Cinsiant.com ads (spam) - Free Instructions
Cinsiant.com ads Removal Guide
What is Cinsiant.com ads?
Cinsiant.com is a fake website that aims to trick people into accepting push notifications from it

Cinsiant.com is an untrustworthy site that individuals might encounter while browsing through low-quality websites or after clicking on unsafe links. The presence of undetected adware on a user's system can increase this risk, as such programs frequently distribute insecure pop-up advertisements.
Users typically become alerted to Cinsiant.com when they notice intrusive pop-ups appearing on their screens. It's easy to jump to the conclusion that these pop-ups are the result of a virus on their system, but that's not necessarily the case. For these pop-ups to appear, certain criteria must be met:
- The user has previously clicked the “Allow” button on a notification prompt from the site.
- A web browser is open, whether or not it's currently being used.
The subtlety of this scheme is in its use of advanced deceptive techniques to lure users into activating its push notifications. Often, these methods include displaying crafty messages designed to camouflage the real reason for the notification request.
Moreover, once the user consents to the notifications by clicking “Allow,” the resulting ads from Cinsiant.com may not surface immediately. This delay can cause users to overlook or forget their past interaction with the website.
| Name | Cinsiant.com |
| Type | Push notifications, ads, scam, pop-ups |
| Distribution | After users click the “Allow” button within the prompt upon site entry |
| Symptoms | The ads shown within push notifications might include misleading messages and links to malicious websites. If clicked, you might end up infecting your system with malware, disclosing your personal information, or losing money |
| Risks | Push notification prompts might include links to malicious websites, resulting in financial losses, personal information disclosure, or malware infections |
| Removal | You may turn off notifications in your browser settings. If you notice more ads and redirects to suspicious sites, run SpyHunter 5Combo Cleaner anti-malware on your computer to check for adware infection |
| Other tips | If you do not clean your browser from cookies and other web data, you see the unwanted ads return, or data continue being tracked. Clean your browsers with FortectIntego to stop these trackers |
Users are tricked by misleading messages
Individuals are naturally averse to agreeing to push notifications from dubious sources. Scammers are aware of this hesitance and have devised clever methods to manipulate users into accepting such alerts. These tactics include setting up fraudulent sites, similar to Cinsiant.com, that trick users into believing that pressing the “Allow” button is benign or even necessary.
The stratagems employed by these swindlers involve various forms of social engineering. They might prompt users with statements that imply a routine verification process is in place, such as confirming one's age or proving they are human, or they might fabricate technical reasons to coax a user's compliance.
- Press “Allow” if you are not a robot
- Click “Allow” to win a prize and get it in our shop!
- If you are 18+, click Allow
- Click Allow to watch the video
- Your file is ready to download – press Allow to continue
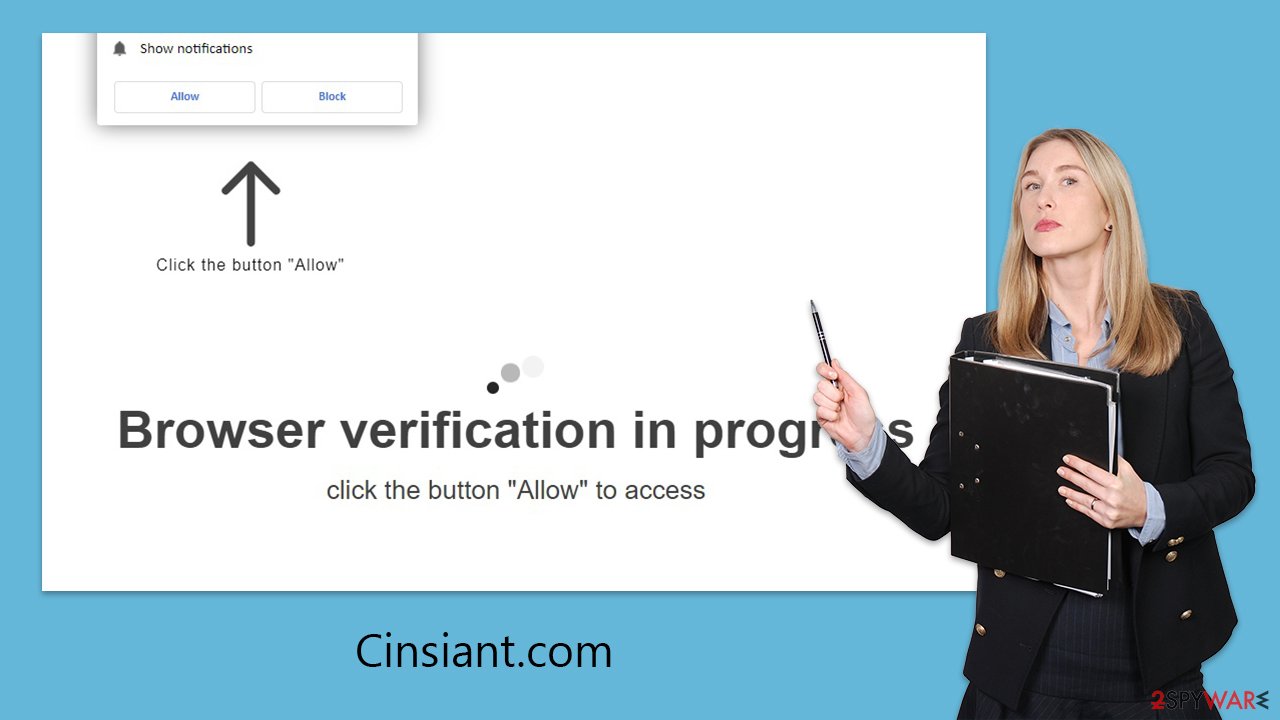
These prompts are cunningly designed to mirror legitimate requests users frequently encounter online, making the deceit harder to discern. They are variations on a theme, widely used across a spectrum of deceptive websites, each with the same goal: to trick users into thinking that clicking “Allow” is a harmless, routine step.
Should you opt to “Block” these notifications, the scheme may redirect you to the same or another website, urging you to perform the action they seek. Succumbing to their requests leads to an increase in unsolicited spam each time you open your browser. It is also wise to exercise caution and avoid interacting with these pop-ups, as they can be gateways to phishing schemes or sites laden with malware.
Dangers of suspicious push notifications
The onset of push notifications from malevolent sites like Cinsiant.com is rarely as sudden as it seems; they are a result of permissions given, often without the user's conscious intent. If unexpected pop-ups from Cinsiant.com have begun to interrupt your online activities, it's an indication that, at some juncture, you've inadvertently agreed to receive them.
These notifications are not restricted to the times you navigate specific websites; they can appear even when the browser is minimized or left running in the background. They typically emerge in particular areas of the display, determined by the system's design.
The content delivered by these pop-ups is a significant concern, as it often includes misleading information. For example, users may be enticed by attractive remote job offers that require an initial investment. Many individuals, lured by the prospect of high returns, engage with these offers only to discover that the job opportunity doesn't actually exist.
Furthermore, some notifications are designed to impersonate legitimate system warnings, suggesting that your computer is at risk and promoting the download of supposed security software. These can be a guise for elaborate tech support swindles, where unwary users may end up installing unnecessary and potentially harmful software.
Removal of unwanted push notifications and adware
Navigating online can sometimes lead to unexpected detours to deceitful websites, and this likelihood increases if adware has compromised your system. Warning signs, like a barrage of pop-ups, a deluge of too-good-to-be-true offers, and unsolicited redirects to dubious web pages, can all indicate the presence of such intrusive software.
In light of these threats, it is imperative to perform an in-depth scan of your system using a reputable security solution. Employing tools such as SpyHunter 5Combo Cleaner, Malwarebytes, or similar dependable antivirus programs can provide a robust defense. A thorough scan not only eradicates existing malware, including adware, browser hijackers, and trojans but also fortifies your system's resistance against future infiltrations.
Post-cleanup, a dedicated utility like FortectIntego is advisable to purify your web browsers from any residual damage caused by the malware. This step is crucial to remove tracking elements and restore your browser to its pristine state.
To halt the invasive push notifications from Cinsiant.com, venture into your browser's settings to prohibit any further alerts from this URL. The specific instructions for this will vary based on the browser you use. Locate the relevant settings section and adhere to the guidance to block these unwanted notifications effectively.
Google Chrome (desktop)
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
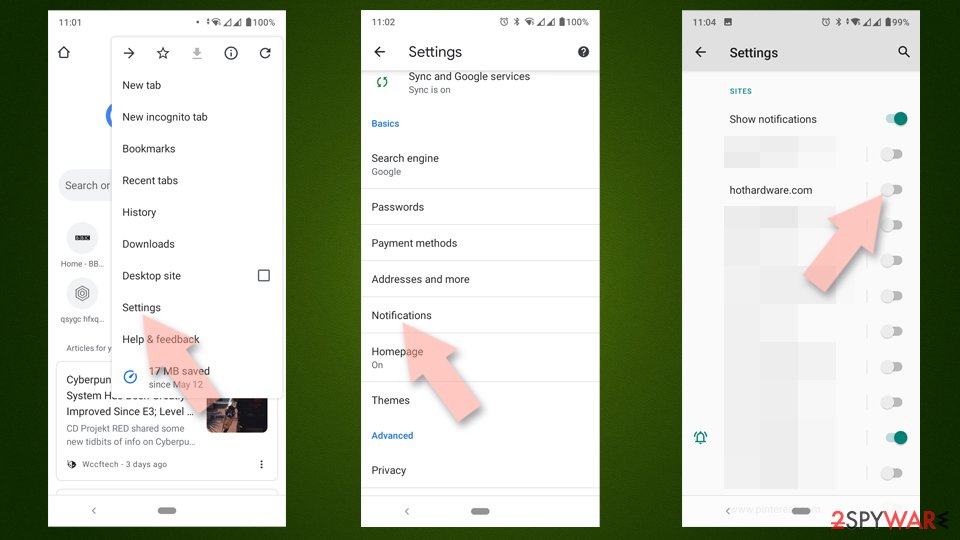
Google Chrome (Android)
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to the Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
![Stop notifications on Chrome Android Stop notifications on Chrome Android]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
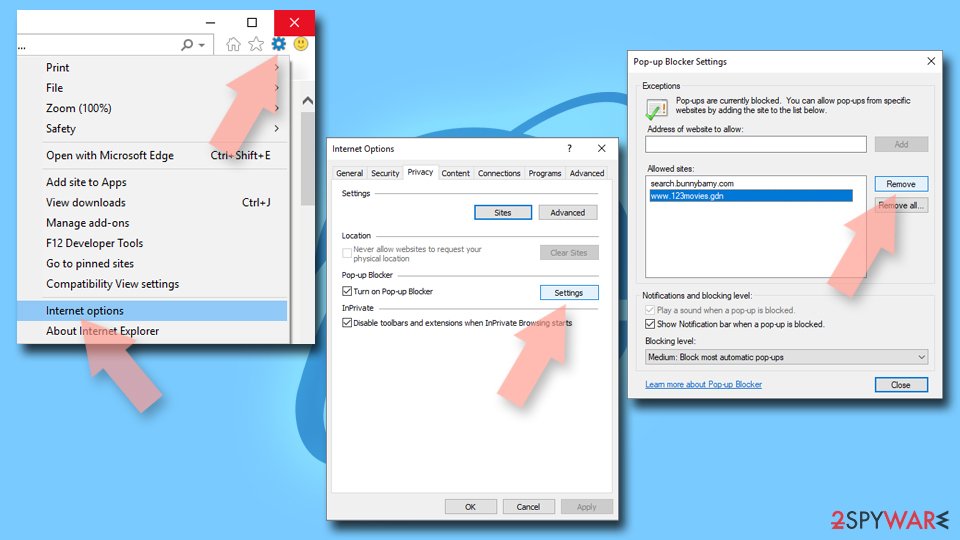
Internet Explorer
- Open Internet Explorer, and click on the Gear icon at the top-right of the window.
- Select Internet options and go to the Privacy tab.
- In the Pop-up Blocker section, click on Settings.
![Stop notifications on Internet Explorer Stop notifications on Internet Explorer]()
- Locate the web address in question under Allowed sites and pick Remove.
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.