RagnarLocker ransomware - Virus Files Removal - May 2020 update
RagnarLocker virus Removal Guide
What is RagnarLocker ransomware?
RagnarLocker is a cryptovirus that targets enterprises and software companies and steals sensitive information
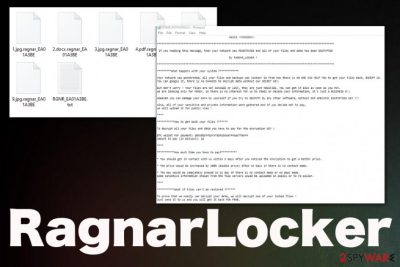
Highly-targeted attacks use RSA-2048 encryption and change the original code of various files found on the network. Once that is done custom note gets developed which includes the name of the affected company and specific ransom amount set for the particular victim.
RagnarLocker ransomware virus developers generate the name of this text file according to the extension that is unique for each target and includes .rangnar and file marker. Ransomware terminates and disables various processes, especially security software and functions used for file backups. This particular locker targets remote management software used by managed service providers. Such applications provide remote support for people, so virus terminates any functions to avoid detection and termination of the attack.
The activity of this cryptovirus was first spotted in February when VGCARGO was targeted by the RagnarLocker virus.[1] However, malware developers seem to go for Big Game Hunting[2] tactics and continue their malicious deeds by attacking companies from various industry sectors, including EDP Renewables North America.[3]
| Name | RagnarLocker ransomware, Ragnar_Locker ransomware |
|---|---|
| Target | Large businesses, enterprises, and software companies |
| File marker | .ragnar_*** or .ragnar_<ID***. Every file extension is customized and includes particular Id generated for specific target |
| Encryption method | Relies on RSA2048, but also uses the combined AES+RSA algorithm for encryption processes |
| Contact email | hello_company@protonmail.com |
| Ransom note | The note including contact information and further instructions contains the personalized message and gets named in the same pattern as the file marker RGNR_***.txt or RGNR_ .txt |
| Ransom amount | Differs from 20 to 60 Bitcoin |
| Distribution | Spam email campaigns include malicious files that trigger the drop of a ransomware executable that launches the encryption immediately. Legitimate looking emails state about financial data or notifications from known companies or services |
| Unique functions | Attackers claim to steal data before encrypting files, so they can additionally blackmail people into paying the ransom. It is not known if that really happens, but such a feature becomes common for enterprise-targeting ransomware threats |
| Elimination | You need to get a proper anti-malware tool for RagnarLocker ransomware removal, so all the related files and malicious applications can be deleted completely from the machine |
| Repair | Malware like this can make big changes and damage crucial places of the OS, so you should repair these issues with the help of a proper system tool or cleaner like FortectIntego |
There are no sources that completely confirm the relation between RagnarLocker ransomware and Ragnarok ransomware, but the name, tactics, and similarities are there. Both threats target companies, use similar patterns of extensions and ransom notes. The Locker may be a new and improved version of the first version that targeted Citrix and got discovered at the end of 2019.
RagnarLocker ransomware developers claim that they have some pre-deployment tasks that get executed before encrypting files found on the system. One of the processes involves stealing personal data and storing particular files on their servers, so when the victim is refusing to pay the demanded amount, all those details get released publicly, exposing valuable and sensitive data.
When criminals are ready, the main function of RagnarLocker ransomware is started – file encryption. In most cases, RSA-2048 is the method used for the file-locking. Before encrypting virus checks the location of the affected devices, so people from Russia, Azerbaijan, Armenia, Georgia, Kazakhstan, Kyrgyzstan, Moldova, Tajikistan, Turkmenistan, Uzbekistan, and Ukraine can be excluded.
RagnarLocker ransomware also checks Windows services running on the machine, so processes with certain strings can be stopped. This is the common method used by threats like this because it is the method that helps to avoid virus detection and termination. These strings include:
- vss
- sql
- memtas
- mepocs
- sophos
- veeam
- backup
- pulseway
- logme
- logmein
- connectwise
- splashtop
- kaseya.
These activities and additional features that malware has, affect the persistence and processes like RagnarLocker ransomware removal significantly. Also, since recovery options, software, and features get disabled, it becomes more difficult to recover after the attack. Unfortunately, the malware runs WMIC.exe shadowcopy delete command and removes Shadow Volume Copies that can be useful for file restoring. 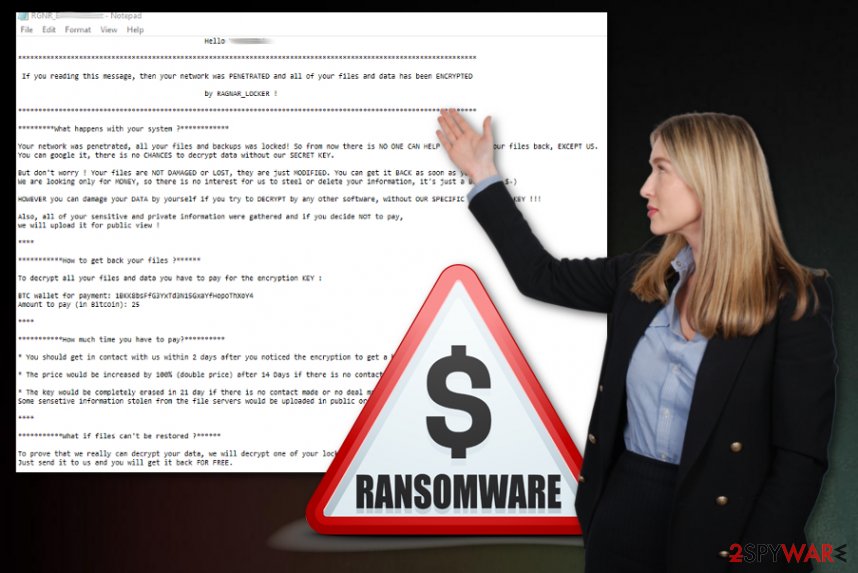
You need a proper anti-malware tool that could detect and terminate the virus for you. When it comes to enterprises, professional security experts need to remove RagnarLocker ransomware completely off of the network since any connected device can get affected by the virus or even damaged.
When the encryption is successfully done, RagnarLocker ransomware creates a unique ransom note and releases the personalized message for the people from the affected company. The message states about encryption, cryptocurrency addresses, contact information. Also, developers provide TOX chad ID that should help to communicate with them and the email address, but the first one is not working.
RagnarLocker virus ransom note:
Hello * !
********************
If you reading this message, then your network was PENETRATED and all of your files and data has been ENCRYPTED
by RAGNAR_LOCKER !********************
*********What happens with your system ?************
Your network was penetrated, all your files and backups was locked! So from now there is NO ONE CAN HELP YOU to get your files back, EXCEPT US.
You can google it, there is no CHANCES to decrypt data without our SECRET KEY.But don't worry ! Your files are NOT DAMAGED or LOST, they are just MODIFIED. You can get it BACK as soon as you PAY.
We are looking only for MONEY, so there is no interest for us to steel or delete your information, it's just a BUSINESS $-)HOWEVER you can damage your DATA by yourself if you try to DECRYPT by any other software, without OUR SPECIFIC ENCRYPTION KEY !!!
Also, all of your sensitive and private information were gathered and if you decide NOT to pay,
we will upload it for public view !****
***********How to get back your files ?******
To decrypt all your files and data you have to pay for the encryption KEY :
BTC wallet for payment: *
Amount to pay (in Bitcoin): 25****
***********How much time you have to pay?**********
* You should get in contact with us within 2 days after you noticed the encryption to get a better price.
* The price would be increased by 100% (double price) after 14 Days if there is no contact made.
* The key would be completely erased in 21 day if there is no contact made or no deal made.
Some sensetive information stolen from the file servers would be uploaded in public or to re-seller.****
***********What if files can't be restored ?******
To prove that we really can decrypt your data, we will decrypt one of your locked files !
Just send it to us and you will get it back FOR FREE.The price for the decryptor is based on the network size, number of employees, annual revenue.
Please feel free to contact us for amount of BTC that should be paid.****
! IF you don't know how to get bitcoins, we will give you advise how to exchange the money.
!!!!!!!!!!!!!
! HERE IS THE SIMPLE MANUAL HOW TO GET CONTCAT WITH US !
!!!!!!!!!!!!!1) Go to the official website of TOX messenger ( hxxps://tox.chat/download.html )
2) Download and install qTOX on your PC, choose the platform ( Windows, OS X, Linux, etc. )
3) Open messenger, click “New Profile” and create profile.
4) Click “Add friends” button and search our contact *
5) For identification, send to our support data from —RAGNAR SECRET—
IMPORTANT ! IF for some reasons you CAN'T CONTACT us in qTOX, here is our reserve mailbox ( * ) send a message with a data from —RAGNAR SECRET—
WARNING!
-Do not try to decrypt files with any third-party software (it will be damaged permanently)
-Do not reinstall your OS, this can lead to complete data loss and files cannot be decrypted. NEVER!
-Your SECRET KEY for decryption is on our server, but it will not be stored forever. DO NOT WASTE TIME !********************
—RAGNAR SECRET—
*
—RAGNAR SECRET—********************
Paying the ransom is never the best answer, experts[5] always note that there is no need to even consider paying the amount that RagnarLocker ransomware or any other cryptovirus creators ask of you. You can get additional malware sent to you via the email or asked to pay more after one transfer.
Even though RagnarLocker ransomware mainly targets large companies and is focused on English-speaking people it can freely get on everyday user devices in any country all over the world, so you should be extremely cautious and pay attention to all the listed features and tips that we gathered.
The middle of April 2020 could be called a new step in Ragnar Locker creators career as they were spotted to invade a giant company of Portugal – Energias de Portugal. The Portuguese electric utility company which is located in Lisbon is a very important electricity and gas supplier in the region. The criminals were not ashamed to ask for a 10 million Euro ransom to give up the encrypted Tb's of the companies data.
In case you have noticed some suspicious activity on your computer, do not wait for the ransom notes to come. Rely on the anti-malware tool and scan the machine to make sure there are no viruses interrupting your PC. If needed, get a PC repair program like FortectIntego and get rid of the virus damage.
Stay away from emails with attached files
Email campaigns spread a handful of different threats and can lead to various malware infections when you don't pay enough attention to the content and sources of the notifications. In most cases, those emails may seem legitimate and safe when the sender is a particular service or company that you know and trust. Don't fall for such tricks.
Pay attention to the particular sender and the type of files attached. Financial information, order details, receipts, and other sensitive data shouldn't end up on your email box when you don't use the service. So keep suspicions and avoid opening emails that are not expected.
Malicious macros can get loaded on these MS files and similar data that gets attached to safe-looking emails. Once the file is downloaded and opened on the machine, the suggestion to enable additional content shows up on the screen. After that, the malicious script gets loaded on the computer, and encryption starts. Delete emails without clicking on any links or attachments.
You need a clean system before you can do anything related to RagnarLocker virus encrypted files
You need to note that RagnarLocker ransomware virus is not only affecting large companies but also can get on devices of users all over the globe without any effort. This is more dangerous because of the advanced methods and techniques used by the threat actors.
The most important thing is the fact that malware gets persistent due to all the additional changes in system folders, settings and added programs, entries on the registry, and so on. For that reason, you not only need to remove RagnarLocker ransomware, but you should also repair those issues and get rid of the virus damage.
Get SpyHunter 5Combo Cleaner, or Malwarebytes for the proper RagnarLocker ransomware removal and then run FortectIntego as a PC repair application and clean any traces or fix affected parts of the malware. Make sure to pay attention to the AV tool delivered results and detection rates, follow the suggested steps and clean possible intruders. You need to get back to a properly cleaned machine before you even consider file restoring.
Getting rid of RagnarLocker virus. Follow these steps
Manual removal using Safe Mode
Reboot the system in Safe Mode with Networking and then run the AV tool that can remove RagnarLocker ransomware virus from the machine for you
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove RagnarLocker using System Restore
System Restore feature can be used to get rid of the RagnarLocker ransomware because this function allows recovering the machine in a previous state
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of RagnarLocker. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove RagnarLocker from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by RagnarLocker, you can use several methods to restore them:
Data Recovery Pro is the program that gives the opportunity to recover your files after the encryption process of RagnarLocker ransomware virus
You can restore affected files with the help of this program. Encrypted, deleted or damaged data can be used again after the Data Recovery Pro restoring
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by RagnarLocker ransomware;
- Restore them.
Windows Previous Versions feature helps with files encoded by the RagnarLocker virus
You can use Windows Previous Versions for your individual files when System Restore gets enabled in advance
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer – a method for file recovery
When RagnarLocker ransomware locks data but leaves Shadow Volume Copies untouched, you can go through restoring them using SdadowExplorer
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
RagnarLocker ransomware is not decryptable at the moment
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from RagnarLocker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ RagnarLocker Ransomware! Target VGCARGO. Twitter. Social media platform.
- ^ Morgan MarquisBoire, Marion Marschalek, Claudio Guarnieri. BIG GAME HUNTING: THE PECULIARITIES IN NATIONSTATE MALWARE RESEARCH. Black Hat. Official report.
- ^ Charlie Osborne. Energy company EDP confirms cyberattack, Ragnar Locker ransomware blamed. ZDNet. Business technology news website.
- ^ Josh Fruhlinger. Ransomware explained: How it works and how to remove it. CSOonline. Cybersecurity and IT news.
- ^ Lesvirus. Lesvirus. Spyware related news.





















