Weatherly browser hijacker (Chrome, Firefox, IE, Edge) - Free Instructions
Weatherly browser hijacker Removal Guide
What is Weatherly browser hijacker?
Weatherly is a potentially unwanted browser extension that takes over your searches and shows unwanted ads

Weatherly is a common type of browser hijacker that often alters browser settings to benefit from ad revenue. Users seldom install such extensions deliberately; rather, they are usually surprised to find Weatherly operating on their system. This often occurs through deceptive tactics like software bundling or through misleading advertisements and deceptive update prompts.
Upon installation, Weatherly immediately modifies the browser’s homepage and new tab settings, typically customizing these based on the user's location. While this alteration may seem minor at first, it serves the hijacker’s primary objective: to generate income through ad placements.
This adjustment can lead to search queries being redirected through dubious URLs or to different search engines. Additionally, advertisements are frequently injected at the top of search results, which may promote various unwanted software. If you find the altered search results and intrusive ads bothersome, it would be wise to eliminate the Weatherly browser hijacker from your system.
| Name | Weatherly |
| Type | Browser hijacker, potentially unwanted browser extension |
| Distribution | Software bundles, ads, redirects |
| Symptoms | A browser extension or an application installed on the device; homepage and new tab address set to its own; ads and sponsored links in search results and elsewhere |
| Risks | Data tracking from various third parties, exposure to malicious ads, redirects to suspicious sites |
| Removal | You can eliminate the browser hijacker by adjusting your browser's settings. Scanning your system with SpyHunter 5Combo Cleaner security software will confirm that there is no adware or malware running in the background |
| Other tips | After removing all potentially unwanted applications, we recommend you employ the FortectIntego utility to clean your web browsers and repair any damaged system files |
What are browser hijackers? Are they dangerous?
While browser hijackers like Weatherly may not pose as severe a threat as some computer viruses, their impact should not be underestimated, especially when they are installed without the user's knowledge. Their primary effect is to disrupt the user's online browsing experience, altering search functions and internet accessibility.
Weatherly, like other browser hijackers, typically pushes non-organic search results and links, often disguised as “ads” at the top of search results. These can be easy to click on inadvertently, leading users to misleading or inaccurate information.
Interestingly, browser hijackers and other potentially unwanted programs (PUPs) often masquerade as beneficial tools. They use appealing descriptions, promising “enhanced,” “fast,” or “secured” searches. In the case of the Weatherly browser extension, it shows the weather forecast on the homepage (functionality can be achieved in many different ways besides installing this app).
However, these promises are merely deceptive tactics used by the creators of PUPs to capture users' attention. In practice, these tools modify the search engine settings and search results to insert more ads, thus increasing their pay-per-click profits.
In conclusion, while browser hijackers like Weatherly may not directly damage your system, they can significantly disrupt your web browsing activities. This is particularly true if users do not pay close attention to the subtle changes these programs make.
Additionally, the increase in advertisements and potential tracking by third parties further adds to the annoyance. Despite their appearance of usefulness, the negative impacts on user experience and privacy are significant and should not be overlooked.
How to remove Weatherly and check the system for other infections?
While browser hijackers like Weatherly are less damaging than malware, they still pose significant risks to a user’s online experience and privacy due to their data monitoring capabilities. Such applications can intrusively modify browsing settings without permission, tracking user activity and displaying unwanted advertisements.
It is crucial, therefore, to remove any potentially unwanted applications, as allowing them to run unchecked offers no benefits to the user and can compromise both performance and security.
Weatherly typically infiltrates systems as a browser extension. To tackle this issue effectively, it is advisable to first identify and remove the extension. Prior to this, as a safety measure, it’s recommended to scan your system for more harmful threats to ensure that the browser hijacker hasn’t left the door open for more severe malware infections.
Tools like SpyHunter 5Combo Cleaner or Malwarebytes are designed to perform these checks quickly and efficiently, ensuring that your system is secure. Once you have confirmed that your system is clear of viruses, you can safely proceed to remove the Weatherly plugin, restoring your browser's original settings and functionality.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the window's top-right).
- Select Add-ons.
- Here, select the unwanted plugin and click Remove.

MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Internet Explorer
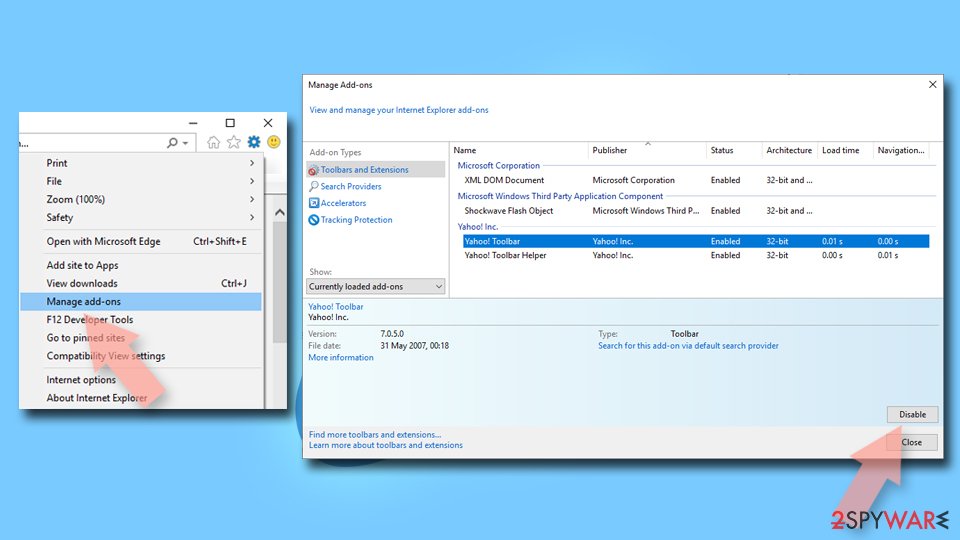
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
Erasing cookies and other web data
Browser hijackers, like many potentially unwanted applications, are notorious for their data-tracking capabilities. They exploit this data, which is highly valuable to marketing companies, often selling or sharing it for profit. To facilitate this, third-party applications utilize various tracking technologies such as cookies, web beacons, and pixels.
These small data-tracking tools can remain on your local machine and continue to operate even after the removal of the hijacker like Weatherly. It's crucial to ensure that web caches, where these trackers are stored, are thoroughly cleaned. Regularly clearing your caches not only removes these trackers but also enhances your overall security and helps avoid bugs and errors while browsing.
The simplest method to cleanse your system of leftovers from potentially unwanted programs is by using FortectIntego. This tool efficiently eliminates all trackers and unnecessary files from your system and addresses any issues that may occur post-malware infection, such as system crashes and program errors. If you prefer to clean your browsers manually, you can follow these steps:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Internet Explorer
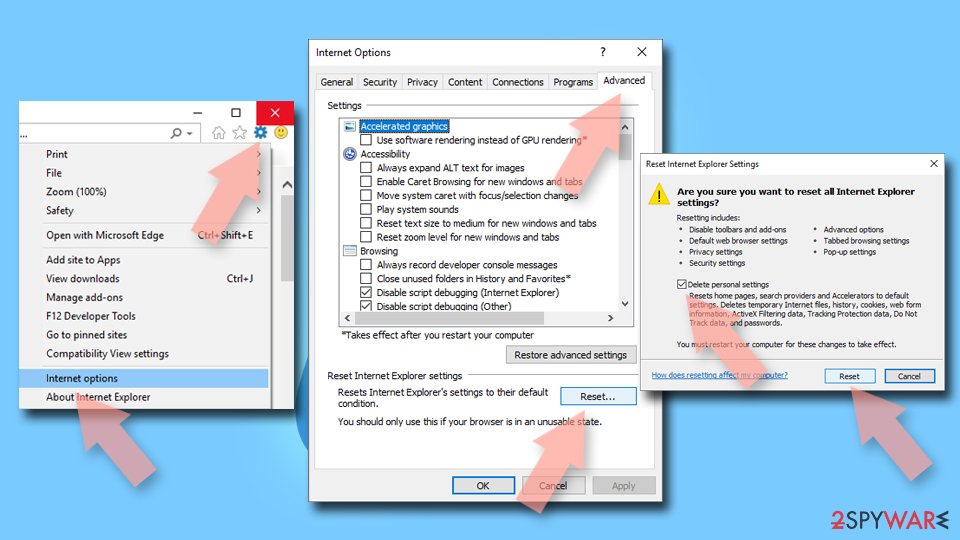
- Click on the Gear icon > Internet options and select the Advanced tab.
- Select Reset.
- In the new window, check Delete personal settings and select Reset.
How to prevent from getting browser hijacker
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
