Bitcoin virus. Main types, distribution techniques and removal explained
Bitcoin virus Removal Guide
What is Bitcoin virus?
Bitcoin virus – malware that can use victims' PC resources to mine cryptocurrency for criminals
Bitcoin virus is a type of malicious program that seeks to mine cryptocurrency illegally while using victims' CPU power. In some cases, a graphics processing unit (GPU) can be utilized as well. The virus typically enters machines via a trojan horse – a backdoor virus that clears the path for coin-mining malware.
The extensive usage of computer hardware diminishes the overall performance of the device (eventually it can lead to its destruction), as well as increases the amount of electricity consumed, leading to raised electric bills. Users can detect the malware in the Task Manager as a questionable process running in the background, such as XMRig. The Miner.Bitcoinminer or similarly named infection can infiltrate Windows, Mac, and Android devices.
| Summary | |
| Name | Bitcoin virus |
|---|---|
| Type | Trojan |
| Sub-type | Cryptojacker[1] |
| Versions | CPU Miner, Vnlgp Miner, etc. |
| Currencies mined | Bitcoin, Monero, Electroneum, and others |
| Distribution | Spam emails, fraudulent messages on Skype, EternalBlue exploit, etc. |
| Symptoms | Increased CPU and GPU usage (making the PC hot), software crashes or freezes, slow overall performance of the device |
| Susceptible systems | Windows, Mac, Android |
| Elimination | Download and install an anti-malware tool to remove the virus fully |
| Sistem fix | Using the FortectIntego tool might help to recover the virus damage |
The virus is capable of harvesting various crypto, including Monero, Electroneum, Litecoin, Ethereum, although the most prominent one is Bitcoin. It is a virtual currency that was first introduced in 2008. However, the usage of this digital currency increased only in 2011. At the time of the writing, the cryptocurrency has already reached a circulation rate of more than 17 million as of late May 2018.[2]
There is no surprise that even the most reputable companies accept this currency. However, it is created not through a central monetary agency, but through the computers that perform CPU-intensive crypto calculations. Therefore, cybercriminals are always looking for new ways to take advantage of this feature by creating new versions of cryptominers.
The virus is detected under various names, including:
- Riskware.Miner
- Trojan.BitMine
- W32/CoinMiner
- Trojan.BitMine
- Trojan.BitCoinMiner
- PUA.CoinMiner, etc.
There are several variants of BitcoinMiner, as well. The most known of them are called CPU Miner and Vnlgp Miner. Unfortunately, you can hardly notice when your computer gets infected by it. According to experts, this malware attempts to hide by trying to work only when the victim is not using his/her device.
However, you can notice the virus by monitoring your PC’s speed. According to research, the use of the machine’s CPU grows up rapidly when this virus infiltrates it, so don’t ignore such changes. What is more, the Trojan horse might also be capable of opening the back door or download other malicious programs.
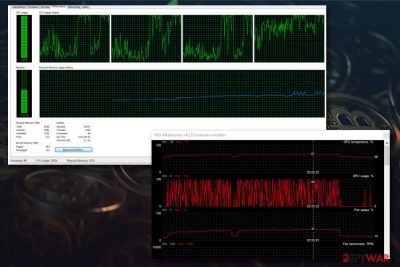
If the GPU of your device is used instead of CPU, you will not be able to spot it in the Task Manager. However, you will be able to see stuttering and freezing frames when performing graphics-intensive tasks, such as gaming or full HD video processing.
Some users may naturally come to the conclusion that their graphics card is about to break. Nevertheless, if you experience such symptoms, you should download software that can measure temperature and workload on your GPU, and check if the infection causes the malfunction.
There are many reasons[3] why your computer might be working slowly – incompatible software or hardware, corrupt system or software files, outdated registry entries, and similar issues. However, it is always worth scanning your machine with reputable anti-virus software first. Malwarebytes, SpyHunter 5Combo Cleaner or similar security software will immediately detect and remove BitcoinMiner from Mac OS X or Windows.
The evolution of the virus: ransomware variant hit the surface
Bitcoin ransomware is a specific version of the cryptocurrency's malware, which can infiltrate a computer without the user’s approval and then encrypt each of his/her files. This threat has been noticed after encrypting the entire network of one medical center in the USA. However, it can also affect regular home users leaving them without access to their files.

Once it finishes the encryption of the victim’s files, the ransomware displays a warning message asking him or her to pay the ransom of 1.5 BTC. Please, do NOT pay it as you may end up with nothing! Keep in mind that you are dealing with scammers who can take money from you and leave you without a special code needed to decrypt your locked files.
In this case, you should perform a virus removal with SpyHunter 5Combo Cleaner Malwarebytes, and try to encrypt your files with the help of these tools: Photorec and R-studio. Keep in mind that dealing with cybercriminals is never an option!
The mining malware has been noticed spreading in Russia
At the end of July 2017, it was reported that cryptocurrency mining malware infected 25% of computer users in Russia. [4] However, some sources state that this cyber infection may have infiltrated 30% of Russian computers.[5]
According to the official data, the majority of affected devices run in Windows OS. Meanwhile, Mac computers and iPhones haven’t suffered a lot from the virus.
Authorities published the information about Bitcoin mining virus[6]. However, security specialists and antivirus vendors claim that the scope of the attack is exaggerated.[7] Experts agree that in the past there were few issues with this malware, but not as vast as it is has been stated recently.

A representative from Kaspersky Labs, which is one of the leading Russian antivirus vendors, claims that if such a massive attack were held, they would have noticed it. However, since the beginning of the year, only 6% of their customers have suffered from infection.[8]
How this malware can infect your device
According to security experts, this virus is mostly spread via Skype network, but it has also been noticed on other social networks, so beware of that. Typically, this virus relies on a spam message, which claims something like „this my favorite picture of you” and includes a malicious file.
Of course, the virus seeks to convince its victims to download the file onto their computers. Certain versions of the malware were also seen being spread using the EternalBlue exploit. If you want to avoid it, stay away from such messages.
Once the victim downloads the “photo,” he not only lets malicious pieces inside the machine but allows the virus to connect the PC to its command-and-control server. When it's inside and active, the virus turns the infected machine into the Bitcoin generator. However, it can also be designed to the virus, which steals banking details, records the keystrokes, or downloads more malware on its target PC.
Bitcoin virus removal guide
If you think that your computer is infected with malware, you should scan it with updated security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. If your device is affected, your chosen security tool will remove Bitcoin virus immediately.
Make sure you check the system immediately after noticing changes in your computer’s speed because it is the only way to get rid of this threat without additional problems. The appearance of other viruses and the loss of your sensitive information can be expected when having the virus on a computer.

These programs should also help you perform Bitcoin virus removal from the system. However, sometimes viruses that are categorized as ransomware block anti-virus software to prevent their removal. If you are dealing with such a problem right now, follow the guide below.
Getting rid of Bitcoin virus. Follow these steps
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Bitcoin and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ What is cryptojacking?. Hacker bits. Monthly tech magazine.
- ^ Bitcoins in circulation. Blockchain. Bitcoin wallet and Bitcoin statistics.
- ^ Natasha Stokes. 14 Reasons Why Your Computer is Slow. Techlicious. Tech website.
- ^ A Strange Bitcoin-Mining Virus is Sweeping all over Russia. SPAMfighter. The global provider of state-of-the-art computer, mobile and server utility and security products.
- ^ William Suberg. Bitcoin Virus ‘Has Infected 30% Of Russian Devices’: Putin Advisor. Cointelegraph . Bitcoin & Ethereum news, analysis and review about technology, finance and markets - Future of Money and FinTech news.
- ^ Bedynet. Bedynet. Russian website about computer viruses.
- ^ Karan Kapoor. Russia Allegedly under Attack By 'Most Dangerous' Malware That Mines Bitcoin https://bitcoinist.com/russia-allegedly-attack-dangerous-malware-mines-bitcoin/. Bitcoinist. News portal providing breaking news about decentralized digital money, blockchain technology and Fintech.
- ^ Diana Ugay. Trojan Bitcoin Miner affects 6% of Russian users. Hype.Codes. Programming Technologies News and Reviews.


















