Xhelper (Free Guide) - Removal Instructions
xhelper Removal Guide
What is xhelper?
xhelper – Android malware that reinstalls itself after termination, uninstallation, and even factory reset
xHelper is the trojan dropper that delivers malware like banking trojans and ransomware on mobile devices. This trojan has already infected 45 000 devices in the past six months, mainly targetting U.S, Russia, and India. Malicious applications created with the malware component get distributed via app stores unnoticed by any antivirus software engines. The malware was spotted back in 2019 but evolved and became an unremovable mobile trojan that affects at least 100 victims per day.[1]
The virus gets installed when the web redirect appears on the screen and encourages downloading third-party applications from outside the Play Store. The website sends users to additional web pages with instructions on how to install the unofficial Android app with the hidden malicious code of the trojan. It is not destructive malware and mainly focuses on intrusive pop-ups or notification spam, advertisements, redirects. However, even though trojan makers make money from pay-per-click,[2] other malicious programs may get installed on the already infected device.
xHelper is not like any other Android virus because the trojan gains access to the targeted device via the application but then installs a separate self-standing malware that is not affected when you uninstall the initial program. Trojan continues to run on the machine, but it cannot be noticed in the system's section of applications. Even when you manually remove the malware, it reinstalls itself, and it does the same after the device's full factory reset.
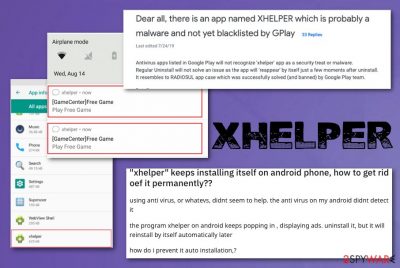
Many users complain about this shady program and its activities that any antivirus program cannot detect.[3] Trojan keeps showing various messages and notifications on the device out of nowhere, and the process is not reversible even by removing the program or cleaning the device. However, the fact that malware survives through termination and other removal processes still is a mystery for researchers and security tool developers.
| Name | xHelper |
|---|---|
| Type | Mobile malware/ Trojan |
| Affects | Android devices. The main targets during these attacks were spotted in the U.S, India, Russia. |
| Symptoms | The program appears running and shows notifications, spam, pop-ups on the device, and shows suspicious content even after cleaning processes or factory resets. it displays ads and mainly focuses on getting monetization from redirects and commercial material |
| Working principle | It loads the web redirect that pushes the installation of third-party applications that contain malicious trojan code. The separate self-standing service gets downloaded and can download, install other programs like ransomware, banking malware, and password stealers or DDoS bots |
| Danger | It spams the user with commercial content and exposes people to possibly dangerous online material. It deploys second-stage malware payloads and can install any malware at any point once it loads on the system, even though the trojan itself is not destructive |
| Distinct features | It loads via the third-party application and then reinstalls the payload separately, so when the program gets uninstalled, it doesn't affect the trojan at all. A malicious program can run and renew itself continuously |
| Distribution | The trojan gets installed when web redirect suggests installing a questionable application from the shady source, possibly posing as a legit Play Store. Particular sites that provide gaming apps. This is the initial method allowing the trojan on the device |
| Possible elimination | The removal is not possible, as researchers note. But you can try to scan the machine using anti-malware tools since databases get often renewed, and it may become possible to terminate the malware later on. For other processes that you can rely on, go to the end of this article |
| System health check | To restore any damage that the system files and settings suffered from the infection, we advise using the time-proven FortectIntego system diagnostics tool |
xHelper was first reported min-May in 2019, but the biggest month for the trojan was August when reportedly 45 000 devices in total got affected by the malware dropper. It mainly acts like a PUP and shows advertisements, redirects, other malicious online content. However, this trojan is more persistent than any adware-type intruder and can install malicious apps, hide its processes from the user and reinstall or uninstall itself unnoticeably.
Even when users delete the application used to spread the trojan or the traces of the malware from the machine, infection appears again, and random pop-ups continue to show up. This is an application component that is not listed in the application launcher or the folder with all Programs. It can easily run in the background because of this.
Unfortunately, that also means xHelper is not manually launched when there is no application icon visible on the machine. The malware is executed when the mobile device is connected or disconnected from the power source or rebooted. Trojan also makes additional changes to keep the persistence higher, like registers itself as a foreground service to lower the possibilities to get killed when the memory is low. Malware also restarts the service when it is stopped what is common for other mobile malware.[4]
When the Trojan is loaded on the machine, it can execute malicious functions and decrypt memory, connect to C&C servers hosted by attackers and execute any commands from there. This is how additional payloads of malware get downloaded on the machine, including:
- payload droppers;
- ransomware;
- rootkits;
- trojans;
- clickers.
Such hidden functions give hackers the opportunity to release any functionality and steal data, completely take over the device with the Trojan's help. This threat is not coming preinstalled. Users install the malicious app from shady sources. To avoid damage that questionable programs can trigger, you should rely on system cleaner tools and anti-malware programs. Find a tool compatible with your particular OS and run the check to see if anything is affected already. FortectIntego is a system tool that can possibly help with virus damage by restoring modified system files.
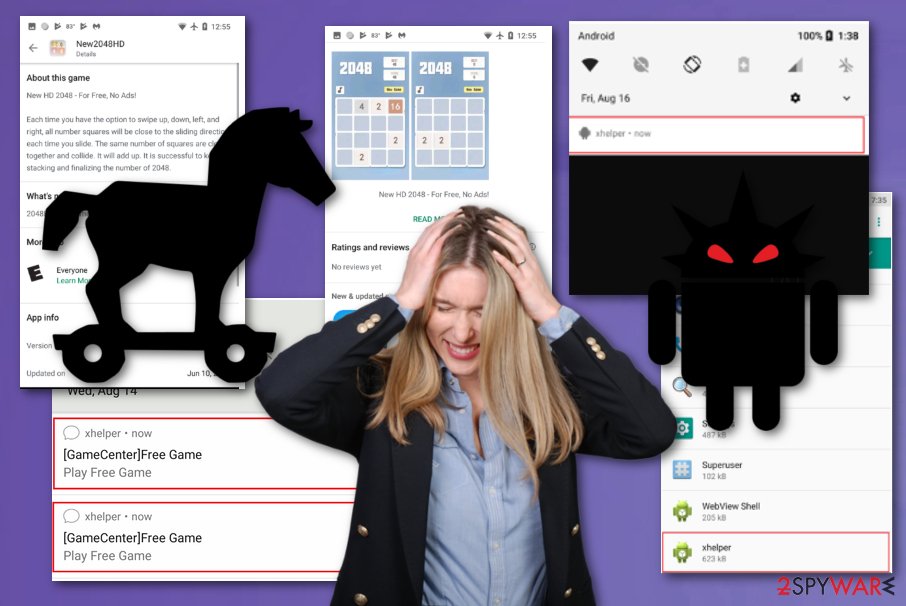
Pressing any of those notifications redirects to additional websites and allows you to play games online on the browser or show commercial content. This is one of the functions that this malware has – collecting views and pay-per-click revenue from each redirect and page visit.
However, this is a huge issue when people want to remove xhelper. The malicious application avoids creating any shortcuts or icons to hide all traces of existence. You can only notice the name in the application information section. Analysis of the trojan showed that servers, where the infection-triggering apps are stored, are located in the United States, so it is not surprising that attacks mainly target the U.S.
This infection gets spread via simple web redirects and sites like gaming sites, application providers. It may seem harmless, but users need to be extra cautious about random redirects and clicking on anything on promotional content or such redirect pages. Going back from the redirect is the best option. It may help you to avoid the infiltration of typical PUP or even threats like this.
Possibly two culprit's malware variants
The semi-stealthy version is the one that appears when the application is loaded on the machine. The program's icon does not appear on the system, so the victim is less likely to notice the presence of the malware. When trojan gets installed, it starts spamming the screen with advertisements, showing notifications, and promoting other sites and services. It is mainly focusing on operations that create views, page visits and generates pay-per-click revenue.
The more stealthy variant of the virus is much more dangerous. The distribution involves a first-stage payload dropping, so creators can infect the machine with more malicious threats and compromise the machine's crucial settings. The victim may not see any symptoms or traces of the app besides the small xhelper indication on notifications or title spotted in the App Info menu. This version is designed to drop secondary payloads and enable remote commands, enable attackers to run wanted processes. 
Mobile trojan propagation involves masking the infection as an application
It is common that threats targeting mobile devices operating systems like Android relies on deceptive techniques and masquerades as popular programs that users often search for and downloads from many different online sources.
People tend to rush through, so it is possible to hide the malicious purpose from the unsuspected victim. The particular trojan is masked as an application that has a couple of dozens of downloads and is loaded on the shady app store, but people still fall for the scam and get the infection on their Android.
The installation of shady applications can lead to more serious infections like this trojan, as you can see. Even though it is more associated with potentially unwanted programs, people tend to skip through it. Hidden files, payload droppers, and direct malicious codes can damage the mobile device immediately or spread the malware further.
You need to keep your device clean by relying on trustworthy sources only and avoiding any suspicious sites, providers, promotions. The malware creators can work around simple installation processes and drop their products without you even noticing if you don't take such actions seriously.
xHelper termination barely possible, but the infection can be managed
xhelper virus is a mobile trojan that employs many techniques to keep the malware persistent. More than one sample was discovered, and the more recent reports show that trojan is under development and can receive updates. It is believed that the natural progression to a more harmful and damaging strain that is even harder to detect is awaited in the future.
To at least try to remove the Trojan, people can rely on anti-malware programs and cleaning processes that possibly can indicate malicious processes, programs with shady purposes, and so on. SpyHunter 5Combo Cleaner or Malwarebytes can help to block content on malicious sites that you get exposed to. System diagnostics tools such as the FortectIntego software should be used to repair any system inconsistencies such as crashing, freezing, etc.
However, to avoid the initial cyber threat infiltration, you need to be cautious while browsing the internet and carefully select pages commonly visited in the mobile device since there are many malware variants that deliver the payload via online content.
Even though the termination is almost impossible, additional tips for xhelper removal or at least avoidance can be:
- keeping the software up-to-date;
- blocking suspicious downloads from unfamiliar sites;
- installing applications from reliable sources only;
- paying attention to permissions and requests that applications display;
- make backups of your data more frequent.
How to prevent from getting malware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ May Ying Tee, Tommy Dong. Xhelper: Persistent Android Dropper App Infects 45K Devices in Past 6 Months. Symantec. Threat intelligence research team.
- ^ Pay-Per-Click. Wikipedia. The free encyclopedia.
- ^ "xhelper" keeps installing itself on android phone, how to get rid oef it permanently??. Reddit. Online community forum.
- ^ What is Mobile Malware?. Forcepoint. Cybersecurity education.
