Security Tool (Virus Removal Guide) - Jul 2019 update
Security Tool Removal Guide
What is Security Tool?
Security Tool is a rogue anti-malware program that generates misleading alerts and fake virus warnings to make users buy its full version
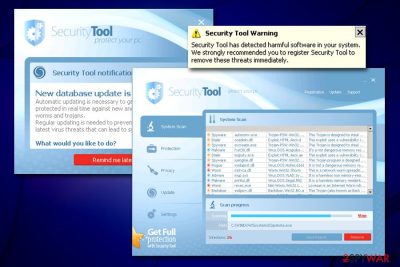
Security Tool is a scareware[1] program that targets less experienced computer users after being installed along with other free software from the internet. In other cases, users might think that it is a legitimate tool that can protect the PC, despite being a virus itself.
As soon as the Security Tool virus is installed, it immediately performs an alleged full system scan, and flags hundreds of fake threats. This behavior is deliberate and typical to rogue anti-spyware programs, as their main goal is to make users believe that their computers are infected with malware. As evident, it is merely a scam, as the Security Tool developers only want to make users purchase the registered version to remediate the bogus infections.
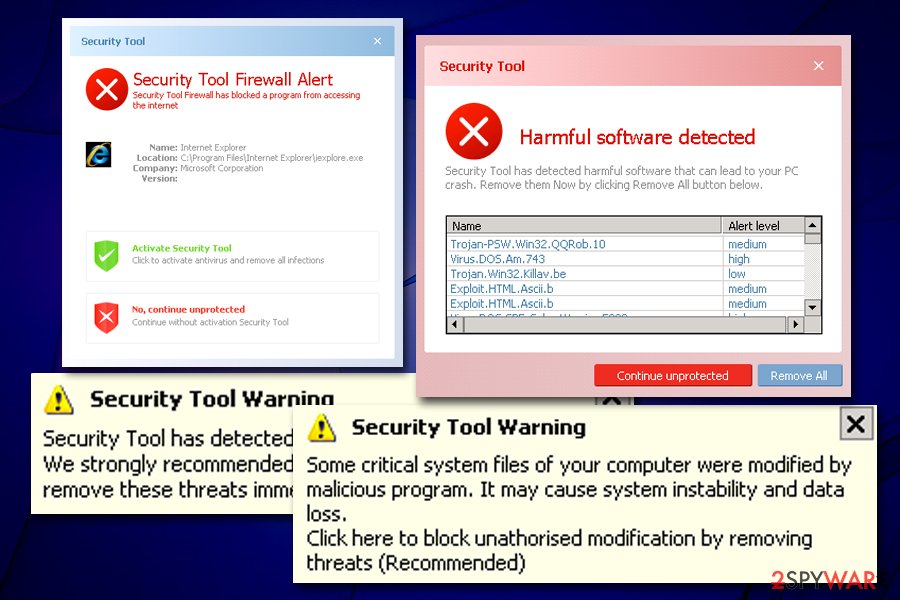
Besides showing fake scan results, Security Tool also engages in intrusive behavior, such as displaying pop-up messages and prompting users to buy its full version. Additionally, if the malware detects Mozilla Firefox or Internet Explorer installed on the system, it will block users from accessing the internet altogether. Finally, the victims will also not be able to launch any programs installed on the device because Security Tool malware will display a dialog message claiming more infections.
| Name | Security Tool / SecurityTool |
| Type | Rogue anti-malware |
| Category | Malware |
| Also known as | Win32/Winwebsec, Security Tool 2011, Security Tool 2012 |
| Infiltration | Software bundles, malicious third-party sites |
| Symptoms | Software does not allow to access the internet and also prevents startup of most programs installed on the device; displays countless fake messages claiming malware infections and asks to buy its registered version |
| Risks | Money loss, computer system compromise |
| Termination | Install security software like FortectIntego or SpyHunter 5Combo Cleaner and perform a full system scan in Safe Mode |
The malicious application is from the same family as Total security 2009 and System Security and many other similar rogue programs that work the same way: display fake scan results in order to make users purchase the registered version. Indeed, Security Tool closely reminds fake alerts that stem within browsers in tech support scam[2] schemes. While browser-based alerts are entirely harmless if not interacted with, hoax programs inject their code into the operating system, similarly how malware behaves.
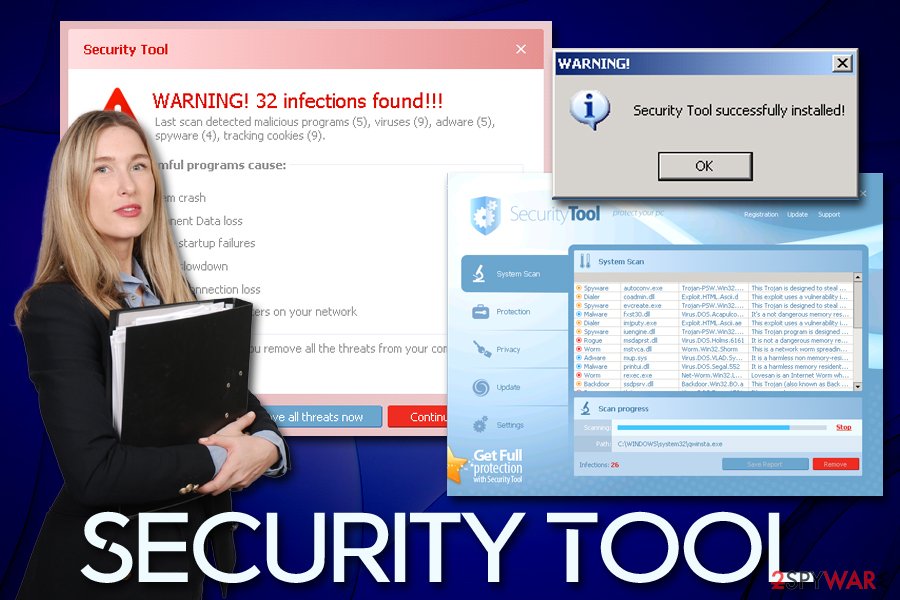
Upon successful installation, Security Tool will display the following message:
Warning!
Security Tool successfully installed!
Unfortunately, that also means that Windows system files are significantly altered, and the infection has been established. Before that, Security Tool malware will engage in the following changes of Windows OS:
- Creates a directory %COMMON_APPDATA% or %APPDATA% and inserts a randomly named executable;
- Modifies HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN registry key to allow its launch with each system boot;
- Creates shortcuts on the desktop and Start/Programs;
- Replaces desktop wallpaper without permission;
- Prevents users from opening most of the installed programs;
- Displays fake notifications on Internet Explorer or Mozilla Firefox, preventing Internet access.
Due to these changes, Security Tool removal might be difficult. Nevertheless, possibly the safest way to terminate the application is by entering Safe Mode with networking and performing a full system scan with tools like FortectIntego or SpyHunter 5Combo Cleaner.
Under no circumstances should you purchase the malicious application, as you will only waste your money. Besides, disclosing credit card details to scammers is not a good idea either, as it can result in serious privacy issues or even identity theft. Instead, you should immediately remove Security Tool malware from your computer, because you will not be able to operate it as usual.
Before installing the software you are not familiar with, read up on it online
There are two ways for the rogue anti-spyware to get onto your PC: you either installed it intentionally thinking it is a legitimate security tool or it got inside your machine during the installation of shareware/freeware. Both of these methods can be avoided, as long as enough attention is paid.
Before installing any applications you never heard of, you should always check more details about it online, preferably from multiple sites. Be aware that fake reviews can be created, so trusting one source is not adequate. Besides, check if the app you are about to install provides important documents, such as Privacy Police or EULA/Terms of Service. Security experts[3] also recommend staying away from torrent sites, as malware is often bundled together with the offered apps. To avoid that, always decline all the deals/offers and pick Advanced/Custom settings so that you would be able to remove pre-selected boxes.
Delete Security Tool virus using reputable anti-spyware
When a non-malicious application is installed onto the operating system, it does not create malicious entries within the registry or other parts of the OS. For that reason, uninstalling programs via the Control Panel or the Apps list is a relatively easy task. However, due to its malicious nature, manual Security Tool removal might be just way too complicated for regular computer users.
Therefore, you should simply install powerful security software and perform a full system scan. As we previously stated, the Security Tool virus stops most of the other applications from being launched, so the legitimate anti-malware might not be able to start. In such a case, you should enter Safe Mode with Networking – a safe environment where the operation of most malware is temporarily disabled (note that such threats like rootkits[4] might still run even in Safe Mode).
Once you get to the Safe Mode, perform a full system scan using anti-malware tool – it should remove Security Tool and all its components from the system.
Getting rid of Security Tool. Follow these steps
Manual removal using Safe Mode
To delete Security Tool malware from Windows OS safely, enter Safe Mode with Networking as explained below:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Security Tool and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting rogue antispyware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Paul Gil. What Exactly Is 'Scareware'?. Lifewire. Tech untangled.
- ^ Protect yourself from tech support scams. Microsoft. Windows security support.
- ^ Udenvirus. Udenvirus. Security advice from Denmark.
- ^ Rootkit. Techopedia. Where IT and Business Meet.














