Findzip ransomware / virus (Bonus: Decryption Steps) - Virus Removal Guide
Findzip virus Removal Guide
What is Findzip ransomware virus?
Files encrypted by Findzip ransomware virus might be decrypted
Findzip ransomware (also known as Filecoder or Patcher ransomware virus) is a file-encrypting virus that targets Mac users. When it was first discovered on February 22, 2017[1], it seemed that victims do not have any possibility to decrypt their files if they do not have data backups. This assumption was made because the virus does not communicate with its Command and Control server. That means that even if a victim decides to pay the ransom, hackers have no ability to decrypt the files. Therefore, victims were just suggested to remove Findzip from the system and forget about their files. However, recently researchers found another flaw in the virus code and revealed data recovery option[2]. Nevertheless, this procedure is complicated and difficult victims, putting some effort and getting back encrypted files is worth it. What is more, malware researchers also find out that virus behaves quite oddly. Usually, ransomware viruses launch whenever a victim turns on an affected computer, but not this one. When Findzip virus is executed and activated on particular User folder and finishes its task, it will never run again.
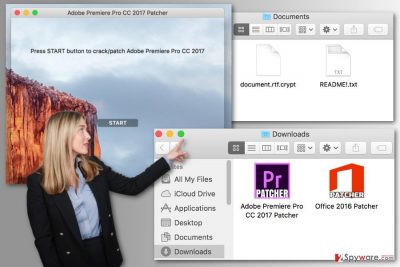
The ransomware spreads via infected or Torrent site as Adobe Premier Pro and Microsoft Office cracks. However, there are other assumptions that malware might be hidden in other programs as well. When people, who are interested in getting the illegal software, downloads and runs the installer, they receive and unusual transparent window with malicious “start” button. Clicking on this button executes Findzip ransomware. The virus immediately starts encryption procedure. Meanwhile, victims receive a window asking to wait up to 10 minutes while the program patching is over. For data encryption, ransomware protects targeted files with the string of randomly generated 25 characters and appended .crypt file extension. The virus creates encrypted .zip files that have the same passcode. When data encryption is over, Findzip virus drops ransom notes on the desktop called README, DECRYPT, and HOW_TO_DECRYPT. All these documents include the same information and informs that victim’s files have been protected by a strong encryption method. Developers demand to transfer 0.25 Bitcoins within one week time in order to get back the files. Though, paying the ransom is not enough. Victims also have to send their bitcoin address and IP to rihofoj@mailinator.com, and then leave their computer turned on and connected to the Internet for the 24 hours. However, as we mentioned at the beginning, the hackers cannot help to decrypt the files no matter how much money you are willing to pay[3]. That’s why it’s important to focus on the Findzip removal and complete it with FortectIntego or other reputable anti-malware software. If you do not have data backups[4], there’s also a way to restore your files.
How can I get infected with ransomware?
Findzip ransomware virus spread as a bogus Adobe Premier Pro and Microsoft Office patchers that can be download from the malicious websites or Torrents. Hence, the only people who risk getting infected with ransomware are those who are willing to download illegal software[5]. Otherwise, there’s no need to be afraid of the ransomware. Bear in mind that the only safe and legal sources are official developers websites. Thus, trying to save some money and avoiding paying for the license might cause you serious problems.
How to remove Findzip from the Mac?
Trying to remove Findzip manually is not recommended. Ransomware viruses are complicated and might be hiding deeply in the system and looking like safe system files. Therefore, it’s easy to delete the wrong file and cause more damage. The only safe and effective way to remove malware from the system is to install reputable malware removal program and perform the automatic Findzip removal. We highly recommend using updated FortectIntego or SpyHunter 5Combo Cleaner for this task. If you do not have data backups, you can try to restore files using R-Studio or Data Rescue tools. However, we suggest trying recently discovered data recovery solution that is presented below. What is more, if virus for some reason managed to infect Windows computer, follow the removal instructions presented at the end of the article.
How to decrypt files encrypted by Findzip ransomware virus?
Malware researchers from Malwarebytes have recently discovered the way to decrypt files encrypted by Findzip. In order to start the procedure, you will need another computer. The instructions below are prepared based on the assumption that you are using another Mac. Also, you can try to use other user’s account on the Mac or your own, if you had force-quit the ransomware and stopped it from encrypting the whole account.
1. Download Apple’s Xcode development environment or TextWrangler text editor.
2. Install the Xcode command-line tools. If you do not have this tools already installed, go to Applications -> Utilities folder -> Terminal app. When in Terminal, enter this command:
xcode-select —install
In the appeared window you will be asked whether you want to install command line developer tools. Select “Install,” and follow the installation wizard.
3. Download pkrack source code.
4. Make sure you have a matching pair of encrypted and safe files. If you have no idea where to get the safe copy of the file, check your email and look for recently sent files.
However, if you cannot find any copy, you can try to run the virus against itself and get necessary of the file. Be careful not to run this app!
- Control-click the malicious Findzip app and chose “Show Package Contents.”
- In the opened window you will see “Contents” folder.
- Inside the folder look for the Info.plist file and copy it.
- On the encrypted system, find the same app and follow the same steps. However, this time you should look up for the Info.plist.crypt file. Copy it.
That’s it. Now you have a necessary pair of files.
5. Before using pkrack, you have to compile it from the source code. The necessary files are in the src directory; however, Mac OS does not allow to access it. For that, you will need to use Xcode or TextWrangler.
- Open the file name “Makefile” and find this line
CFLAGS=-O6 -Wall
and change it to:
CFLAGS=-O2 -Wall
Save and close the file.
- Open the exfunc.c file, find and delete this line:
#include
Save and close the file.
- Remove the same line from these files, and don’t forget to save them:
extract.c
main.c
readhead.c
zipdecrypt.c
7. Open the Terminal app (Applications -> Utilities -> Terminal) and type this command, but do not press return:
cd
Make sure that there’s a space between “cd.”
8. Drag the src folder from the pkcrack-1.2.2 folder onto the Terminal window.
9. Switch back to the Terminal and press return.
10. Enter this command:
make
You will see the code, but do not worry about it.
12. In the src folder you should now see these files (they are known as Unix executables or binaries):
extract
findkey
makekey
pkcrack
zipdecrypt
Move them to another folder, for instance, bin.
13. Now you need to use the pair of encrypted and unencrypted files. Move these files to the same (bin) folder where you dropped pkrack binaries. Then, rename an original (unencrypted) file (e.g. Info_orig.plist)
14. In Terminal, use the “cd” command to change to the bin directory, and type this command:
./extract -p Info.plist.crypt Info.plist
Rename produced Info.plist file, for instance, to Info_enc.plist.
Note. If you are using your files, you should rename them to your preferred names. We just give an example. If your filenames have spaces, enclose them in quotes:
./extract -p “Some Word file.docx.crypt” “Some Word file.docx”
15. Search for the keys by entering this command:
./pkcrack -c Info_enc.plist -p Info_orig.plist
16. Now pckrack should start working with the encrypted file and trying to find the passcode. You will be notified about the completed task after the two beeps. The terminal will provide you the information, where you will also find three keys (key0, key1, key2) that are necessary for data encryption.
Note. You can force-quit pkrack’s attempts to find the passcode by pressing control-C.
17. Start data encryption by entering this command:
./zipdecrypt c054acf9 d1656d7b 3549626f Info.plist.crypt Info.plist.zip
However, you should replace these keys with the obtained ones.
18. This program is supposed to generate a new Info.plist.zip file, and you just have to unzip it. There you will find lots folders. Check all of them to find decrypted file.
Getting rid of Findzip virus. Follow these steps
Manual removal using Safe Mode
If ransomware managed to get inside Windows OS, follow these steps to reboot your PC to the Safe Mode. This mode might be necessary to install malware removal program, such as FortectIntego, to start automatic virus removal.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Findzip using System Restore
If Safe Mode method did not help to install malware removal tool, follow these steps. Then, try to install, update and run full system scan with your chosen security tool.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Findzip. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Findzip from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Findzip, you can use several methods to restore them:
Try Data Recovery Pro to decrypt files encrypted by Findzip ransomware virus
Data Recovery Pro is a professional tool that helps to restore damaged, corrupted and encrypted files. Follow these steps:
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Findzip ransomware;
- Restore them.
Windows Previous Versions feature to restore files encrypted by Findzip ransomware
If System Restore function has been enabled before ransomware attack, follow these steps to recover at least some of the files:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Use ShadowExplorer to restore files encrypted by Findzip virus
If malware did not delete Shadow Volume Copies of the targeted files, ShadowExplorer may help to restore encrypted data:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Findzip decryption software
Unfortunately, there’s any specific software that can help to decrypt files encrypted by Findzip.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Findzip and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Marc-Etienne M.Léveillé. New crypto-ransomware hits macOS. WeLiveSecurity. News, views, and insight from ESET security community.
- ^ Thomas Reed. Decrypting after a Findzip ransomware infection. Malwarebytes Labs. The official blog by Malwarebytes.
- ^ Aj Dellinger. Mac Ransomware: New 'Patcher' Attack Won't Decrypt User Files Even After Ransom Is Paid. International Business Times. Business News, Technology, Politics.
- ^ Nat Maple. Why backing up your data is more important than ever before. TechRadar. The latest technology news and reviews, covering computing, home entertainment systems, gadgets and more.
- ^ Simon Crowfoot. The Dangers of Downloading Illegal Software. ICENI Technology Blog. All about PDF Editors, PDF Editing and Office Productivity.





















