TrueCrypt ransomware / virus (Virus Removal Instructions)
TrueCrypt virus Removal Guide
What is TrueCrypt ransomware virus?
What must you know about TrueCrypt virus?
TrueCrypt ransomware virus aims to attack your computer and lock the personal files. Moreover, once it succeeds in this mischievous deed, it threatens you to transmit the money within 72 hours. Otherwise, the private key which is needed for decryption will be eliminated permanently. Though all this seems terrifying, however, you should not go panicking. Instead, think of the ways to remove TrueCrypt virus from the system. Luckily, we present you with the most suitable solutions. One of such is installing FortectIntego.
How does the virus function?
Some may suspect that TrueCrypter virus was given such name not just by accident. There is a program also called “TrueCrypt” which enables users to lock the data from unauthorized users. Thus, IT professionals have reported that some versions of the program had been distributed supplemented with a trojan. Likewise, some might relate this information to this ransomware. Speaking of the virus, it acts like other samples of the ransomware. It might attack users via spam emails which contain infected attachments. Once they are opened, the virus gets activated and starts searching for .cfm, .class, .cmd, .config, .cpp, .cr2, .crw, .cs, .csh, .csproj, .csr, .css, .csv, .cxx, .d, .db, .dcr, .dds, .deb, .dib, .dng, .doc, .docm, .docx, .dot, .dotm, .dotx, .dtd, .eps, .fla, .fpx, .gif, .gif, .gz, .gzip, .h, .hpp, .hta, etc. The virus locks the data and compresses it to %APPDATA%\Microsoft\TrueCrypter\Encrypted.dat. When the information is locked, TrueCrypt ransomware forcefully replaces your desktop wallpaper with a ransom note alarming you to pay the money within the specified period of time.
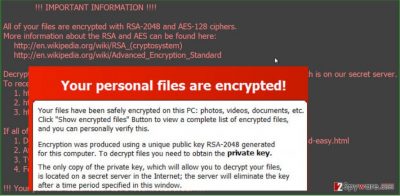
Moreover, it seems that the virus also uses an RSA-2048 algorithm. One of new features might be perceived as providing the email for contacting — trueransom_@_mail2tor.com. Moreover, the virus is relatively modest; it asks only for 93$ ransom while other “siblings” of the same family – 400$ and more. In the text file with the data recovery instructions, TrueCrypt malware provides information how users can create BitCoin wallet. Additionally, the virus accepts financial transactions via Amazon gift cards. In relation, these techniques might have flaws since tracking the source domain of the virus might not be a significantly difficult task. However, for the time being, TrueCrypter still roams unstoppable.
You should be aware that the virus might sneak into a computer via “fileless infections” as well. These files are peculiar in the sense that they leave few traces on the system and usually serve as minor spies which collect the information about the operating system. Afterward, hackers might use the compiled data to develop new techniques for creating ransomware. Note that it is crucial to ward off these files from your system. Therefore, it is a must to have a reputable spyware and malware removal tool. You might also try using data recovery programs – PhotoRec and R-studio, as well. Now let us proceed with TrueCrypt removal.
How can I remove TrueCrypt?
There are mainly two options to get rid of this hideous virtual threat. The first method includes manual TrueCrypt removal. If you feel confident enough that you will deal with this elaborate virus on your own, you can take a look at the removal instructions provided below. Thoroughly go through each step. You shouldn’t miss any detail. You can terminate TrueCrypt virus automatically as well. In fact, this option provides more guarantees that the threat will be permanently deleted. An anti-spyware program is specifically created for detecting and removing malware and ransomware. Lastly, when your system is completely cleaned and restored, consider the alternatives to store your personal data to avoid its loss again.
Getting rid of TrueCrypt virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove TrueCrypt using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of TrueCrypt. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from TrueCrypt and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.





















