TrickBot virus (Virus Removal Instructions) - Jul 2020 update
TrickBot virus Removal Guide
What is TrickBot virus?
TrickBot – a modular banking malware employed by criminals in different campaigns to steal sensitive data

TrickBot is a financial Trojan first discovered in 2016 and targeted customers of leading banks in the UK, US, Australia, and other countries. The virus is well-known for its ability to mimic online banking windows and steal personal information, such as log-in names and passwords, with the help of the post-exploitation tool Mimikatz. It is also capable of stealing information from Bitcoin wallets, acquiring access to email accounts and stealing network/system data to proliferate laterally. Additionally, the compromised system might start sending spam emails boobytrapped with Trickbot's payload.
Analysts revealed that this malicious program was invented and released to the cyberspace after cybercriminals noticed the significant success of Dyre trojan[1], and began using it as malware-as-a-service.TrickBot was actively performing attacks on CRMs (Customer relationship management) and Payment Processors, and over the years, has seen a variety of malspam campaigns.[2] In 2019, malware managed to hijack 250 million email accounts to increase its operations.[3] During the coronavirus pandemic, cybercriminals behind Trick bot virus employed medical advice and testing lures to make users click on attachments and execute malicious macro commands.[4]
| Summary | |
| Name | TrickBot |
| Also known as | Trojan.Trickbot.e, Trojan.Trickbot, Trojan:W32/Trickbot, and many others |
| Type | Banking Trojan |
| Distribution | Malspam, botnets |
| Operation principle | Malware-as-a-Service (MaaS) |
| Symptoms | Some users might experience increased CPU usage, inability to access certain websites, slowdown in computer response, errors, crashes, and similar. However, Trojans rarely exhibit any symptoms |
| Functionality |
TrickBot possesses a wide array of capabilities:
|
| Danger level | High. While the infection of malware remains the biggest threat to corporation networks and businesses, regular computer users can be victims as well |
| Associated risks | Companies and consumers might suffer significant financial losses, sensitive data compromise, identity theft, customer data exposure, and other devastating ramifications |
| Programming language | C++ |
| First appearance | August 2016 |
| Elimination | To get rid of malware, a network-wide scan with anti-malware should be initiated. In some cases, Safe Mode access might be needed – we provide the instructions below |
| System fix | Virus damage and system remediation can be performed with the help of FortectIntego |
Analysis revealed that this banking Trojan employs similar encryption techniques and hijack strategies as Dyre (alternatively known as Dyreza). Malware can bypass some security applications and infiltrates the system when users click on the malicious link or download a fake program.
After the invasion, TrickBot injects its malicious scripts and codes into banking websites. In other words, the cyber threat switches the original version of the site with its malignant substitute. In order to enforce this technique, C encryption language is used. In this regard, the newly detected Trick Bot malware also uses the improved version of the algorithm – C++.
What is more, the technique is supplemented with Microsoft CryptoAPI algorithm unlike AES and SHA256, previously employed by Dyre. Unlike the previous version of the virus, Trojan.TrickBot executes COM and TaskScheduler commands to maintain the computer under control.
The first campaigns were targeted Australian banks only. However, on April 2017 TrickBot Trojan has been spotted attacking banks in The United States, Canada, United Kingdom, Ireland, Germany, France, Switzerland, and New Zealand.[6]

While TrickBot Trojan mainly targets corporate networks and businesses, regular users might encounter it as well. In case of the attack, you need to run a full system scan with a reputable malware removal program, such as SpyHunter 5Combo Cleaner or Malwarebytes. It will help to remove TrickBot from the system entirely.
Due to excessive malware's capabilities, systems that the infection occurred on might struggle to operate properly, even after TrickBot removal. In such a case, the affected machines can be remediated with the help of repair tool FortectIntego.
Fake Lloyd's bank emails help to distribute Trick Bot
Experts have recently spotted a new way which was employed to distribute TrickBot trojan. The malware was spreading inside the email letters from fake Lloyds Bank[7]. It was disguised as an attachment holding confidential account documents. Note that official Lloyds Bank is not related to this malspam campaign in any way, except that its name was used for malevolent purposes.
Victims report receiving an email from <secure@lloyds-commercial.com> on December 6, 2017, which contained Protected32.doc attachments. Obviously, the letter was designed to look extremely genuine and has convinced many people to believe its legitimacy.
The email briefly explained to the recipients that it is an automatically sent message which does not require a reply. It simply encouraged the gullible people to check the attachment and included the following instructions:
To unlock/view your documents, follow the instructions below.
1. Look for an attachment (Protected.doc) ( typically at the top or bottom; location varies by email service).
2. Your Authorization code is: 430SJAOPS982XXS.
3. Enter the authorization code when prompted.
Remember, that you should not open any email attachments which look suspicious or unrelated to you. We want to remind you about the previous techniques which hackers used to spread TrickBot malware. The hackers have tried to employ a similar malspam campaign in June 2017 which was almost identical to the one spreading Jaff ransomware.

Cybercriminals used social engineering techniques to trick users into opening a malicious email attachment. They included an obfuscated PDF file that opens a Word document. This file asked to enable macro command in order to see the content. Clicking “Enable Macros” button executes Trojan on the system. New victims of TrickBot were banks in India, Singapore, Netherlands, and Bulgaria. [8]
However, financial institutions were not the only ones who have been suffering from TrickBot Trojan. Now it is also targeting two Customer Relationship Manager (CRM) SaaS providers and PayPal users. In May security researchers discovered two malware distribution campaigns that targeted 210 URLs.
Latest TrickBot's appearances
TrickBot's update came in March 2018, when hackers improved the code by making its detection and defense more complicated. It has also been utilized to provide screen-locking capabilities, working similarly to ransomware. However, it seems that this aspect of the virus is not fully developed yet, as the module that is meant to encrypt files does not accomplish its goal.
In May same year, security researchers[9] noted a collaboration of two viruses – TrickBot and IcedID. While most Trojans would usually remove previously installed malware, authors of these malicious threats decided to work together and share profits. Apparently, computers infected with IcedID were also injected with TrickBot, making the operation of malware much more efficient.
In June 2018,[10] TrickBot targeted UK citizens, sending them spoofing HM Revenue & Customs emails, which claimed that there is an outstanding amount of money that victims need to pay back. Users were then prompted to click on a malicious link or on the attachment, which delivered TrickBot malware.
In 2019, Trickbot was seen in several campaigns that were also infecting users with such threats as Ryuk ransomware or Emotet. In summer, more than 250 million email accounts were compromised by the malware, sending out malspam to other targets worldwide. Additionally, security experts also noticed several updates to TrickBot during 2019, including its “TrichBooster” module that allows the exploitation of SMB (Server Message Block) vulnerability in order to send spam and avoid detection from deleting sent emails from the outbox.[11]
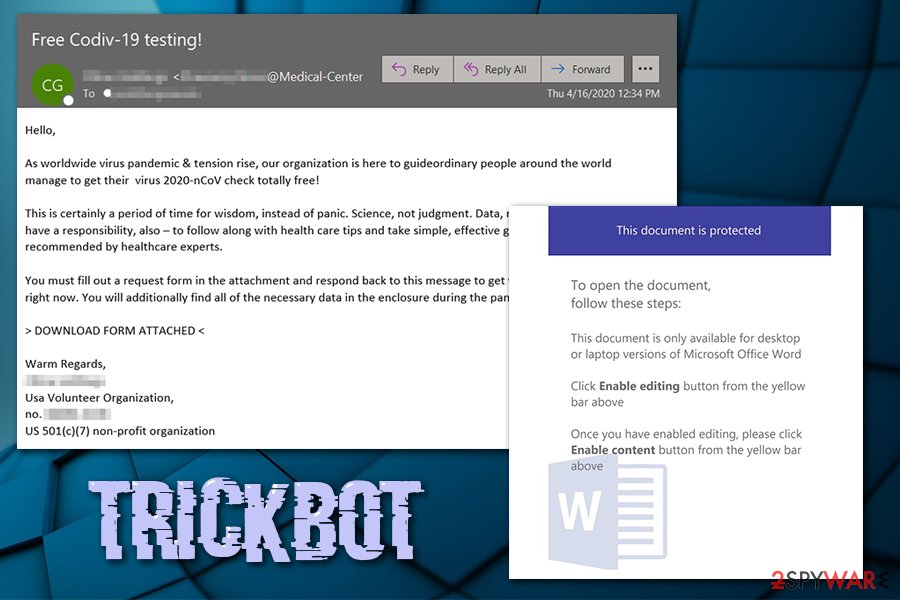
During the 2020 COVID-19 pandemic, TrickBot was also employed in malicious coronavirus-themed spam emails, where the attackers use WHO (World Health Organization) and other entities. Security experts are warning organizations that more variations of phishing emails are targeting companies and businesses with TrickBot and other malware:[12]
Attacks/campaigns using COVID-themed lures has continued to increase over the last week. We continue to observe increasing amounts of malicious messages and websites preying on the fear and uncertainty around the pandemic.
Criminals released a test version of the password-stealing grabber.dll module by mistake
In the first half of July 2020, cybersecurity researcher Vitaly Kremez[13] shared the news about the infamous credential-stealer TrickBot on Twitter. In fact, it turns out that the managers of this deadly dangerous Trojan failed to initiate their latest attack. According to the researcher, crooks released a test module of password-stealing grabber.dll, which once installed informs the victim via the default web browser that the system has been infected. Google Chrome, Mozilla Firefox, Internet Explorer, Microsoft Edge, Opera, and users of other web browsers started reporting the following message last week:
You see this message because the program named grabber gathered some information from your browser. If you do not know what is happening it is the time to start be worrying.
Please, ask your system administrator for details.
TrickBot trojan is being distributed via spam email attachments and, usually, initiates its malicious activities in a way to remain unnoticed. Thus, the above message showing up on web browsers indicates the fact that it's the first time when criminals failed and the current campaign is not going to be very successful.
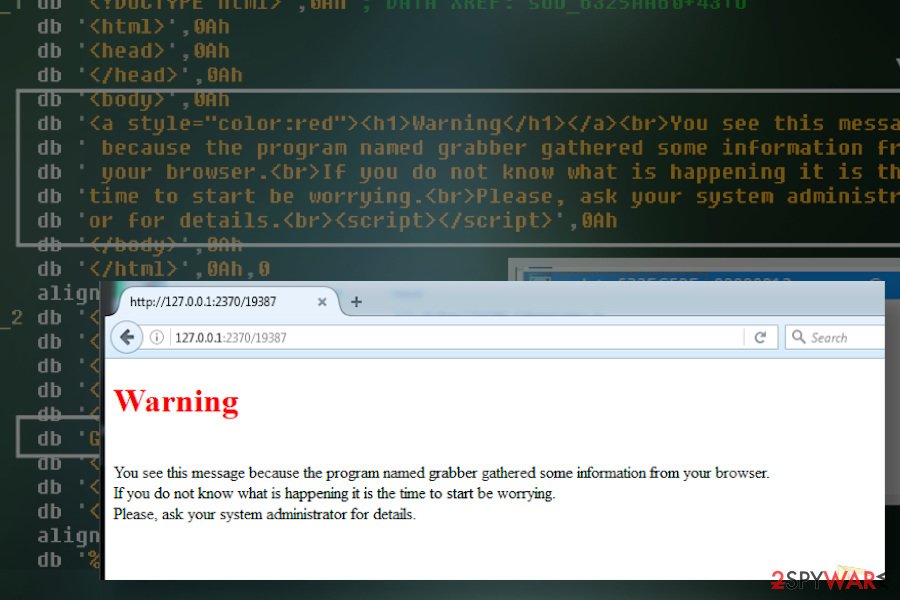
The notification saying “the program named grabber gathered some information from your browser” is genuine. It's not a scam as many consider it. The alert is triggered by the grabber.dll, which is one of the main TrickBot virus executables aiming at harvesting saved passwords and browser credentials. In case of success, the virus gets all credentials that are required for the connection to the victim's bank account or other accounts.
People who have received the notification about “program named grabber” while web browsing must immediately close the browser, restart the machine into Safe Mode, and run a full system scan with a professional anti-malware program. This notification means that a TrickBot Grabber has been recently installed and has to be removed to prevent data leakage, identity theft, and money loss.
Trojan has mostly been spread via phishing emails
Experts have detected that phishing emails are still the primary distribution method used by hackers to infiltrate TrickBo[14]. They might disguise under genuine looking PDF or DOC documents and contain Invoice or Private Details subject line. People are easily tricked to open malicious attachments since criminals imitate well-known companies.
Malware also aims at PayPal users. Thus, if you receive an email from PayPal about suspicious activities in your account or reporting about other problems, you should login into their website directly instead of clicking provided links or attached documents.
The crooks develop different techniques to access personal information. Thus, such emails are usually very convincing. Do not fall into their trap even if they ask you to review suspicious invoice documents or tax reports.
Furthermore, the Trojan can attach itself to a free application. So you should give it a second thought before installing even a new media player. The latter often happens to be the carrier of more malicious cyber threats. By exercising additional caution, you will reduce the probability of TrickBot hijack.

Terminate TrickBot virus using trusted security software
The only way to clean your system from Trojan horse is to employ a reliable security software for TrickBot removal. This malicious program has the ability to imitate legitimate computer processes or files.
Therefore, trying to find and eliminate all malware-related files from the computer is a difficult and complicated task that might lead to irreparable damage to the system.
We highly recommend installing powerful anti-malware software and running a full system scan. In case the malware managed to affect the whole network or a server, appropriate scans should be executed. We want to remind you that you have to remove TrickBot immediately because this data-stealing trojan might lead to money loss and other serious privacy-related issues.
It is also important to change all the server/system-related passwords and tokens (if such were used) in order to avoid future compromise.
Getting rid of TrickBot virus. Follow these steps
Manual removal using Safe Mode
If TrickBot does not let you operate the anti-virus program properly, enter Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove TrickBot using System Restore
Another way to get rid of the virus is by using System Restore function:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of TrickBot. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from TrickBot and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Trick Bot – Dyreza’s successor. Malwarebytes Labs. The Security Blog By Malwarebytes.
- ^ Pierluigi Paganini. Threat actors behind the financial trojan TrickBot have been updating its campaigns targeting Payment Processors and CRM Providers. SecurityAffairs. The Website About Online Security.
- ^ Zack Whittaker. TrickBot malware learns how to spam, ensnares 250M email addresses. TechCrunch. Startup and Technology News.
- ^ Microsoft Security Intelligence. Based on Office 365 ATP data, Trickbot is the most prolific malware operation using COVID-19 themed lures. Twitter. Social network.
- ^ Luciano Hernández. What is TrickBot?. F-Secure. Security blog.
- ^ Limor Kessem. TrickBot Is Hand-Picking Private Banks for Targets — With Redirection Attacks in Tow!. SecurityIntelligence. Analysis & Insight on Information Security.
- ^ Trickbot delivered via fake Lloyds Bank Confidential account documents malspam. My Online Security. How to protect yourself and tighten security.
- ^ Sara Boddy, Jesse Smith, Doron Voolf. TrickBot Expands Global Targets Beyond Banks And Payment Processors To CRMs. F5 Labs. Threat Data Blog.
- ^ Vitali Kremez. Trickbot and IcedID Botnet Operators Collaborate to Increase Impact. Flashpoint. Security research team.
- ^ Fake HMRC “Important : Outstanding Amount ” delivers Trickbot via CVE-2018-8174. My Online Security. Security site.
- ^ TRICKBOT’s newly released modules makes it even trickier. Trend Micro. Security blog.
- ^ Jim Walter. Threat Intel | Cyber Attacks Leveraging the COVID-19/CoronaVirus Pandemic. SentinelLabs. Security blog.
- ^ Vitali Kremez profile. Twitter. Social networking platform.
- ^ Brendan Griffin. TrickBot Featured in New Wave of Phishing Emails Signaling Renewed Use of this Botnet Malware. PhishMe. The Website About Phishing, Prevention And Latest News.







