NMoreira ransomware removal and data recovery steps
NMoreira virus Removal Guide
What is NMoreira ransomware virus?
NMoreira ransomware – dangerous file-encrypting malware which replaces the boot section with its own text
NMoreira ransomware is a file-encrypting and ransom-demanding threat that replaces the boot section with its own text and appears to encrypt partitions in the hard disk. This type of information comes from the latest update which has been posted by a virus researcher Dave Logue on Twitter.[1] NMoreira virus has first been spotted at the end of 2016 and released a new variant (NMoreira 2.0) in 2017. Furthermore, this notorious malware has collected other names also, some people know it as XPan and XRatTeam virus. The most affected users are considered people residing in Portugal and English-speaking countries as the ransomware displays messages in these types of languages. Typically, this ransomware appends .maktub, .__AiraCropEncrypted!, .m4ktub or____xratteamLucked extension to each of affected files.
NMoreira ransomware displays the Portuguese-based ransom note named Recupere seus arquivos. Leia-me!.txt which provides the contatomaktub@email.tg email address for ransom price discussing purposes. Furthermore, this virus also displays a Recovers your files.html message which is all written in English. It announces that files have been locked with the help of AES-256 and RSA-2048 encryption ciphers and provides two links one of which needs to be accessed to continue with the payment process.
| Name | NMoreira |
|---|---|
| Type | Ransomware |
| Also known as | XPan, XRatTeam |
| Extension | .maktub |
| Encryption used | AES-256 and RSA-2048 |
| Main targets | Portugal and English-speaking countries |
| Other versions | NMoreira 2.0 |
| Similar to | AiraCrop |
| Programming language | C++ |
| Unique activity | Boots its on text while rebooting the PC |
| Distribution | Email spam, P2P sites |
| Malware detection | FortectIntego can help you with malicious content detection |
If you decide to click on one of the hyperlinks that are provided by NMoreira ransomware, you will land on a dark web-based[2] website where you will be asked to make a donation of 3 BTC and offered to send three files no bigger than 2 MB for free decryption. The other link will also take you to a .onion website where you will see this email address provided: 6699nm@protonmail.com that is also given for considering file decrypting purposes.
The criminals who promote NMoreira ransomware threaten victims that encrypted files can only be recovered with their software and other products are not an option. Gladly, you do not have to consider the option of paying Bitcoins to these people as Emsisoft cybersecurity organization has released a decryptor for .maktub files about a couple of years ago.
What is very interesting, NMoreira ransomware seems to be identical to another file-encrypting threat, known as AiraCrop and include some relations with TeamXRat cyber campaign.[3] When it comes to ransomware, the identity of its developers often remains in secret. Nonetheless, certain peculiarities help guess the nationality of the cybercriminals.
In the case of this ransomware, IT experts speculate that this virus is the creation of Brazilian hackers who specialize in banking trojans. Interestingly, there have been a couple of file-encrypting malware created by these crooks, for example, TorLocker. Therefore, they decided to advance to the new level by combining their knowledge and experience and launch the ultimate virus.
Luckily, it is not that hard to remove NMoreira virus if you opt for the automatic solution. However, file decryption is another matter. Since the virus is not an ordinary computer pest, recovering the files might be a complicated task. In this regard, you may also find some recommendations on how to retrieve the data below the article.
The elimination should not be postponed as the ransomware virus has been spotted traveling via a trojan [4], so the entire NMoreira removal process should not be delayed. Malicious elements might accelerate the further infection of the operating system. While you are reading, launch FortectIntego to start the malware-detecting process.
What is more, NMoreira ransomware has been written in C++ programming language.[5] Unfortunately, the virus targets a wide range of files, including .doc, .zip, .rar, .jpeg, etc. It only avoids affecting .exe, and .dll files. After the successful infiltration, the virus appends its extensions at the beginning of the files and starts showing its ransom note which is displayed below:
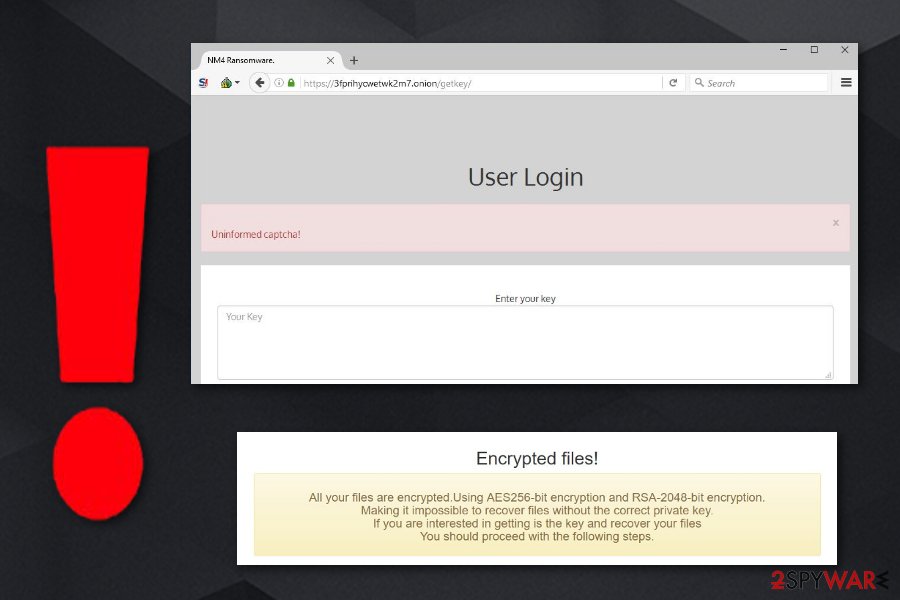
Encrypted Files!
All your files are encrypted. Using encryption AES256-bit and RSA-2048-bit.
Making it impossible to recover the files without the correct private key.
If you are interested in getting is key, and retrieve your filesFor information on how to reverse the file encryption
send email to:
XXXXXXXXX
enter your KEY in the subject or email body.=======================================================
Remember your email is not answered within 24 hours,
visit one of the link below to get a new mail contact
https://
https://
https://
[….]
Interestingly, the former version, with the three characters, encrypts the files with a single 255-symbol password, while the latter variant creates a distinctive password for each file. Later on, it is encoded with RSA-2048 key[6] and inserted in the ransom instructions. Even though that the key might be located, it does not help to decrypt the files easily. In any case, we do not recommend paying the money and addressing the crooks via xRatTeam@mail2tor.com.
Update January 2017: Nmoreira 2.0 version emerges
In response to the released decryption software by the “good guys,” the creators of this threat uploaded to new improved versions of the threat. Nmoreira 2.0 virus is a slightly modified copy of the initial virus' version, however, it goes without saying that this one is a more sophisticated one. NMoreira 2.0 ransomware sticks to using the same ransom message (Recupere seus arquivos.Leia-me!.txt).
There are slight modifications in the file extension. In comparison with the previous edition, now the malware attaches .m4ktub file extension. NMoreira 2 virus keeps spreading via trojans. Surprisingly, that well-known security applications do not have updated virus databases which results in overlooking the infection. On the contrary, less known products were able to detect the ransomware in its disguise as a trojan.
It was spotted as FileCryptor.NDJ, Win32/Filecoder.XRatLocker.B, and Trojan.Win32.Generic. Besides visible modifications, it also contains key internal changes. The virus starts multiple tasks and functions at the same time covering its tracks. Improved Nmoreira malware also meddles with important registry changes.
In addition, the ransomware gets access to personal data and technical information containing specifications about the device and the user. One of the most destructive features has been spotted as the ability to access administrative rights and delete critical files.
Ransomware spreading tactics and how to decrease the risk of malware infections
According to Virusai.lt experts,[7] secret installation of a ransomware virus might have happened during your stay in suspicious domains such as P2P file sharing websites or gambling web pages. A piece of advice would be to keep a distance from all secondary networks and get a reliable antimalware tool that includes safe browsing and protects you during your work.
These domains may also disguise exploit kits [8]. Gaming web pages also happen to be the frequent haven for a variety of virtual threats. Keep in mind that some perpetrators might infect outdated applications, forge their ratings, and then distribute them online. In this case, check the original publisher of the program and try to find out certain information about the original application to distinguish the hoax from the original version.
Continuously, ransomware and other types of malware (e.g. trojans) are spread via dubious email attachments. Criminals who try to distribute malicious payload via legitimate-looking emails tend to drop messages to peoples inboxes pretending to be from various reputable organizations (healthcare, airlines, etc.). You should always manage your email carefully and overthink all possibilities before opening a letter you were not expecting to receive.
NMoreira removal instructions and decryption solutions
You can remove NMoreira virus with the help of an anti-spyware tool, also, use programs such as FortectIntego or Malwarebytes for scanning the entire system and checking it for outdated registry entries and other locations that can include malware. After the process is complete, you can check our data recovery options provided in “Data Recovery” section. In relation to this, there are a couple of programs which might be able to help you retrieve your valuable files and any other information.
If by any chance, you encounter difficulties in NMoreira removal process (the ransomware can try to block programs given above), you can use the below-displayed guidelines to regain full control of the device. On the final note, cautiousness still remains to be of key importance while escaping cyber threats [9].
Getting rid of NMoreira virus. Follow these steps
Remove NMoreira using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of NMoreira. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove NMoreira from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by NMoreira ransomware, you should use optional methods that are given below to recover the access to them. Fortunately, security experts have just presented NMoreira decrypter that you can use as well.
If your files are encrypted by NMoreira, you can use several methods to restore them:
Use Data Recovery Pro to recover your files encrypted by NMoreira ransomware
File encrypted by NMorera could be restored with the help of Data Recovery Pro software. You ned to download this program, install it on your computer and follow the wizard to recover at least some of your files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by NMoreira ransomware;
- Restore them.
Retrieve your files using Windows Previous Versions feature
Windows Previous Versions feature is another solution to solve your problem. There is a chance that you might retrieve the previously saved copies of your valuable data. Keep in mind that this functionality only works when System Restore function is activated.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Using ShadowExplorer when infected with NMoreira
This utility succeeds recreating the files only in that case if the malware does not delete the copies in advance.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Use NMoreira decrypter to release your files
Recently, security experts from Emsisoft Company presented NMoreira decryptor. You can download it from here.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from NMoreira and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ David Logue. David Logue. Status. Twitter. Social Network.
- ^ Daren Guccione. What is the dark web? How to access it and what you'll find. CSO Online. Articles.
- ^ Daniel Stoyanov. Brazilian Ransomware Gang Targets Hospital. Virus Guides. Powered by Knowledge .
- ^ Danny Palmer. Trojan malware blamed for cyberattack at Barts Health NHS hospitals. ZDNet. Technology News, Analysis, Comments, and Product Reviews for IT professionals .
- ^ C++ Programming Language. Techopedia. Tech terms and definitions.
- ^ What is RSA-2048? How can I deal with it?. Quora.com. Relevant questions and answers.
- ^ Virusai.lt. Virusai. Security and spyware news.
- ^ Darren Pauli. Sundown exploit kit weaves Edge hack hole. The Register. Bitting the hand that feeds IT.
- ^ Doug Olenick. Ransomware decryptors and blockers not always a help to victims. SC Magazine. The cybersecurity source .







