Pcdsecuresupdates.live scam (virus) - Free Guide
Pcdsecuresupdates.live scam Removal Guide
What is Pcdsecuresupdates.live scam?
Pcdsecuresupdates.live – a malicious website designed to imitate legitimate security providers
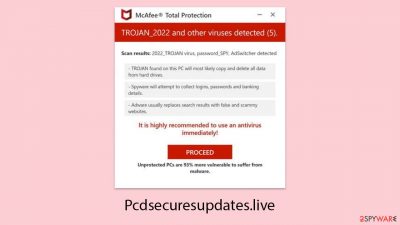
Pcdsecuresupdates.live is recognized as a fraudulent website meticulously crafted to mislead individuals into believing their devices are infected with malware. Upon visiting, users are immediately confronted with a fabricated alert, designed to resemble a McAfee security notification. This false alert declares that the user's device has been compromised by viruses and malicious websites, triggering unwarranted concerns.
It is vital to acknowledge that this alert is entirely bogus and has no association with legitimate McAfee products. These fake warnings serve as manipulative tools used by fraudsters to profit from advertisements and affiliate marketing through questionable practices.
Moreover, Pcdsecuresupdates.live deceptively prompts users to enable push notifications. Yielding to this request may result in frequent disruptions from these fictitious virus alerts. Individuals are advised to avoid any interaction with Pcdsecuresupdates.live and to perform a thorough scan of their system for potential adware. Staying informed and vigilant is crucial for protecting one's device from these deceptive strategies.
| Name | Pcdsecuresupdates.live |
| Type | Scam, ads, redirect, rogue website |
| Infiltration | Compromised websites, pop-up ads, potentially unwanted applications |
| Scam content | Scammers report that their alleged security software – McAfee – has expired and that their systems are in danger. They immediately recommend downloading software from the affiliated link |
| Dangers | Installation of other potentially unwanted software or malware, personal information disclosure to cybercriminals, financial losses due to scams, etc. |
| Removal | You should not interact with the content shown by a scam website. Check your system for adware or malware infections with SpyHunter 5Combo Cleaner security software |
| Remediation | To prevent third parties from tracking your online activities, we recommend clearing browser caches and other leftover files with FortectIntego |
Scamming techniques used by crooks
Fraudsters exploit fear by employing various schemes to take advantage of people, particularly those who may not be tech-savvy. They prey on fears to deceive and swindle.
A common tactic is to issue fake warnings about malware threats. These are often seen on dubious websites that use advertising networks not thoroughly vet ad content. Consequently, users visiting sites with pirated content or unauthorized streams might encounter scam alerts or harmful ads.
For example, tactics similar to those used by sites like Pcdsecuresupdates.live include crafting alerts that mimic the look of legitimate security software. These false alarms might present alarming messages such as (can vary):
Your PC is infected with 5 viruses!
IMMEDIATE ACTION REQUIRED!
Your McAfee subscription has expired!
Renew now to keep your PC protected.
Viruses found on this PC most likely track internet activity to collect banking details and login credentials. Unprotected PCs are 93% more vulnerable to suffer from malware.
It's critical to recognize that real malware detection and removal can only be conducted by legitimate security software actually installed on your device. Signs of scam alerts are their uniform message, irrelevant to the actual condition of your device, and the fact that real security notifications are not distributed via browser pop-ups, highlighting the deceitful nature of these alerts.
Tips to avoid being deceived or infected with malware
People often stumble upon scam websites via two main methods: accidental clicks on compromised links or through the influence of adware and other malicious software.
In the first case, individuals might visit legitimate sites that, due to security weaknesses or the use of outdated technologies, have been manipulated by hackers. These attackers insert harmful codes into the site that redirect users to dangerous websites when interacted with. These deceptive links are skillfully designed to look genuine, making them difficult to recognize. Typically, the scam is only realized after it has inflicted harm.
Alternatively, a user's device may become infected with adware or similar types of malware. This kind of software aggressively forces unwanted ads onto the user, often sneaking in bundled with other downloads from the internet. As a result, individuals may find themselves redirected to unintended web pages or bombarded with pop-ups leading them to scam sites.
Regardless of the path to these fraudulent websites, the consequences can be severe, from financial losses to breaches of personal identity. This situation highlights the critical need for vigilant online behavior and the maintenance of robust security measures on all devices.
How to recover from encountering Pcdsecuresupdates.live scam
Addressing the fraudulent activities of Pcdsecuresupdates.live involves varied remedial steps, depending on your engagement with the site and the software installed on your device. If you have interacted with the site's suspicious prompts or clicked on compromised links, it's possible that malicious software has been installed on your computer.
Even without direct interaction, keeping your system secure is critical, especially since adware often plays a significant role in the infiltration of phishing sites into your system. To comprehensively remove any potential adware, a full system scan with reliable security software SpyHunter 5Combo Cleaner or Malwarebytes is recommended. Trusted tools are designed to effectively identify and eliminate malicious content swiftly.
While manual removal of unwanted applications is an option, utilizing automated apps is generally easier and safer. Incorrect manual deletion could accidentally remove necessary software, leading to unintended consequences.
After clearing your system of harmful programs and intrusive ads, it's also important to remove any cookies or trackers that may remain in your browser. You can either use a dedicated cleaning tool FortectIntego or follow simple manual steps to ensure your browser is also free from privacy threats.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Fraudulent websites like Pcdsecuresupdates.live have broadened their schemes to exploit features beyond direct engagement, notably leveraging the push notification functionality. Push notifications, intended by genuine sites for delivering immediate updates or alerts to users' screens, have been manipulated by scam sites.
They trick users into enabling these notifications through deceptive prompts or counterfeit warnings. Once permission is given, these sites can flood the user with questionable messages, independent of active site navigation.
The challenge persists even after the removal of any dubious software from one's computer, as these alerts are not tied to installed applications but to the browser's permissions. Thus, the elimination of malware doesn't halt the intrusive notifications, which can continue to disturb the user's online experience.
These persistent notifications can be used for various harmful objectives, including phishing schemes or directing users to more scam sites. Fortunately, there is a solution to this problem. Detailed steps to stop these malevolent push notifications are provided below, offering a way to regain control over one's online interaction environment.
Google Chrome
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the URL's drop-down menu.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
- Click on More actions and select Block.
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.








