How to remove malware
Malware: why you should not forget it exists

Malware is an umbrella term used to describe all malicious programs to provide one or several benefits to cybercriminals, all while being damaging to victims affected. Malicious software can be targeted at a computer network within the company or individual personal computers. It includes a wide array of types, such as Trojans, rootkits, ransomware, viruses, some potentially unwanted programs, spyware, etc.
Malware is usually installed on the system without the user’s knowledge or approval, and there could be many attack vectors that malicious actors employ to distribute it. For example, one of the most popular methods for malware distribution is malicious spam emails (otherwise known as malspam), although more advanced methods, such as software vulnerabilities or exploit kits, can be used as well.
Only an updated anti-malware program is capable of preventing its infiltration or mitigating the impact of an infected machine. Security experts urge people to consider installing a reputable application for protecting their computers and avoiding cyberattacks.
Malicious software is mostly used to initiate unauthorized activity on a computer and help its owner to generate revenue. It can be designed to steal personal information, like logins and banking data, or it can try to encrypt precious files on a computer and make its owner pay a ransom in exchange for the decryption key.
Nevertheless, some versions of malware (adware, browse hijackers, and similar) are used just for showing promotional content on peoples' computers and generating pay-per-click revenue. Almost every type of malicious software can block or corrupt legitimate security software. In addition, they can also update themselves, download additional malware or cause security flaws on the affected PC system.
Many computer users go lightly about it, as they believe that they can always outsmart criminals and always stay on top. Unfortunately, it is not how it works – most malware is designed in a way to stay invisible to computer users, hence they won't even know that it is installed.
Additionally, some people intentionally engage in high-risk behavior and put their computer safety and personal security at risk. One of the best examples is software cracks or pirated programs – these are downloaded to avoid licensing process of software and receive it for free. This can often come at a cost, as there is almost no way to check whether a software crack is boobytrapped with malicious code, which would infect a computer with ransomware or other dangerous malware.
This is why you should not ignore the fact the malware is out there on the world wide web, and you should take precautions to prevent its infiltration and dire consequences of its presence on a PC.

Evolution of malware
The first example of malware showed up in 1986 when two brothers from Pakistan released a program known as Brain. It is considered the first malicious software sample, which was compatible with IBM. It spread through floppy disks and caused only annoying messages on the affected system.
The next serious threat showed up only in 1992. It was called Michelangelo and seemed to be much similar to viruses of our days. According to various reports, almost 20 thousand PC users reported about the data loss because of the Michelangelo virus.
At the beginning of the 2000s, security experts started noticing a serious growth in malware. Modern parasites, such as worms and trojans, started spreading around. Infected PCs were connected to botnets and turned into huge revenue machines.
Nowadays, malware authors are getting more and more serious and release more modern versions of computer threats. It has been reported that, since 2005, the amount of malware has increased from 1 million to 96 million different versions. Quite impressive, right?
By the end of 2020, ransomware has become the to-go malware that attacks regular computer users and prominent companies and organizations. With the help of malware, cybercriminals are also capable of breaching networks and servers of businesses, stealing data, and sometimes putting customers' private information at risk.
Crooks won't stop because malware became an extremely lucrative, although illegal, business. This is why home users, as well as corporations, should increase the level of security for all devices that are connected to the internet.
Malware infiltration techniques
Malware can be spread using various methods – here are the most common ones:
- Illegal and infected websites. Illegal websites have always been considered the main participant in the distribution of malware. The majority of such sites are filled with pornographic content, but you can also get infected after visiting a gaming, torrent, or even a legitimate news website that was compromised by attackers who injected a malicious script into it.
- Infected emails and attachments: Typically, this malware distribution scheme relies on botnets that are used to send misleading email messages to recipients. These fake emails are supposed to convince people to click the malicious link or download an infected executable file to the system. Nowadays, hackers have increased the number of fake email messages because people can hardly check their trustworthiness before downloading them to the system.
- Malvertising. Malware can also be spread thru malicious ads and links, and, in fact, they have been actively exploited nowadays. These links and ads can disguise themselves as updates for needed software, information about price reductions, and offers to take part in the survey. As soon as the victim clicks such link or ad, malware enters the system and causes unwanted activity.
Other malware. Different types of malware can be used for downloading additional threats to the affected PC system. If your computer is infected with ransomware or rogue anti-spyware, you may discover that another malware virus, such as adware or browser hijacker, was installed on your computer without your authorization as well.

Symptoms of the malware attack
One of the most common signs showing that your computer is infected with malware is fake security notifications and messages about your locked files. In this case, you can be infected with one of these malware versions:
The first group of threats seeks to scare users into believing that they are dealing with a reputable security utility that is trying to warn them about viruses. In reality, all these warnings are used just to scare users into purchasing fake anti-spyware.
The second group of malware shows a single warning, claiming that the user needs to pay a fine for illegal activity on the Internet. In addition, ransomware can also encrypt your important files and then make you pay the ransom.
If you have been suffering from redirects on a web browser or an excessive amount of pop-up ads, then you are dealing with:
These programs rely on a pay-per-click scheme, so their main aim is to hijack the web browser and display different kinds of pop-up ads. After clicking them, a user is redirected to sponsored websites. The majority of such programs are not malicious, but they have disrupted their victims with undesirable and sometimes even harmful content.
System slowdowns, stability issues, performance-related problems, and blocked security applications can also be noticed after the infiltration of malware. Unfortunately, this symptom can hardly help you to identify the type of malware you are dealing with, as it could be anything of the following:
Each of these malware threats is capable of using a considerable amount of computer resources. In addition, such programs can easily block legitimate security software and try to prevent their removal in this way. Beware that ignoring these symptoms can lead you to additional issues, like identity theft or losing your banking data and other information. Finally, keeping malware on the system can make your computer vulnerable to other threats in the future.

Malware examples
This program can also be added to the “fake PC optimization tools” category because it claims to be capable of improving a computer's performance, but it has nothing to do with that. Its activity is based on useless system scanners that report about invented registry entries, bad files, and other system components that are supposedly slowing PC's performance.
Once it convinces its victims that they have to remove this “harmful” data from their computers, the PC optimizer redirects them to its purchase page. Of course, you should never pay for its licensed version because you won't see any improvement after downloading it to your computer.
This is an especially dangerous example of malware, which has also been categorized as “Trojan Horse.” When inside the system, it can easily change the computer's settings, monitor your activity on a computer, and steal your important data.
It can also download other threats to the system without your authorization and knowledge. This virus has been actively spread with the help of fake Flash and FLV Player updates, so it is believed that thousands of computers have already been infected with COM Surrogate malware.
No matter that most adware can hardly initiate serious issues on your computer, DNS Unblocker should be avoided. First of all, it can cause an excessive amount of pop-up ads and similar commercial content on each of your favorite websites.
Secondly, it may use these ads to redirect you to malicious websites. Finally, it can collect information about your browsing activity on the Internet and then share it with related (and unrelated!) parties.
Malware removal options
The most reliable way to remove malware is to use a reliable anti-malware tool. Only an automatic removal option can help you to identify each malware version and eliminate each malicious component. In addition, you may be dealing with the seriously difficult type of malware, which may block your security software. If our recommended tool failed to help you fix your computer, you should perform these alternative steps:
- Repeat installation of anti-spyware. Then rename executable file and launch it;
- Reboot computer to Safe Mode and repeat installation of anti-malware;
- Install alternative anti-malware program;
- Fix virus damage with the help of a repair tool FortectIntego;
- Contact 2spyware customer service via the “Ask Us” section.
Latest malware added to the database
“Security Status not satisfied” email scam fix
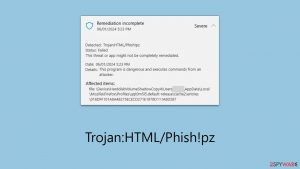
Removal of Trojan:HTML/Phish!pz
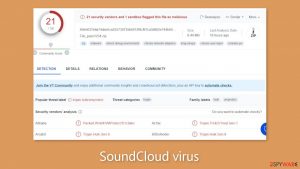
SoundCloud virus removal steps
Information updated: 2021-06-03