Qepi ransomware (virus) - Free Instructions
Qepi virus Removal Guide
What is Qepi ransomware?
Qepi ransomware is a type of malware that prevents access to all personal files on Windows
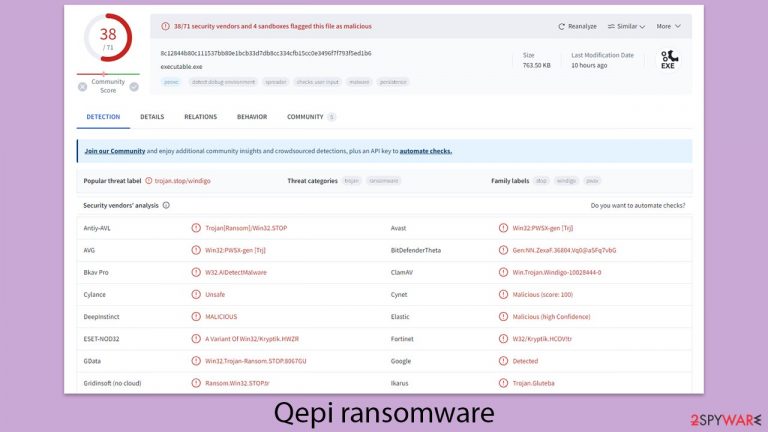
Qepi ransomware is a significant cyber threat due to its potent encryption techniques, known for rendering files completely inaccessible. This virus is part of the Djvu malware family and introduces its own unique extension by appending “.qepi” to the filenames it encrypts, utilizing the robust RSA encryption method. Once it infiltrates a system, it swiftly begins encrypting files, denying users access to their data.
Following the encryption, the malware leaves behind a note titled “readme.txt” in the affected directories. This note outlines the attackers' demands, asking for a ransom of $999 in exchange for a decryption tool that they claim can recover the encrypted files.
In an apparent bid to entice prompt communication, the note also offers a 50% discount, reducing the ransom to $499 if victims make contact within a specified time. The ransom note includes contact details (support@freshingmail.top and datarestorehelpyou@airmail.cc) through two email addresses provided for initiating communication.
This strategy of extortion brings considerable anguish to affected users and signals a troubling trend in cyber threats. For further information on the Qepi ransomware, including advice on removal and data recovery options, further details are provided in the following sections.
| Name | Qepi virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .qepi extension appended to all personal files, rendering them useless |
| Family | Djvu |
| Ransom note | _readme.txt dropped at every location where encrypted files are located |
| Contact | support@freshingmail.top and datarestorehelpyou@airmail.cc |
| File Recovery | There is no guaranteed way to recover locked files without backups. Other options include paying cybercriminals (not recommended, might also lose the paid money), using Emisoft's decryptor (works for a limited number of victims), or using third-party recovery software |
| Malware removal | After disconnecting the computer from the network and the internet, do a complete system scan using the SpyHunter 5Combo Cleaner security app |
| System fix | Upon installation, malware can cause severe damage to system files, resulting in instability issues such as crashes and errors. However, FortectIntego PC repair can automatically fix any such damage |
Ransom note analysis
After the ransomware attack, criminals mostly interact with their victims via a ransom note. This notification is intended to instruct the victim on the payment process required to potentially decode their encrypted data.
The ransom note usually specifies the precise amount of Bitcoin required and gives specific instructions for making the payment. Qepi virus developers attempt to be professional in their communication, creating ransom notes that appear convincing and serious.
This note typically pops up on the victim’s device once the encryption process is complete. It often comes in the form of a text document, although it can also appear as an image or a webpage. The note generally includes comprehensive guidelines on how to proceed with the payment to regain access to the locked files.
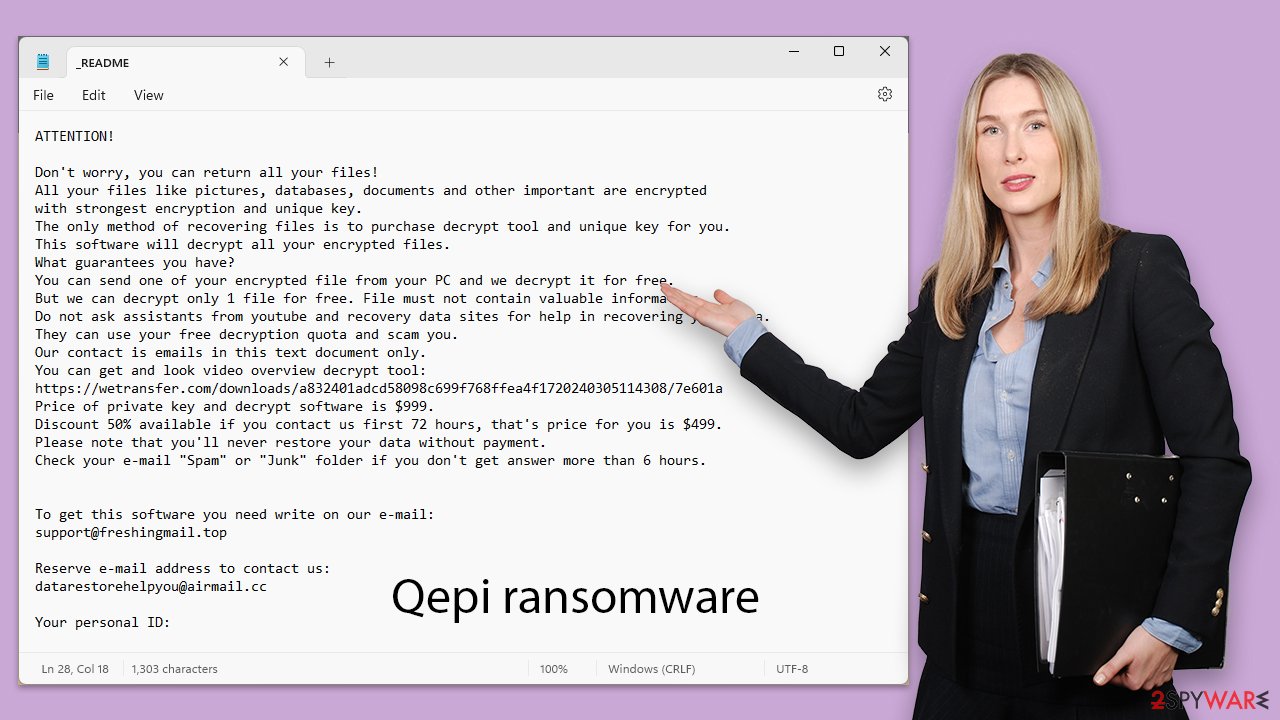
In the case of Qepi ransomware, the note is commonly found in a text document (similar to previous Djvu versions like Baaa or Bgzq) format and states the following:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted
with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
Do not ask assistants from youtube and recovery data sites for help in recovering your data.
They can use your free decryption quota and scam you.
Our contact is emails in this text document only.
You can get and look video overview decrypt tool:
https://wetransfer.com/downloads/a832401adcd58098c699f768ffea4f1720240305114308/7e601a
Price of private key and decrypt software is $999.
Discount 50% available if you contact us first 72 hours, that's price for you is $499.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshingmail.topReserve e-mail address to contact us:
datarestorehelpyou@airmail.ccYour personal ID:
Ransomware attackers frequently use psychological pressure to coerce victims into paying promptly. A frequent tactic employed by those behind Qepi ransomware is to promise a 50% “discount” on the ransom if paid within a specified time window. Sometimes they will supply a sample decryption to demonstrate the feasibility of data recovery.
Despite these potentially appealing offers, cybersecurity professionals and law enforcement strongly advise against paying the ransom. By agreeing, victims unintentionally subsidize additional criminal activity and attacks. Furthermore, there is no guarantee that the attackers will uphold the agreement by giving a valid decryption key, as trustworthiness is not a characteristic of cybercriminals.
How to safely remove the virus
Dealing with a ransomware attack, such as one from Qepi, can be daunting for those unfamiliar with such situations. Making the right moves early on is crucial for improving the chances of recovering your data.
One of the first steps to take is to isolate your computer by disconnecting it from the internet. This action helps prevent the spread of the malware to other devices on the same network and cuts off communication with any external control servers that the malware might use. Here are the steps you should follow to effectively disconnect your device:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If your device has been compromised by Qepi ransomware and is currently offline, you might consider manually removing the malware. However, this is a complex task that typically requires significant IT expertise. Usually, it's safer to use specialized software designed specifically for removing ransomware or to get help from a professional.
Manually removing ransomware can be risky and may cause additional damage if not executed properly. Therefore, it's recommended to conduct a full system scan using dependable security tools like SpyHunter 5Combo Cleaner or Malwarebytes. These programs are effective in detecting and eliminating all traces of the ransomware.
Furthermore, after removing the virus, using a reliable recovery program FortectIntego is highly recommended. This can help resolve any system issues like crashes or errors that might arise post-removal.
Ransomware usually locks files permanently, although there is hope
Handling the ransomware attack can be complex, and there are numerous misconceptions about the mechanisms of data encryption and malware operations. For instance, some believe that simply running a security scan or renaming files might reverse the encryption of files, but this is rarely the case.
The encryption employed by Qepi ransomware utilizes advanced algorithms to create secure cryptographic sequences, which are extremely difficult to crack. Simply removing the malware does not unlock the encrypted files; they remain inaccessible without the unique decryption key held by the attackers.
Qepi ransomware not only locks data but also assigns each encrypted file a unique identifier and complex encryption key, using this structure to demand a ransom and profit from the victim’s urgent need to regain access to their data. This approach makes ransomware a lucrative scheme for cybercriminal groups.
While paying the ransom might seem like the easiest solution, exploring other recovery options is advisable. Always ensure you have a secure backup of your data before attempting any recovery techniques to minimize further data loss.
One potential recovery approach could involve tools like the Emsisoft decryption utility. However, the success of such tools varies depending on the ransomware strain and other factors, so it's crucial to approach recovery with an understanding of these challenges and limitations.
- Download the app from the official Emsisoft website.
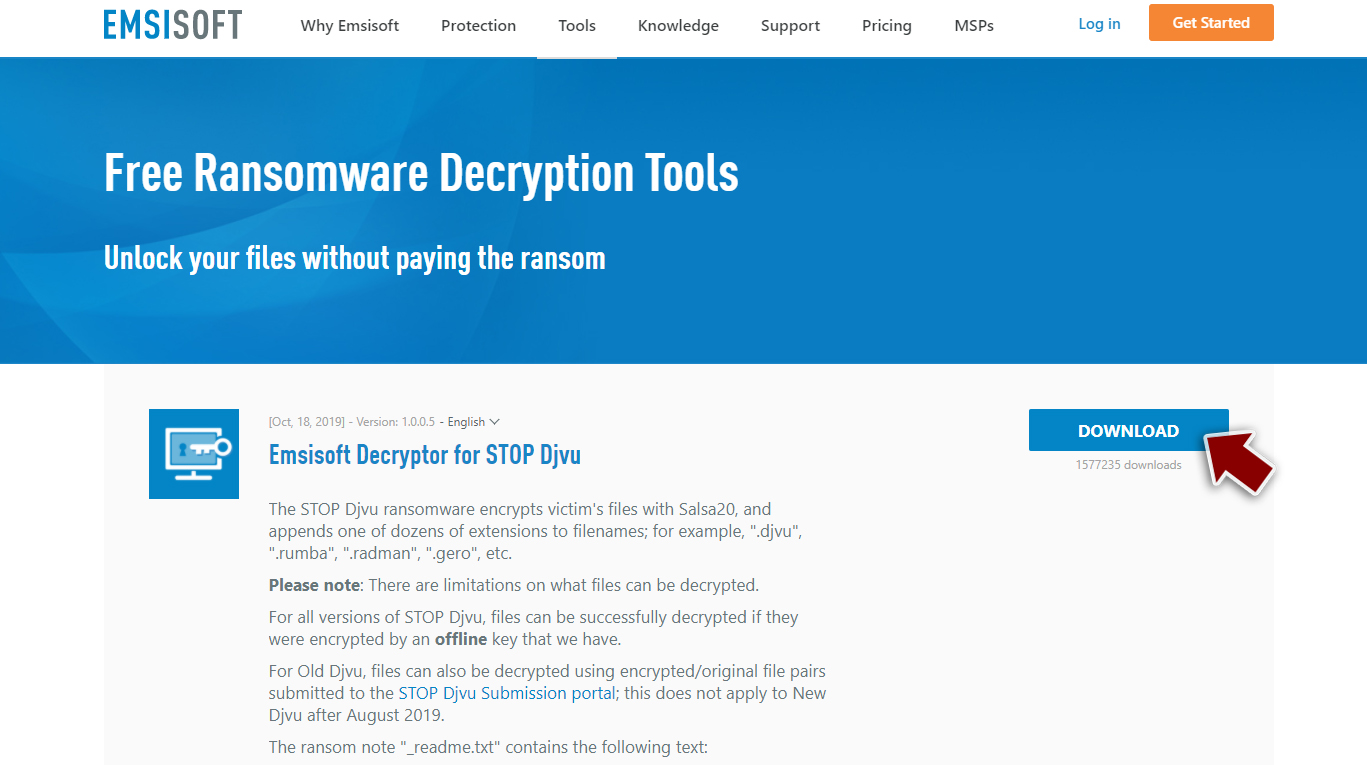
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.

- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.

- Press Decrypt.

From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
If your data was encrypted with an online ID, Emsisoft's tool won't work. In such a case, we recommend trying specialized data recovery software instead.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Another option is to wait for security experts and organizations to come up with a free decryption tool. This usually happens when flaws are found in the encryption code used by the malware or when law enforcement captures the servers operated by the cybercriminals. It's crucial to understand that there is no assured promise of such a solution being available later on. However, we suggest checking the links provided to see if there is a decryptor available for this specific virus.
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Getting rid of Qepi virus. Follow these steps
Restore Windows "hosts" file to its original state
Some ransomware might modify Windows hosts file in order to prevent users from accessing certain websites online. For example, Djvu ransomware variants add dozens of entries containing URLs of security-related websites, such as 2-spyware.com. Each of the entries means that users will not be able to access the listed web addresses and will receive an error instead.
Here's an example of “hosts” file entries that were injected by ransomware:
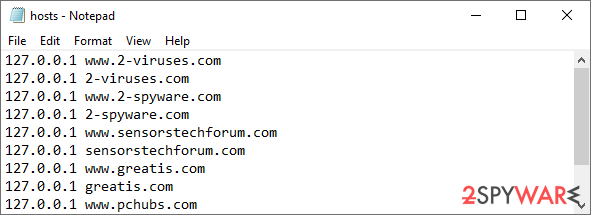
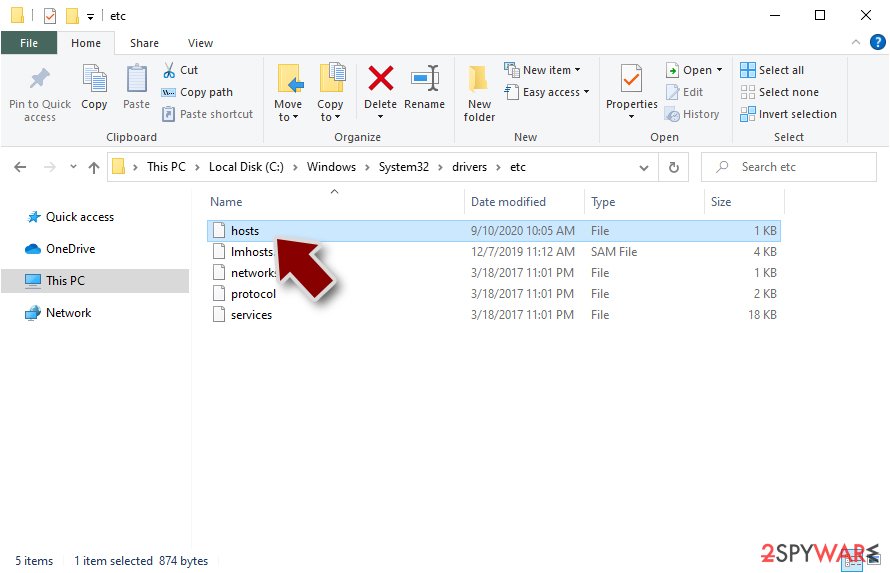
In order to restore your ability to access all websites without restrictions, you should either delete the file (Windows will automatically recreate it) or remove all the malware-created entries. If you have never touched the “hosts” file before, you should simply delete it by marking it and pressing Shift + Del on your keyboard. For that, navigate to the following location:
C:\\Windows\\System32\\drivers\\etc\\
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
