Malicious Skype ads spread malware disguised as Flash Player Update
Microsoft Windows users should be aware of ongoing Skype malvertising campaign[1], which pushes bogus Flash Player updates to users. It shortly became apparent that culprits working behind this malvertising campaign are highly skilled cyber criminals[2] that continuously create domains to host malware on and delete the old ones rapidly. It turns out that due to a malvertising campaign Skype users are receiving suggestions to install Flash Player update every time they logged into their accounts. These malicious ads immediately trigger a “File Download – Security Warning” window, which asks the user whether one wants to run or save the file called FlashPlayer.hta. The only suspicious thing about this pop-up is the source where the “required update” is going to be downloaded from.
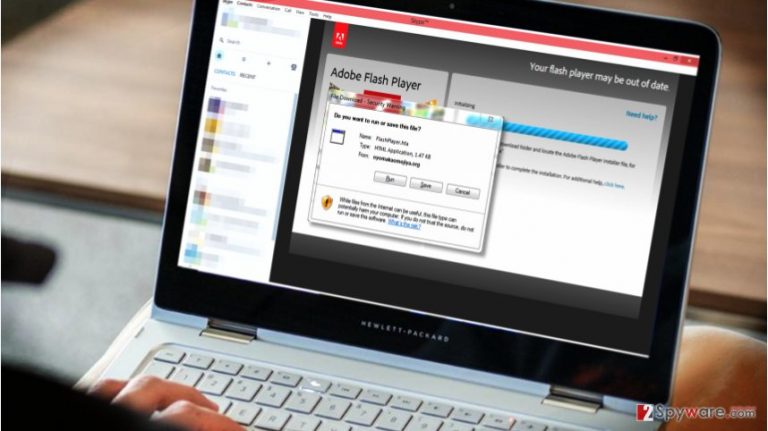
According to user’s reports and screenshots posted on Twitter, Reddit, as well as Skype Community forums[3], malicious Flash Player updates were hosted on oyomakaomojiya(.)org, admdownload.adobe.com and cievubeataporn(.)net, which, obviously, are not web pages related to Adobe, which is the official developer of Adobe Flash software. The malicious FlashPlayer.hta file was used to launch and run a PowerShell script, which downloads the final payload[4]. The described malvertising campaign reportedly distributes malicious FlashPlayer.jse file, which hasn't been analyzed yet because researchers can no longer get a sample of it – all of the aforementioned domains were taken down shortly after being set up. However, considering that the malvertising campaign pushed encrypted JS files to users, there is a reason to believe that they were distributing ransomware viruses, most likely Locky, which used JavaScript-based attacks to infect victims in the past[5], or Cerber. According to the latest reports, websites used to host malware that was pushed to users via Skype were registered using email accounts that were previously used to set up hundreds of other highly suspicious sites.
The quick register-deregister process reportedly helps criminals to sidestep the need to pay for the domain and also contributes to keeping malware analysts away from malware samples. Representatives of Microsoft commented on the issue by saying that the described ads appeared due to “social engineering” efforts, and said that the company is not responsible for these malicious ads. According to the spokesperson of Microsoft, these bogus warnings were just rogue ads displayed to users and that the most efficient way to run a system check with anti-spyware or anti-malware software. We would like to add that you should definitely familiarize with the latest tricks used by cyber criminals to know what to expect and how to prevent malicious attacks against your PC. For instance, you can learn more about Skype viruses by reading this article. You might also be interested in ways how criminals employ fake software updates for ransomware distribution.
- ^ Bogdan Popa. Microsoft’s Skype Serving Fake Flash Player Update Ads Deploying Malware. Softpedia. Latest News & Reviews.
- ^ Michael Hill. Techniques of Cyber-Criminals Continue to Evolve. Infosecurity Magazine. Information Security & IT Security News and Resources.
- ^ BEWARE! Adobe Flash Player Update. Skype Community. Skype Peer-to-Peer Support and Discussion Community.
- ^ Fake Flash Player ads on Skype push malware to users. eSolutions Blog. News, Tips and Updates on Cyber Security.
- ^ Maharlito Aquino. Locky Ransomware Now Embedded in JavaScript. Cyren Security Blog. Security Research & Analysis.

