Hermes 2.1 ransomware / virus (Nov 2018 update) - updated Nov 2018
Hermes 2.1 virus Removal Guide
What is Hermes 2.1 ransomware virus?
Hermes 2.1 is a ransomware virus which is using AZORult trojan horse to spread around

Hermes 2.1 is a ransomware-type cyber infection that belongs to the same family as Hermes ransomware and Hermes 2.0. It was detected at the end of 2017 by the group of cybersecurity experts attacking computers of English-speaking users. In March 2018, a new Hermes 2.1 ransomware variant has been detected. This time, it was targeting South Korea PC users via 7 exploit kit called GreenFlash Sundown Flash Player, which helped the virus to infiltrate systems undetected. The new variant is using AZORult trojan horse to get into target PC systems. In addition, the virus encrypts files by using a combination of RSA public key and AES cipher. Each encrypted file gets a .HERMES or .hrm file extension. At the moment, the virus is appending [unlockmeplease@cock.li ].hrm file extension.
| Name | Hermes 2.1 |
|---|---|
| Type | Ransomware |
| Versions | Hermes, Hermes 2.0 |
| Danger level | High. Initiates modifications on Windows registry, compromises Windows startup, creates many batch files, and encrypts personal files |
| Detection date | October 2017. The latest version – November 2018 |
| File Extensions | .HERMES, .hrm, .[unlockmeplease@cock.li ].hrm |
| Emails Addresses | unlockmeplease@cock.li; pretty040782@gmail.com; pretty040782@keemail.me |
| Cryptography | RSA and AES |
| Target | English-speaking users and South Korean PC users |
| Ransom Note | DECRYPT_INFO.txt and DECRYPT_INFORMATION.html |
| Distribution | Exploit kits, malspam campaigns, fake software updates or cracks, Trojan horses |
The main difference between the older and newer version of Hermes 2.1 is that it has started using a new file marker at the end of the compromised file's content. According to the previous analysis, it used to leave HERMES file marker while now it has been supplemented with numerous random characters and symbols. So, only some part of Hermes 2.1 virus variants are appending [unlockmeplease@cock.li ].hrm or .HRM file extensions.
However, it is not the most important feature of the updated version. The latest offspring now combines AES-256 algorithm which is encrypted by RSA-2048 algorithm. This change makes it only harder for IT professionals to generate the decryption key because each encoded file features a diverse coding.
Although, other features of Hermes 2.1 remain the same — its developer still places the mp3 code of Vivaldi‘s Spring composition[1]. Additionally, the perpetrator continues to mention Wichita State University located in Kansas city and leaves two emails with considerations whether these details were left intentionally or unintentionally:
- BM-2cTSTDcCD5cNqQ5Ugx4US7momFtBynwdgJ@bitmessage.ch;
- BM2cT72URgs1AWGV6Wy6KBu2yuj3ychN5vxC@bitmessage.ch.
Fortunately, Hermes 2.1 malware and its newest version are already detectable by the majority of security applications as Trojan[Ransom]/Win32.AGeneric, Ransom.Hermes. Trojan.GenericKD.6154143, etc. It functions via the file called as ClrgraphicsOperation and My video.exe.
Certainly, the malware might disguise under alternative file. If you noticed some of your files already locked and marked with the .hermes, .HRM or .[unlockmeplease@cock.li ].hrm file extension or you receive DECRYPT_INFO.txt, and DECRYPT_INFORMATION.html, it is high time you initiated Hermes 2.1 removal.
You can remove Hermes 2.1 with the help of one of professional security software. We suggest using FortectIntego, but first, your must disable the virus to unblock your system and get access to download the antivirus. Learn how to do that from the guide which is attached at the end of this article.
The latest Hermes 2.1 variant spreads via Office documents embedded with Flash exploit: South Koreans under attack
South Korean Emergency Response Team (KrCERT) publicized about Hermes 2.1 ransomware virus which is currently attacking South Koreans via Flash Player 28.0.0.137 vulnerability using a sophisticated exploit kit dubbed as GreenFlash Sundown.[2] The same exploit has earlier been used by Lazarus,[3] a group of North Korean hackers who have previously attacked Taiwanese bank.
Ransomware payload is being distributed via malicious Word Office documents. Multiple scam campaigns have already been initiated to spread the payload widely. The first attack has been initiated via compromised Korean website at the end of February 2018.
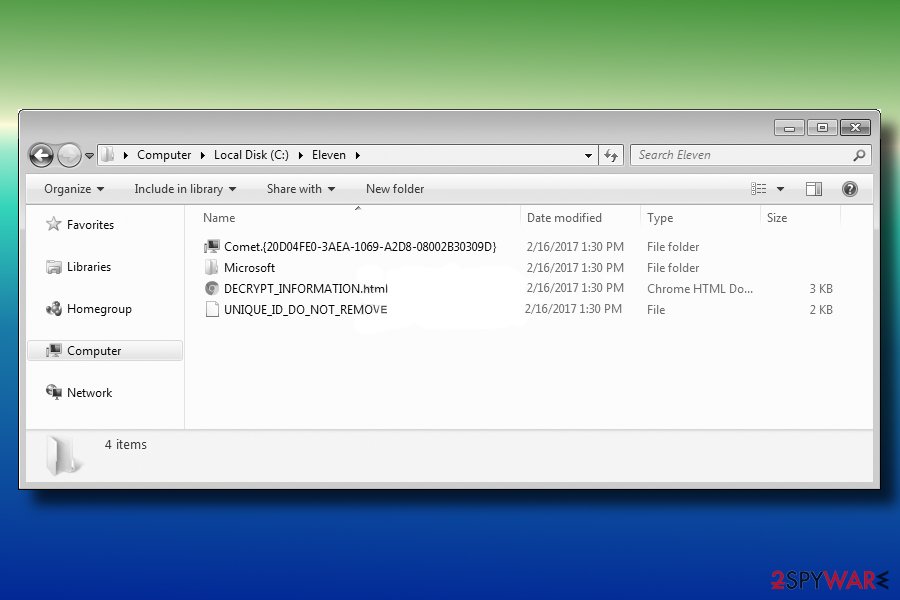
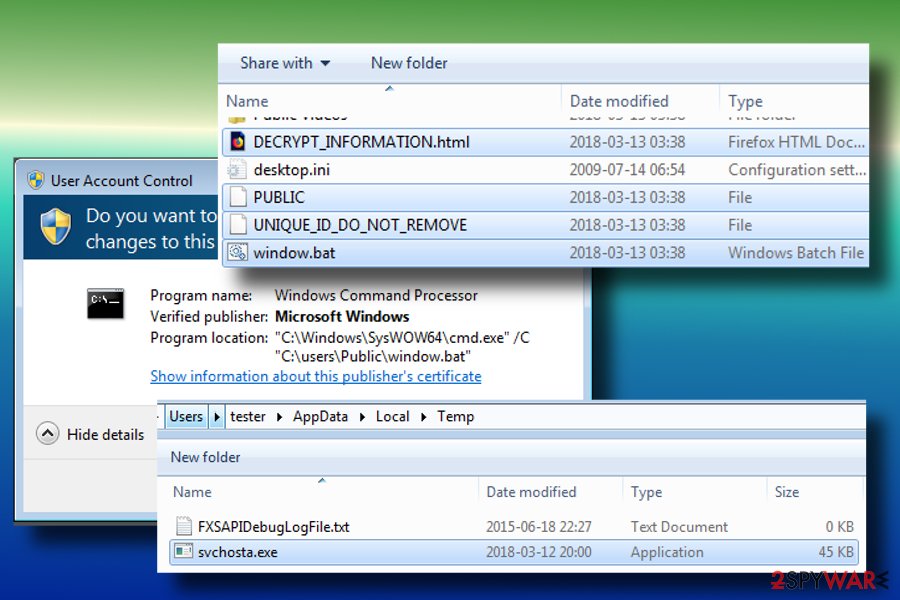
Once the Hermes 2.1 ransomware payload is executed, it creates a svchosta.exe file in %TEMP% folder. During the execution, the victim is asked for a permission to run the script. Even though the permission is not given, the virus starts encryption anyway.
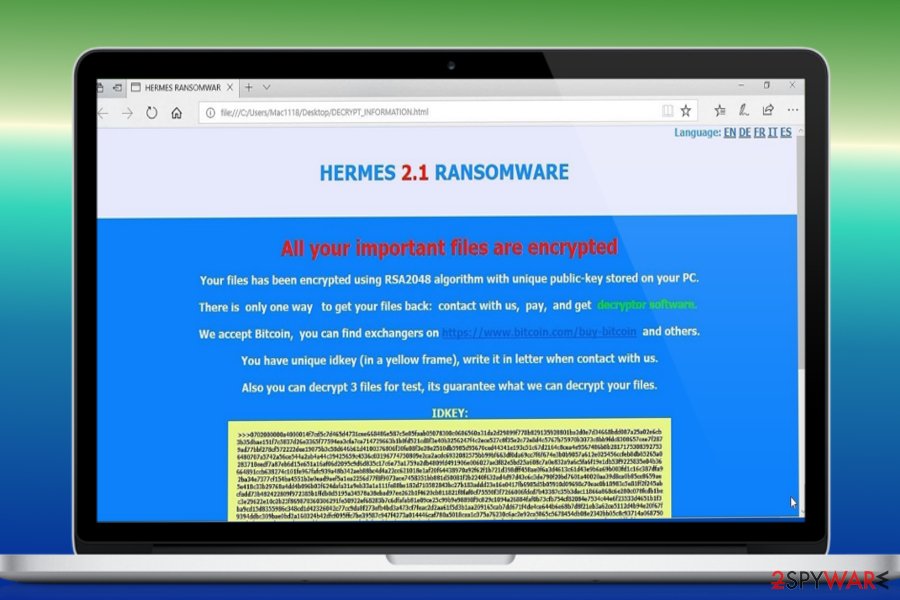
Upon encryption, it creates a file UNIQUE_ID_DO_NOT_REMOVE, which contains private RSA key and a ransom note named DECRYPT_INFORMATION.html in C:\Users\Public\ directory. The ransom note contains the following information:
All your important files are encrypted!
Your files have been encrypted using RSA2048 algorithm with unique public-key stored on your PC.
There is only one way to get your files back: contact with us, pay, and get decryptor software.
We accept Bitcoins, and other cryptocurrencies, you can find exchanges in bestbitcoinexchange.io
You have unique idkey (in a yellow frame), write it in letter when contact with us.
Also you can decrypt 1file for test, its guarantee what we can decrypt your files.
Each encrypted files gets the HERMES file extension. The victim is asked to contact the crooks via pretty040782@gmail.com, pretty040782@keemail.me or unlockmeplease@cock.li. The size of the ransom is unknown, though it may vary from 200 to 1500 USD.
Ransomware researches noticed an interesting tendency of this ransomware to exit the encryption code it detects registry key for Russian (0x419), Belarusian (423), or Ukrainian (422) language codes. Thus, we can only guess that the North Korean hackers are collaborating with Russian-speaking countries.
The original Hermes 2.1 ransomware variant is known to be cracked down after security experts created a free Hermes decryptor. Despite some minor modifications, the core behavior of all three variants of this ransomware is very similar, so you should try a free decryptor.
If the decryptor failed to unlock your files, the best solution you have is to remove Hermes 2.1 completely and then recover your data using backups or other alternative methods.
Those who wonder how to protect themselves from this infection has only one option – to install a reputable anti-virus and keep its definitions up-to-date. Besides, stay away from questionable email messages and DO NOT open their attachments.
Common attack vectors of ransomware
Unfortunately, criminals employ multiple distribution techniques to help them infiltrate the ransomware on as many computers as possible. As a result, it might become hard to identify the potential sources of this dangerous cyber threat. However, we aim to raise awareness and help regular computer users protect their systems.[4]
These are the most common attack vectors of ransomware:
- Exploit kits;
- Malspam campaigns;
- Fake software updates or cracks;
- Trojan horses.
Considering the executable name, it is likely that the malware is spread in gaming sites at the moment. If you value your data, you should consider avoiding such domains. It is common knowledge that pirated software, keygens, and cracks have been popular tool exploited by malware developers.
Likewise, in order to limit the possibility of Hermes 2.1 hijack, install a couple of different security applications. In addition, be careful reviewing spam emails especially if they are sent by the official institutions. Examine the content of the message and inquire the official institution again to verify the received attachment.
Instructions on how to uninstall Hermes 2.1 virus
Unfortunately, ransomware-type viruses are explicitly dangerous and hazardous computer threats. Even IT experts might struggle to remove Hermes 2.1 from the victimized systems. Likewise, regular computer users should not try to eliminate the malware without any assistance.
If you found [unlockmeplease@cock.li ].hrm, .hermes or .hrm file extensions appended to your files, you need to get rid of Hermes 2.1 with the help of robust malware removal software. However, this is a complex virus which might block your system and prevent you from installing the antivirus. You should de-activate the ransomware by booting your computer into Safe Mode.
Instructions on how to do that are appended at the end of this article. Afterward, you should be able to access the tool and complete Hermes 2.1 removal. Only after the elimination is complete, proceed to data recovery. Experts from DieViren.de[5] suggest you might try using the free Hermes decrypter designed for the original version.
Getting rid of Hermes 2.1 virus. Follow these steps
Manual removal using Safe Mode
It is important that you disable the ransomware before installing antivirus software. If you fail to do so, it will block you from downloading any content which might be used against the virus. Learn how to boot your system into Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Hermes 2.1 using System Restore
Here is another method which might help you circumvent the system of the ransomware:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Hermes 2.1. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Hermes 2.1 from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Hermes 2.1, you can use several methods to restore them:
Data Recovery Pro might be useful
Initially, experts have developed this tool to assist the users if their information has been damaged during the system crash or they unintentionally deleted them. However, in some cases, it might be helpful if you are the victim of ransomware attack as well.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Hermes 2.1 ransomware;
- Restore them.
Experts say you might try Hermes 2.1 Decryptor
Since Hermes 2.1 is an offspring of the original Hermes program, you can try using its decryption tool here. You will have to provide an encrypted file and its original, just drag and drop them on the executable. However, if the hackers fixed flaws related to their first version, the decrypter can fail to work.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Hermes 2.1 and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Michael Gilespie. New Hermes 2.1 ransomware spotted by malwrhunterteam. Twitter. Online source for communication and news.
- ^ CVE-2018-4878 (Flash Player up to 28.0.0.137) and Exploit Kits. MDNC. Malware don't need coffee. Blog.
- ^ Chasing Lazarus: A Hunt for the Infamous Hackers to Prevent Large Bank Robberies. Kaspersky Lab.
- ^ Pranshu Bajpai, Aditya K Sood, Richard Enbody. A Key-Management-Based Taxonomy for Ransomware. Anti-phishing working group, inc..
- ^ Eliminate computer threats. Dieviren. Security news in German.





















