SamSam ransomware / virus (Removal Instructions) - updated Dec 2018
SamSam virus Removal Guide
What is SamSam ransomware virus?
SamSam a dangerous ransomware virus that is using brute-force attacks for propagation
SamSam ransomware is a cryptovirus that was first spotted making rounds in March 2016. Despite being a relatively old infection, it is still prevalent in the US and some Asian countries. Fortunately, its developers, Faramarz Shahi Savandi and Mohammad Mehdi Shah, have already been found guilty.[1] Initially, malware used JBoss software vulnerability to install the payload remotely. In 2018, researchers observed hackers conducting brute-force attacks via FTP, RDP or Java-based servers. SamSam ransomware is huge, with total earnings of 6 million dollars during its time of operation over two and a half years.[2] It concurred such institutions like Labcorb or city of Atlanta, resulting in millions in damages. The malware is used exclusively for money extortion purposes – it uses RSA-2048 to lock up personal files and adds an appendix (such as .weapologize, .AreYouLoveMyRansFile, .breeding123, .country82000, etc.), making them inaccessible. To decipher them, victims have to pay a ransom in Bitcoin which can range up to $51,000.
| Summary of the cyber threat | |
|---|---|
| Name | SamSam |
| Type | Ransomware |
| Danger level | High. Makes system changes and encrypts files |
| Release date | June 2016 |
| Cryptography | RSA-2048 |
| Appended extensions |
|
| Ransom notes |
|
| Ransom | Varies. Some versions ask to pay 0.7 Bitcoins for one computer; others demand 45 BTC for the whole network. |
| To uninstall SamSam ransomware, install FortectIntego and run a full system scan | |
SamSam virus is identified by major security programs as Trojan.Ransom.SamSam, MSIL/Filecoder_Samas.B!tr, Backdoor.Ratenjay.Gen!c, Msil.Trojan.Dothetuk.Tccf, etc.[3] However, the virus is designed to bypass the computer's security, so it's not enough to install reputable security software to avoid the attack. Samsam.exe executable is dropped on the system when a victim opens a malicious email attachment.
Initially, SamSam ransomware is known to rely on fake email messages pretending to be notifications from UPS or similar delivery company. However, researchers noted malware shifted overtime and started using brute-force attacks to infect systems and its networks.
Once inside the system, ransomware encrypts files and provides a special email address (nullforwarding@qualityservice.com, etc.) to contact its developers. The data is typically encrypted with the RSA-2048 encryption algorithm, so there is no chance to guess the code needed for its decryption.
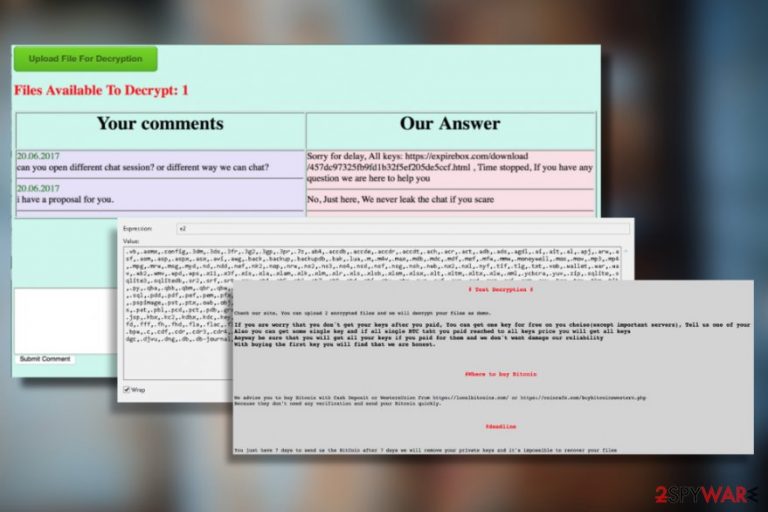
One of the examples of SamSam ransom notes:
#What happened to your files?
All your files encrypted with RSA-2048 encryption. For more information search in Google “RSA Encryption.”
#How to recover files?
RSA is a asymmetric cryptographic algorithm, You need one key for encryption and one key for decryption
So you need Private key to recover your files.
It’s not possible to recover your files without private key
#How to get private key?
You can get your private key in 3 easy step:
Step1: You must send us 1,7 Bitcoin for each affected PC or 29 BitCoins to receive ALL Private Keys for ALL affected PCs.
Step 2: After you send us 1,7 Bitcoin, Leave a comment on our Site with this detail: Just write your “host name” in your comment.
* Your host name is: XXXXXXXXXXXX
[…]
However, paying the ransom is not recommended. Crooks are known for not giving working decryption software and putting victims into more significant problems. Therefore, it is recommended to remove SamSam ransomware instead of taking shady cybercriminals' offers to recover files. In some cases, malware fails to delete Shadow Volume Copies, and data can be restored with third-party tools, but first, you need to get rid of the virus.

SamSam removal requires using anti-malware software. Use professional tools like FortectIntego or Malwarebytes to clean the affected device. However, if you cannot download or run security software, you should reboot the affected machine to Safe Mode with Networking as we have explained at the end of this article.
SamSam ransomware – a large scale business
SamSam ransomware authors rely on a strange code of “honesty and fairness.” Quite often, hackers use “Sorry” in the titles of their ransom notes, and also offer free decryption of several personal files. It seems like bad actors try to make others believe that that they are nice and friendly people, which is complete nonsense.
Nevertheless, SamSam managed to reach incredible highs throughout its existence, crippling large hospitals, city municipalities, and other large-scale organizations.
SamSam ransomware was detected after it infected several hospitals in the United States[4] in 2016. MedStar hospital was in the worst position after this ransomware attack because it was required to pay 45 Bitcoins or $18,500 in exchange for the encrypted data. Fortunately, IT specialists in this hospital managed to remove SamSam virus and find backups of encoded data and used them to recover affected files. Hence, cybercriminals did not receive the money.
Therefore, the main targets of the malware are organizations and businesses. FBI has officially warned the corporations and companies to increase their cybersecurity.[5] According to the latest information, malware relies on the targeted attacks and does not seem to infect random computers. The functionality of the virus requires attackers participation – he or she has to enter a specific password to begin the attack.[6]

Atlanta City attack – a devastating hit that cost $2.6 million
Atlanta suffered SamSam ransomware intrusion in March 2018, when the citizens of the city were unable to process certain actions:[7]
The City of Atlanta is currently experiencing outages on various customer facing applications, including some that customers may use to pay bills or access court-related information. We will post any updates as we receive them.
The infection affected five city departments out of 13, and employees were forced to connect personal computers in order to perform operations and deal with sensitive data. Additionally, some police records were lost in the attack.
The officials were given two choices: either pay $6,000 per infected machine or a whopping $51,000 to recover operation of all networks at once. While it is unknown if any of the demanded money was paid, the attackers quickly closed down the payment portal and left the city in havoc.
Atlanta ended up spending over $2.6 million for the damages caused by SamSam ransomware.
LabCorp: SamSam ransomware hits one of the largest medical testing companies in US
LabCorp, one of the most prominent medical diagnostics company, has recently reported about a suspicious activity on their network on July 14.[8] At that time, IT specialists couldn't identify the cause of it. Although, now the official report from the LabCorp confirms about a ransomware attack, SamSam in particular.
Luckily, security experts have managed to shut down affected parts of the system in 50 minutes and prevent further damage. Currently, the recovery process has started and the company already operates at 90-percent capacity. However, some clients may not be able to access test results as a result of SamSam ransomware attack.
According to the analysis, SamSam virus was infiltrated on the company's network via Brute Force against Remote Desktop Protocol (RDP). Thanks to quick response by cybersecurity specialists, none of the customers' information was stolen. Although, the ransomware managed to encrypt the following parts of the network:
- 7,000 systems;
- 1,900 servers;
- 350 production servers.
Sophisticated infections are distributed in multiple ways
The key difference of this file-encrypting from other ransomware-type infections is that it uses targeted attacks. In other terms, it does not aim to infect the computers of regular users rather than target large-scale organizations. Thus, the developers of the virus create unique spam emails to infiltrate the networks of well-known firms.
This threat has been distributed using other methods too. The most shocking discovery is that this virus has been relying on vulnerability found in JBoss application. Alternatively known as WildFly,[9] it helped the virus infect the entire network and invade several computers at the same time.
When spreading with the help of this method, the virus uses a special tool called JexBossooks to look for JBoss vulnerabilities. Once the vulnerabilities are detected, it drops Trojan:BAT/Samas.B [10] and Trojan:BAT/Samas.C.[11] to steal personal credentials. After obtaining such data, the hackers launch their ransomware as a psexec.exe file and initiate the attack of the ransomware.
Therefore, to avoid ransomware attack, you have to:
- Be careful with received emails and do not rush opening any attached files;
- Install all software and OS updates to avoid exploitation of vulnerabilities;
- Download updates and security patches from the official websites.
Perform the following steps to remove SamSam ransomware from your device
It is evident that the attackers try their best to create an infection which is persistent. Therefore, SamSam ransomware removal process is not an easy task. Although, professional security tools can significantly help with the elimination of this cyber threat.
We suggest eliminating the virus with one of these programs FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. Security programs cannot only delete all ransomware-related files but keep your computer protected from cyber threats in the future.
For it to maintain its functionalities flawlessly, you need to update the software daily. If you cannot remove SamSam virus because of the inability to launch the security program or access other important OS programs, take a look at the recovery guidelines below.
You should also create a safe environment on your computer before initiating Samsam removal. To help you protect your registry entries and similar components, we prepared a video guide to show you how it is done:
Getting rid of SamSam virus. Follow these steps
Manual removal using Safe Mode
In some cases, ransomware prevents users from accessing or running security programs. Thus, you have to reboot your computer to the Safe Mode with Networking as shown below to start its removal. Then repeat system scan.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove SamSam using System Restore
System Restore method can also help you disable the virus in order to run automatic ransomware removal. For that, use the following steps:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of SamSam. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove SamSam from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by SamSam ransomware, you can try decrypting them only after you remove the ransomware. For that, make sure you choose one of the following methods:
If your files are encrypted by SamSam, you can use several methods to restore them:
Recover your files encrypted by SamSam virus with the help of Data Recovery Pro
If you are infected with SamSam virus, you can try using Data Recovery Pro to recover your encrypted files. This application is widely known for helping people revive their accidentally deleted files and similar data.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by SamSam ransomware;
- Restore them.
Use Windows Previous Versions feature to recover separate files encrypted by SamSam ransomware
If you have files that are very important to you, you can try recovering them with the help of Windows Previous Versions feature. However, to use it, you need to make sure that System Restore function was enabled before the appearance of SamSam.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
SamSam decrypter
At the moment, there is a SamSam decrypter available on the Internet, however, since Google SafeBrowsing considers it dangerous, we cannot share a link to it here. We will update the article as soon as a 100% safe and official decrypter appears. Be patient!
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from SamSam and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Olivia Morelli. Iranian hackers found guilty for launching SamSam ransomware attack. 2spyware news and virus removal guides.
- ^ SamSam: The (Almost) Six Million Dollar Ransomware. Sophos. Cybersecurity made simple.
- ^ valley2.exe. VirusTotal. Free malicious URL analysis service.
- ^ Samsam may signal a new trend of targeted ransomware. Official Symantec Blog.
- ^ Incidents of Ransomware on the Rise. Protect Yourself and Your Organization. An official site of the U.S. government, U.S. Department of Justice.
- ^ SamSam ransomware: controlled distribution for an elusive malware. Malwarebytes Labs. Cyber security news.
- ^ Ransomware attack. City of Atlanta. Twitter. Social network.
- ^ Lucia Danes. SamSam ransomware: Labcorp's systems infected via brute force attack. 2-spyware. Cybersecurity news and articles.
- ^ What is Wildfly. Wikipedia, the free encyclopedia.
- ^ Trojan: BAT/Samas.B. Microsoft Malware Protection Center.
- ^ Trojan: BAT/Samas.C. Microsoft Malware Protection Center.







