How to remove keyloggers
A keylogger (also known as keystroke logger)[1] is a software that monitors and records each keystroke on a keyboard and saves this information in a file or remote server. The program can collect information from computers, laptops, smartphones, and other mobile devices. Usually, such software is associated with spyware and is used for stealing passwords, logins, credit card information, and similar information.
Keyloggers can be both, legal and illegal. Such tracking applications can be used in workplaces or by researching user's behavior on computers or other gadgets.[2] Cybercriminals often take advantage of such “spying” programs too to steal personal information. However, even legal programs work without the monitored user’s knowledge and consent. Malicious actors can also use them. Therefore, these tools shouldn't be classified as less harmful threats than certain parasites.
If you suspect that your keystrokes might be recorded and used for illegal purposes, you should not hesitate and check the system with a reputable anti-malware software. A professional and up-to-date tool should detect and remove keylogger immediately. After that, changing all your passwords and monitoring bank transactions are crucial tasks to protect your privacy.

The difference between hardware and software keyloggers
There are two types of keyloggers available on the market:
- hardware
- software
The hardware keylogger is a small physical device that can be dropped between the keyboard’s plug and the computer’s keyboard port. A hardware keylogger records all keystrokes and saves them into its own memory. Such a device does not rely on a particular software or a driver. Therefore, it can work in different environments. However, it does not take screenshots and can be easily found during a thorough computer inspection. Software keyloggers are divided into parasitical and legitimate applications.
Malicious keyloggers are very similar to viruses and trojans. They are used by hackers to violate users' privacy. Legitimate keyloggers, also known as computer surveillance tools, are commercial products targeted mostly to parents, employers, and teachers. They allow to find out what children or employees are doing online.
Ilegal and malicious use of the keylogger
Practically all keyloggers seek to violate user's privacy. They can track their victims for months and even years until they are noticed.[3] During all this time, a regular keylogger is capable of finding out as much information about the user as possible. Someone who controls a keylogger gets priceless information, including passwords, login names, credit card numbers, bank account details, contacts, interests, web browsing habits, and much more. All this information can be used to steal the victim's documents and money.
The main features of the keyloggers
- Logging keystrokes on the keyboard.
- Taking screenshots of the user's activity on the Internet at predetermined time intervals.
- Tracking user's activity by logging window titles, names of launched applications, and other specific information.
- Monitoring user's online activity by recording the addresses of visited websites, entered keywords, and other similar data.
- Recording login names, details of various accounts, credit card numbers, and passwords.
- Capturing online chat conversations on instant messengers.
- Making unauthorized copies of outgoing and incoming e-mail messages.
- Saving all collected information into a file on a hard disk, and then silently sending this file to a required e-mail address.
- Complicating its detection and removal.
Keyloggers cannot be compared with regular computer viruses. They do not spread themselves as these threats do and, in most cases, must be installed as any other software. However, the latest examples of ransomware have also been found to have keylogger capabilities. Unfortunately, this can reveal the fact that viruses will become even more sophisticated in 2019.[4]
Methods used to spread and install keyloggers on the system
As you already know, keyloggers can be legal and illegal. However, both of them are usually installed without the user's knowledge, but this task achieved using different methods.
- A legitimate keylogger can be manually installed on the system by the developer,[5] system's administrator, or any other user who has needed privileges for this activity. A hacker can break into the system and set up his keylogger. In both cases, a privacy threat gets installed on the system without the user’s knowledge and consent.
- Malicious keyloggers can be installed on the system with the help of other parasites, such as viruses, trojans, backdoors, or other malware. They get into the system without the user's knowledge and affect everybody who uses a compromised computer. Such keyloggers do not have any uninstall functions and can be controlled only by their authors or attackers.
In most of the cases, keyloggers affect computers running Microsoft Windows operating system. However, all viruses are constantly updated, so there is no guarantee that they are not capable of hijacking other popular platforms.
Examples of the most dangerous keystroke loggers
There are lots of different keystroke logging applications, both commercial and parasitical. The following examples illustrate typical keylogger behavior.
All In One Keylogger
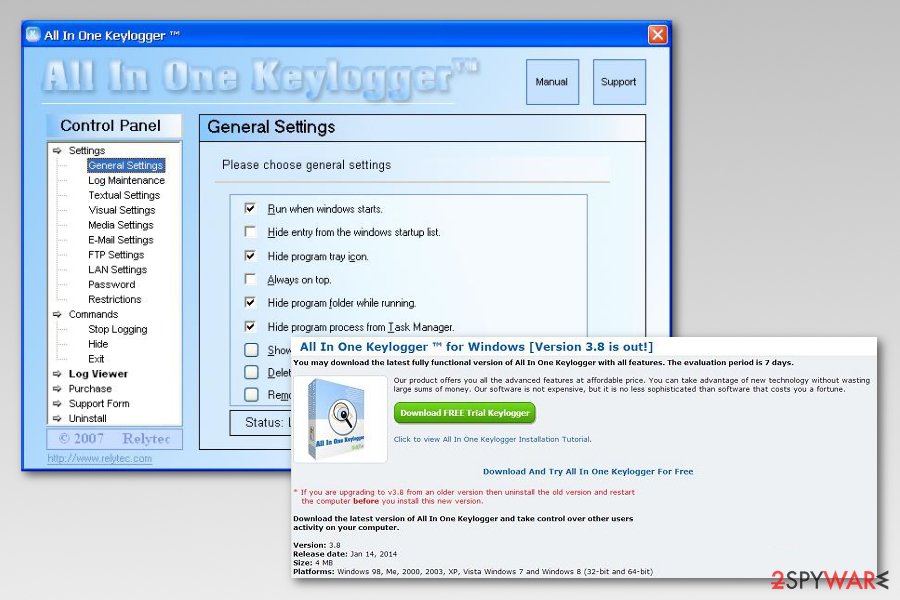
All In One Keylogger is a malicious program targeted at PC users and their personal information. Typically, people who work behind it, seek to steal as much information as possible. AllInOne KeyLogger is designed to record all user's keystrokes, take screenshots and initiate other activities. You can hardly notice this threat on your computer as it hides deep inside the system.
Ardamax Keylogger
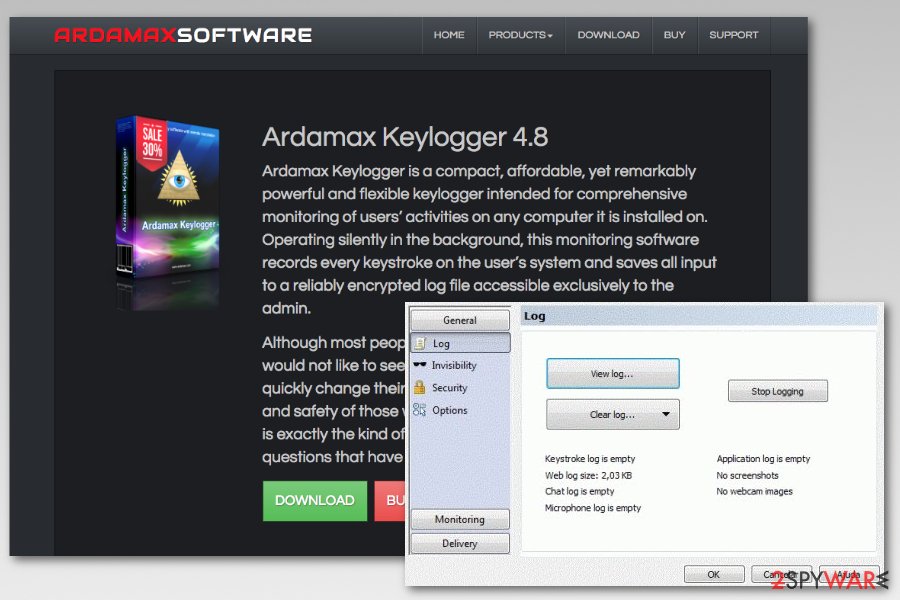
Ardamax Keylogger is a legitimate program that was created for professional usage. However, cybercriminals managed to compromise 4.6 version of the program and used it for malicious purposes. Once users downloaded the program from the official website, the program started collecting keystrokes, recording audio, and using visual surveillance which was sent to the remote criminals' server.
Invisible Stealth Keylogger
Invisible Stealth Keylogger is the harmful trojan horse with keystroke-logging functions. This parasite not only records every user's keystroke but also gives the opportunity for the remote attacker to have unauthorized access to a compromised computer. He or she can easily download and execute arbitrary code, steal user’s vital information (passwords, e-mail messages or bank account details). Once it collects the needed amount of data, this threat sends it to the attacker through a background Internet connection. Moreover, they can cause general system instability and even corrupt files or installed applications.
Perfect Keylogger
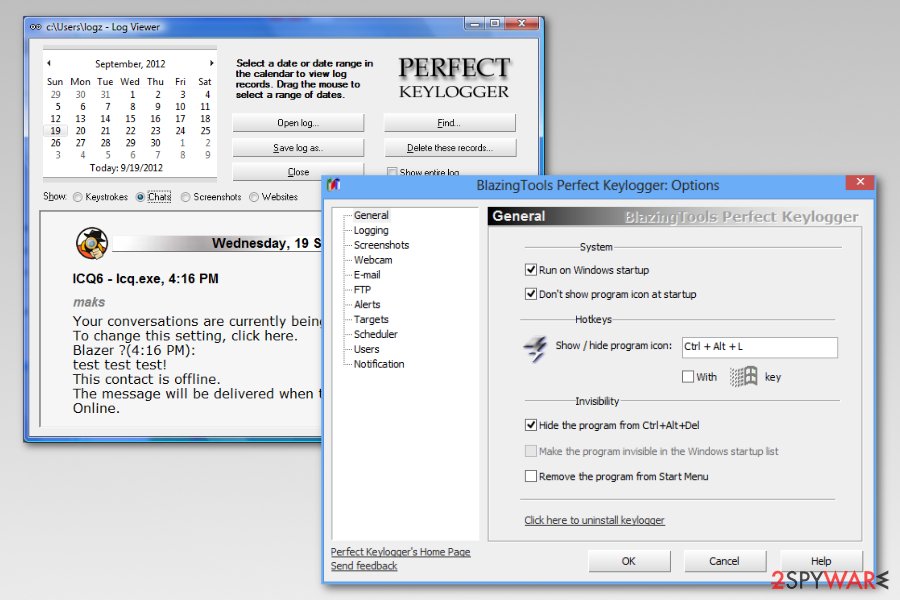
Perfect Keylogger is a complex computer surveillance tool with rich functionality. It records all user keystrokes and passwords, takes screenshots, tracks user activity on the Internet, captures chat conversations and e-mail messages. Perfect Keylogger can be remotely controlled. It can send gathered data to a configurable e-mail address or upload it to a predefined FTP server. Although it is a commercial product, it’s even more dangerous than most parasitical keyloggers.
Remove Keylogger with reputable security software
There is no doubt that keylogging software poses a serious danger to user's safeness.[6] Keylogger removal must be performed as soon as possible. As you already know, these types of programs can steal personal information and use it for further cybercrimes. Keystroke loggers might be hiding in the system and be invisible in the Task Manager. For this reason, you should use reputable anti-virus/anti-malware software to detect and eliminate this cyber threat.
Also, make sure you fix the virus damage by running a full system scan with FortectIntego. It will recover your system to its previous state by eliminating changes initiated by the malware. If you have some difficulties and cannot remove Keylogger from the device or fix errors that it caused, you can share your question with us using the Ask Us page. We will be glad to help you solve your problems.
Steps to take after keylogger removal
Once you get rid of the keylogger, you should also take care of your personal information:
- Change all of your passwords (email, social media, bank, etc.);
- Set strong and unique passwords for each account;
- Enable two-factor authentication to strengthen your accounts;
- Monitor your banking transactions and if you notice suspicious transactions, inform your bank directly;
- Install and regularly update antivirus software to make sure that any keyloggers are not trying to steal your personal information.
- ^ Keystroke logging. Wikipedia, the free encyclopedia.
- ^ Leah Heilbrunn. How Much Does Your IT Department Know About You?. Tom's Hardware. Helps you buy the best hardware and build the best PC to play, create and work.
- ^ Bradley Barth. Android spyware BusyGasper has many features, but few known victims. PC Authority. A leading Australian magazine publishing business focusing on providing passionate communities with the information they seek.
- ^ Catalin Cimpanu. New Virobot malware works as ransomware, keylogger, and botnet. ZDNet. Delivers 24/7 news coverage and analysis on the trends, technologies and opportunities that matter to IT professionals and decision makers.
- ^ HP laptops found to have hidden keylogger. BBC News. All the latest news about Cyber-security from the news giant.
- ^ Violet Blue. FEATURE Keyloggers: Beware this hidden threat. PCWorld. The dedicated to helping tech users of all experience levels get more from the hardware and software that's central to a PC-centric universe.
Latest keyloggers added to the database
Delete SpyBossPro
NetSpy removal guide
How to remove Hooker Trojan Keylogger
Information updated: 2021-01-11



