XData ransomware / virus (Removal Guide) - updated May 2017
XData virus Removal Guide
What is XData ransomware virus?
After using XData ransomware to cause havoc in Ukraine, hackers publish master decryption keys
Xdata virus operates as the ransomware that encrypts files with AES encryption algorithm[1]. The malicious program seems to be attacking Ukraine mainly, although there are victims in Russia, Estonia and Germany[2]. The virus presents quite a plain design as it does not launch its specific GUI. Instead, it opens HOW_CAN_I_DECRYPT_MY_FILES.txt with the instructions how to locate ID and contact hackers via email addresses. Surprisingly, the perpetrators present even 6 of them: beqins@colocasia.org, bilbo@colocasia.org, frodo@colocasia.org, trevor@thwonderfulday.com, bob@thwonderfulday.com, bil@thwonderfulday.com. The domain names suggest that hacker was in a good mood generating the malware, however, victims of this malware experience the feeling far from joy. Not only their files now are marked with .~xdata~ file extension, but they remain locked as well. Furthermore, it seems that the malware is designed based on the trojan which has emerged several years ago – HEUR:Trojan.Win32.Generic. Furthermore, it seems that the malware uses more than 20 IP addresses to cover tracks. Until the decryption tool will be created, we recommend you to proceed to Xdata removal. For that purpose, you may find FortectIntego or Malwarebytes useful.
UPDATE: On 30 May, 2017 hackers revealed master decryption keys of XData ransomware. Thanks to that, Kaspersky and Avast have already released decrypters for this virus. You should run them right after removing the virus from your system.
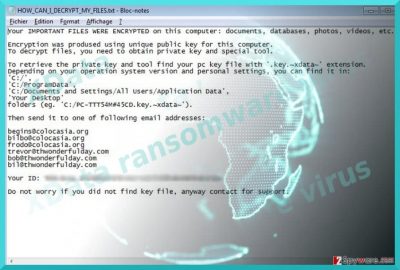
The ransom note suggests that the malware employs ordinary encryption method, specifically public key to encode netizens‘ data. As a rule, in order to decrypt the files, users need to obtain a unique private key. The cyber criminals seem to be using Command and Control server to store the key. This feature also grants more flexibility to manage several registered domains and, likewise, grant more anonymity. Furthermore, the penetrators ask users to find their ID by locating the file with .key.~xdata~ file extension. Then, they should contact hackers via indicated email addresses. The ransom note left by Xdata ransomware does not present any specific amount of ransom. Such peculiarity might be explained from two perspectives: either the hackers forgot to provide it, or they are ready for negotiations. In any case, we do not recommend contacting the criminals. It is understandable if you decide to risk paying the money but note that there is no guarantee that the hackers will return the files[3]. Thus, you might want to remove Xdata completely.
Starting with the first day of xData ransomware appearance, researchers noticed that the virus mainly rampages in Ukraine[4]. Surprisingly, they report that the virus managed to infect four times more computers than an infamous WannaCry succeeded in a whole week. What’s shocking is that WannaCry was mainly acting on a global scale, while the new computer virus targets only one country mainly. There is no surprise that X Data virus managed to jump into the second position of the most active ransomware families on May 19, and the only virus that it failed to surpass was Cerber.

Methods used to distribute ransomware
There are several distribution methods used by hackers to increase the number of computers infected with ransowmare. Most popular of them is targeting users with spam emails. Note that emails which report about undelivered packages, present invoices or another important documents might be fake and hide a highly troublesome virus. Thus, by opening such file, you may allow XData ransomware or another ransomware[5] to infect your computer. The ransomware starts these processes on an infected host – msaddc.exe, mscomrpc.exe, msdcom.exe, msdns.exe, mssecsvc.exe, mssql.exe and msdcom.exe. To lower the risk of infection, proper security application should be installed. If you already have one and it just quarantined one of the following detections – Trojan.Heur.TP.E72C6B, Gen:Trojan.Heur.TP.eqW@baZ37zo or Ransom_XDATA.A, you should know that XData virus just attempted to encrypt files on your system.
Xdata ransomware removal
When it comes to ransomware removal, users should opt for automatic elimination method. Unless you are an IT security specialist yourself, it would be futile to track all malware files which are spread throughout the entire system. Only after you remove Xdata virus, you may proceed data recovery instructions. Some of them might be of use to you. Lastly, if you are about to enable new browser extensions or install new applications when UAC message pops up and asks you to enable the installation of new files, beware of the above-mentioned executable files. If the program, downloaded from entertainment websites, asks you to enable msaddc.exe or msdcom.exe, you should be alerted because you might need to think about XData ransowmare removal after enabling them.
Getting rid of XData virus. Follow these steps
Manual removal using Safe Mode
This option should help you recover control of the device, in case the malware shuts down anti-virus tools and prevents you from terminating it any other way.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove XData using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of XData. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove XData from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by XData, you can use several methods to restore them:
Data Recovery Pro option
It is promoted as a tool which is able to recover damaged files and even recover lost emails.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by XData ransomware;
- Restore them.
The benefits of ShadowExplorer
There are fair chances that you might recover your files if you use this program. It uses shadow volume copies as patterns to recreate wanted files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Use XData decrypters to recover your files
If infected with XData ransomware, you should know that its creators have already released master decryption keys of this virus. Thanks to that, experts from Kaspersky and Avast have already updated/released their decrypters. To recover your files, you can use either RakhniDecryptor or a free decryption tool by Avast.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from XData and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ S!Ri. Tweet by @siri_urz. Twitter. Online News and Social Networking Service.
- ^ MalwareHunterTeam. Tweet by @malwrhunterteam. Twitter. Online News and Social Networking Service.
- ^ Jeffrey Esposito. Hospital learns the hard way why you don’t pay ransomware crooks. The Kaspersky Lab Blog. Information to Help Protect you Against Viruses, Spyware, Hackers, Spam & Other Forms of Malware.
- ^ Lily Hay Newman. Another Ransomware Nightmare Could Be Brewing in Ukraine. WIRED. In-Depth Coverage of Current and Future Trends in Technology.
- ^ Israel Barak. Here’s everything you need to know about ransomware. Tech City News. IT News and Comments.





















