WebCoordinator Mac virus (Tutorial)
WebCoordinator Mac virus Removal Guide
What is WebCoordinator Mac virus?
WebCoordinator – a malicious application that can put you and your Mac in danger
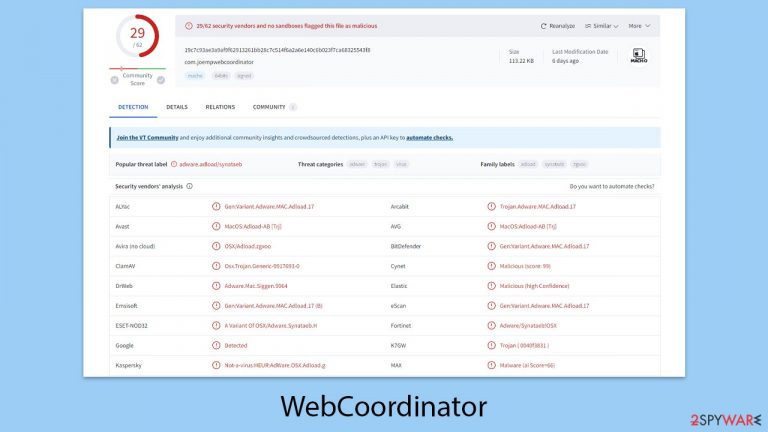
WebCoordinator is a Mac virus that falls under the Adload malware family, a group notorious for its harmful activities online. This virus commonly hijacks browser settings, displays unwanted ads, and steals sensitive data such as passwords and credit card numbers. It often tricks users into downloading it by pretending to be something harmless like a Flash Player installer, effectively acting as a Trojan horse to enter your system.
Once it infiltrates a computer, WebCoordinator gains root access, allowing it to spread further by installing more of its kind or other harmful software. This can significantly compromise your system’s security. The ads it inserts are not just annoying; they can be dangerous too, leading to more infections if clicked on accidentally.
A clear sign of infection is when your usual browser settings, whether on Safari, Chrome, or another browser, are altered without your permission, often redirecting to a dubious search engine like Safe Finder.
The threat WebCoordinator poses to both your privacy and online safety is severe. To protect yourself, be cautious about what you download and ensure your operating system and antivirus are always up to date. If you suspect your device has been compromised by this virus, take immediate action to remove it following the guidelines provided here.
| Name | WebCoordinator |
| Type | Mac virus, adware, browser hijacker |
| Malware family | Adload |
| Distribution | Pirated software installers, fake Flash Player updates, misleading ads |
| Symptoms | A new extension is installed on the browser, along with an application of the same name; search and browsing settings altered to an alternative search provider; new profiles and login items are set up on the account; intrusive ads and redirects |
| Removal | The easiest way to remove Mac malware is to perform a full system scan with SpyHunter 5Combo Cleaner security software. We also provide a manual guide below |
| System optimization | For best performance and system remediation, employ FortectIntego. Also, cleaning web browser caches is highly advised after the elimination of malware for better privacy and security |
Spreading techniques
WebCoordinator shows minimal changes to its code, indicating its original design is effectively disrupting Apple devices. Its longevity and minimal updates reflect its success in exploiting Apple's ecosystem using sharp distribution tactics and operational methods.
Adload itself has become a well-known threat largely due to its clever but simple distribution strategies. One prevalent tactic involves displaying deceptive prompts for Flash Player updates on various websites. Users typically encounter these prompts after clicking on a dubious link on a risky website or when adware is already active on their systems.
The trick is straightforward but effective. Users are misled into believing they need to install or update Flash Player to view certain multimedia content. However, since Flash Player was officially discontinued by its developers a few years ago, any prompt to install or update it is undoubtedly fraudulent.
Another common method for spreading Adload involves malicious installers shared on peer-to-peer networks and sites offering pirated software. These platforms are notorious for spreading malware, and it is wise to avoid downloading software from these sources.
To stay safe from such threats, it is essential to be cautious about where you download software from and to keep your system's security measures up to date. If WebCoordinator or any other Adload-related malware infects your device, taking immediate steps to remove the infection and secure your system is critical.
WebCoordinator virus in detail
WebCoordinator has been part of the Adload malware family for over seven years, and during that time, it has seen only minor updates. This suggests that the original malicious code is so effective that hackers have felt little need to change it. This particular strain thrives on Apple devices due to its highly effective distribution methods and operational tactics.
The main goal of WebCoordinator is to display ads and generate revenue through pay-per-click schemes. However, it also includes several features that support its primary advertising functions. For instance, it can bypass Mac's built-in defenses like XProtect and Gatekeeper by using AppleScript. This allows the malware to download and install other harmful software without the user's permission.
Once the virus is on a device, it often adds a browser extension that bombards the user with intrusive and harmful ads during web sessions. This extension does more than just annoy the user; it can also track and collect a variety of personal information. This includes passwords, credit card details, and other sensitive data entered into browsers, posing a significant threat to user privacy and security.
To protect your device from such threats, it's crucial to stay vigilant about what you download and keep your security software up to date. If you find that your device has been compromised by the WebCoordinator virus, immediate action is necessary to remove the malware and secure your information.
Remove the threat thoroughly
Once the malware has infiltrated the system, it initiates background processes to carry out its harmful activities. To uninstall the main application, you should first open the Activity Monitor and terminate its associated processes by following these steps:
- Open Applications folder
- Select Utilities
- Double-click Activity Monitor
- Here, look for suspicious processes related to adware and use the Force Quit command to shut them down
- Go back to the Applications folder
- Locate the malicious app and move it to Trash.

After handling the main app, open Safari, Chrome, or any other browser you use, and remove the extension identified by a magnifying glass icon on a gray background.
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

In certain situations, it might not be possible to remove the malware’s extension through regular methods. Resetting your browser can help bypass the app’s persistence mechanisms and allow you to remove the extension smoothly. If you require assistance with this process, follow these instructions:
Safari
- Click Safari > Preferences…
- Go to the Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

Google Chrome
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Remove Login items and leftover components
Even if you remove the browser extension and the main application, numerous residual files may still linger on your system. For instance, Login items that the virus uses to launch itself each time macOS starts up, and virus-associated profiles that allow it to operate covertly. Therefore, it's crucial to delete these remaining files to fully clean your system.
- Go to Preferences and select Accounts
- Click Login items and delete everything suspicious
- Next, pick System Preferences > Users & Groups
- Find Profiles and remove unwanted profiles from the list
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and delete all the related .plist files.

Finally, clean your browsers from cookies and other web data, as they are commonly used to track users in various ways. To take care of these trackers regularly, you could employ a powerful repair and maintenance utility FortectIntego.
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
