Alpha ransomware / virus (Virus Removal Guide) - Oct 2020 update
Alpha virus Removal Guide
What is Alpha ransomware virus?
Alpha ransomware is a file-locking PC infection that delivers a lengthy ransom note
Alpha ransomware, otherwise known as Alfa virus, is a malicious computer program designed to hold personal files on the infected machine hostage. Security researchers detected that this malware sample belongs to the broad family of Cerber, which was first introduced in March 2016, and is most commonly spread via contaminated email attachments (mainly .doc and .wsf files).
Once inside the system, Alpha ransomware virus makes a variety of Windows system changes in order to perform file encryption process, which appends .bin extension to them. Suchlike modified data can no longer be accessed, as it requires a unique key that only criminals behind malware has the access to.
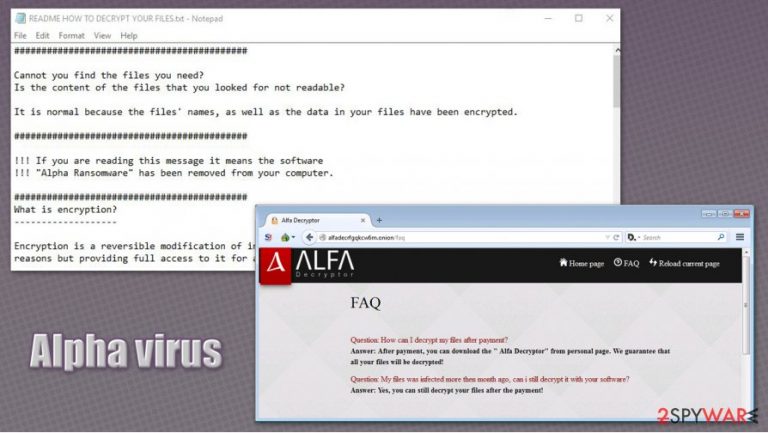
In the README HOW TO DECRYPT YOUR FILES.TXT and README HOW TO DECRYPT YOUR FILES.HTML ransom notes, cybercriminals explain to users what happened to their files, and that they need an “Alpha Decryptor” in order to recover data. Of course, victims have to pay for it in Bitcoin cyroptocurrency.
| Name | Alpha ransomware virus |
| Also known as | Alfa ransomware |
| Type | File locking virus |
| Family | Cerber |
| Extension | .bin. Example of encrypted file – “picture.bin” |
| Ransom note | README HOW TO DECRYPT YOUR FILES.TXT and README HOW TO DECRYPT YOUR FILES.HTML |
| Ransom size | 1.5 bitcoin |
| Removal | Ransomware should be removed with powerful anti-malware software, such as SpyHunter 5Combo Cleaner |
| System fix | To fix Windows system after ransomware infection, use FortectIntego |
As the type of Alpha ransomware virus already suggests, the malware attempts to lock out the important files and demand for a ransom. The main feature of this virus is that it asks 1.5 Bitcoin for data recovery (price of cryptocurrency varies greatly, so the demand price can be different, depending on when you get infected.
However, not all ransomware developers use Bitcoins or other cryptocurrency for ransom payments. For instance, TrueCrypt, demands its victims to pay a ransom via Amazon gift cards. Thus, some might suspect that the developers of this virus are either premature, or they regard such activity as a mere free-time spending alternative.
Ransomware which involves in global scams usually chooses more discrete methods of receiving the ransom, in order to maintain the identities of their developers undisclosed. Nevertheless, the approach to ransom collection does not determine the damage these programs are capable of inflicting. So, if you have become a victim of this ransomware, then keep reading to find out about Alpha virus removal – it should be performed with the help of trusted security tools, such as SpyHunter 5Combo Cleaner or Malwarebytes.
Additionally, it is important to note that file recovery and malware elimination are not the only steps that should be done in order to completely recover from the infection. Some Windows system files might be negatively impacted by Alpha ransomware, resulting in crashes, freezes, errors, and other issues. Thus, to fix these problems, experts recommend using FortectIntego.
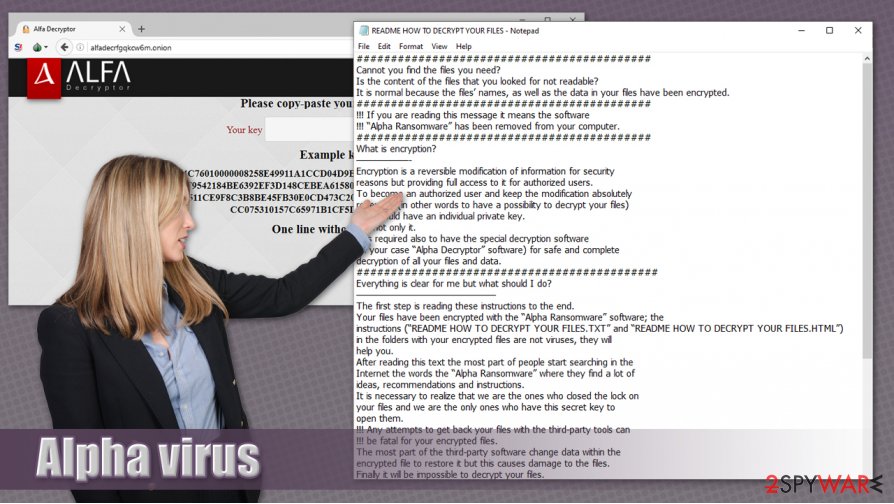
When the virus stealthily infiltrates the system, it will not take long to start scanning it for pictures, video files, Office documents and other data included in the predetermined target list. The victim’s personal files are encrypted with the AES-256 algorithm, making them virtually inaccessible, unless a private key is used to decrypt them.
The whole file encryption process does not take long and after it is completed, a README HOW TO DECRYPT YOUR FILES.TXT and README HOW TO DECRYPT YOUR FILES.HTML files are dropped on every infected folder of the victim’s computer. This document features instructions to the locked data recovery:
###########################################
Cannot you find the files you need?
Is the content of the files that you looked for not readable?
It is normal because the files’ names, as well as the data in your files have been encrypted.
###########################################
!!! If you are reading this message it means the software
!!! “Alpha Ransomware” has been removed from your computer.
###########################################
What is encryption?
——————-
Encryption is a reversible modification of information for security
reasons but providing full access to it for authorized users.
To become an authorized user and keep the modification absolutely
reversible (in other words to have a possibility to decrypt your files)
you should have an individual private key.
But not only it.
It is required also to have the special decryption software
(in your case “Alpha Decryptor” software) for safe and complete
decryption of all your files and data.
############################################
Everything is clear for me but what should I do?
————————————————
The first step is reading these instructions to the end.
Your files have been encrypted with the “Alpha Ransomware” software; the
instructions (“README HOW TO DECRYPT YOUR FILES.TXT” and “README HOW TO DECRYPT YOUR FILES.HTML”)
in the folders with your encrypted files are not viruses, they will
help you.
After reading this text the most part of people start searching in the
Internet the words the “Alpha Ransomware” where they find a lot of
ideas, recommendations and instructions.
It is necessary to realize that we are the ones who closed the lock on
your files and we are the only ones who have this secret key to
open them.
!!! Any attempts to get back your files with the third-party tools can
!!! be fatal for your encrypted files.
The most part of the third-party software change data within the
encrypted file to restore it but this causes damage to the files.
Finally it will be impossible to decrypt your files.
When you make a puzzle but some items are lost, broken or not put in its
place – the puzzle items will never match, the same way the third-party
software will ruin your files completely and irreversibly.
You should realize that any intervention of the third-party software to
restore files encrypted with the “Alpha Ransomware” software may be
fatal for your files.
####################################
!!! There are several plain steps to restore your files but if you do
!!! not follow them we will not be able to help you, and we will not try
!!! since you have read this warning already.
####################################
For your information the software to decrypt your files (as well as the
private key provided together) are paid products.
After purchase of the software package you will be able to:
1. decrypt all your files;
2. work with your documents;
3. view your photos and other media;
4. continue your usual and comfortable work at the computer.
If you understand all importance of the situation then we propose to you
to go directly to your personal page where you will receive the complete
instructions and guarantees to restore your files.
######################################
If you need our help:
1. run your Internet browser (if you do not know what it is run the Internet Explorer);
2. enter or copy the address https://www.torproject.org/download/download-easy.html.en into the address bar of your browser and press ENTER;
3. wait for the site loading;
4. on the site you will be offered to download Tor Browser; download and run it, follow the installation instructions, wait until the installation is completed;
5. run Tor Browser;
6. connect with the button “Connect” (if you use the English version);
7. a normal Internet browser window will be opened after the initialization;
8. type or copy the address in this browser address bar;
9. press ENTER;
10. the site should be loaded; if for some reason the site is not loading wait for a moment and try again.
11. enter your personal key:
12. press ENTER;
If you have any problems during installation or operation of Tor Browser,
please, visit https://www.youtube.com/ and type request in the search bar
“install tor browser windows” and you will find a lot of training videos
about Tor Browser installation and operation.
If TOR address is not available for a long period (2-3 days) it means you
are late; usually you have about 2-3 weeks after reading the instructions
to restore your files.
#######################################
Additional information:
You will find the instructions for restoring your files in those folders
where you have your encrypted files only.
The instructions are made in two file formats – HTML and TXT for
your convenience.
Unfortunately antivirus companies cannot protect or restore your files
but they can make the situation worse removing the instructions how to
restore your encrypted files.
The instructions are not viruses; they have informative nature only, so
any claims on the absence of any instruction files you can send to your
antivirus company.
########################################
Alpha Ransomware Project is not malicious and is not intended to harm a
person and his/her information data.
The project is created for the sole purpose of instruction regarding
information security, as well as certification of antivirus software for
their suitability for data protection.
Together we make the Internet a better and safer place.
#########################################
If you look through this text in the Internet and realize that something
is wrong with your files but you do not have any instructions to restore
your files, please, contact your antivirus support.
#########################################
Remember that the worst situation already happened and now it depends on
your determination and speed of your actions the further life of
your files.
This note may have an apologetic ring to it, but it does not change the fact that your highly important files are now inaccessible, and you are required to pay a considerable amount of money to retrieve them. Luckily, an IT specialist Michael Gillespie has managed to find vulnerabilities of this virus and developed a program capable of decrypting the data without any charge. This Alpha Decrypter can be found online.
Ransomware virus distribution methods
Since the threat is relatively new, there isn’t much information about all possible ways to encounter Alpha virus. However, the main methods prevail. As the majority of the viruses of this type, your computer can get infected via malicious email attachment. Be aware that cyber criminals have improved their persuasion techniques, so avoid opening any suspicious email even if it is sent from an existing company or governmental institution with the invoice, postal or traffic notifications.
Alternatively, you should hurry to install a reliable cyber security program which is able to detect exploit kits. It has been observed that some ransomware samples spread via them. They are especially treacherous since they can sneak into the system without getting quarantined by the anti-virus program. That is why it is a necessary to have an additional repair application, such as FortectIntego, operating side-by-side with the primary anti-virus software.
Lastly, since the hackers of Alpha ransomware seem to prefer iTunes, you should stay vigilant and refrain from entering any suspicious hyperlinks provided on the website. You can never be guaranteed that using a legitimate website will prevent you from getting assaulted by the ransomware. Thus, let us proceed to the section where we will present you the ways to remove Alpha.
Alpha virus removal guidelines
There are only two main ways to remove Alpha virus from the damaged system – automatic and manual one. The manual removal instructions are provided below. Taking into account that this virus is ransomware, you should not take it too lightly. Precision and attention are necessary in order to remove Alpha without leaving any traces.
Alternatively, we recommend installing an anti-spyware program which is specifically created for terminating similar viruses. Besides Alpha removal, it can also ward off minor malware, such as previously-mentioned exploit kits. Though this time you can consider yourself lucky since you can decrypt your files, however, you should start considering alternative ways to store your personal data.
Getting rid of Alpha virus. Follow these steps
Manual removal using Safe Mode
You can access Safe Mode with Networking to remove Alfa ransomware virus without problems:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Alpha using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Alpha. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Alpha from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Alpha, you can use several methods to restore them:
Use Data Recovery Pro
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Alpha ransomware;
- Restore them.
Windows Previous Versions feature might be of use
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might sometimes be able to restore all your files
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Alpha and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.







