MacRansom ransomware / virus (Virus Removal Instructions) - Decryption Methods Included
MacRansom virus Removal Guide
What is MacRansom ransomware virus?
MacRansom virus might be the first Ransomware-as-a-Service that targets Mac OS
MacRansom is a malicious Ransomware-as-a-Service[1] virus that targets Mac operating systems and encrypts files stored in them. The developer of the ransomware suggests joining his affiliate system for free and provides ransomware samples for free. It takes less than a minute for this virus to encrypt files on victim’s Mac. After encrypting the files, the virus creates a ransom note (._README_ file) that it displays on the screen, and demands 0.25 Bitcoin (approximately $700). The victims are asked to contact getwindows@protonmail.com for information on how to decrypt files. Instead of doing so, we suggest you start thinking about MacRansom removal. 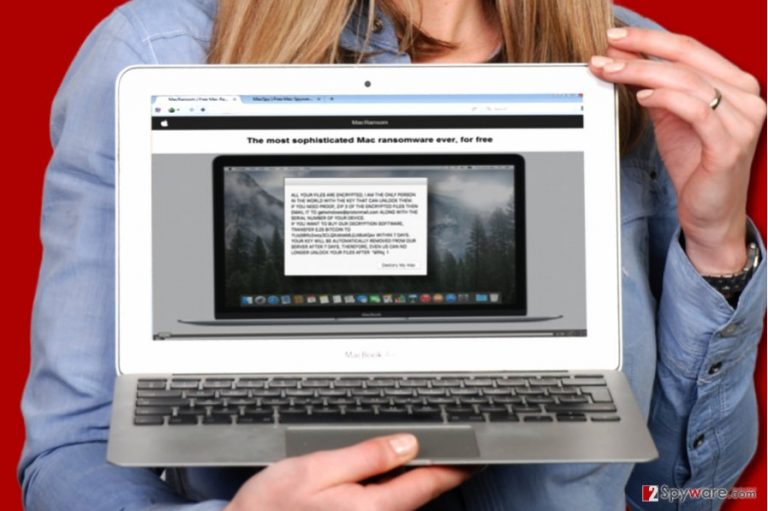
Before launching the malicious payload, the ransomware performs several checks – it determines whether it is being run in a Mac environment or not, also if it is being debugged, and if the machine has two CPUs. Following that, the virus creates a launch point: ~/LaunchAgent/com.apple.finder.plist and then copies the ransomware executable to ~/Library/.FS_Store. The virus purposely uses original (or similar) names of legitimate files to avoid detection. The virus also manipulates the time date stamp to confuse investigators. Finally, the virus uses launchctl to open the com.apple.finder.plist file it created. The virus checks trigger time and, if the condition is met, it starts the encryption process. After encrypting all of the victim’s files, the ransomware encodes its own files, changes the time date stamp and then removes them from the system.
The ransomware uses symmetric encryption, which, in typical cases, allows decrypting files more easily, however, we do not recommend paying the ransom if your PC has been infected. It turns out that the ransomware doesn’t communicate with C&C server[2], and that means criminals won’t have the copy of it. However, since they key is only 8 bytes long, it might be possible to brute-force it. So if you have been assaulted by this Mac ransomware, we suggest you remove MacRansom from the OS using Malwarebytes software and check available data decryption methods explained at the end of this post.
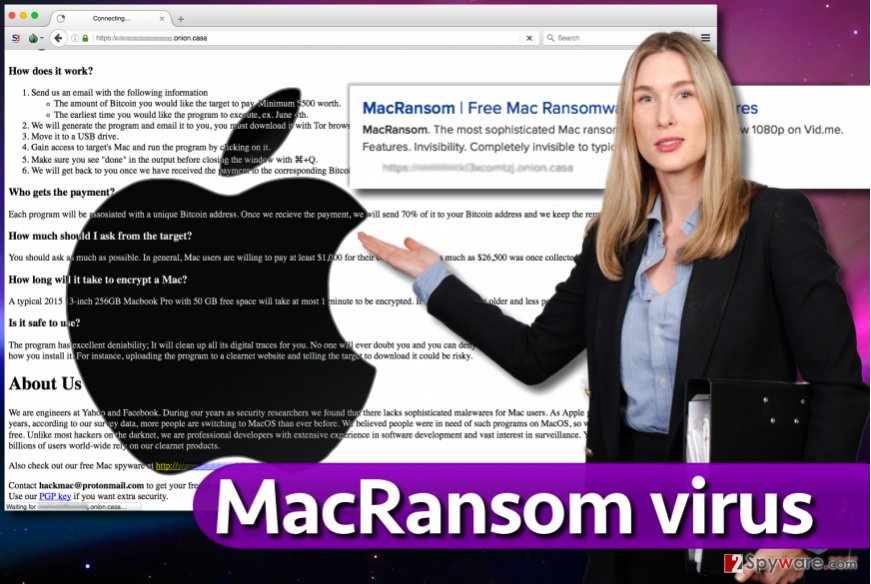
Distribution methods
Ransomware-as-a-Service is distributed by affiliates who decide to partner with the ransomware developer. Currently, it is being distributed via email spam, although we believe that attackers might be trying to inject the virus into unsecured websites or distribute it alongside untrustworthy or illegal software for Macs. The developer of MacRansom, however, suggests moving the malicious virus to a USB, using it to transfer the malicious file on a target system, and manually launching it. It goes without saying that it is a much slower and more dangerous way to distribute this malicious virus. The ransomware developers promise to give their affiliates 70% from all collected ransoms, keeping 30% to themselves.
Remove MacRansom from Mac OS
If you want to continue using your Mac, we highly recommend you to remove MacRansom virus remains using powerful malware removal tool. You must use software that is compatible with Macs. Our suggestion is to use Malwarebytes software. Do not delay MacRansom removal and delete it as soon as you can because keeping the malware on your system poses a threat to your privacy and opens security vulnerabilities that can be exploited by other malicious actors. Once you run the anti-malware program and let it delete malicious files for you, use the given guidelines to decrypt your data.
Getting rid of MacRansom virus. Follow these steps
Bonus: Recover your data
Guide which is presented above is supposed to help you remove MacRansom from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.To recover your data, please be patient – ransomware analysts are about to release MacRansom decryption tools shortly. In the meantime, you can restore part of your files from data backup. Before importing any external files, remove the malware using anti-malware software that is compatible with Mac OS.
If your files are encrypted by MacRansom, you can use several methods to restore them:
MacRansom decrypter isn't available yet
However, it doesn't mean that you should pay the ransom. It is unlikely that scammers will help you to restore encrypted files anyway.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from MacRansom and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Christopher Budd. Outsourcing crime: How Ransomware-as-a-Service works. Trend Micro Blogs. Simply Security News, Views and Opinions.
- ^ Command-and-control (C&C) server. Trend Micro USA. Threat Definitions.
