Sharebutton.to referral spam (Tutorial) - Free Guide
Sharebutton.to referral spam Removal Guide
What is Sharebutton.to referral spam?
What should you know about Sharebutton.to referral spam?
Sharebutton.to referral spam was one of the first examples of Ghost Spam[1]. Many website owners and webmasters have seen this troublesome domain in Google Analytics[2]. It’s still one of the most popular and active types of spam that mess up with website’s statistics. This technique allows spammers to advertise promotional websites by repeatedly sending fake visits to Google Analytics. When spammer’s URL appears in the statistics, the owner is encouraged to visit it. However, visiting these promotional sites might end up pretty bad. You might be redirected to a phishing[3] or infected website. For this reason, you should learn to recognize the Sharebutton.to referral spam examples. The spam attack might be held in different forms and names. Though, the names of the spam URL address often has words -free, -floating, – social, -share, -traffic or -button. Nevertheless, the names of the address may differ, they still redirect to the main Sharebutton.to website. This simply designed site offers to add codes that are supposed to add social buttons and help to drive traffic to your website. Even though free methods to boost traffic may look like a great opportunity, using them is not recommended. The biggest danger of these scripts is that they may hide malicious code[4]. Once you add them to your site, you may install malware as well. Hence, if you already did it, delete this script immediately and check whether your website was infected or not.
Sharebutton.to referral spam does not cause damage to your website, it’s ranking on Google or popularity, and does not expose it to any security issues (unless you add the previously mentioned code). This spam tool only causes chaos in the Analytics, and only the site owner or webmaster can see this issue. However, there’s no need to ignore the spam attack because sooner or later it might be hard to analyze it. It’s important to block Sharebutton.to referral spam immediately. Referral spam messes up with the statistical data, and it may become hard to understand users’ behavior, what is the best for your customers, clients or advertisers.
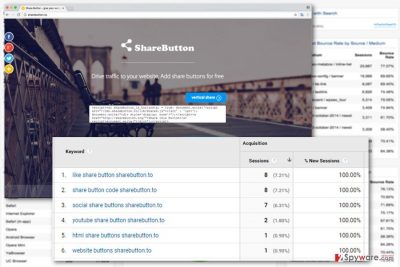
Why was my Google Analytics attacked?
Usually, the main purpose of the referral spam is to boost traffic to the particular websites. Most of the time spammers attack website’s data to make webmaster to visit promoted website or look information about it on Google. What is more, this activity also helps these websites to rank higher in the Google Search results and acquire backlinks. However, in some cases, spammers attack Analytics to redirect webmaster to the affiliate websites and get commissions[5]. Even though this activity is not dangerous, you should not let spammers mess up with your statistics. Once you have noticed Sharebutton.to referral spam in the Analytics, follow the steps below and block this annoying activity.
How to block Sharebutton.to referral spam?
Real statistical data is important to each website owner. It helps to plan the content and achieve better results, increase sales, etc. There’s no doubt that referral spam distorts them. Fortunately, you can easily block Sharebutton.to referral spam and see real statistics again.
Method 1. Create a new filter in Google Analytics:
- In your Google Analytics account go to Admin section -> All Filters -> Add Filter.
- In the Filter Name value add Sharebutton.to.
- Choose Custom Filter Type.
- Open Filter Field drop down menu and choose Campaign Source.
- In the Filter Pattern box, type Sharebutton.to.
- Select Views to Apply Filter.
- Click Save.
Method 2. Block Sharebutton.to referral spam from your server
First of all, access .htaccess file:
- Login to the CPanel account.
- Go to File Manager -> click the check-box Document Root for -> your website. Also, select Show Hidden Files and click Go.
- Once you find the .htaccess file, right-click on it and choose Code edit.
- Copy and paste this code and select Save Changes:
RewriteEngine on
RewriteCond %{HTTP_REFERER} ^http://.*sharebutton \.to/ [NC,OR]
RewriteCond %{HTTP_REFERER} ^http://.*sharebutton \-for\-website\.to/ [NC,OR]
RewriteRule ^(.*)$ – [F,L]
How to prevent from getting spam tools
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Ghost Spam . Web Analytics Consulting, Web Analytics Assessments, Web Analytics Training and Analytics Audits.
- ^ Jonathan Hochman. New wave of referrer spam wrecking Google Analytics data. MarketingLand. Digital Marketing .
- ^ What is phishing?. Phishtank. Clearing house for information on phishing sites reported by the public plus an open API to integrate the data into anti-phishing applications.
- ^ Josep Albors. Clearing house for information on phishing sites reported by the public plus an open API to integrate the data into anti-phishing applications. WeLiveSecurity. News, views, and insight from the ESET security community.
- ^ Affiliate marketing. Wikipedia. The Free Encyclopedia.
