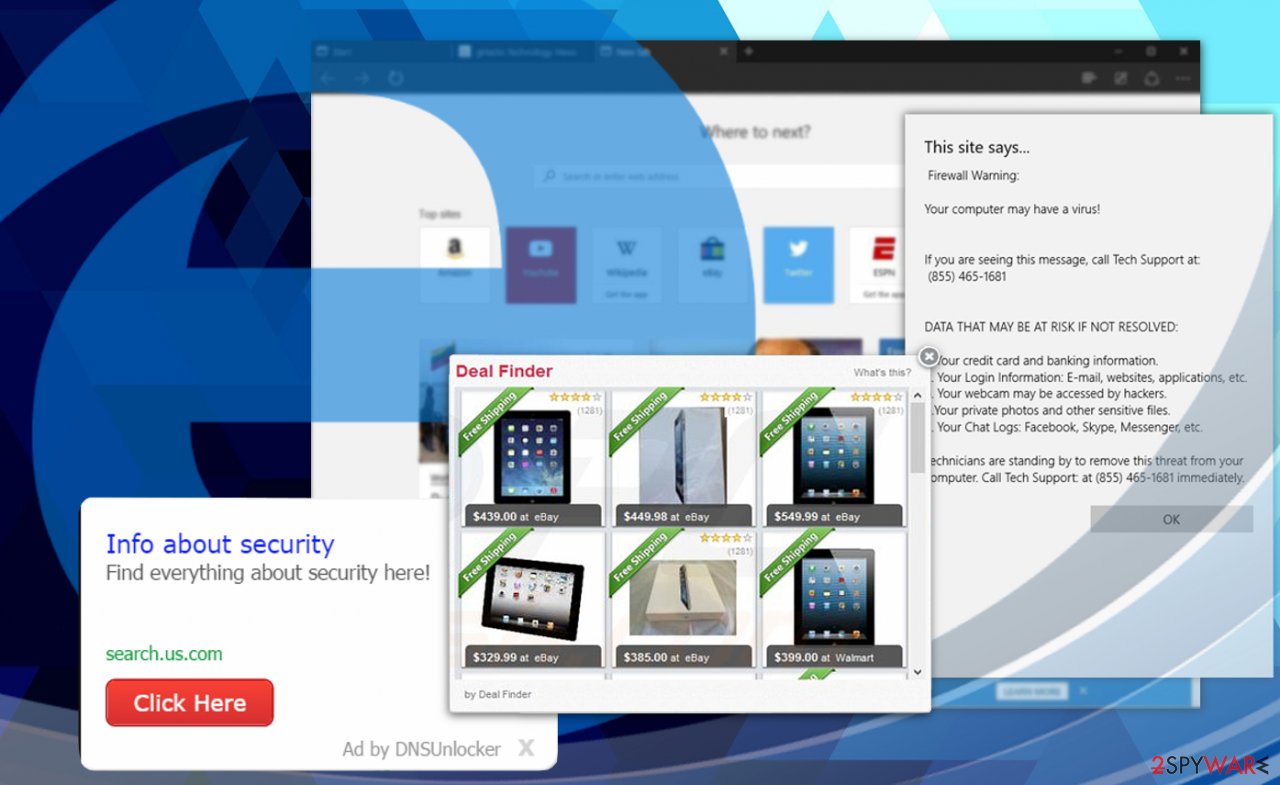
Adware is a type of potentially unwanted program (also known as PUP or PUA) that delivers advertisements, flashing pop-up windows, banners, in-text links, auto-play video ads, and other commercial content via web browsers or other means.
While adware is usually nowhere near as bad as malware, some security advocates ask for it to be called and treated as the latter.[1] Ad-supported program can initiate browser redirects to scam, phishing, or commercial content-filled sites – the activity is not only annoying but can also compromise user and computer safety and expose to various online threats.
The displayed advertisements are meant to grasp users’ attention and steer them straight to the affiliate websites, this way increasing their attendance and boosting their popularity or sales. That's why they include celebrity images, huge logos of well-known companies, or tempting sums of money that can seemingly be acquired quickly and without much effort.[2]
Due to the excessive amount of advertisements, adware-ridden browsers often become relatively difficult to navigate. In some cases, the infection might also cause other applications to crash, change some desktop icon functionality, and cause many other technical difficulties.
Ad-supported applications typically arrive at computers uninvited, as they are delivered via deceptive methods, so users rarely notice the entry point. Most users find PUPs installed on their systems after downloading freeware from third-party sites, trust deceptive ads, get tricked by a fake update prompt, or when they install the app intentionally without realizing that it has some troublesome features.
Finally, another annoying trait of these ad-supported programs is persistence techniques – many different methods are employed to stay on the infected computer as long as possible, displaying users ads that bring revenue to various third-parties. As a result, they struggle with adware removal and are looking for ways how to eliminate these uninvited guests.
Adware in 2021: What to expect from ad-supported app developers
Potentially unwanted software has been causing numerous problems for computer users worldwide, and they are constantly looking for ways to remove adware from their computers. Ad-supported programs became extremely prevalent, as multiple deceptive methods are used to deliver it to a large number of users on a daily basis.
Trends of adware did not change much for the past few years: an increasing number of people are struggling with infections on Macs, Androids, and iPhones, while Windows systems are becoming more prone to malware, such as ransomware or Remote Access Trojans. In particular, macOS users are currently the focus of adware developers, as distribution and prevalence methods are evolving for this platform, which is rapidly gaining popularity.
According to researchers, malware development (of which a big part is adware) for Macs outpaced Windows malware during 2019,[3], and this trend is believed to continue. Unfortunately, numerous Mac users still believe that their machines are immune to cyberthreats. Since they do not believe that they need third-party software to protect their devices,[4] versatile adware attacks become more prominent, and more users suffer from infections such as OSX/Shlayer.[5]
Thus, security experts suggest using adequate protection methods for computers, laptops, and mobile devices to prevent the need for often difficult adware removal. Here are some tips:
- invest in reputable security software;
- do not download suspicious programs or apps from unknown sources or created by unknown developers;
- install software properly, using Advanced/Custom settings to avoid infiltration of undesired apps;
- do not agree to download any browser extensions, toolbars or security programs from ads, pop-ups or redirect websites;
- beware of fake updates and bogus notification prompts about allegedly infected device.
Adware.gen – detection name that multiple security tools give to ad-supported software
Adware is a wide term used to describe numerous different applications that are used for displaying commercial content. Meanwhile, adware.gen represents a group of malware that shares similar features or belongs to the same family. Typically, reputable security programs can identify relations between these adware based on heuristic detection methods.[6]
Variations of adware.gen might also refer to more dangerous cyber infections than adware – for instance, Trojans that might steal banking information or credentials. Thus, if your browser or computer became sluggish due to the increased amount of ads, it’s recommended to scan the device with reputable security software for full PUP removal.
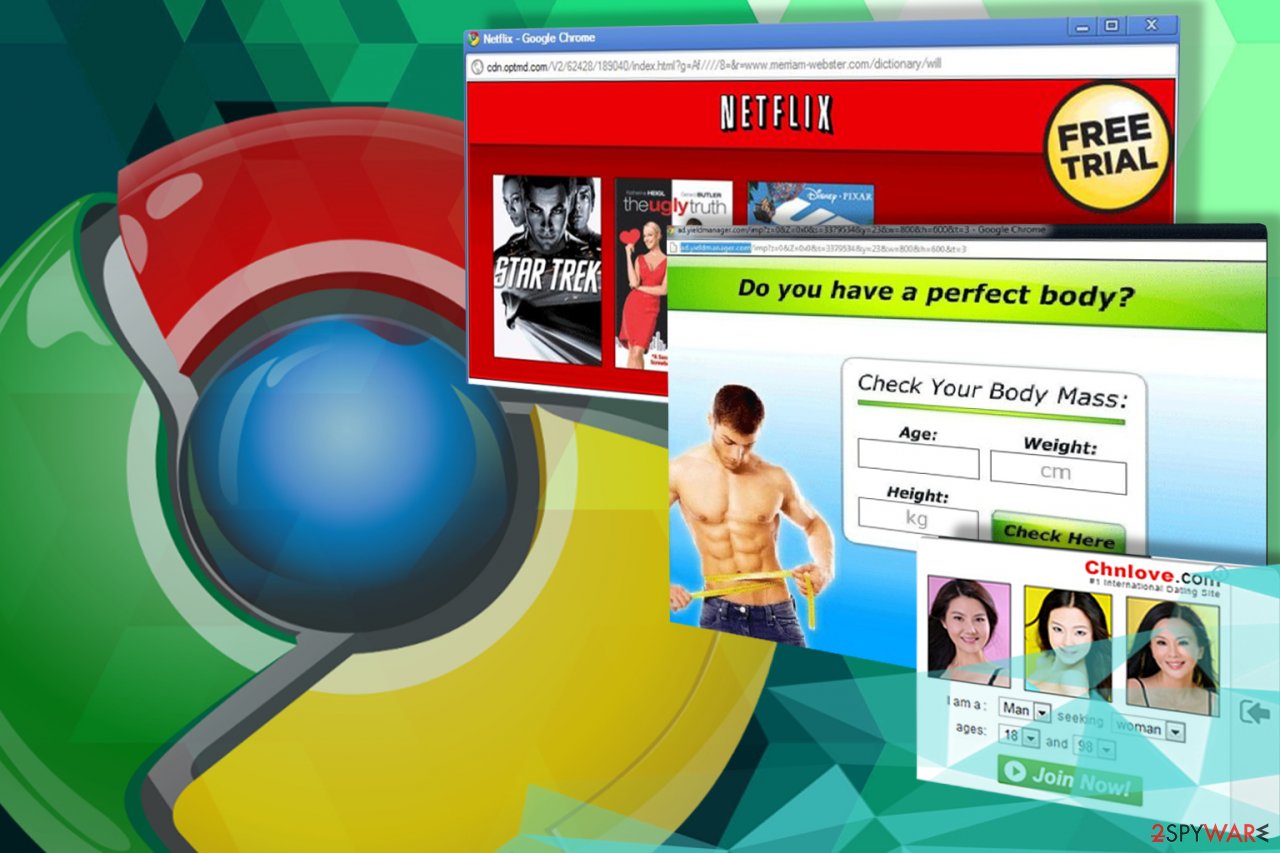
Adware functionality and different malicious techniques
When the adware targets a computer, it first deploys its malicious files on the system to be able to execute its intended functions. After this stage of the attack is complete, and the virus settles in, that’s when the hijack symptoms start taking their toll. Here is a list of the typical features that manifest on the infected devices and primary reasons for the adware removal:
- Pop-up ads, banners, and in-text links. This content is supposed to promote affiliate parties that are seeking to increase their popularity or sales.
- Redirects. Ad-based malware tends to reroute users to affiliate websites with or without their permission. Such activity is also initiated for trying to increase web traffic to these websites.
- Unauthorized installations. Often, the victims witness the attempts to install additional third-party software, the so-called browser helper objects (BHO’s)[7] without their permission. Unauthorized installations are typically used either to promote the software or to use it as tools for tracking user’s browsing habits. Keep in mind that such parasites are typically tricky to remove, so system scan with some security software is always recommended.
- Tracking. People’s activity on the Internet is of special interest to these ad-based programs. Gathering the information about their interests, mostly viewed websites, entered data, etc. allows advertisers to create more appealing content. Nevertheless, some of the more malicious programs may even endanger the more sensitive data such as logins, email address, computer’s IP address, and its location.
- System performance issues. Some parasites are poorly programmed, meaning they can cause various malfunctions, including system slowdowns and computer instability.
- Arbitrary updates. These potentially unwanted programs are capable of updating themselves via the Internet without notifying the user. This is why experts recommend to hurry up with the removal before the parasite residing on your PC receives an injection of some new malicious features.
- Adware removal prevention. Most of the ad-supported apps lack the uninstallation function, or it turns out to be useless. This persistence mechanism allows the program to continue operating on the computer without restrictions.
To remain stealthy, the adware may disguise its working components as elements of legitimate applications that help the malware run on the system undetected for an extended period of time. Of course, it all depends on a particular infection, but most of these parasites invade computers the same way Trojans do. Therefore, the previously listed behavior cannot be terminated that easily. In fact, the victims must remove the virus from the computer very carefully, so that no malicious components are left to continue running on the system.
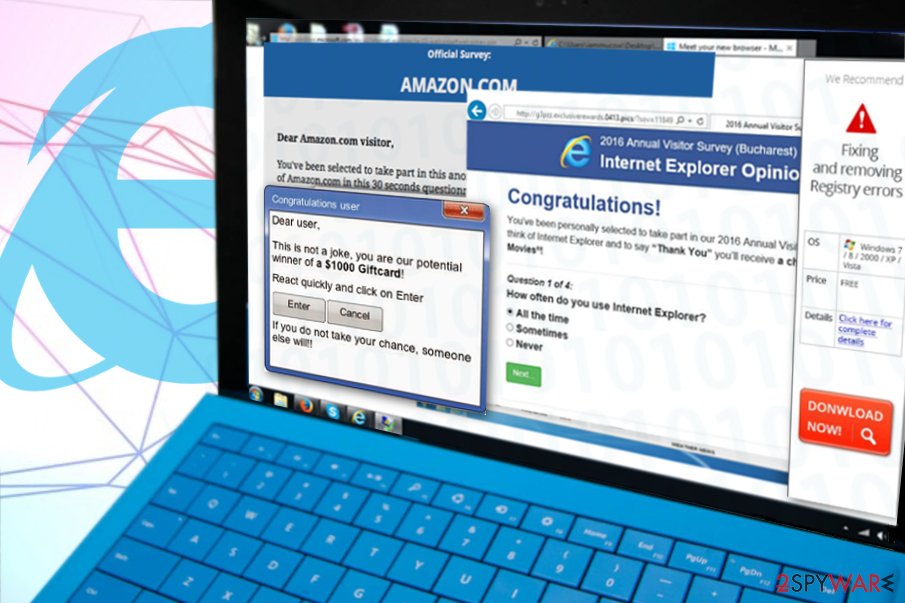
Adware distribution strategies used by developers
Adware programs do not spread around as malware does. For example, you are highly unlikely to find a malicious email attachment that installs adware on your machine. As we mentioned earlier, adware may apply Trojan-like principles for the system infiltration, but generally, it does not need additional software or special conditions to arrange and carry out a successful system hijack. Typically, such threats rely on three basic distribution techniques:
1. Misleading official websites
Most ad-supported programs have their official websites presenting them as handy tools, for instance, powerful browser add-ons, useful shopping assistants, or amusing gaming plugins. If you fall into believing that such an application is capable of helping you to save the money, you may end up with a nasty virus on your computer. That is why it is always recommended to conduct a little research and learn more about the program you are about to install before hitting the download button.
The latest reports reveal that you cannot be sure about the content you are presented even if you use the official stores, e.g., Google Play.[8] This is why it imperative to check user reviews and read up on unknown programs on social media platforms such as Reddit.
2. Fake pop-up ads
Clicking on misleading pop-ups can also be dangerous and may lead you to the infiltration of the annoying advertising programs. Such browser notifications typically “recommend” downloading missing software updates, various security products, free system scans, and propose similar attention-grabbing offers. Keep in mind that messages coming from your browser about malware infections or outdated Flash Player are fake. Security experts recommend ignoring such content and remind that the safest way to update/install the required programs is by accessing their official websites.
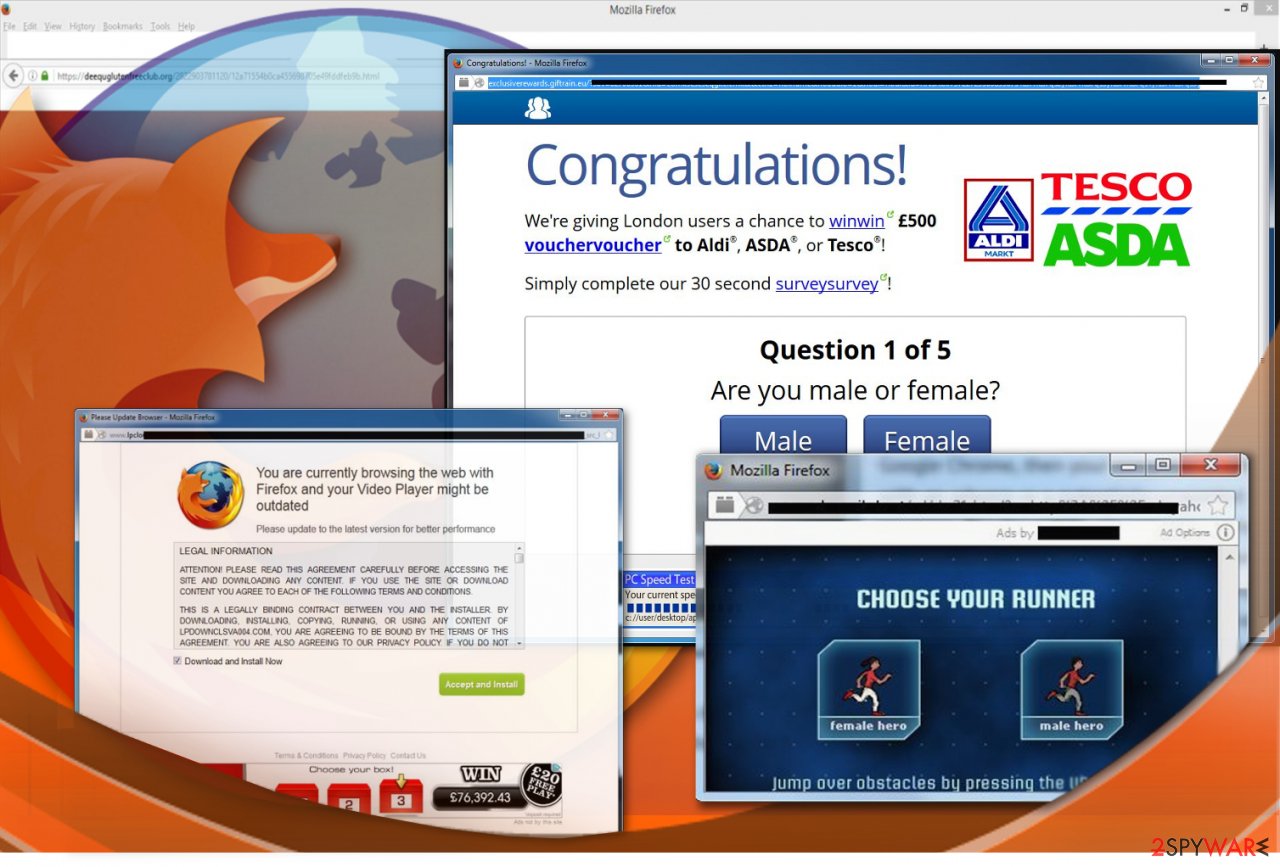
3. Bundling
There are lots of free programs (freeware and shareware) that have been bundled with adware. Such deceptive software packages are typically promoted on unreliable software sharing sites or peer-to-peer networks. If you tend to visit these places often, you may end up downloading a browser add-on, extension, plugin, toolbar with an advertising revenue-oriented parasite hidden in the list of recommended installs.
The worst part of the hijack is that even if you remove the host application, it will not help to get rid of its undesirable companion. Only the professional tools, such as anti-malware or antivirus suites can really banish it from the computer. This distribution method is the most common when promoting similar parasites, such as browser hijackers. To protect themselves, users should always select either “Custom” or “Advanced” installation modes when setting up freeware on their computers.
Adware removal guide for different browsers
Adware might be an extension that attaches itself to the web browser. In such a case, the best way to get rid of adware is to uninstall the unwanted plugin. However, similarly to the installable applications, extensions might also be difficult to eliminate due to changed web browser settings.
Adware can affect all popular web browsers, such as Google Chrome, Mozilla Firefox, Internet Explorer, and Safari, that are installed on Windows and Mac computers. Adware removal is similar to each of the web browsers. Typically, it requires uninstalling the suspicious add-on and resetting the browser. Though, we would briefly explain how to remove adware from popular browsers.
Removing adware from Chrome
Google Chrome is one of the most popular browsers to be targeted by greedy advertisers, so its users are constantly looking for professional removal advice. Sadly, there is no magic technique that will rid the system of all malware without exception. Indeed, though their working principles may be similar, every virus is unique so adware removal strategies must be fitted according to the particular infection.
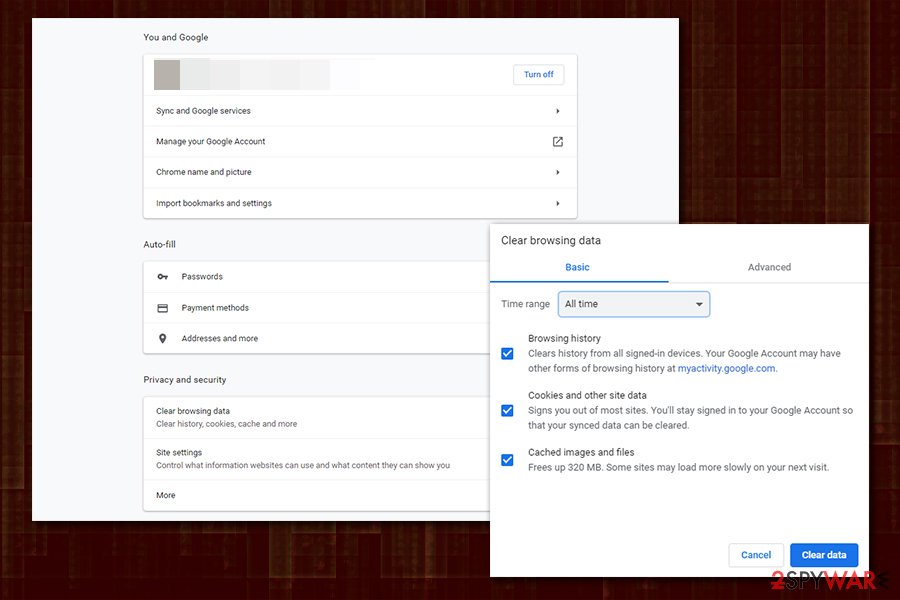
For some infections, a simple browser reset may suffice, while other adware might be extremely persistent in Chrome. Additionally, even after Chrome adware removal, its settings can remain on the system. To ensure this does not happen, it is advisable to clear web browser data:
- Click on menu (three vertical dots) located at the top-right corner of the window
- Go to Settings
- Under Privacy and security section, click on Clear browsing data
- Select All time from the drop down menu under Time range
- Select the required fields (some are optional, but ensure that Cookies and other site data is ticked) and click on Clear data
Additionally, some settings linking you to malicious websites and showing you ads might be stored on Google's servers. To stop this from happening, you need to reset sync of your Google account. For that, visit the sync page and click on the RESET SYNC option at the bottom.
Getting rid of adware in Internet Explorer
Despite what most users may think, browser recovery does not necessarily start with the reset (go to Explorer reset instructions). The notion results in complete loss of all browser extensions, as well as preferred settings for it. Therefore, you should first access the list of add-ons and delete the unfamiliar entries and see if ads disappeared. Additionally, you can also try to delete browser data and cookies that accumulated over time. If these steps did not help, you may then perform the browser reset.
If you are using Internet Explorer, it might be that your computer is also running an older version of Windows. In the past, IE has been scolded by users for being prone to malware attacks. This is probably one of the reasons Microsoft has turned to Microsoft Edge in Windows 10 and also rebuilt it in with a new release of Chromium-based Edge in January 2020. In any case, the use of Internet Explorer is highly discouraged, as it is a slow, vulnerable, and outdated version of a modern-day browser.
Fix Microsoft Edge after the adware attack
Microsoft Edge is a new and improved browser from Microsoft designed specifically for Windows 10 operating systems, although the Chromium-based version is available on all platforms, including macOS. Unfortunately, despite the refined cyber attack resistance capacities, this browser also gets targeted by malware, and the parasites that infect it often apply advanced techniques to achieve that.
The next-gen malware may also hide on the system preventing adware removal from Edge. You may bypass these obstacles by employing anti-malware tools and using them to scan the infected system. This way, you will remove the malware from your computer much quicker and will be able to get back to your default Microsoft Edge settings sooner as well. If you need help, follow Edge reset instructions.
Instructions for Chromium-based MS Edge
It is not a secret that the new Edge has nothing to do with the latter – even the icon does not resemble the old version of the browser at all. Microsoft has indeed improved multiple aspects of the program – Edge is not faster, feature-packed, and more secure. Unfortunately, it is still vulnerable to adware attacks, especially now that Chrome extensions are now compatible with the browser.
If you use MS Edge as your main browser, you should not forget to clean it well if you found that adware managed to infiltrate it. Delete cookies and browsing data in order to keep the unwanted app from operating. If that fails, the browser can be quickly reset and the leftovers deleted with powerful anti-malware software.
Remove adware-related components from Mozilla Firefox
Mozilla Firefox runs both on Windows and macOS operating systems, which tempts malware creators to use it for their attacks. They may hide the virus files inside the system in order to prevent the victims from eliminating Mozilla Firefox adware properly.
Luckily, reputable security utilities block the malicious activities and remove the infectious components from the system, so be sure to run a system scan with one of such tools to get back to your regular browsing safely. Do not forget to reset Mozilla Firefox default parameters when the system scan is done! Click the link “How to reset Mozilla Firefox?” or type this into the search bar on the top right corner of the screen to find a bunch of useful browsers reset tips prepared by our experts.
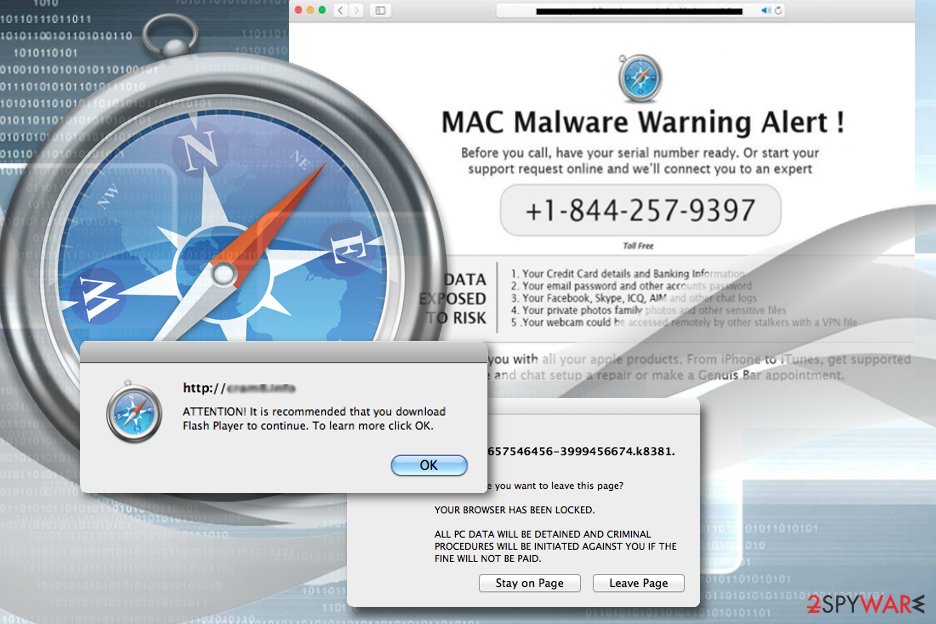
Stop ads and redirects in Safari
Safari is no longer a safe haven where Apple users can hide from malware. There are numerous ad-revenue hungry programs that infect these browsers as well. Fortunately, our experts have accumulated a sophisticated knowledge base that is used to compile tutorials that help desperate users remove adware from Macs and its signature browser. You may use these removal guidelines next to all the new Safari-based threats.
Despite the usual success of manual elimination, numerous cases have also shown that such a computer cleanup approach can be complicated because potentially unwanted programs typically travel around bundled with various other components. To avoid leaving unwanted files on your computer, you should always rely on specialized virus-fighting software and clean your device automatically. However, you should always read reviews of reputable security experts to prevent fake security software on your Mac.[9] Additionally, after the automatic scan, Safari reset might also be needed.
How to remove adware effectively and prevent its return
The most reliable way to remove adware and its components from the corrupted devices is by using a legitimate anti-spyware program. In this case, you should choose carefully because there are lots of misleading reviews on the Internet that may praise completely useless products. Always read the reviews or consult security advisors before obtaining one just to be safe.
Keep in mind that only reputable and acknowledged anti-malware software has regularly updated virus databases which allow them to detect and eliminate the latest malware infections. Besides, investing in such tools will pay off in the future as they will prevent malware attacks. Our team recommends cleaning computers from adware using reputable security tools like SpyHunter or Malwarebytes Anti Malware.
Our recommended programs can easily detect and eliminate the latest cyber threats and also protect from their reinstallation. Though, before running a full system scan with anti-malware tool, you should update it. It helps to make sure that your software has an up-to-date database and can clean all related entries.
Nevertheless, you should remember that the automatic scan will only delete the adware components from your computer, whereas you will have to perform the browser reset yourself.
How to remove adware from Android
Mobile devices have seen significant improvements when it comes to their operation and usability. Currently, technical specifications for Android phones or tablets can often compare to many laptops or desktop computers, as processing power has been increased tremendously. In other words, mobile devices should be treated similarly as workstations, including safety procedures.
That being said, Android viruses and adware have been plaguing this versatile operating system for several years now. As a result, users keep looking for ways on how to remove adware from Android systems for good. However, this process might be by far more difficult than it is on a desktop computer or a Mac.
Typically, users get infected with adware or malware on Androids when they download applications from third-party sources. There are millions of apps available on the official sources, although, for some reason, users still visit suspicious sites and download malware on their devices to this day. To avoid getting infected with Android threats, users should only opt for official sources such as Google Play.

Google and other reputable companies use effective scanners that prevent malicious applications from being placed on its official store. However, some malware manages to slip in even pas IT giant's defenses, as Google was forced to pull out a multitude of applications that showed disruptive ads,[10] gathered sensitive information, used malvertising, proliferated other malware, etc.
To remove adware from Android, users should first go to Settings > Apps & notifications/Apps section and remove everything that looks suspicious. However, some malicious apps grant themselves elevated permissions on the device, preventing users from removing them. To avoid that, you should access Safe Mode on your phone/tablet and then uninstall the rooted app for good. Note: instructions on how to reach the mode differ based on the OS version and the brand of the phone.
Finally, you should employ a reputable anti-malware program and scan the device thoroughly. Note that there are hundreds of useless “security” apps on Google Play that do not only fail to remove adware and malware but also are causes of persistent advertisements. Thus, we suggest using independent lab test results by such bodies as AV-Comparatives.
In some cases, ads on Android can be caused by notification prompts that were accepted by accident, or users were tricked into doing so. To stop that from happening, follow these steps on Chrome:
- Tap on three dots at the top-right and pick Settings
- Scroll down and select Site settings
- Go to Notifications section
- You will see a list of blocked and allowed websites – remove the ticks from all suspicious websites on the list.
- ^ Thomas Claburn. Let adware be treated as malware, Canuck boffins declare after breaking open Wajam ad injector. The Register. Biting the hand that feeds IT.
- ^ Alana Mitchelson. Why fake celebrity endorsement ads are so successful in scamming Australians. The NewDaily. Free news for all Australians.
- ^ Danny Palmer. Mac malware threats are now outpacing attacks on Windows PCs. ZDNet. Technology News, Analysis, Comments.
- ^ Jeffrey Esposito. Wait, my Mac can be infected?. KasperskyLab. Security news from the global cybersecurity company.
- ^ Anton V. Ivanov, Mikhail Kuzin, Ilya Mogilin. Shlayer Trojan attacks one in ten macOS users. SecureList. Kaspersky security blog.
- ^ What is Heuristic Analysis?. Forcepoint. Cybersecurity blog.
- ^ Browser Helper Object. Wikipedia, the free encyclopedia.
- ^ May Ying Tee. More Fraudulent Apps Containing Aggressive Adware Found on Google Play. Symantec Blogs. Efficient investigation, and remediation processes.
- ^ Lily Hay Newman. One of most popular Mac apps acts like spyware. Wired. Magazine focusing on how emerging technologies affect culture, the economy, and other themes.
- ^ Babu Mohan. Google pulls 600 apps from the Play Store for serving 'disruptive' ads. AndroidCentral. News, Reviews, Deals & Help on Android.
Latest adware added to the database
Remove Woodrating4.xyz ads
Removal of Precludestore.com ads
Remove Wait4me.space scam
Information updated: 2021-06-07